标签:
一.概述
以太网的arp数据包结构:
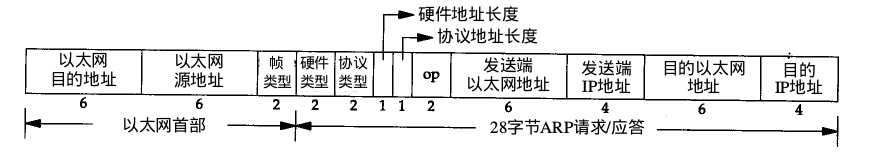
arp结构op操作参数:1为请求,2为应答。
常用的数据结构如下:
1.物理地址结构位于netpacket/packet.h
1 struct sockaddr_ll 2 { 3 unsigned short int sll_family; 4 unsigned short int sll_protocol; 5 int sll_ifindex; 6 unsigned short int sll_hatype; 7 unsigned char sll_pkttype; 8 unsigned char sll_halen; 9 unsigned char sll_addr[8]; 10 };
sll_ifindex是网络(网卡)接口索引,代表从这个接口收发数据包
2.网络(网卡)接口数据结构位于net/if.h
1 struct ifreq 2 { 3 # define IFHWADDRLEN 6 4 # define IFNAMSIZ IF_NAMESIZE 5 union 6 { 7 char ifrn_name[IFNAMSIZ]; /* Interface name, e.g. "en0". */ 8 } ifr_ifrn; 9 10 union 11 { 12 struct sockaddr ifru_addr; 13 struct sockaddr ifru_dstaddr; 14 struct sockaddr ifru_broadaddr; 15 struct sockaddr ifru_netmask; 16 struct sockaddr ifru_hwaddr; 17 short int ifru_flags; 18 int ifru_ivalue; 19 int ifru_mtu; 20 struct ifmap ifru_map; 21 char ifru_slave[IFNAMSIZ]; /* Just fits the size */ 22 char ifru_newname[IFNAMSIZ]; 23 __caddr_t ifru_data; 24 } ifr_ifru; 25 };
该结构里面包含2个union,第一个是接口名,如:eth0,wlan0等。可以通过ioctl()函数来获取对应的接口信息,ip地址,mac地址,接口索引等。
3.以太网首部结构位于net/ethernet.h
1 struct ether_header 2 { 3 u_int8_t ether_dhost[ETH_ALEN]; /* destination eth addr */ 4 u_int8_t ether_shost[ETH_ALEN]; /* source ether addr */ 5 u_int16_t ether_type; /* packet type ID field */ 6 } __attribute__ ((__packed__));
ether_type帧类型:常见的有IP,ARP,RARP,都有对应的宏定义。
4.arp包结构位于netinet/if_ether.h
1 struct ether_arp { 2 struct arphdr ea_hdr; /* fixed-size header */ 3 u_int8_t arp_sha[ETH_ALEN]; /* sender hardware address */ 4 u_int8_t arp_spa[4]; /* sender protocol address */ 5 u_int8_t arp_tha[ETH_ALEN]; /* target hardware address */ 6 u_int8_t arp_tpa[4]; /* target protocol address */ 7 }; 8 #define arp_hrd ea_hdr.ar_hrd 9 #define arp_pro ea_hdr.ar_pro 10 #define arp_hln ea_hdr.ar_hln 11 #define arp_pln ea_hdr.ar_pln 12 #define arp_op ea_hdr.ar_op
上面的ether_arp结构还包含一个arp首部,位于net/if_arp.h
1 struct arphdr 2 { 3 unsigned short int ar_hrd; /* Format of hardware address. */ 4 unsigned short int ar_pro; /* Format of protocol address. */ 5 unsigned char ar_hln; /* Length of hardware address. */ 6 unsigned char ar_pln; /* Length of protocol address. */ 7 unsigned short int ar_op; /* ARP opcode (command). */ 8 }
二.arp请求代码
1 /** 2 * @file arp_request.c 3 */ 4 5 #include <stdio.h> 6 #include <stdlib.h> 7 #include <string.h> 8 #include <unistd.h> 9 #include <sys/ioctl.h> 10 #include <sys/socket.h> 11 #include <arpa/inet.h> 12 #include <netinet/in.h> 13 #include <netinet/if_ether.h> 14 #include <net/ethernet.h> 15 #include <net/if_arp.h> 16 #include <net/if.h> 17 #include <netpacket/packet.h> 18 19 /* 以太网帧首部长度 */ 20 #define ETHER_HEADER_LEN sizeof(struct ether_header) 21 /* 整个arp结构长度 */ 22 #define ETHER_ARP_LEN sizeof(struct ether_arp) 23 /* 以太网 + 整个arp结构长度 */ 24 #define ETHER_ARP_PACKET_LEN ETHER_HEADER_LEN + ETHER_ARP_LEN 25 /* IP地址长度 */ 26 #define IP_ADDR_LEN 4 27 /* 广播地址 */ 28 #define BROADCAST_ADDR {0xff, 0xff, 0xff, 0xff, 0xff, 0xff} 29 30 void err_exit(const char *err_msg) 31 { 32 perror(err_msg); 33 exit(1); 34 } 35 36 /* 填充arp包 */ 37 struct ether_arp *fill_arp_packet(const unsigned char *src_mac_addr, const char *src_ip, const char *dst_ip) 38 { 39 struct ether_arp *arp_packet; 40 struct in_addr src_in_addr, dst_in_addr; 41 unsigned char dst_mac_addr[ETH_ALEN] = BROADCAST_ADDR; 42 43 /* 转换成网络字节序 */ 44 inet_pton(AF_INET, src_ip, &src_in_addr); 45 inet_pton(AF_INET, dst_ip, &dst_in_addr); 46 47 /* 整个arp包 */ 48 arp_packet = (struct ether_arp *)malloc(ETHER_ARP_LEN); 49 arp_packet->arp_hrd = htons(ARPHRD_ETHER); 50 arp_packet->arp_pro = htons(ETHERTYPE_IP); 51 arp_packet->arp_hln = ETH_ALEN; 52 arp_packet->arp_pln = IP_ADDR_LEN; 53 arp_packet->arp_op = htons(ARPOP_REQUEST); 54 memcpy(arp_packet->arp_sha, src_mac_addr, ETH_ALEN); 55 memcpy(arp_packet->arp_tha, dst_mac_addr, ETH_ALEN); 56 memcpy(arp_packet->arp_spa, &src_in_addr, IP_ADDR_LEN); 57 memcpy(arp_packet->arp_tpa, &dst_in_addr, IP_ADDR_LEN); 58 59 return arp_packet; 60 } 61 62 /* arp请求 */ 63 void arp_request(const char *if_name, const char *dst_ip) 64 { 65 struct sockaddr_ll saddr_ll; 66 struct ether_header *eth_header; 67 struct ether_arp *arp_packet; 68 struct ifreq ifr; 69 char buf[ETHER_ARP_PACKET_LEN]; 70 unsigned char src_mac_addr[ETH_ALEN]; 71 unsigned char dst_mac_addr[ETH_ALEN] = BROADCAST_ADDR; 72 char *src_ip; 73 int sock_raw_fd, ret_len, i; 74 75 if ((sock_raw_fd = socket(PF_PACKET, SOCK_RAW, htons(ETH_P_ARP))) == -1) 76 err_exit("socket()"); 77 78 bzero(&saddr_ll, sizeof(struct sockaddr_ll)); 79 bzero(&ifr, sizeof(struct ifreq)); 80 /* 网卡接口名 */ 81 memcpy(ifr.ifr_name, if_name, strlen(if_name)); 82 83 /* 获取网卡接口索引 */ 84 if (ioctl(sock_raw_fd, SIOCGIFINDEX, &ifr) == -1) 85 err_exit("ioctl() get ifindex"); 86 saddr_ll.sll_ifindex = ifr.ifr_ifindex; 87 saddr_ll.sll_family = PF_PACKET; 88 89 /* 获取网卡接口IP */ 90 if (ioctl(sock_raw_fd, SIOCGIFADDR, &ifr) == -1) 91 err_exit("ioctl() get ip"); 92 src_ip = inet_ntoa(((struct sockaddr_in *)&(ifr.ifr_addr))->sin_addr); 93 printf("local ip:%s\n", src_ip); 94 95 /* 获取网卡接口MAC地址 */ 96 if (ioctl(sock_raw_fd, SIOCGIFHWADDR, &ifr)) 97 err_exit("ioctl() get mac"); 98 memcpy(src_mac_addr, ifr.ifr_hwaddr.sa_data, ETH_ALEN); 99 printf("local mac"); 100 for (i = 0; i < ETH_ALEN; i++) 101 printf(":%02x", src_mac_addr[i]); 102 printf("\n"); 103 104 bzero(buf, ETHER_ARP_PACKET_LEN); 105 /* 填充以太首部 */ 106 eth_header = (struct ether_header *)buf; 107 memcpy(eth_header->ether_shost, src_mac_addr, ETH_ALEN); 108 memcpy(eth_header->ether_dhost, dst_mac_addr, ETH_ALEN); 109 eth_header->ether_type = htons(ETHERTYPE_ARP); 110 /* arp包 */ 111 arp_packet = fill_arp_packet(src_mac_addr, src_ip, dst_ip); 112 memcpy(buf + ETHER_HEADER_LEN, arp_packet, ETHER_ARP_LEN); 113 114 /* 发送请求 */ 115 ret_len = sendto(sock_raw_fd, buf, ETHER_ARP_PACKET_LEN, 0, (struct sockaddr *)&saddr_ll, sizeof(struct sockaddr_ll)); 116 if ( ret_len > 0) 117 printf("sendto() ok!!!\n"); 118 119 close(sock_raw_fd); 120 } 121 122 int main(int argc, const char *argv[]) 123 { 124 if (argc != 3) 125 { 126 printf("usage:%s device_name dst_ip\n", argv[0]); 127 exit(1); 128 } 129 130 arp_request(argv[1], argv[2]); 131 132 return 0; 133 }
流程:命令行接收网卡接口名和要请求的目标IP地址,传入arp_request()函数。用PF_PACKET选项创建ARP类型的原始套接字。用ioctl()函数通过网卡接口名来获取该接口对应的mac地址,ip地址,接口索引。接口索引填充到物理地址sockaddr_ll里面。然后填充以太首部,源地址对应刚刚的网卡接口mac地址,目标地址填广播地址(第28行定义的宏)。以太首部帧类型是ETHERTYPE_ARP,代表arp类型。接着填充arp数据包结构,同样要填充源/目标的ip地址和mac地址,arp包的操作选项填写ARPOP_REQUEST,代表请求操作。填充完成后发送到刚刚的物理地址sockaddr_ll。
三.接收arp数据包
1 /** 2 * @file arp_recv.c 3 */ 4 5 #include <stdio.h> 6 #include <stdlib.h> 7 #include <string.h> 8 #include <unistd.h> 9 #include <sys/socket.h> 10 #include <arpa/inet.h> 11 #include <netinet/in.h> 12 #include <netinet/if_ether.h> 13 #include <net/if_arp.h> 14 #include <net/ethernet.h> 15 16 /* 以太网帧首部长度 */ 17 #define ETHER_HEADER_LEN sizeof(struct ether_header) 18 /* 整个arp结构长度 */ 19 #define ETHER_ARP_LEN sizeof(struct ether_arp) 20 /* 以太网 + 整个arp结构长度 */ 21 #define ETHER_ARP_PACKET_LEN ETHER_HEADER_LEN + ETHER_ARP_LEN 22 /* IP地址长度 */ 23 #define IP_ADDR_LEN 4 24 25 void err_exit(const char *err_msg) 26 { 27 perror(err_msg); 28 exit(1); 29 } 30 31 int main(void) 32 { 33 struct ether_arp *arp_packet; 34 char buf[ETHER_ARP_PACKET_LEN]; 35 int sock_raw_fd, ret_len, i; 36 37 if ((sock_raw_fd = socket(PF_PACKET, SOCK_RAW, htons(ETH_P_ARP))) == -1) 38 err_exit("socket()"); 39 40 while (1) 41 { 42 bzero(buf, ETHER_ARP_PACKET_LEN); 43 ret_len = recv(sock_raw_fd, buf, ETHER_ARP_PACKET_LEN, 0); 44 if (ret_len > 0) 45 { 46 /* 剥去以太头部 */ 47 arp_packet = (struct ether_arp *)(buf + ETHER_HEADER_LEN); 48 /* arp操作码为2代表arp应答 */ 49 if (ntohs(arp_packet->arp_op) == 2) 50 { 51 printf("==========================arp replay======================\n"); 52 printf("from ip:"); 53 for (i = 0; i < IP_ADDR_LEN; i++) 54 printf(".%u", arp_packet->arp_spa[i]); 55 printf("\nfrom mac"); 56 for (i = 0; i < ETH_ALEN; i++) 57 printf(":%02x", arp_packet->arp_sha[i]); 58 printf("\n"); 59 } 60 } 61 } 62 63 close(sock_raw_fd); 64 return 0; 65 }
流程:创建ARP类型的原始套接字。直接调用接收函数,会收到网卡接收的arp数据包,判断收到的arp包操作是arp应答,操作码是2。然后剥去以太首部,取出源mac地址和ip地址!!!
四.实验
为了更直观,我们打开wireshark一起观察,我这里是wlan环境,监听wlan0。原始套接字要以root身份运行,先运行arp_recv,然后运行arp_request发送arp请求:
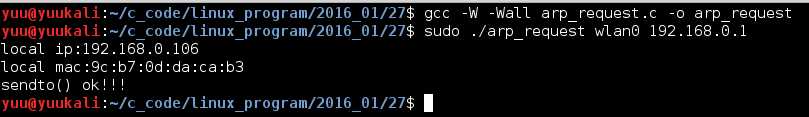
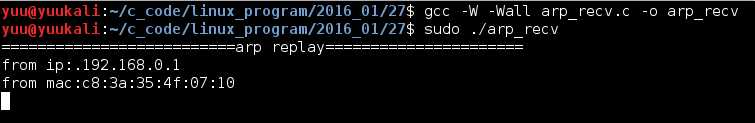
wireshark结果:
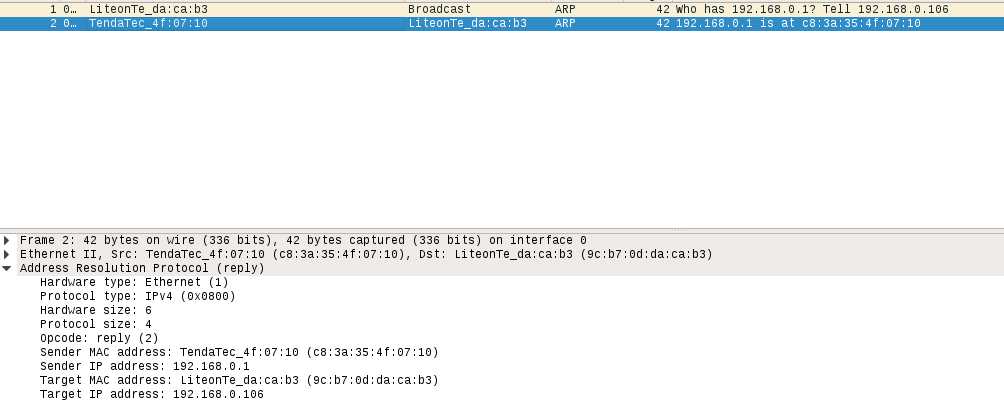
上面可以看到,第一条数据包询问谁是192.168.0.1,然后第二条数据包发送了一个回复,可以看到wireshark里面Opcode:reply(2)。源ip和mac地址跟我们自己的接收程序一样。
标签:
原文地址:http://www.cnblogs.com/yuuyuu/p/5164685.html