SSH: Secure shell, prototol, 22/tcp,安全的远程登录
OpenSSH: ssh协议的开源实现
ssh协议版本
v1: 基于CRC-32做MAC,不安全: man-in-middle
v2: 双方主机协议选择安全的MAC方式, 基于DH算法做密钥交换,基于RSA或DSA算法实现身份认证;
两种方式的用户登录认证:基于Password & 基于key
OpenSSH: C/S
Client: ssh, scp, sftp,
Server: sshd
备注:Windows clinet: xshell, putty, securecrt, sshsecureshellclient
客户端组件:sshd
ssh, 配置文件 :/etc/ssh/ssh_config
格式:ssh [user@]host [COMMAND] ssh [ –l user ] host [COMMAND] -p port: 远程服务器监听的端口;
服务器端组件:sshd
sshd, 配置文件: /etc/ssh/sshd_config
示例:模拟环境
CentOS 7, IP: 192.168.0.111
CentOS 6.7,IP:192.168.0.113
可以使用如下命令查看系统的版本信息(适用用RedHat, CentOS)
[root@jimjimlv ~]# cat /etc/redhat-release CentOS release 6.7 (Final)
不指定用户远程登录主机CentOS 6.7
[root@localhost ~]# cat /etc/redhat-release CentOS Linux release 7.1.1503 (Core) [root@localhost ~]# ssh 192.168.0.113 The authenticity of host ‘192.168.0.113 (192.168.0.113)‘ can‘t be established. RSA key fingerprint is a8:16:d9:15:8a:01:e5:d3:fb:26:bd:94:13:3e:50:6e. Are you sure you want to continue connecting (yes/no)? yes #第一次授权密钥确认 Warning: Permanently added ‘192.168.0.113‘ (RSA) to the list of known hosts. root@192.168.0.113‘s password: #输入root管理密码 Last login: Fri Feb 19 22:14:48 2016 from 192.168.0.109 #成功登录远程主机 [root@jimjimlv ~]# cat /etc/redhat-release CentOS release 6.7 (Final)
使用exit命令退出远程登录
[root@jimjimlv ~]# exit logout Connection to 192.168.0.113 closed.
指定用户centos6.7远程登录主机CentOS 6.7
[root@localhost ~]# ssh centos6.7@192.168.0.113 centos6.7@192.168.0.113‘s password: [centos6.7@jimjimlv ~]$ cat /etc/redhat-release CentOS release 6.7 (Final)
生产环境当中,从安全的角度出发,默认的主机访问端口都需要修改掉,以下将演示修改端口后的主机远程访问方法
步骤一、修改配置文件/etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.93 2014/01/10 05:59:19 djm Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/local/bin:/usr/bin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options override the # default value. # If you want to change the port on a SELinux system, you have to tell # SELinux about this change. # semanage port -a -t ssh_port_t -p tcp #PORTNUMBER # Port 2223 #AddressFamily any ListenAddress 0.0.0.0 #ListenAddress ::
重启sshd服务
[root@localhost ssh]# systemctl restart sshd.service
关闭防火墙
CentOS 6 #service sshd restart CentOS 7 #systemctl stop firewalld.service Xsheel:\>ssh 2223 #IP地址后紧跟着新端口号
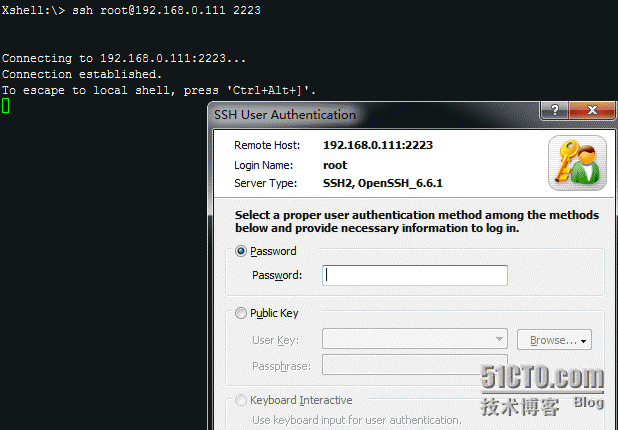
Last login: Sat Feb 20 22:49:35 2016 from 192.168.0.109 [root@localhost ~]# cat /etc/redhat-release CentOS Linux release 7.1.1503 (Core)
基于key的ssh远程登录
[root@localhost .ssh]# ssh-keygen -t rsa #生成密钥命令 Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: 9d:fc:93:7d:9a:00:01:47:23:69:9e:08:0c:cf:ca:bd root@localhost.localdomain The key‘s randomart image is: +--[ RSA 2048]----+ | .o oo+ | | oo o+ . | | o. + .. | | . o . oo o | | o . S = | | . o o | | E = . .| | o + | | o | +-----------------+ [root@localhost .ssh]# ls #密钥存储的位置为/root/.ssh/ id_rsa id_rsa.pub known_hosts [root@localhost .ssh]# ssh-copy-id -i /root/.ssh/id_rsa root@192.168.0.113 #复制密钥到远程主机 /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@192.168.0.113‘s password: #输入root登录密码 Number of key(s) added: 1 Now try logging into the machine, with: "ssh ‘root@192.168.0.113‘" and check to make sure that only the key(s) you wanted were added. [root@localhost .ssh]# ssh root@192.168.0.113 #访问登录远程主机时,无需提供账户与密码认证登录 Last login: Sat Feb 20 01:53:08 2016
直接运行远程主机的某个命令:
[root@localhost .ssh]# ssh root@192.168.0.113 ‘ifconfig‘ eth0 Link encap:Ethernet HWaddr 00:0C:29:F0:55:67 inet addr:192.168.0.113 Bcast:192.168.0.255 Mask:255.255.255.0 inet6 addr: fe80::20c:29ff:fef0:5567/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:6116 errors:0 dropped:0 overruns:0 frame:0 TX packets:1449 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:526598 (514.2 KiB) TX bytes:181464 (177.2 KiB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:8 errors:0 dropped:0 overruns:0 frame:0 TX packets:8 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:628 (628.0 b) TX bytes:628 (628.0 b) [root@localhost .ssh]#
本文出自 “WE BECOME WHATWEPRACTICE” 博客,请务必保留此出处http://nearlv.blog.51cto.com/2432295/1743797
原文地址:http://nearlv.blog.51cto.com/2432295/1743797