标签:
Network Hardware
1. A computer network is a collection of computers connected by communication links
2. communication link:
1.Point to Point
2.Broadcast
3. Nodes: the entities in the network(hosts, routers, servers, devices, programs, etc)
Edges/Links: the connections between entities
4. Topology: a topologyrefers to the physical layout of the network.
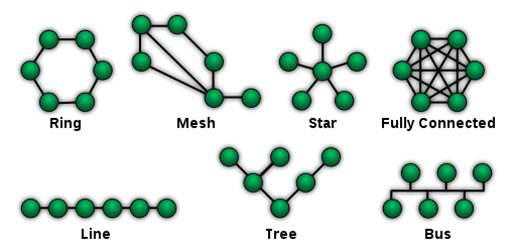
5.Network hardware:
1m: Personal area network
Point-to-point: USB/Serial/Parallel/Infrared
Boradcast: Bluetooth
10m to 1km: Local area network(LAN)
Boradcast:
1.Cable 100Mbps to 10Gbps (Switched Ethernet)
2.Radio(Wlan) 11Mbps to hundreds Mbps (Wifi)
10km: Metropolitan area network
100km to 1000km: Wide area network(WAN)
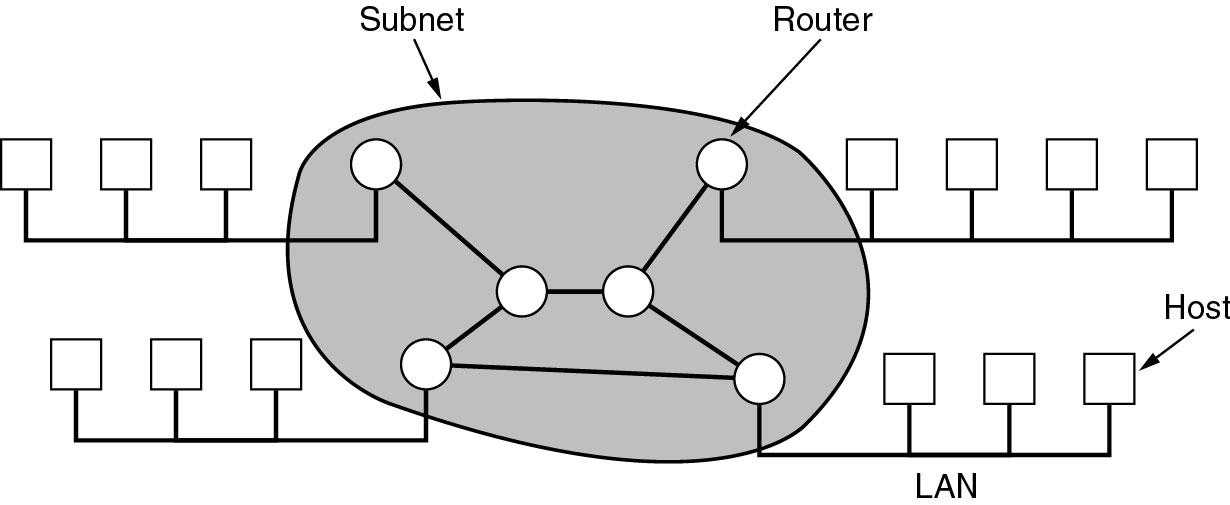
Router: A computer that provde communications service
Subnet: Collection of routers
Host: Send packets of data to each other via LAN and Rounter
---
SubNet: End systems (hosts) are interconnected via a communication sub-network
SubNet is composed of lines (wires) and switches
SubNet may be based on packet-switched and/or circuit-switched technologies
–Packet switched means users compete for bandwidth
–Circuit-switched means users are guaranteed bandwidth
10000km: The Internet
Connecting networks together to form a network of networks is called an internet
*The largest (worldwide) internet is called the Internet
6. The Internet is an infrastructure
The World Wide Web is just another service that uses The Internet
-----------------------------------------------------------------------
Network Software
1. Communication protocols
Communication protocols consist of a set of rules governing the interaction of processes in a network
Communication protocols define:
1. The service it provides
2. The assumptions about the environment where it executes, including the services it uses
3. The type and format of the messages (called frames or packets) used to implement it
4. The rules (algorithms) guarding the consistency of message exchanges and the integrity of the service provided
2. Connection-oriented service protocol:
1. Connection-oriented Packet Switching(Virtual Circuit Switching)
Establish a connection→Use it for data transfer(if the connection is established)→Release the connection
*Data is always delivered and in the order sent
3. Connectionless service protocol:
1. Connectionless packet switching(Datagram Switching)
1.There is no attempt to set up a connection
2.Each message carries the full destination address
3.Each message is routed through the network independent of all the others
4. Protocol/service hierarchies
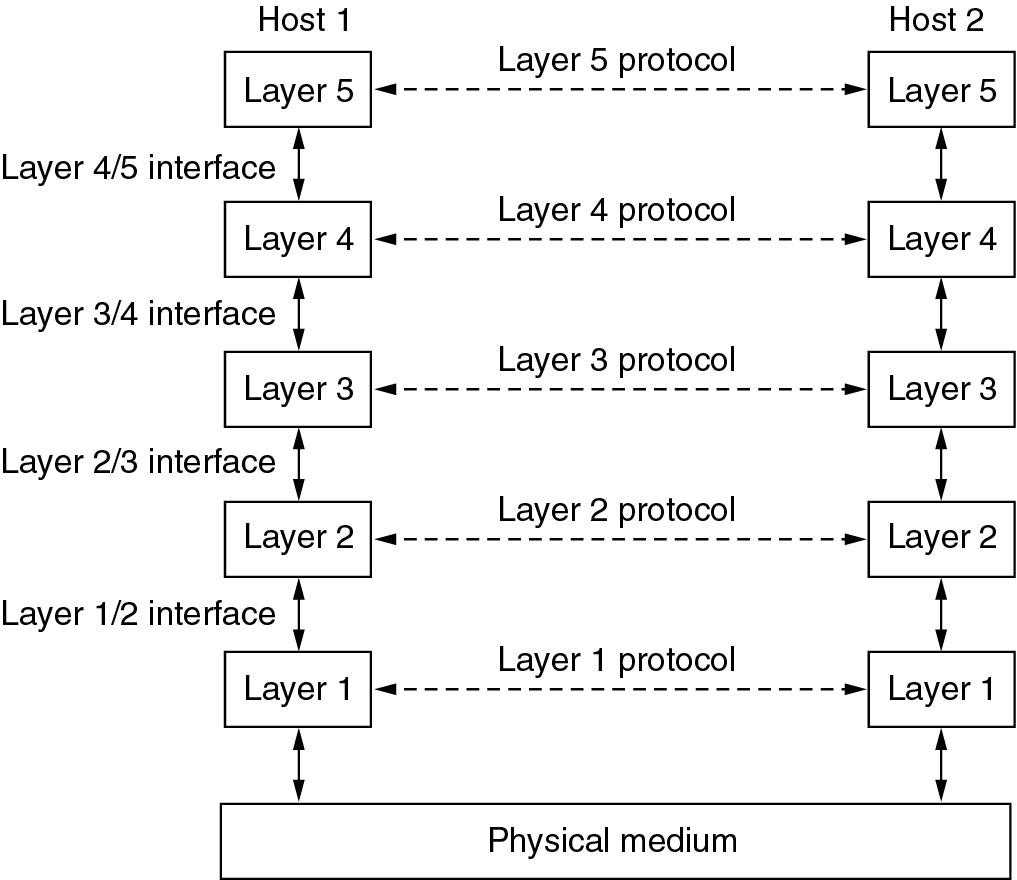
1. Networks are organised as a series of layers, each one built on the one below it
2. The lower layers provide services to the upper layers, the upper layers are shielded how the services implemented
3. When Layer N in one machine holds a conversation with Layer N in another machine(peer):
The rules and conventions are called protocols.
Data is send indirectly between the peers, by using the services of the lower layers
4. The interface between adjacent layers defines the primitive operations and services offered
5. OSI Reference Model
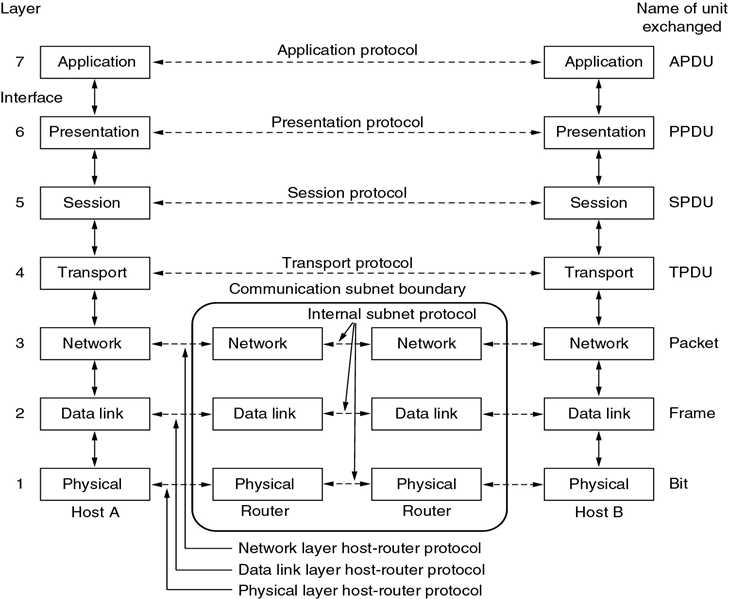
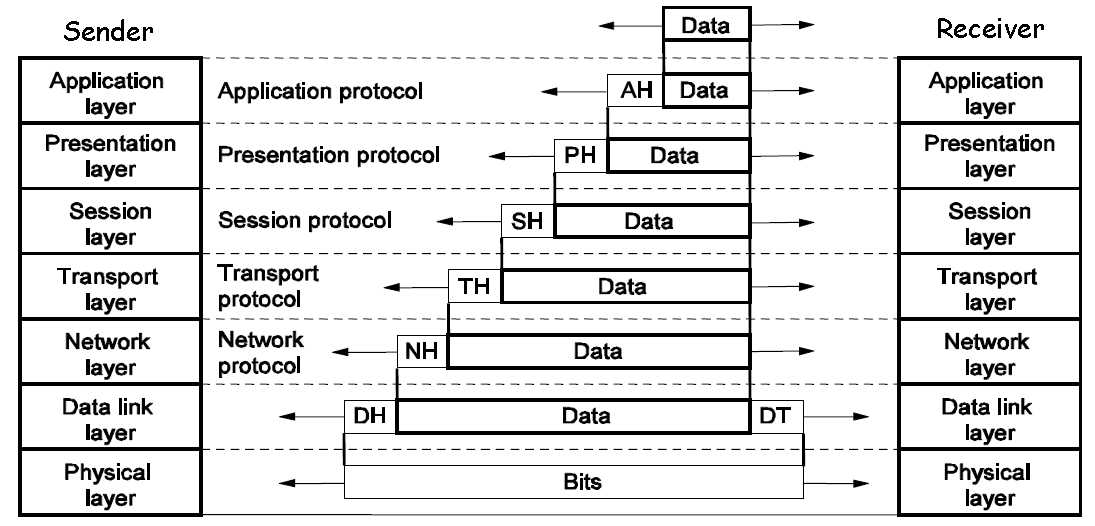
1. The data switch between appliction is translated as following:
Layer 7 → Layer 3(Then packed) → Layer 1 → Layer 3 in router this side → Layer 3 in router target side → Layer 3 target side(unpacking) → Layer 7
2. Layer
1. Layer 1 (Physical layer) defines the electrical, mechanical, procedural, and functional specifications
–activating the physical link between end systems
–maintaining the physical link between end systems
–deactivating the physical link between end systems
2. Layer 2 (Data Link Layer) provides a data transmission service free of transmission errors between adjacent nodesusing the physical layer
Layer 2 breaks data from the network layer into frames
–process acknowledgements
–detect and recover from damaged, lost and duplicate frame problems
–make sure the transmitter does not drown the receiver (flow control)
–control the access to the medium in broadcast networks(MAC-Medium Access Control sublayer)
3. Layer 3 (Network Layer) controls how a packet is routed from source to destination through a subnet
–determine the route for each source/destination pair
–perform congestion control (when there are too many messages in transit)
–maintain accounting information
–overcome the problem of interconnecting heterogeneous subnets (LANs and WANs, each with different protocols)
4. Layer 4 (Transport Layer) creates a distinct network connection for each transport connection
1.Layer 4 is the real (lowest) end-to-end layer between source and destination applications
2.It creates a distinct network connection for each transport connection
–or creates multiple connections and divides the data among those connections to improve performance
–or shares several transport connections onto the same network connection to reduce cost
3.It provides end to end flow control (data link layer only deals with adjacent nodes)
4.It provides end to end error detection and correction
5.It may provide additional congestion control
5. Layer 5 (Session Layer)
1.Performs dialogue control(Who’s turn is it to talk?)
2.Token management(Who has access to shared resource?)
3.Data synchronisation(Where were we before the line went down?)
6. Layer 6(Presentation Layer)
1.Concerned with syntax and semantics of data rather than it’s transmission
2.Provides common data abstractions to allow communication between heterogeneous computers
7. Layer 7(Application Layer) is where the applications reside
–Network virtual terminals (TELNET)
–File transfer (FTP)
–Electronic mail (SMTP)
–Newsgroups (NNTP)
–Web (HTTP)
–Directory lookup (DNS)
–Electronic commerce
3. Terminology
1. Entities : Active elements in each layer
2. Entities in the same layer on different machines are called peer entities. They exchange Protocol Data Units (PDU)
3. Entities in layer N implement a service used by layer N+1. Layer N is the “service provider”, Layer N+1 is the “service user”
4. Layers N and N+1 exchange Interface Data Units (IDU), containing Interface Control Information (ICI) and Service Data Units (SDU)
5. Services are accessible at a SAP (Service Access Point)
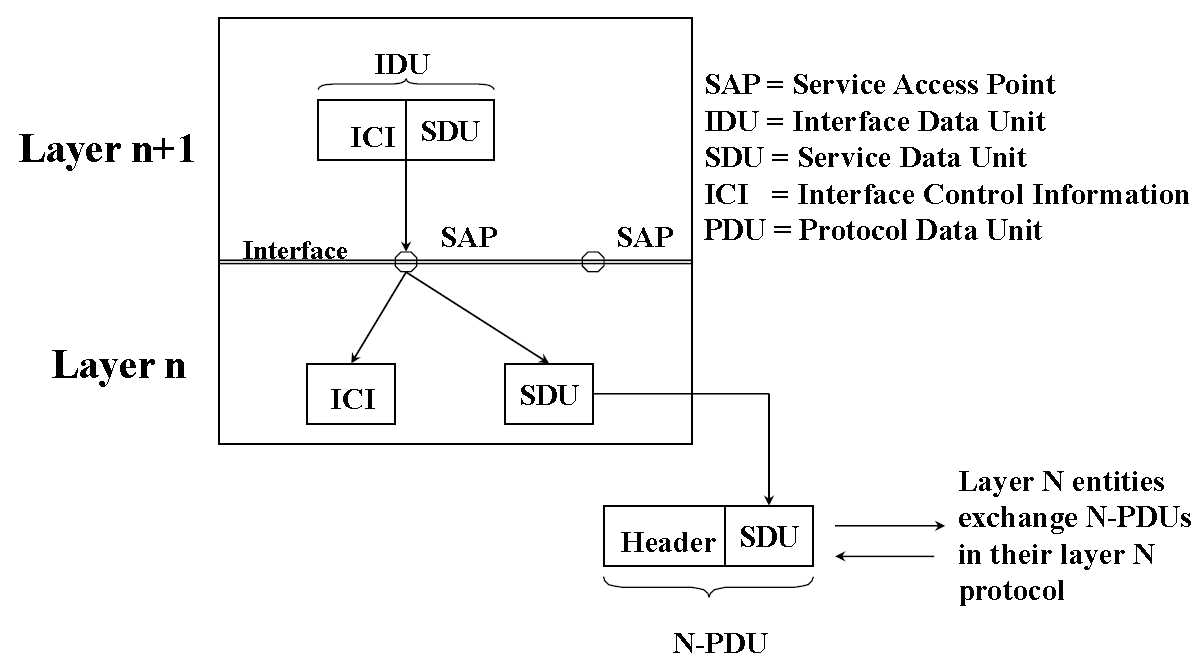
4. OSI encapsulation
1. As each data unit is passed down the layers, moreheaders are added
2. As each data unit is passed up the layers, headers are removed
*ICIs do not form part of message or header and do not propagate
6. TCP/IP(Transmission Control Protocol/Internet Protocol) Reference Model
1.The difference between TCP/IP and OSI
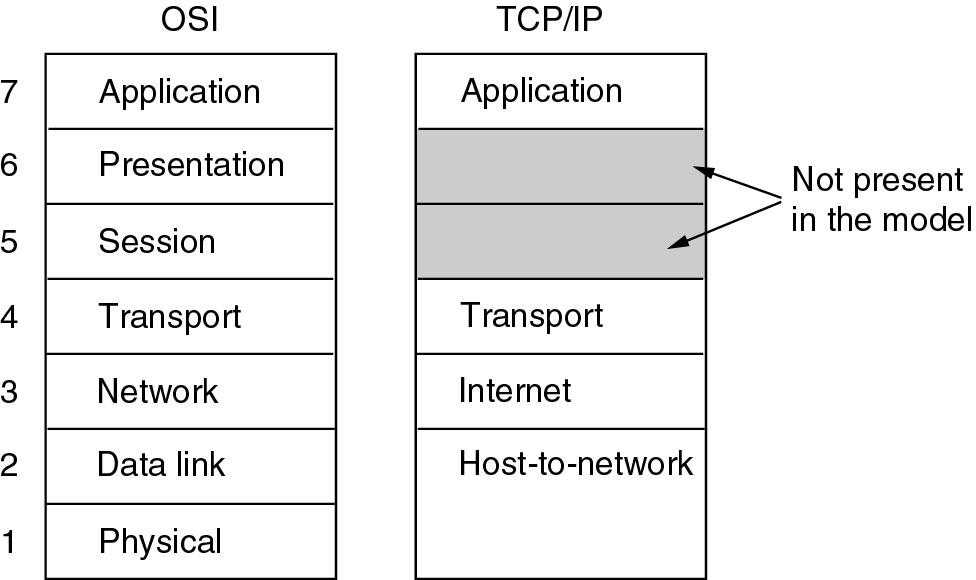
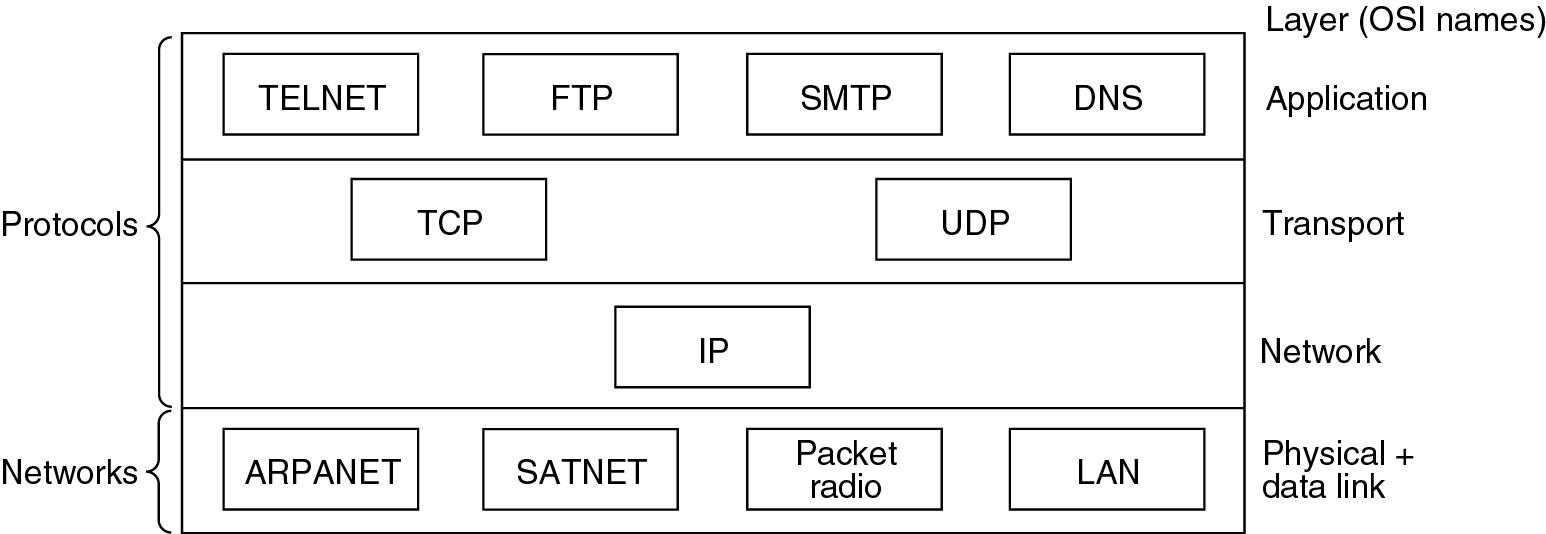
2. The different Layers
1. Host-to-network layer ( = OSI physical+ data link layers):
–The reference model does not really say much about this layer
–TCP/IP runs over almost any layer 1-2 protocols (egEthernet, Frame relay, ATM)
2. Internet layer (=OSI network layer):
–This is a packet-switching network based on a connectionless layer
–Packets travel independently to the destination (could arrive out of sequence)
–The official packet format and protocol is called IP
–Packet routing and congestion control are the major issues here
3. Transport layer
–Designed to allow peer entities on the source and destination hosts to exchange data
–Two end-to-end protocols are defined: TCP and UDP
–TCP (Transmission Control Protocol) is a reliable connection-oriented protocol:
»it works on byte stream
»it can fragment application data before sending it to the network layer
»it handles flow control
–UDP (User Datagram Protocol) is an unreliable connectionless protocol, used for client-server type request-reply queries and applications which require prompt delivery (egspeech and video)
标签:
原文地址:http://www.cnblogs.com/eli-ayase/p/5429221.html