1、建立httpd服务,要求:
(1) 提供两个基于名称的虚拟主机www1, www2;有单独的错误日志和访问日志;
(2) 通过www1的/server-status提供状态信息,且仅允许tom用户访问;
(3) www2不允许192.168.0.0/24网络中任意主机访问;
2、为上面的第2个虚拟主机提供https服务;
实验要求并不多,但是考虑到仅仅是为了测试,所以域名无需去互联网申请,也无需到互联网中的根CA注册证书,一切自给自足即可。为了达成实验要求,我准备了四台虚拟机,一台CentOS6.8、两台CentOS7.2和一台windowsXP,他们的主机名分别是CentOS68A、CentOS72A和CentOS72B。其中CentOS68A和CentOS72A分别作为httpd-2.2和httpd-2.4服务器,CentOS72B作为私有DNS服务器和私有CA,WindowsXP作为测试客户机。
对于三台服务器的部署如下:
1.三台虚拟机的IP地址规划如下:
[root@Centos68A ~]# ip a l dev eth0
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:d0:5b:1b brd ff:ff:ff:ff:ff:ff
inet 172.16.9.61/16 brd 172.16.255.255 scope global eth0
inet6 fe80::20c:29ff:fed0:5b1b/64 scope link
valid_lft forever preferred_lft forever
[root@Centos72A ~]# ip a l dev eno16777736
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:e0:46:e1 brd ff:ff:ff:ff:ff:ff
inet 172.16.9.71/16 brd 172.16.255.255 scope global eno16777736
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fee0:46e1/64 scope link
valid_lft forever preferred_lft forever
[root@Centos72B ~]# ip a l dev eno16777736
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:07:0e:a7 brd ff:ff:ff:ff:ff:ff
inet 172.16.9.72/16 brd 172.16.255.255 scope global eno16777736
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe07:ea7/64 scope link
valid_lft forever preferred_lft forever
注:WIndowsXP的IP地址为172.16.9.9/16,DNS指向172.16.9.72,因不需访问其他网段,故没有为其设置网关属性。
2.在三台服务器上安装相应的软件包
[root@Centos68A ~]# yum -y install httpd mod_ssl
[root@Centos72A ~]# yum -y install httpd mod_ssl
[root@Centos72B ~]# yum -y install bind
3.首先构建私有DNS服务和私有CA服务。
1)构建私有DNS服务,计划域名为"test.com",在DNS中要为DNS服务器,CA服务器以及两个虚拟服务器上的四个虚拟主机站点提供相对应的名称解析。主要步骤和配置文件片段如下:
DNS主配置文件:/etc/named.conf
options {
directory "/var/named";
listen-on port 53 { localhost; };
allow-recursion { 172.16.0.0/16; };
};
zone "." IN {
type hint;
file "named.ca";
};
zone "test.com" IN {
type master;
file "test.com.zone";
};
test.com域的数据库文件:/var/named/test.com.zone
$TTL 1D
@ IN SOA ns1.test.com. root.test.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS ns1
ns1 A 172.16.9.72
ca A 172.16.9.72
websrv1 A 172.16.9.61
www1 CNAME websrv1
www2 CNAME websrv1
websrv2 A 172.16.9.71
www3 CNAME websrv2
www4 CNAME websrv2
检查语法正确之后,启动服务待用。
[root@Centos72B named]# systemctl start named.service
[root@Centos72B named]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 10 172.16.9.72:53 *:*
LISTEN 0 10 127.0.0.1:53 *:*
LISTEN 0 128 *:22 *:*
LISTEN 0 128 127.0.0.1:631 *:*
LISTEN 0 128 127.0.0.1:953 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::22 :::*
LISTEN 0 128 ::1:631 :::*
LISTEN 0 128 ::1:953 :::*
LISTEN 0 100 ::1:25 :::*
2)构建私有根CA,事先编辑openssl的配置文件/etc/pki/tls/openssl.conf,设置了其中的req_distinguished_name段的某些关键参数的默认内容,如下所示:
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Beijing
localityName = Locality Name (eg, city)
localityName_default = Beijing
0.organizationName = Organization Name (eg, company)
0.organizationName_default = TestTech
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = Tech
commonName = Common Name (eg, your name or your server\‘s hostname)
commonName_default = ca.test.com
commonName_max = 64
emailAddress = Email Address
emailAddress_default = caadmin@test.com
emailAddress_max = 64
接下来创建CA的私钥文件、自签证书以及其他相关文件:
[root@Centos72B named]# cd /etc/pki/CA
[root@Centos72B CA]# pwd
/etc/pki/CA
[root@Centos72B CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
.............................................................+++
............................................................................................+++
e is 65537 (0x10001)
[root@Centos72B CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [Beijing]:
Locality Name (eg, city) [Beijing]:
Organization Name (eg, company) [TestTech]:
Organizational Unit Name (eg, section) [Tech]:
Common Name (eg, your name or your server‘s hostname) [ca.test.com]:
Email Address [caadmin@test.com]:
[root@Centos72B CA]# touch index.txt
[root@Centos72B CA]# echo 01 > serial
至此,一个私有CA建设完毕。CentOS72B上的工作也暂时告一段落。
4.在CentOS68A和CentOS72A上分别构建需要的虚拟主机
1)CentOS68A上的配置:
I.两个虚拟主机分别被命名为www1.test.com和www2.test.com;
II.由于要使用的是基于FQDN的虚拟主机,而CentOS6系列上以rpm包的方式来安装的httpd的版本是2.2的,所以为了能够使用这样的虚拟主机,需要将主配置文件/etc/httpd/conf/httpd.conf中的NameVirtualHost指令进行配置,具体操作为:复制NameVirtualHost所在行,取消注释,并将后面的"*"改成监听的IP地址。即:
NameVirtualHost 172.16.9.61:80 注意:在httpd2.2版本中,配置FQDN的虚拟主机,这行指令必不可少。
III.两个虚拟主机的配置文本被放置在/etc/httpd/conf.d目录中,分别命名为vhost-www1.conf和vhost-www2.conf,其中vhost-www2.conf是将ssl.conf文件重命名而来的;
vhost-www1.conf的主要配置指令及其值
<VirtualHost 172.16.9.61:80>
ServerName www1.test.com
DocumentRoot /myweb/test.com/www1
ErrorLog logs/www1_error.log
CustomLog logs/www1_access.log combined
<Location /server-status>
SetHandler server-status
AuthType basic
AuthName "The status of Web site, Only allow tom."
AuthUserFile "/etc/httpd/conf.d/.www1_htpasswd"
Require User tom
</Location>
</VirtualHost>
创建认证用户文件:
[root@Centos68A conf.d]# htpasswd -c -m .www1_htpasswd tom
New password:
Re-type new password:
vhost-www2.conf的主要配置指令及其值
LoadModule ssl_module modules/mod_ssl.so
Listen 443
SSLPassPhraseDialog builtin
SSLSessionCache shmcb:/var/cache/mod_ssl/scache(512000)
SSLSessionCacheTimeout 300
SSLMutex default
SSLRandomSeed startup file:/dev/urandom 256
SSLRandomSeed connect builtin
SSLCryptoDevice builtin
<VirtualHost 172.16.9.61:443>
DocumentRoot "/myweb/test.com/www2"
ServerName www2.test.com:443
<Directory "/myweb/test.com/www2">
Options None
AllowOverride None
Order allow,deny
Deny from 192.168.0.0/24
Allow from all
</Directory>
ErrorLog logs/www2_ssl_error_log
TransferLog logs/www2_ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite DEFAULT:!EXP:!SSLv2:!DES:!IDEA:!SEED:+3DES
SSLCertificateFile /etc/httpd/secure/httpvh_www2.crt
SSLCertificateKeyFile /etc/httpd/secure/httpvh_www2.key
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown downgrade-1.0 force-response-1.0
CustomLog logs/www2_ssl_request_log "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
IV.两个虚拟主机的文档根目录是/myweb/test.com/目录中分别命名为www1和www2的目录,并为两个虚拟主机提供可访问的测试页面。
[root@Centos68A conf.d]# mkdir -pv /myweb/test.com/www{1,2}
mkdir: created directory `/myweb‘
mkdir: created directory `/myweb/test.com‘
mkdir: created directory `/myweb/test.com/www1‘
mkdir: created directory `/myweb/test.com/www2‘
[root@Centos68A conf.d]# echo "<h1>www1 Home Page</h1>" > /myweb/test.com/www1/index.html
[root@Centos68A conf.d]# echo "<h1>www2 Test Page</h1>" > /myweb/test.com/www2/index.html
V.为www2创建httpd私有和证书请求文件:
[root@Centos68A httpd]# mkdir secure
[root@Centos68A httpd]# cd secure/
[root@Centos68A secure]# (umask 077;openssl genrsa -out httpvh_www2.key 2048)
Generating RSA private key, 2048 bit long modulus
..............+++
.....................................................................................................................+++
e is 65537 (0x10001)
[root@Centos68A secure]# openssl req -new -key httpvh_www2.key -out httpvh_www2.csr -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [Beijing]:
Locality Name (eg, city) [Beijing]:
Organization Name (eg, company) [TestTech]:
Organizational Unit Name (eg, section) [Tech]:
Common Name (eg, your name or your server‘s hostname) [www2.test.com]:
Email Address [admin@test.com]:
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@Centos68A secure]#
将已经生成的证书请求传给私有根CA,让其签署并生成公钥证书:
[root@Centos68A secure]# scp httpvh_www2.csr 172.16.9.72:/tmp
httpvh_www2.csr 100% 1054 1.0KB/s 00:00
[root@Centos68A secure]#
[root@Centos72B tmp]# openssl ca -in httpvh_www2.csr -out httpvh_www2.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jul 9 07:54:54 2016 GMT
Not After : Jul 9 07:54:54 2017 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = TestTech
organizationalUnitName = Tech
commonName = www2.test.com
emailAddress = admin@test.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
C8:FF:5F:B3:D1:9E:F7:C5:45:15:CC:AD:2A:89:86:FD:DC:A7:B2:B1
X509v3 Authority Key Identifier:
keyid:0E:3D:4B:D7:08:F4:B5:4D:EF:59:C9:03:8F:20:C6:0F:B6:1B:67:1B
Certificate is to be certified until Jul 9 07:54:54 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@Centos72B tmp]# scp httpvh_www2.crt 172.16.9.61:/etc/httpd/secure
httpvh_www2.crt 100% 4613 4.5KB/s 00:00
使用客户机进行测试即可:
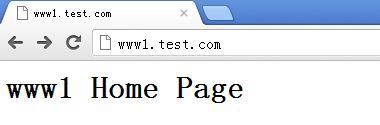
在客户机的浏览器的地址栏中输入:http://www1.test.com来测试第一个虚拟主机
在客户机的浏览器的地址栏中输入:https://www2.test.com来测试第二个虚拟主机
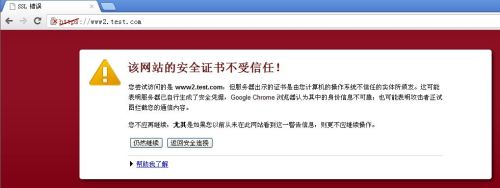
证书不受信任
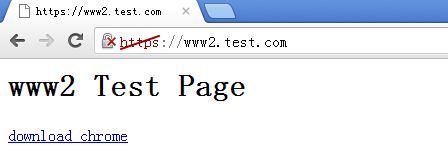
但如果选择“仍然继续”的话还是可以访问的。为了方便使用chrome,在网站页面上加了个下载超链接
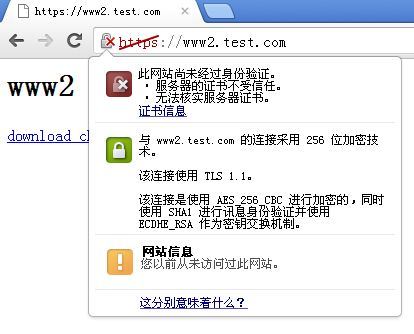
查看到具体的信息就是:无法核实CA的证书是否合法,因此由这样的CA颁发的证书也不受信任
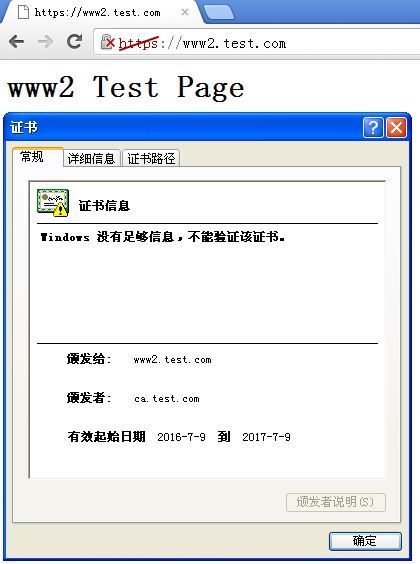
结果确实是我们自己给自己颁发的那个证书了,只是能在实验场合用用而已,无法用于互联网的。
2)CentOS72A上的配置:
I.两个虚拟主机分别被命名为www3.test.com和www4.test.com;
II.两个虚拟主机的配置文本被放置在/etc/httpd/conf.d目录中,分别命名为vhost-www3.conf和vhost-www4.conf,其中vhost-www4.conf是将ssl.conf文件重命名而来的;
vhost-www3.conf的主要配置指令及其值
<VirtualHost 172.16.9.71:80>
ServerName www3.test.com
DocumentRoot /myweb/test.com/www3
ErrorLog logs/www3_error.log
CustomLog logs/www3_access.log combined
<Directory "/myweb/test.com/www3">
Options None
AllowOverride None
Require all granted
</Directory>
<Location /server-status>
SetHandler server-status
AuthType basic
AuthName "The status of Web site, Only allow tom."
AuthUserFile "/etc/httpd/conf.d/.www3_htpasswd"
Require user tom
</Location>
</VirtualHost>
创建认证用户文件:
[root@Centos72A conf.d]# htpasswd -c -m .www3_htpasswd tom
New password:
Re-type new password:
vhost-www4.conf的主要配置指令及其值
LoadModule ssl_module modules/mod_ssl.so
Listen 443 https
SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog
SSLSessionCache shmcb:/run/httpd/sslcache(512000)
SSLSessionCacheTimeout 300
SSLRandomSeed startup file:/dev/urandom 256
SSLRandomSeed connect builtin
SSLCryptoDevice builtin
<VirtualHost 172.16.9.71:443>
DocumentRoot "/myweb/test.com/www4"
ServerName www4.test.com:443
<Directory "/myweb/test.com/www4">
Options None
AllowOverride None
<RequireAny>
Require not ip 192.168.0.0/24
Require all granted
</RequireAny>
</Directory>
ErrorLog logs/www4_ssl_error_log
TransferLog logs/www4_ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5:!SEED:!IDEA
SSLCertificateFile /etc/httpd/secure/httpvh_www4.crt
SSLCertificateKeyFile /etc/httpd/secure/httpvh_www4.key
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
BrowserMatch "MSIE [2-5]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
III.两个虚拟主机的文档根目录是/myweb/test.com/目录中分别命名为www3和www4的目录,并为两个虚拟主机提供可访问的测试页面。
[root@Centos72A conf.d]# mkdir -pv /myweb/test.com/www{3,4}
mkdir: created directory `/myweb‘
mkdir: created directory `/myweb/test.com‘
mkdir: created directory `/myweb/test.com/www3‘
mkdir: created directory `/myweb/test.com/www4‘
[root@Centos72A conf.d]# echo "<h1>www3 Home Page</h1>" > /myweb/test.com/www3/index.html
[root@Centos72A conf.d]# echo "<h1>www4 Test Page</h1>" > /myweb/test.com/www4/index.html
IV.为www4创建httpd私有和证书请求文件:
[root@Centos72A httpd]# mkdir secure
[root@Centos72A httpd]# cd secure/
[root@Centos72A secure]# (umask 077;openssl genrsa -out http_www4.key 2048)
Generating RSA private key, 2048 bit long modulus
.................................................+++
...........+++
e is 65537 (0x10001)
[root@Centos72A secure]# openssl req -new -key http_www4.key -out http_www4.csr -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [Beijing]:
Locality Name (eg, city) [Beijing]:
Organization Name (eg, company) [TestTech]:
Organizational Unit Name (eg, section) [Tech]:
Common Name (eg, your name or your server‘s hostname) [www4.test.com]:
Email Address [admin@test.com]:
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@Centos72A secure]#
将已经生成的证书请求传给私有根CA,让其签署并生成公钥证书:
[root@Centos72A secure]# scp httpvh_www4.csr 172.16.9.72:/tmp
httpvh_www4.csr 100% 1054 1.0KB/s 00:00
[root@Centos72A secure]#
[root@Centos72B tmp]# openssl ca -in httpvh_www4.csr -out httpvh_www4.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 2 (0x2)
Validity
Not Before: Jul 9 11:37:03 2016 GMT
Not After : Jul 9 11:37:03 2017 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = TestTech
organizationalUnitName = Tech
commonName = www4.test.com
emailAddress = admin@test.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6E:34:E7:5D:57:A2:05:D6:7C:24:58:F6:77:F2:3C:99:B3:3D:65:F0
X509v3 Authority Key Identifier:
keyid:0E:3D:4B:D7:08:F4:B5:4D:EF:59:C9:03:8F:20:C6:0F:B6:1B:67:1B
Certificate is to be certified until Jul 9 07:54:54 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@Centos72B tmp]# scp httpvh_www4.crt 172.16.9.71:/etc/httpd/secure
httpvh_www4.crt 100% 4613 4.5KB/s 00:00
使用客户机进行测试即可:
在客户机的浏览器的地址栏中输入:http://www3.test.com来测试第一个虚拟主机
在客户机的浏览器的地址栏中输入:https://www4.test.com来测试第二个虚拟主机
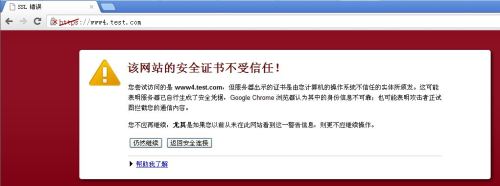
同样是不受信任的证书提示
不管提示,仍然继续,访问是没有问题的。
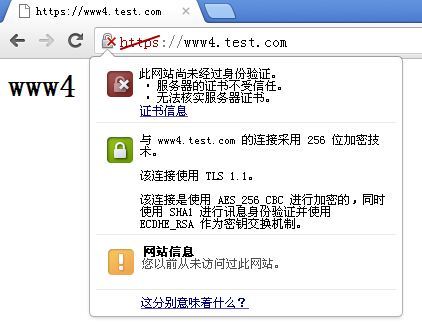
提示证书服务器CA的证书无法核实,也就认为CA颁发的证书不受信任
这张证书也确实是我们自己的私有CA为www4颁发的,这毫无疑问。
本文出自 “运维者的家” 博客,请务必保留此出处http://zhaotianyu.blog.51cto.com/132212/1826484
原文地址:http://zhaotianyu.blog.51cto.com/132212/1826484