标签:
1,现象
今天需要远程连接ossim的mysql数据库读取些东西,于是登录ossim的终端,发现这个mysql客户端无法直接登录,使用自己安装时候那些口令都不行
alienvault:~# mysql -uroot -p
Enter password:
ERROR 1045 (28000): Access denied for user ‘root‘@‘localhost‘ (using password: YES)
alienvault:~# mysql -uroot -p
Enter password:
ERROR 1045 (28000): Access denied for user ‘root‘@‘localhost‘ (using password: NO)
? ?
2,后来查资料说ossim-db命令可以直接登录,果然!!
alienvault:~# ossim-db
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 40993
Server version: 5.6.23-72.1 Percona Server (GPL), Release 72.1, Revision 0503478
? ?
Copyright (c) 2009-2015 Percona LLC and/or its affiliates
Copyright (c) 2000, 2015, Oracle and/or its affiliates. All rights reserved.
? ?
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
? ?
Type ‘help;‘ or ‘\h‘ for help. Type ‘\c‘ to clear the current input statement.
? ?
mysql>
3,修改密码
mysql> update user set password=password("123456") where user="root";
ERROR 1146 (42S02): Table ‘alienvault.user‘ doesn‘t exist
mysql> show tables
-> ;
+--------------------------------------+
| Tables_in_alienvault |
+--------------------------------------+
| acl_assets |
| acl_entities |
| acl_entities_assets |
| acl_entities_stats |
| acl_entities_users |
| acl_login_sensors |
| acl_perm |
| acl_sensors |
| acl_templates |
| acl_templates_perms |
| action |
| action_email |
| action_exec |
| action_risk |
| action_type |
| alarm |
| alarm_categories |
| alarm_ctxs |
| alarm_groups |
| alarm_hosts |
| alarm_kingdoms |
| alarm_nets |
| alarm_taxonomy |
| asset_filter_types |
| asset_filters |
| backlog |
| backlog_event |
| bp_asset_member |
| bp_member_status |
| category |
| category_changes |
| classification |
| component_tags |
| config |
| control_panel |
| corr_engine_contexts |
| credential_type |
| credentials |
| custom_report_profiles |
| custom_report_scheduler |
| custom_report_types |
| dashboard_custom_type |
| dashboard_tab_config |
| dashboard_tab_options |
| dashboard_widget_config |
| databases |
| device_types |
| event |
| extra_data |
| host |
| host_agentless |
| host_agentless_entries |
| host_group |
| host_group_history |
| host_group_reference |
| host_group_scan |
| host_ip |
| host_mac_vendors |
| host_net_reference |
| host_plugin_sid |
| host_properties |
| host_property_reference |
| host_qualification |
| host_scan |
| host_sensor_reference |
| host_services |
| host_software |
| host_source_reference |
| host_types |
| host_vulnerability |
| idm_data |
| incident |
| incident_alarm |
| incident_anomaly |
| incident_custom |
| incident_custom_types |
| incident_event |
| incident_file |
| incident_metric |
| incident_subscrip |
| incident_tag |
| incident_tag_descr |
| incident_tag_descr_seq |
| incident_ticket |
| incident_ticket_seq |
| incident_type |
| incident_vulns |
| incident_vulns_seq |
| location_sensor_reference |
| locations |
| log_action |
| log_config |
| map |
| map_element |
| map_element_seq |
| map_seq |
| net |
| net_cidrs |
| net_group |
| net_group_reference |
| net_group_scan |
| net_qualification |
| net_scan |
| net_sensor_reference |
| net_vulnerability |
| notes |
| pass_history |
| plugin |
| plugin_group |
| plugin_group_descr |
| plugin_reference |
| plugin_scheduler |
| plugin_scheduler_host_reference |
| plugin_scheduler_hostgroup_reference |
| plugin_scheduler_net_reference |
| plugin_scheduler_netgroup_reference |
| plugin_scheduler_sensor_reference |
| plugin_scheduler_seq |
| plugin_sid |
| plugin_sid_changes |
| plugin_sid_orig |
| policy |
| policy_actions |
| policy_extra_data_reference |
| policy_forward_reference |
| policy_group |
| policy_host_group_reference |
| policy_host_reference |
| policy_idm_reference |
| policy_net_group_reference |
| policy_net_reference |
| policy_plugin_group_reference |
| policy_port_reference |
| policy_reputation_reference |
| policy_risk_reference |
| policy_role_reference |
| policy_sensor_reference |
| policy_target_reference |
| policy_taxonomy_reference |
| policy_time_reference |
| port |
| port_group |
| port_group_reference |
| product_type |
| repository |
| repository_attachments |
| repository_relationships |
| reputation_activities |
| restoredb_log |
| risk_indicators |
| risk_maps |
| rrd_anomalies |
| rrd_anomalies_global |
| rrd_config |
| sem_stats_events |
| sensor |
| sensor_interfaces |
| sensor_properties |
| sensor_stats |
| server |
| server_forward_role |
| server_hierarchy |
| server_role |
| sessions |
| signature |
| signature_group |
| signature_group_reference |
| software_cpe |
| software_cpe_links |
| subcategory |
| subcategory_changes |
| system |
| tag |
| task_inventory |
| user_component_filter |
| user_config |
| user_ctx_perm |
| user_host_filter |
| user_host_perm |
| user_net_perm |
| user_sensor_perm |
| users |
| vuln_hosts |
| vuln_job_assets |
| vuln_job_schedule |
| vuln_jobs |
| vuln_nessus_category |
| vuln_nessus_category_feed |
| vuln_nessus_family |
| vuln_nessus_family_feed |
| vuln_nessus_latest_reports |
| vuln_nessus_latest_results |
| vuln_nessus_plugins |
| vuln_nessus_plugins_feed |
| vuln_nessus_preferences |
| vuln_nessus_preferences_defaults |
| vuln_nessus_report_stats |
| vuln_nessus_reports |
| vuln_nessus_results |
| vuln_nessus_servers |
| vuln_nessus_settings |
| vuln_nessus_settings_category |
| vuln_nessus_settings_family |
| vuln_nessus_settings_plugins |
| vuln_nessus_settings_preferences |
| vuln_settings |
| web_interfaces |
| webservice |
| webservice_default |
| webservice_operation |
| wireless_aps |
| wireless_clients |
| wireless_locations |
| wireless_networks |
| wireless_sensors |
+--------------------------------------+
215 rows in set (0.00 sec)
换种方法改密码
mysql> SET PASSWORD = PASSWORD(‘123456‘);
Query OK, 0 rows affected (0.03 sec)
? ?
mysql>
? ?
4,问题来了
这下客户端可以连进来了,但是发现页面无法显示了,这下麻烦了。怎么办?
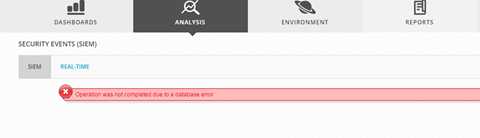
分析前面命令ossim-db ,希望不是二进制的,结果运气不错,果然是个脚本
alienvault:~# whereis ossim-db
ossim-db: /usr/bin/ossim-db
alienvault:~# more /usr/bin/ossim-db
#!/bin/bash
? ?
if test -z "$1"; then
# DB="ossim"
DB="alienvault"
else
DB="$1"
fi
? ?
if [ ! -f "/etc/ossim/ossim_setup.conf" ];then
>&2 echo "ossim_setup.conf not found"
exit 0
fi
? ?
HOST=`grep ^db_ip= /etc/ossim/ossim_setup.conf | cut -f 2 -d "=" | sed ‘/^$/d‘`
USER=`grep ^user= /etc/ossim/ossim_setup.conf | cut -f 2 -d "=" | sed ‘/^$/d‘`
PASS=`grep ^pass= /etc/ossim/ossim_setup.conf | cut -f 2 -d "=" | sed ‘/^$/d‘`
? ?
if test -z "$HOST"; then
HOST=localhost
fi
? ?
sshpass -p $PASS mysql --default-character-set=utf8 -A -u $USER -h $HOST $DB -p -e "exit" &>/dev/null
? ?
if [ $? -ne 0 ]; then
>&2 echo "Access denied. Trying old settings..."
? ?
if [ ! -f /etc/ossim/ossim_setup.conf_last ]; then
>&2 echo "ossim_setup.conf_last not found"
exit 0
fi
? ?
HOST=`grep ^db_ip= /etc/ossim/ossim_setup.conf_last | cut -f 2 -d "=" | sed ‘/^$/d‘`
USER=`grep ^user= /etc/ossim/ossim_setup.conf_last | cut -f 2 -d "=" | sed ‘/^$/d‘`
PASS=`grep ^pass= /etc/ossim/ossim_setup.conf_last | cut -f 2 -d "=" | sed ‘/^$/d‘`
fi
? ?
sshpass -p $PASS mysql --default-character-set=utf8 -A -u $USER -h $HOST $DB -p
alienvault:~#
? ?
5,解决
看来有希望,取出PASS参数就可以了,好,看看
alienvault:~# grep ^pass= /etc/ossim/ossim_setup.conf | cut -f 2 -d "=" | sed ‘/^$/d‘
XDdTX6oRdV
alienvault:~#
? ?
再给改回去,反正知道密码就可以了
alienvault:~# mysql -uroot -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 43029
Server version: 5.6.23-72.1 Percona Server (GPL), Release 72.1, Revision 0503478
? ?
Copyright (c) 2009-2015 Percona LLC and/or its affiliates
Copyright (c) 2000, 2015, Oracle and/or its affiliates. All rights reserved.
? ?
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
? ?
Type ‘help;‘ or ‘\h‘ for help. Type ‘\c‘ to clear the current input statement.
? ?
mysql> SET PASSWORD = PASSWORD(‘XDdTX6oRdV‘);
Query OK, 0 rows affected (0.00 sec)
? ?
mysql> exit
Bye
alienvault:~#
OK,客户端终于可以连入了。
标签:
原文地址:http://www.cnblogs.com/iamqiu/p/5726815.html