标签:
项目地址:SQLiScanner
叕一款基于SQLMAP和Charles的被动SQL 注入漏洞扫描工具
从内部安全平台 分离出来的一个模块, 支持 Har 文件的扫描(搭配 Charles 使用: Tools=>Auto Save)
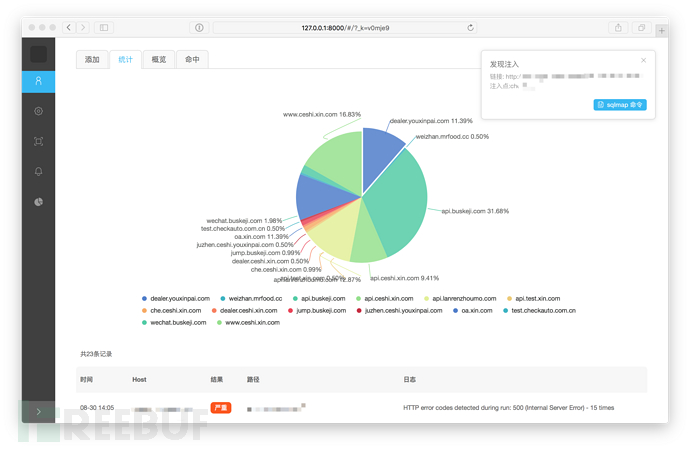
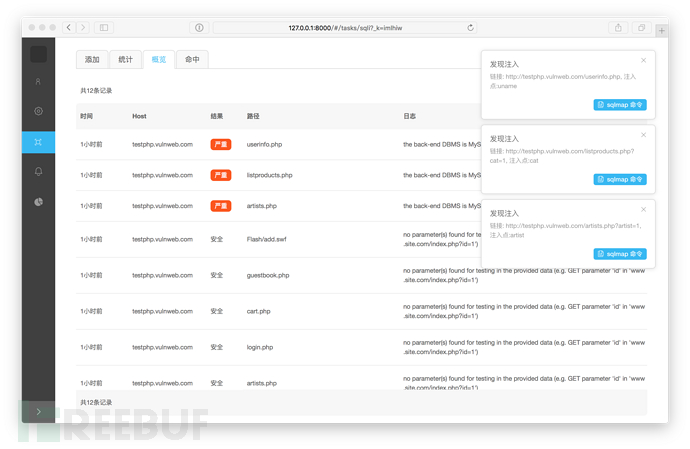
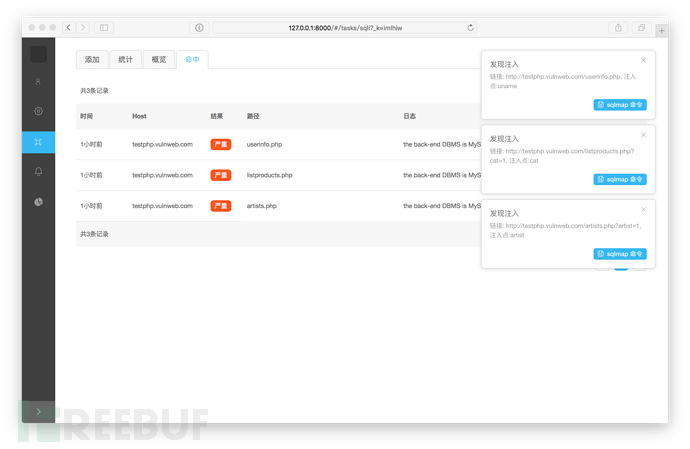
克隆项目到本地
git clone https://github.com/0xbug/SQLiScanner.git --depth 1
配置 sqlmap:
git clone https://github.com/sqlmapproject/sqlmap.git --depth 1
SQLiScanner 支持 Python version 3.x on Linux and osx.
安装依赖
cd SQLiScanner/
virtualenv --python=/usr/local/bin/python3.5 venv
source venv/bin/activate
pip install -r requirements.txt
创建数据库(需要配置数据库)
python manage.py makemigrations scanner
python manage.py migrate
创建 superuser
python manage.py createsuperuser
数据库设置
SQLiScanner/settings.py:85
DATABASES = {
‘default‘: {
‘ENGINE‘: ‘django.db.backends.postgresql‘,
‘NAME‘: ‘‘,
‘USER‘: ‘‘,
‘PASSWORD‘: ‘‘,
‘HOST‘: ‘127.0.0.1‘,
‘PORT‘: ‘5432‘,
}
}
邮件通知配置
SQLiScanner/settings.py:152
# Email
EMAIL_BACKEND = ‘django.core.mail.backends.smtp.EmailBackend‘
EMAIL_USE_TLS = False
EMAIL_HOST = ‘‘
EMAIL_PORT = 25
EMAIL_HOST_USER = ‘‘
EMAIL_HOST_PASSWORD = ‘‘
DEFAULT_FROM_EMAIL = ‘‘
scanner/tasks.py:13
class SqlScanTask(object):
def __init__(self, sqli_obj):
self.api_url = "http://127.0.0.1:8775"
self.mail_from = ""
self.mail_to = [""]
redis-server
python sqlmapapi.py -s -p 8775
python manage.py celery worker --loglevel=info
python manage.py runserver
*本文投稿作者:Blur,转载须注明来自FreeBuf.COM
SQLiScanner:一款基于SQLMAP和Charles的被动SQL 注入漏洞扫描工具
标签:
原文地址:http://www.cnblogs.com/adislj777/p/5886146.html