标签:without linux终端 statistic 使用 output grep 程序 path 端口号
今天在使用linux的时候,要查看端口号,但是不知道要使用哪一个命令所以就学习了一下,原来是使用netstat,接下来给大家一起来学习。
Netstat 命令用于显示各种网络相关信息,如网络连接,路由表,接口状态 (Interface Statistics),masquerade 连接,多播成员 (Multicast Memberships) 等等。
Netstat 是一款命令行工具,可用于列出系统上所有的网络套接字连接情况,包括 tcp, udp 以及 unix 套接字,另外它还能列出处于监听状态(即等待接入请求)的套接字。
如果你想确认系统上的 Web 服务有没有起来,你可以查看80端口有没有打开。以上功能使 netstat 成为网管和系统管理员的必备利器。
在linux终端中输入netstat:
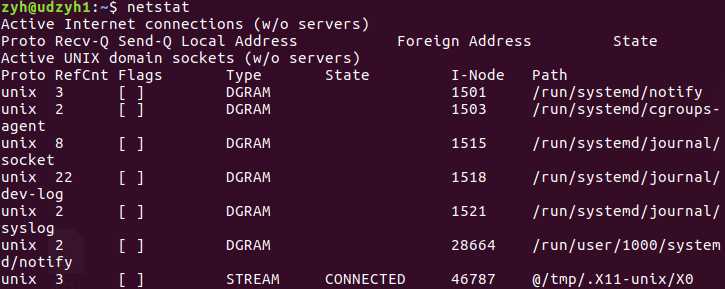
分析: 从上面可以看出,可以分为两个部分:
一个是Active Internet connections,称为有源TCP连接,其中"Recv-Q"和"Send-Q"指%0A的是接收队列和发送队列。这些数字一般都应该是0。如果不是则表示软件包正在队列中堆积。这种情况只能在非常少的情况见到。
另一个是Active UNIX domain sockets,称为有源Unix域套接口(和网络套接字一样,但是只能用于本机通信,性能可以提高一倍)。
Proto显示连接使用的协议,RefCnt表示连接到本套接口上的进程号,Types显示套接口的类型,State显示套接口当前的状态,Path表示连接到套接口的其它进程使用的路径名。
-a (all)显示所有选项,默认不显示LISTEN相关 -t (tcp)仅显示tcp相关选项 -u (udp)仅显示udp相关选项 -n 拒绝显示别名,能显示数字的全部转化成数字。 -l 仅列出有在 Listen (监听) 的服務状态 -p 查看进程信息 -r 显示路由信息,路由表 -e 显示扩展信息,例如uid等 -s 按各个协议进行统计 -c 每隔一个固定时间,执行该netstat命令。 提示:LISTEN和LISTENING的状态只有用-a或者-l才能看到
1) 列出所有端口 netstat -a
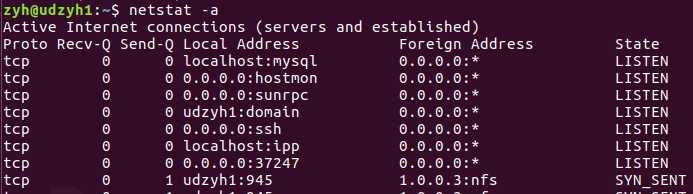
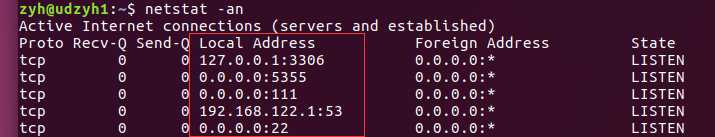
当我们加上-n的时候就禁止端口使用别名了,比如上面的mysql它的端口号是3306
2) 列出所有 tcp 端口 netstat -at

Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 localhost:mysql 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:hostmon 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:sunrpc 0.0.0.0:* LISTEN tcp 0 0 udzyh1:domain 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN tcp 0 0 localhost:ipp 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:37247 0.0.0.0:* LISTEN tcp 0 1 udzyh1:945 1.0.0.3:nfs SYN_SENT tcp 0 1 udzyh1:945 1.0.0.3:nfs SYN_SENT tcp6 0 0 [::]:hostmon [::]:* LISTEN tcp6 0 0 [::]:sunrpc [::]:* LISTEN tcp6 0 0 [::]:ssh [::]:* LISTEN tcp6 0 0 ip6-localhost:ipp [::]:* LISTEN tcp6 0 0 [::]:33729 [::]:* LISTEN
3)列出所有 udp 端口 netstat -au

1 Active Internet connections (servers and established) 2 Proto Recv-Q Send-Q Local Address Foreign Address State 3 udp 0 0 0.0.0.0:ipp 0.0.0.0:* 4 udp 0 0 0.0.0.0:950 0.0.0.0:* 5 udp 0 0 udzyh1:domain 0.0.0.0:* 6 udp 0 0 localhost:domain 0.0.0.0:* 7 udp 0 0 0.0.0.0:bootps 0.0.0.0:* 8 udp 0 0 0.0.0.0:bootpc 0.0.0.0:* 9 udp 0 0 0.0.0.0:60485 0.0.0.0:* 10 udp 0 0 0.0.0.0:sunrpc 0.0.0.0:* 11 udp 0 0 0.0.0.0:mdns 0.0.0.0:* 12 udp 0 0 0.0.0.0:hostmon 0.0.0.0:* 13 udp6 0 0 [::]:950 [::]:* 14 udp6 0 0 [::]:sunrpc [::]:* 15 udp6 0 0 [::]:41132 [::]:* 16 udp6 0 0 [::]:mdns [::]:* 17 udp6 0 0 [::]:hostmon [::]:*
1)只显示监听端口 netstat -l
2)只列出所有监听 tcp 端口 netstat -lt
3)只列出所有监听 udp 端口 netstat -lu
4)只列出所有监听 UNIX 端口 netstat -lx
显示所有端口的统计信息 netstat -s
打印出网络统计数据,包括某个协议下的收发包数量。

Ip: Forwarding: 1 44825 total packets received 1 with invalid addresses 0 forwarded 0 incoming packets discarded 44016 incoming packets delivered 49606 requests sent out 80 outgoing packets dropped 110382753 dropped because of missing route Icmp: 13821 ICMP messages received 4791 input ICMP message failed ICMP input histogram: destination unreachable: 13798 echo requests: 7 echo replies: 16 13868 ICMP messages sent 0 ICMP messages failed ICMP output histogram: destination unreachable: 13845 echo requests: 16 echo replies: 7 IcmpMsg: InType0: 16 InType3: 13798 InType8: 7 OutType0: 7 OutType3: 13845 OutType8: 16 Tcp: 6871 active connection openings 6 passive connection openings 6833 failed connection attempts 2 connection resets received 0 connections established 20654 segments received 26166 segments sent out 6838 segments retransmitted 0 bad segments received 2 resets sent Udp: 5822 packets received 213 packets to unknown port received 0 packet receive errors 2529 packets sent 0 receive buffer errors 0 send buffer errors IgnoredMulti: 3508 UdpLite: TcpExt: 1938 ICMP packets dropped because they were out-of-window 107 ICMP packets dropped because socket was locked 19 TCP sockets finished time wait in fast timer 196 delayed acks sent 1 delayed acks further delayed because of locked socket Quick ack mode was activated 4 times 12 packets directly queued to recvmsg prequeue TCPDirectCopyFromPrequeue: 2 13426 packet headers predicted 247 acknowledgments not containing data payload received 6758 predicted acknowledgments 1 congestion windows recovered without slow start after partial ack TCPTimeouts: 6736 3 connections aborted due to timeout TCPRetransFail: 16 TCPRcvCoalesce: 2012 TCPSpuriousRtxHostQueues: 13337 TCPAutoCorking: 3 TCPSynRetrans: 6750 TCPOrigDataSent: 6868 TCPKeepAlive: 189 IpExt: InNoRoutes: 498 InMcastPkts: 4985 OutMcastPkts: 1483 InBcastPkts: 3508 OutBcastPkts: 10 InOctets: 25359234 OutOctets: 3397412 InMcastOctets: 415880 OutMcastOctets: 116579 InBcastOctets: 303775 OutBcastOctets: 460 InNoECTPkts: 57259 InECT0Pkts: 65
显示 TCP 或 UDP 端口的统计信息 netstat -st 或 -su
使用netstat -st

IcmpMsg: InType0: 16 InType3: 13828 InType8: 7 OutType0: 7 OutType3: 13875 OutType8: 16 Tcp: 6886 active connection openings 6 passive connection openings 6848 failed connection attempts 2 connection resets received 0 connections established 20654 segments received 26181 segments sent out 6853 segments retransmitted 0 bad segments received 2 resets sent UdpLite: TcpExt: 1942 ICMP packets dropped because they were out-of-window 107 ICMP packets dropped because socket was locked 19 TCP sockets finished time wait in fast timer 196 delayed acks sent 1 delayed acks further delayed because of locked socket Quick ack mode was activated 4 times 12 packets directly queued to recvmsg prequeue TCPDirectCopyFromPrequeue: 2 13426 packet headers predicted 247 acknowledgments not containing data payload received 6758 predicted acknowledgments 1 congestion windows recovered without slow start after partial ack TCPTimeouts: 6751 3 connections aborted due to timeout TCPRetransFail: 16 TCPRcvCoalesce: 2012 TCPSpuriousRtxHostQueues: 13367 TCPAutoCorking: 3 TCPSynRetrans: 6765 TCPOrigDataSent: 6868 TCPKeepAlive: 189 IpExt: InNoRoutes: 498 InMcastPkts: 4986 OutMcastPkts: 1483 InBcastPkts: 3508 OutBcastPkts: 10 InOctets: 25361943 OutOctets: 3401852 InMcastOctets: 415949 OutMcastOctets: 116579 InBcastOctets: 303775 OutBcastOctets: 460 InNoECTPkts: 57290 InECT0Pkts: 65
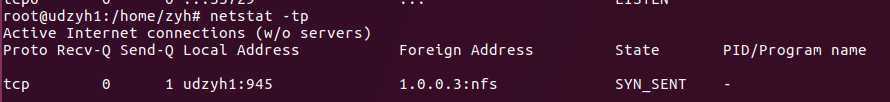
netstat -p 可以与其它开关一起使用,就可以添加 “PID/进程名称” 到 netstat 输出中,这样 debugging 的时候可以很方便的发现特定端口运行的程序。
注意:使用 -p 选项时,netstat 必须运行在 root 权限之下,不然它就不能得到运行在 root 权限下的进程名,而很多服务包括 http 和 ftp 都运行在 root 权限之下。
相比进程名和进程号而言,查看进程的拥有者会更有用。使用 -ep 选项可以同时查看进程名和用户名。
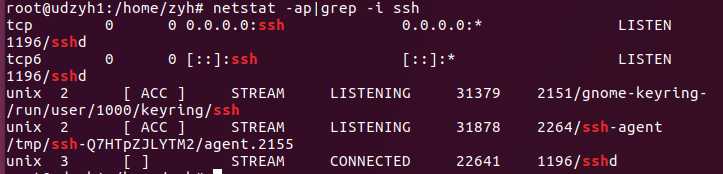
netstat -ap|grep -i ssh
并不是所有的进程都能找到,没有权限的会不显示,使用 root 权限查看所有的信息。
netstat -i
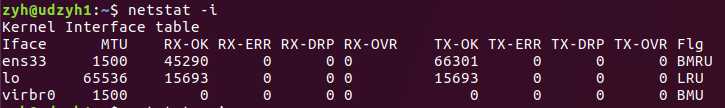
显示详细信息,像是 ifconfig 使用 netstat -ie。输出信息与 ifconfig 输出的信息一样。
觉得不错的大佬点个“推荐”哦!
标签:without linux终端 statistic 使用 output grep 程序 path 端口号
原文地址:http://www.cnblogs.com/zhangyinhua/p/7488771.html