标签:strive struggle endeavo attempt
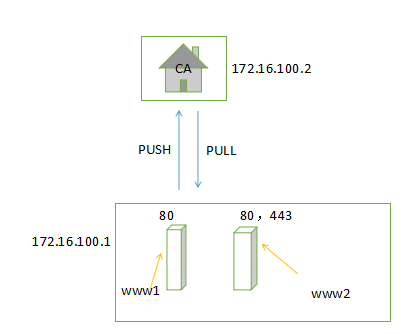
提供两个基于名称的虚拟主机
wp.mykernel.cn,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1.err,访问日志为/var/log/httpd/www1.access;
www.mykernel.cn, 页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2.err,访问日志为/var/log/httpd/www2.access;
为两个虚拟主机建立各自的主页文件index.html,内容分别为其对应的主机名;
通过wp.mykernel.com/server-status输出httpd工作状态相关信息,且只允许提供帐号密码才能访问(status:status);
为上面的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
要求使用证书认证,证书中要求使用的国家(CN)、州(ChengDu)、城市(ChengDu)和组织(MageEdu);
设置部门为Ops,主机名为www.mykernel.cn,邮件为admin@mykernel.cn;
172.16.100.1>配置yum源
* 挂载光盘
# mkdir /media/cdrom
# mount -r /dev/cdrom /media/cdrom
* yum仓库配置
# mv /etc/yum.repos.d/CentOS-Base.repo{,.bak}
# vim CentOS-Base.repo
[C6-media]
name=Base repo for CentOS 6
failovermethod=priority
baseurl=file:///media/cdrom
gpgcheck=1
gpgkey=file:///media/cdrom/RPM-GPG-KEY-CentOS-6
enabled=1安装httpd-2.2程序
# yum -y install httpd
启动服务<172.16.100.1>
# service httpd start
用支持纯文本协议客户端工具访问测试
安装 # yum -y install curl elinks telnet 测试 # curl -I localhost # elinks --dump http://localhost # telnet 172.16.100.1 80 GET / HTTP/1.1 Host: 172.16.100.1
准备DocumentRoot,及对应的index.html文件<172.16.100.1>
# install -d /web/vhosts/www{1,2}/
# echo "wp.mykernel.cn" > /web/vhosts/www1/index.html
# echo "www.mykernel.cn" > /web/vhosts/www2/index.html修改/etc/httpd/conf/httpd.conf配置文件<172.16.100.1>
备份配置文件:
# cp -v /etc/httpd/conf/httpd.conf{,.bak}
在配置文件中修改并添加如下内容:
# vim /etc/httpd/conf/httpd.conf
#DocumentRoot "/var/www/html"
NameVirtualHost *:80
<VirtualHost *:80>
ServerName wp.mykernel.cn
DocumentRoot /web/vhosts/www1
ErrorLog logs/wp.err
CustomLog logs/wp.access combined
<Location /server-status>
SetHandler server-status
Order allow,deny
allow from all
AuthType Basic
AuthName "Secure Type/Domain"
AuthUserFile "conf.d/.htpasswd"
Require user status
</Location>
</VirtualHost>
<VirtualHost *:80>
ServerName www.mykernel.cn
DocumentRoot /web/vhosts/www2
ErrorLog logs/www.err
CustomLog logs/www.access combined
</VirtualHost>
退出配置文件后:
# httpd -t
# htpasswd -c -s /etc/httpd/conf.d/.htpasswd status
# service httpd reload在windows主机中测试,虚拟账号是否能正常登陆
手动添加解析条目
进入此文件C:\Windows\System32\drivers\etc,添加如下条目 172.16.100.1 wp.mykernel.cn 172.16.100.1 www.mykernel.cn
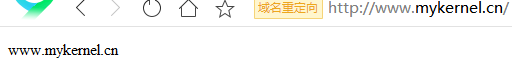
在浏览器中,输入URL,测试结果
http://wp.mykernel.cn http://www.mykernel.cn http://wp.mykernel.cn/server-status 账号:status,密码:status
图片 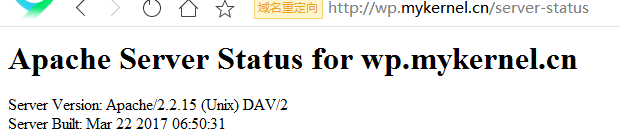
自建CA<172.16.100.2>
# dir=/etc/pki/CA # touch $dir/index.txt # echo "01" > $dir/serial # (umask 077;openssl genrsa -out $dir/private/cakey.pem 2048) # openssl req -new -x509 -key $dir/private/cakey.pem -out $dir/cacert.pem -days 7300 (CN, Beijing, Beijing, MageEdu, Ops, ca.magedu.com, admin@mykernel.cn)
生成请求<172.16.100.1>
# install -d /etc/httpd/ssl && cd /etc/httpd/ssl # (umask 077;openssl genrsa -out httpd.key 2048) # openssl req -new -key httpd.key -out httpd.csr -days 365 (CN, Beijing, Beijing, MageEdu, Ops, www.mykernel.cn, admin@mykernel.cn)
提交请求PUSH<172.16.100.1>
# scp httpd.csr root@172.16.100.2:/tmp
验证并颁发证书<172.16.100.2>
# openssl ca -in /tmp/httpd.csr -out $dir/certs/www.mykernel.cn.crt -days 365
获取证书PULL<172.16.100.1>
# scp root@172.16.100.2:/etc/pki/CA/certs/www.mykernel.cn.crt .
安装mod_ssl模块<172.16.100.1>
# yum -y install mod_ssl
修改/etc/httpd/conf.d/ssl.conf配置<172.16.100.1>
备份配置文件:
# cp -v /etc/httpd/conf.d/ssl.conf{,.bak}
修改配置文件:
# vim /etc/httpd/conf.d/ssl.conf
<VirtualHost *:443>
DocumentRoot "/web/vhosts/www2"
ServerName www.mykernel.cn
SSLEngine on
SSLCertificateFile /etc/httpd/ssl/www.mykernel.cn.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
退出配置文件:
# httpd -t
# service httpd restart
查看443端是否处于监听状态
# ss -tnl测试是否能正常访问
Linux主机测试<172.16.100.2>
添加解析记录: # vim /etc/hosts 172.16.100.1 www.mykernel.cn # openssl s_client -connect www.mykernel.cn:443 -CAfile /etc/pki/CA/cacert.pem New, TLSv1.2/SSLv3
Windows主机测试
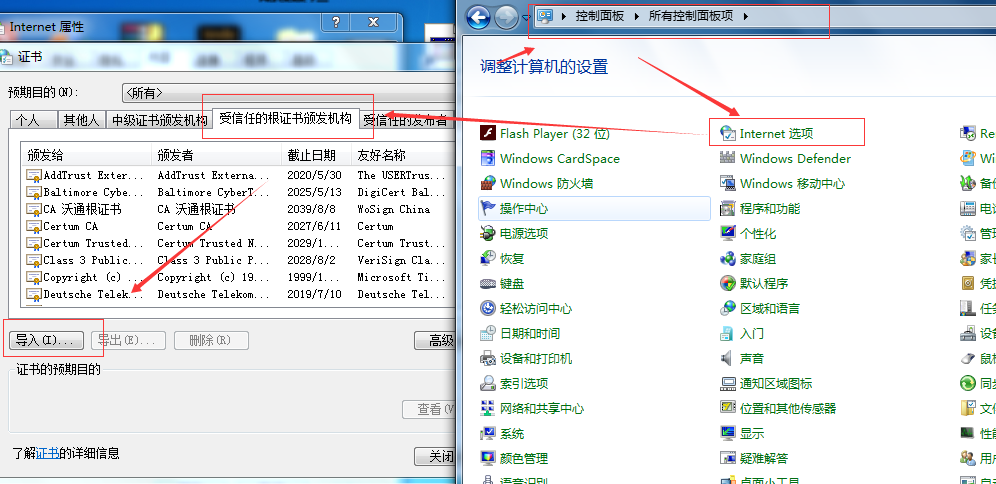
* 将172.16.100.2中的公钥,导入至Windows中的受信任的证书颁发机构列表中 访问https://www.mykernel.cn即可
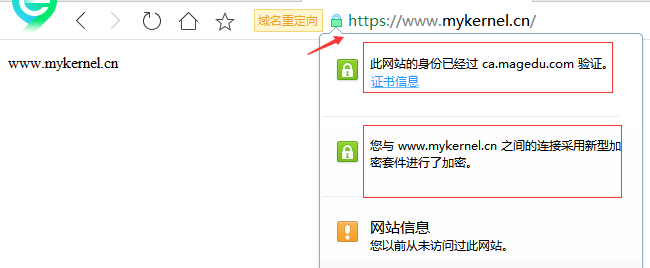
在使用中有任何问题,欢迎反馈给我,可以用以下联系方式跟我交流
邮件:lccnx@foxmail.com
QQ: 2192383945
本文由我表哥引导制作,在此留下QQ,博客
QQ: 2580259468

本文出自 “Reading” 博客,请务必保留此出处http://sonlich.blog.51cto.com/12825953/1969289
httpd-2.2项目(虚拟主机、用户认证、私有网络安全实现)
标签:strive struggle endeavo attempt
原文地址:http://sonlich.blog.51cto.com/12825953/1969289