标签:number mis int dprint win code desc 技术分享 替代
以下内容参考黑客防线2012合订本第294页
其实没什么好说的,直接上代码:
ssdt的结构,和win32差不多,但是要注意这里的指针类型不能用ULONG替代,如果要非要替代应该用ULONGLONG,原因就不说了.
//SSDT的结构 typedef struct _SystemServiceDescriptorTable { PVOID ServiceTableBase; PVOID ServiceCounterTableBase; ULONGLONG NumberOfService; PVOID ParamTableBase; }SystemServiceTable, *PSystemServiceTable; PSystemServiceTable KeServiceDescriptorTable;
获取上面的结构的地址的代码;
ULONGLONG GetKeSeviceDescriptorTable64() { /* 思路是读取0xC0000082 这个寄存器的值是KiSystemCall64函数地址,然后通过特征码搜索即可 ssdt特征码是 0x4c8d15 接着就是ssdt的地址值的偏移了,然后通过公式: 真实地址 = 当前地址+当前指令长度+偏移 得到ssdt地址 找shadow ssdt地址类似 */ PUCHAR startSearchAddress = (PUCHAR)__readmsr(0xC0000082); PUCHAR endSearchAddress = startSearchAddress + 0x500; PUCHAR i = 0; UCHAR b1 = 0, b2 = 0, b3 = 0; ULONG temp = 0; ULONGLONG addr = 0; for ( i = startSearchAddress; i < endSearchAddress; i++) { if (MmIsAddressValid(i) && MmIsAddressValid(i + 1) && MmIsAddressValid(i + 2)) { b1 = *i; b2 = *(i + 1); b3 = *(i + 2); if (b1 == 0x4c && b2 == 0x8d && b3 == 0x15) { memcpy(&temp, i + 3, 4); addr = (ULONGLONG)temp + (ULONGLONG)i + 7;//加上指令长度 KdPrint(("find ssdt is %p\n", addr)); return addr; } } } KdPrint(("find ssdt error\n")); return 0; }
遍历所有Native API 地址:
void througnAllServiceFuncAddr() { ULONG dwTemp = 0; PULONG ServiceTableBase = 0; ULONG i = 0; for ( i = 0; i < KeServiceDescriptorTable->NumberOfService; i++) { if (MmIsAddressValid(KeServiceDescriptorTable->ServiceTableBase)) { ServiceTableBase = (PULONG)KeServiceDescriptorTable->ServiceTableBase; dwTemp = ServiceTableBase[i]; dwTemp = dwTemp >> 4; DbgPrint("the %dth func addr is %p!\n", i, ((ULONGLONG)dwTemp + (ULONGLONG)ServiceTableBase) & 0xffffffff0fffffff); } else { DbgPrint("ServiceTableBase is fault!\n"); return 0; } } }
测试结果:
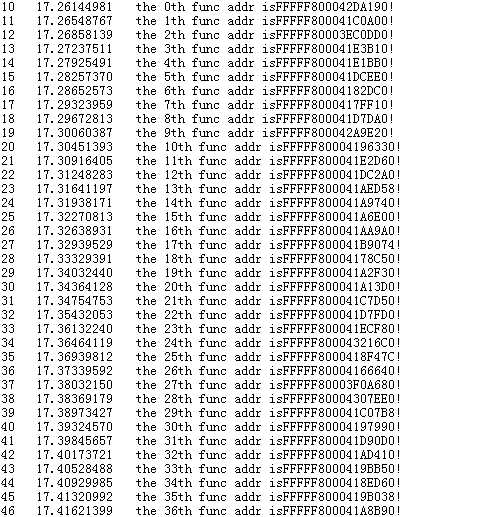
windbg查看的结果:
以ZwOpenProcess为例:
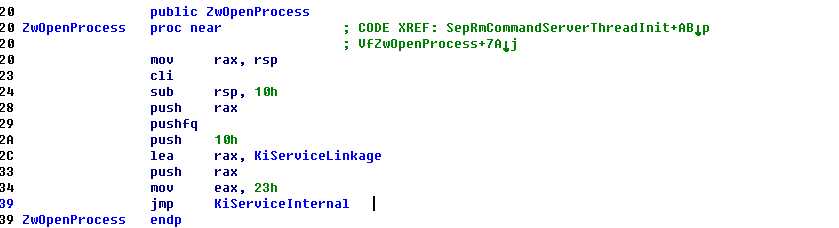
ida中发现他的id是0x23 也就是 35 对应 测试结果是 fffff8000419b038
windbg结果:
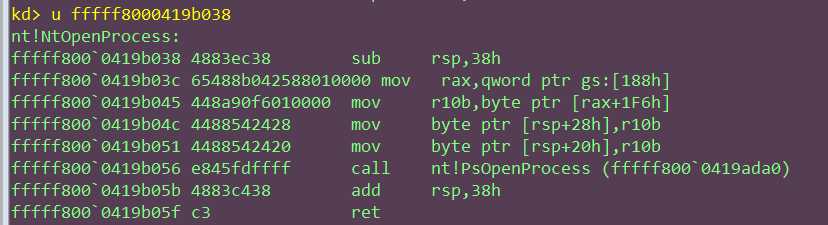
测试无误.
最后如果想hook它那就很简单了.
标签:number mis int dprint win code desc 技术分享 替代
原文地址:http://www.cnblogs.com/freesec/p/7617752.html