标签:password miss several started storage task next fat lan
When it comes to networking,there is probably nothing that cannot be done with Linux.Linux is used to build all sorts of networking systems and appliances(器具,器械,装置),including firewalls,routers,name servers,NAS(Network Attached Storage)boxes and on and on.
Just as the subject of networking is vast(巨大的,广大的),so are the number of commands that can be used to configure and control it.We will focus our attention on just a few of the most frequently(频繁地,屡次地) used ones.The commands chosen for examination include those used to monitor networks and those used to transfer files.In addition,we are going to explore the ssh program that is used to perform remote logins.This chapter will cover:
We‘re going to assume a little background in networking.In this,the Internet age,everyone using a computer needs a basic understandng of networking concepts.To make full use of this chapter we should be familiar with the following terms:
IP(Internet Protocal) address
Host and domain name
URI(Uniform Resource Identifier) 统一资源标识符
Please see the "Further Reading" section below for some useful articles regarding these terms.
Note:Some of the commands we will cover may(depending on your distribution) require the installation of additional packages from your distribution‘s repositories,and some may require superuser privileges to execute.
Check and monitor network
Even if you‘re not the system administrator,it‘s often helpful to examine the performance and operation of a network.
ping
The most basic network command is ping.The ping command sends a special network packet called an ICMP ECHO_REQUEST to a specified host.Most network devices receiving this packet will reply to it,allowing the network connection to be verified.
Note:It is possible to configure most network devices(including Linux hosts) to ignore these packets.This is usually done for security reasons,to partially obscure(遮掩) a host from a potential attacker.It is also common for firewalls to be configured to block ICMP traffic.
For example,to see if we can reach linuxcommand.ort(one of our favorite sites),we can use ping like this:
Once started,ping continus to send packets at a specified interval(default is one second) until it is interrupted:
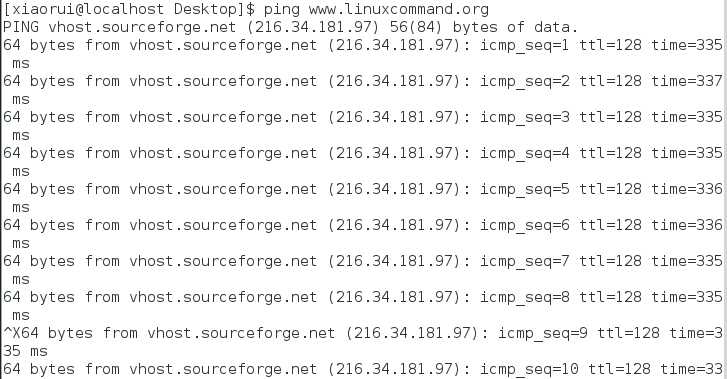
After it is interrupted(in this case after the sixth packet)by pressing Ctrl-c,ping prints performance statistics.A properly performing network will exhibit(展示,展览) zero percent loss.A successful "ping" will indicate that the elements of the network(its interface cards,cabling,routing and gateways) are in generally good working order.
Traceroute
The traceroute program(some systems use the similar tracepath program instead) displays a listing of all the "hops" network traffic takes to get from the local system to a specified host.For example,to see the route taken to reach slashdot.org,we would do this:
The output looks like this:
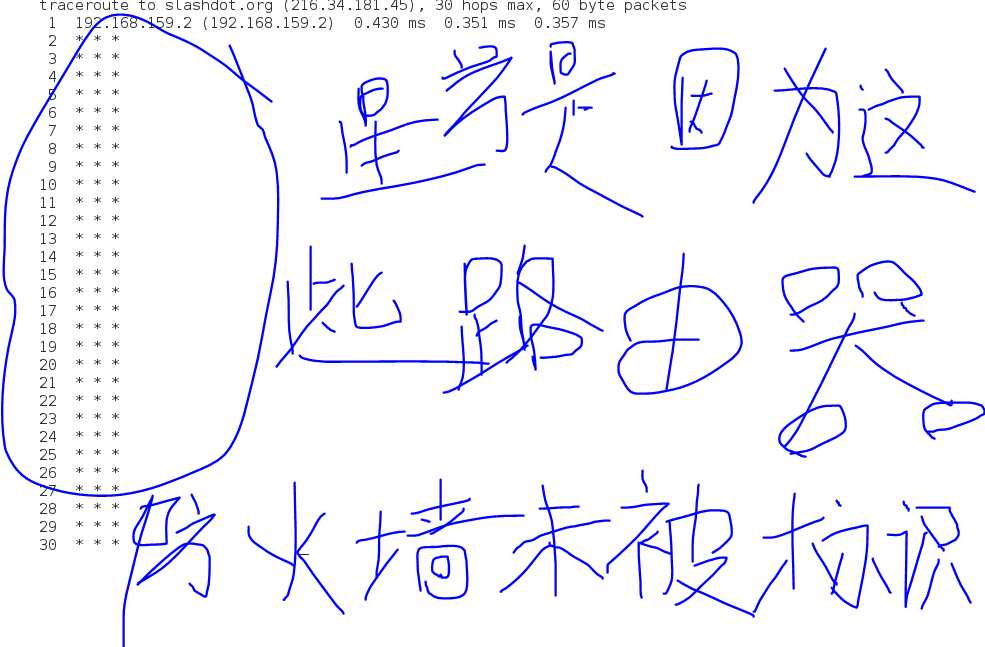
In the output,we can see that connecting from our system to slashdot.org requires traversing(穿越,穿过) thirty routers.For routers that provided identifying information,we see their host names,IP addresses and performance data,which includes three samples of of round-trip time from the local system to the router.For routers that do not provide identifying information(because of router configuration,network congestion(拥堵),firewalls,etc) we see asterisk(星号) as in the line for hop number two.
netstat
The netstat program is used to examine various network settings and statistics.Through the use of its many options,we can loot at a variety of features in our network setup.Using the "-ie" option,we can examine the network interfaces in our system:
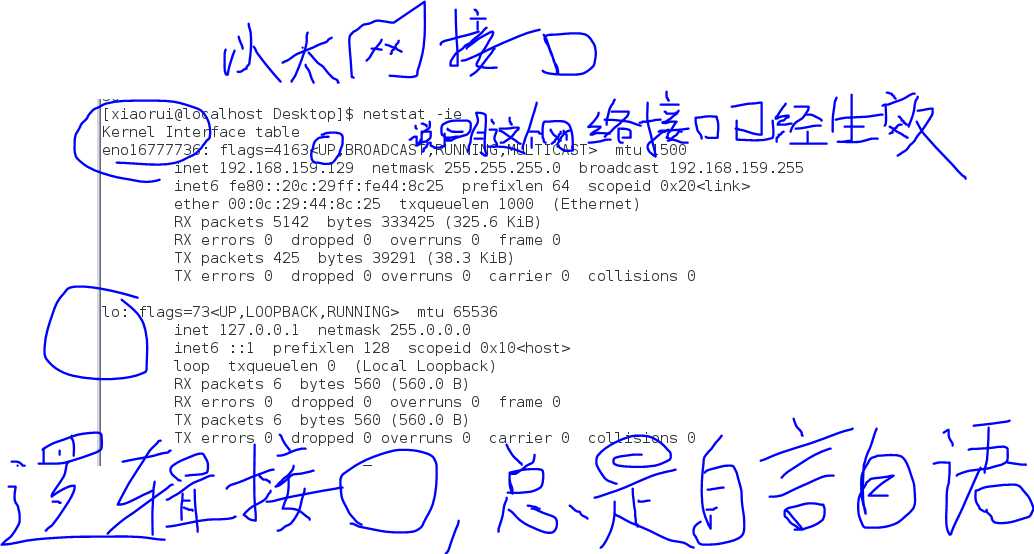
In the example above,we see that our test system has two network interfaces.The first,called etho,is the Enternet interface and the second,called lo,is the loopback interface,a virtual interface that the system uses to "talk to itself."
When performing causal(有原因的,因果关系的) network diagnostics(诊断学)(当执行日常网络诊断时), the important things to look for are the presence(出席,参加,存在) of the word "UP" in the middle of the first line for each interface,indicating that the network interface is enabled,and the presence of a valid IP address in the inet addr field on the second line.For systems using DHCP(Dynamic Host Configuration Protocol), a valid IP address in the inet addr field on the second line.For systems using DHCP(Dynamic Host Configuration Protocol), a valid IP address in this field will verify that the DHCP is working.
Using the "-r" option will display the kernel‘s network routing table.This show how the network is configured to send packets from network to network:
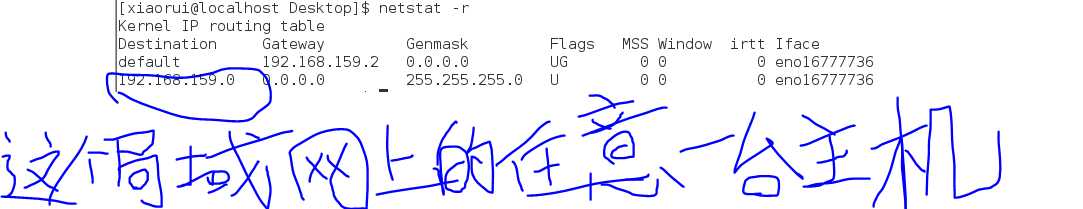
In this simple example,we see a typical routing table for a client machine on a LAN(Local Area Network)behind a firewall/router.The second line of the listing shows the destination 192.168.159.0. IP address that end in zero refer to networks rather than individual hosts,so this destination means any host on the LAN.The next field,Gateway,is the name or IP address of the gateway(router) used to go from the current host to the destination network.An asterisk(星号) in this field indicates that no gateway is needed.
The first line contains the destination default.This means any traffic destined for a network that is not otherwise listed in the table.In our example,we see that the gateway is defined as a router with the address of 192.168.159.2,which presumably(大概,可能) knows what to do with the destination traffic.
The netstat program has many options and we have only looked at a couple.Check out the netstat man page for a complete list.
Transfer files over network
What good is a network unless we know how to move files across it?There are many programs that move data over networks.We will cover two of them now and several more in later sections.
FTP
One of the true "classic" programs,ftp gets it name from the protocol it uses,the File Transfer Protocol.FTP is used widely on the Internet for file downloads.Most,if not all,web browsers support it and you often see URIs starting with the protocol ftp://. Before there were web browsers,there was the ftp program.ftp is used to communicate with FTP servers,machines that contain files that can be uploaded and downloaded over a network.
FTP(in its original form) is not secure,because it send account names and passwords in cleartext.This means that they are not encrypted and anyone sniffing(嗅) the network can see them.Because of this,almost all FTP done over the Internet is done by anonymous FTP servers.An anonymous server allows anyone to login using the login name "anonymous" and a meaningless password.
In the example below,we show a typical session with the ftp program downloading an Ubuntu iso image located in the /pub/cd_images/Ubuntu-8.04 directory of the anonymous FTP server fileserver:
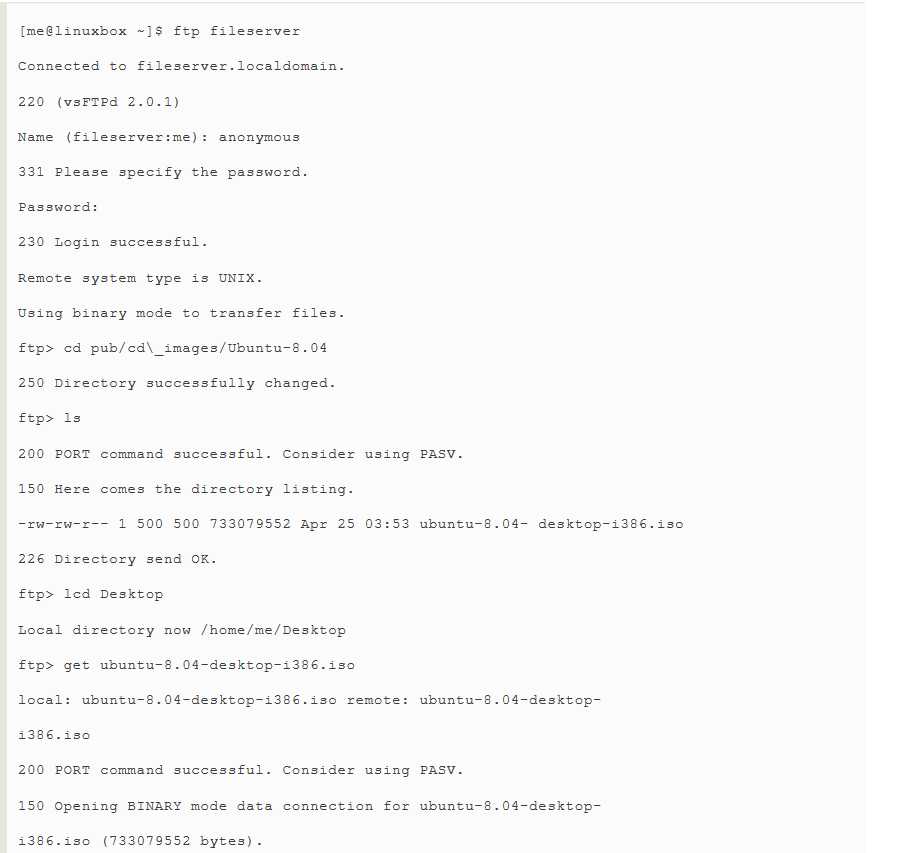
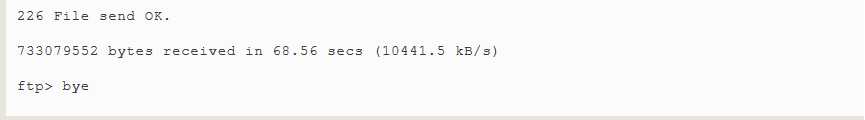
Here is an explanation of the commands entered during this session:
Table 17-1:
| Command | Meaning |
| ftp filesever | Invoke the ftp program and have it connect to FTP server fileserver. |
| anonymous | Login name.After the login prompt,a password prompt will appear.Some servers will accept a blank password,others will require a password in the form of a email address.In that case,try something like "user@example.com". |
| cd pub/cd_images/Ubuntu-8.04 | Change to the directory on the remote system containing the desired file.Note that on most anonymous FTP servers,the files for public downloading are found somewhere under the pub directory. |
| ls | List the directory on the remote system. |
| lcd Desktop | Change the directory on the local system to ~/Desktop. In the example,the ftp program was invoked when the working directory was ~.This command changes the working directory to ~/Desktop. |
| get ubuntu-8.04-desktop-i386.iso | Tell the remote system to transfer the file unbuntu-8.04-desktop i386.iso to the local system.Since the working directory on the local system was changed to ~/Desktop,the file will be downloaded there. |
| bye | Log off the remote server and end ftp program session.The commands quit and exit may also be used. |
Typing "help" at the "ftp>" prompt will display a list of the supported commands.Using ftp on a server where sufficient(足够的,充足的) permissions have been granted,it is possible to perform many ordinary file mangement tasks.It‘s clumsy(笨拙的,笨重的),but it does work.
lftp-better ftp
ftp is not the only command line FTP client.In fact,there are many.One of better(and more popular) ones is lftp by Alexander Lukyanow.It works much like the traditional ftp program,but has many additional convenience features including multiple protocol support(including HTTP),automatic re-try on failed downloads,background processes,tab completion of path names,and many more.
weget
Another popular command line program for file downloading is wget.It is useful for loading content from both web and FTP sites.Single files,multiple files,and even entire sites can be downloaded.To downloaded the first page of linuxcommand.org we could do this:
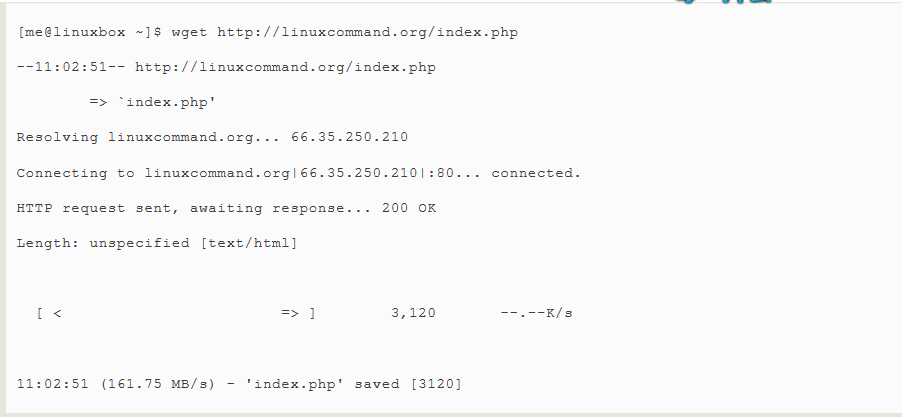
The program‘s many options allow wget to recursively download,download files in the background(allowing you to log off but continue loading),and complete the download of a partically downloaded file.These features are well documented in its better-than-average man page.
Communicate safely with remote hosts
For many years,Unix-like operating systems have had the ability to be administered remotely via a network.In the early days,before the general(普遍) adoption(接受)of the Internet,there were a couple of popular programs used to log in to remote hosts.These were the rlogin and telnet programs.These programs,however,suffer from the fatal(致命的,灾难性的) flaw(缺点,瑕疵) that the ftp program does;they transmit all their communications(including login names and passwords) in cleartext.This makes them wholly(完全地,全部) inappropriate(不恰当的,不适宜的) for use in the Internet age.
ssh
To address this problem,a new protocol called SSH(Secure Shell) was developed.SSH solves the two basic problems of secure communication with a remote host.First,it authenticates that the remote host is who it says it is (thus preventing so-called"man in the middle" attacks),and second,it encrypts all of the communications between the local and remote hosts.
SSH consists of two parts.An SSH server runs on the remote host,listening for incoming connections on port twenty-two,while an SSH client is used on the local system to communicate with the remote server.
Most Linux distributions ship an implementaion(实现) of SSH called OpenSSH from the BSD project.Some distributions include both the client and the server packages by default(for example,Red Hat),while others(such as Ubuntu) only support the client.To enable a system to receive remote connections,it must have the OpenSSH-server package installed,configured and running,and (if the system is either running or is behind a firewall) it must allow incoming network connections on TCP port 22..
Tip:If you don‘t have a remote system to connect to but want to try these examples,make sure the OpenSSH-server package is installed on your system and use localhost as the name of the remote host.That way,your machine will create network connection with itself.
The SSH client program used to connect to remote SSH servers is called,appropriately(适当地) enough(顺理成章),ssh.To connect to a remote host named remoted-sys,we would use the ssh client program like so;
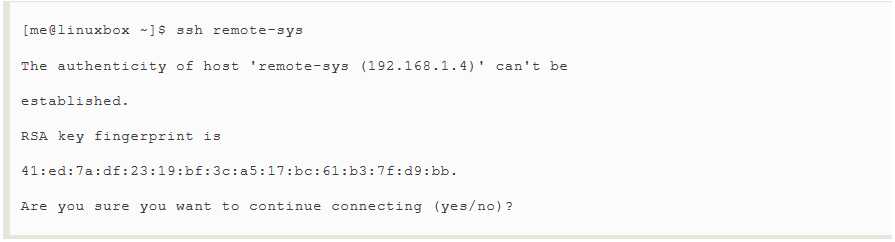
The first time the connection is attempted(试图,尝试),a message is displayed indicating that the authenticity of the remote host cannot be established.This is because the client program has never seen this remote host before.To accept the credentials(资格证书) of the remote host,enter"yes" when prompted.Once the connection is established,the user is prompted for his/her password:
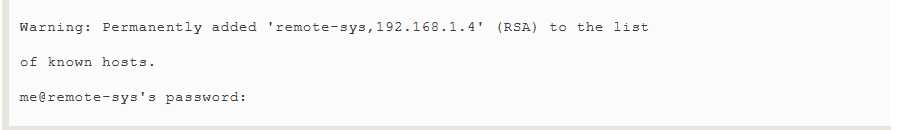
After the password is successfully entered,we receive the shell prompt from the remote system:

The remote shell session continues until the user enters the exit command at the remote shell prompt,thereby closing the remote connection.At this point,the local shell session resumes(恢复) and the local shell prompt reappears.
It is also possible to connect to remote systems using a different user name.For example,if the local user "me" had an account named "bob" on a remote system,user me could log in the account bob on the remote systems as follows:

As stated before,ssh verifies(核实,查证) the authenticity of te remote host.If the remote host does not successfully authenticate,the following message appears:
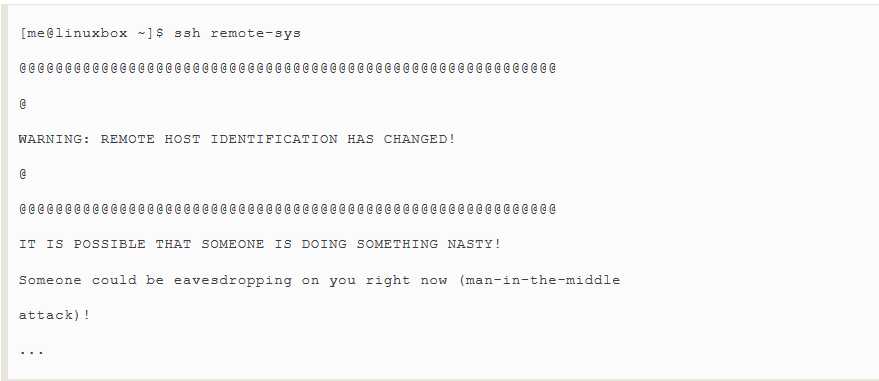
This message is caused by onte of two possible situations.First,an attacker maybe attempting a "man-in-the-middle" attack.This is rare,since everybody knows that ssh alerts(使警觉地到,警告) the user to this.The more likely culprit(犯人,罪犯) is that the remote system has been changed somehow;for example,its operating system or SSH server has been reinstalled.In the interests of security and safety however,the first possibility should not be dismissed out of hand.Always check with the administrator of the remote system when this message occurs.
After it has been determined that the message is due to a benign(良性的,吉利的) cause,it is safe to correct the problem on the client side.This is done by using a text editor(vim perhaps) to remove the obsolete(老式的,废弃的) key from the ~/.ssh/known_hosts file.In the example message above,we see this:

(offending 不愉快的,厌恶的)
This means that line one of the known_host file contains the offending key.Delete this line from the file,and the ssh program will be able to accept new authentication credentials (资格证书) from the remote system.
Besides opening a shell session on a remote system,ssh also allows us to execute a single command on a remote system.For example,to execute the free command on a remote host named remote-sys and have the results displayed on the local system:
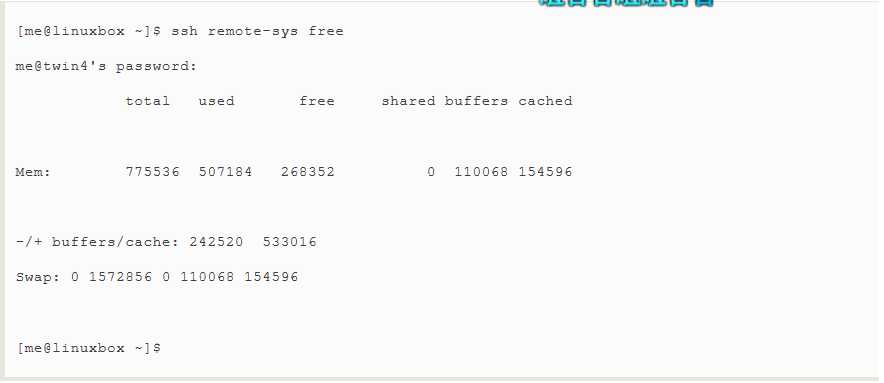
It is possible to use this technique in more interesting ways,such as this example in which we perform an ls on the remote system and redirect the output to a file on the local system:
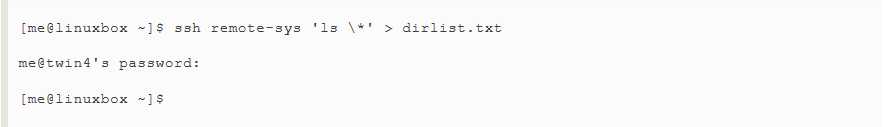
Notice the use of the single quotes in the command above.This is done because we do not want the pathname expansion performed on the local machine.;rahter,we want it to be performed on the remote system.Likewise,if we had wanted the output redirected to a file on the remote machine,we could have placed the redirection operator and the filename within the single quotes:
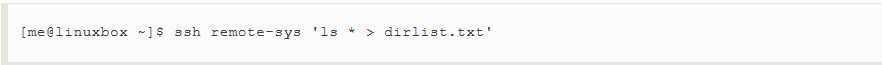
Tunneling With SSH
Part of what happens when you establish a connection with a remote host via SSH is that an encrypted tunnel is created between the local and remote systems.Normally,this tunnel is used to allow commands typed at the local system to be transimitted safely to the remote system,and for the results to be transmitted safely back.In addition to this basic function,the SSH protocol allows most types of network traffic to be sent through the encrypted tunnel,creating a sort of VPN(Virtual Private Network) between the local and remote systems.
Perhaps the most common use of this feature is to allow X Window system traffic to be transmitted.On a system running an X server(that is, a machine displaying a GUI),it is possible to launch and run an X client program(a graphical application) on a remote system and have its display appear on the local system.It‘s easy to do,here‘s an example:let‘s say we are sitting at a Linux system called linuxbox which is running an X server,and we want to run the xload program on a remote system named remote-sys and see the program‘s graphical output on our local system.We could do this:
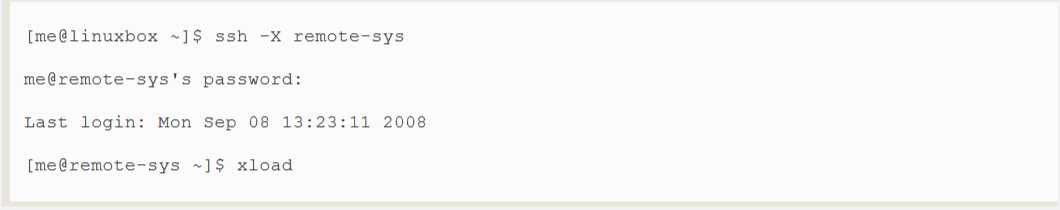
After the xload command is executed on the remote system,its window appears on the local system.On some systems,you may need to use the "-Y" option rather than the "-X" option to do this.
Scp and sftp
The OpenSSH package also includes two programs that can make use of an SSH encrypted tunnel to copy files across the network..The first,scp(secure copy) is used much like the familar cp program to copy files.The most notable(值得注意的,显著的,著名的) difference is that the source or destination pathnames may be preceded(在...之前,先于) with the name of a remote host,followed by a colon character.For example,if we wanted to copy a document named document.txt from our home directory on the remote system,remote-sys,to the current working directory on our local system,we could do this:
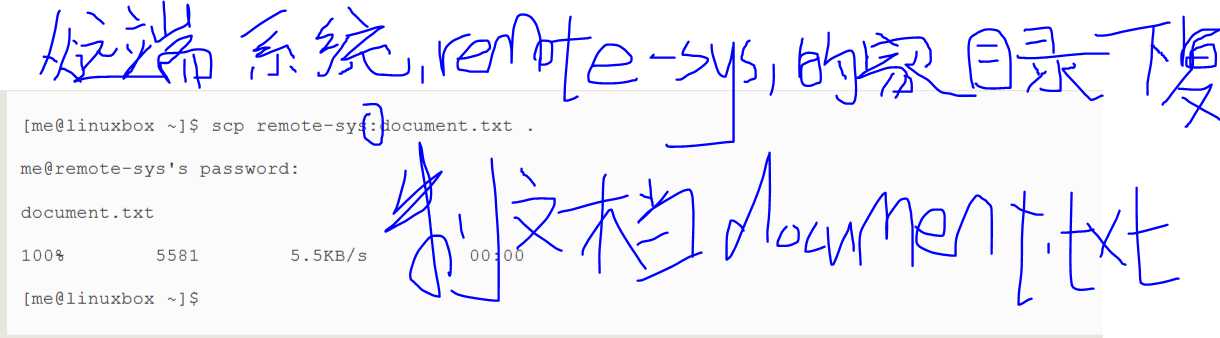
As with ssh,you may apply a user name to the beginning of the remote host‘s name if the desired remote host account name does not match that of the local system:

The second SSH file copying program is sftp which,as its name implies(暗示,意味,隐含),is a secure replacement for the ftp program,sftp works much like the original ftp program that we used earlier;however,instead of transmitting everything in cleartext,it uses an SSH encrypted tunnel.sftp has an important advantage over conventional(依照惯例的,常规的) ftp in that it does not require an FTP server to be running on the remote host.It only requires the SSH server.This means that any remote machine that can connect with the SSH client can also be used as a FTP-like server.Here is a sample(样本,会话) session:
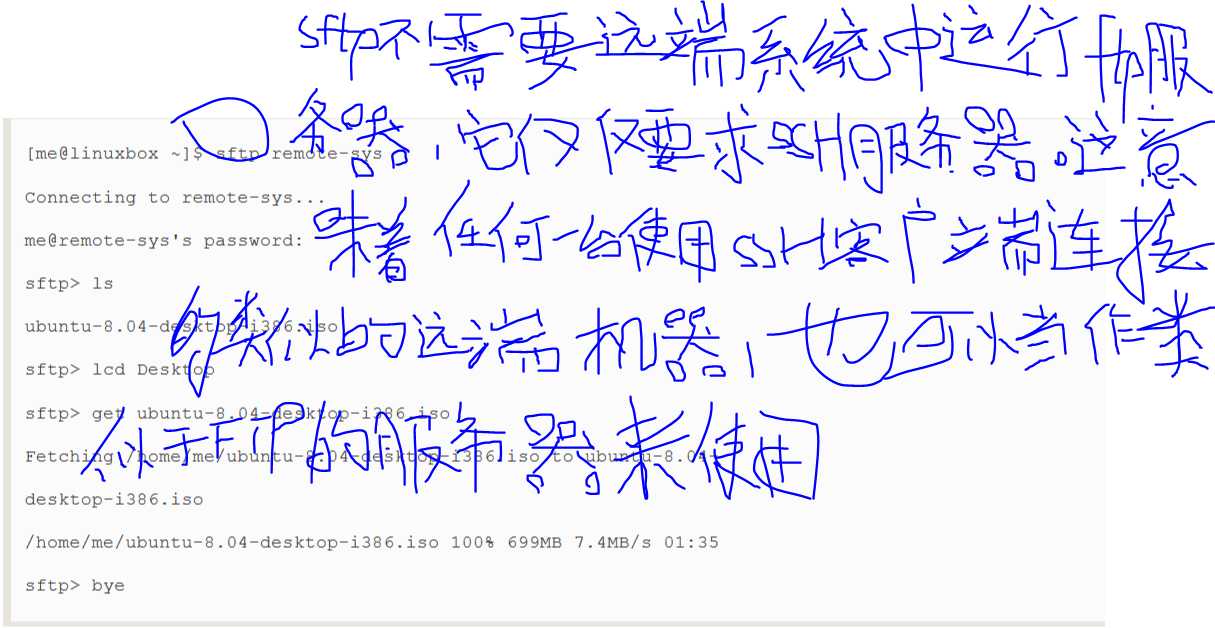
Tip:The SFTP protocol is supported by many of the graphical file managers found in Linux distributions.Using either Nautilus(GNOME) or Konqueror(KDE) ,we can enter a URI beginning with sftp://into the location bar(位置栏) and operate on files stored on a remote system running an SSH server.
An SSH Client For Windows?
Let‘s say you are sitting at a Windows machine but you need to log in your Linux server and get some real work done,what do you do?Get an SSH client program for your Windows box,of course !There are a number of these.The most popular one is probably PuTTY by Simon Tatham and his team.The PuTTY program displays a terminal window and allow a Windows user to open an SSH(or telnet) session on a remote host.The program also provides analogs(类似物,同类的) for the scp and sftp programs.
标签:password miss several started storage task next fat lan
原文地址:http://www.cnblogs.com/itmeatball/p/7617137.html