标签:缓存 tin image tab manage exp res try lookup
dns_bind_正反向域名解析
bind服务支持TSIG安全加密传输机制
dns域名解析服务用于解析域名与IP地址对应关系服务
正向解析:根据域名查找对应IP地址
反向解析:根据IP地址查找对应域名
dns结构模型:
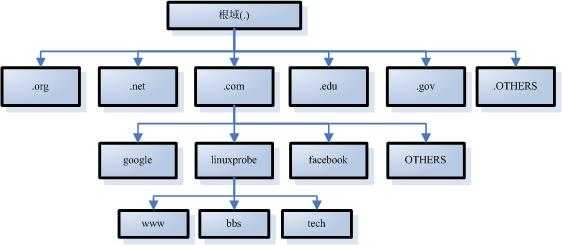
但靠几台dns服务器不能满足全球用户的需求,所以工作形式分为主、从、缓存服务器
主服务器:在特定区域内具有唯一性,负责维护该区域内的域名与IP对应关系
从服务器:从主服务器获取域名与IP对应关系并且维护,起备份作用
缓存服务器:通过向其他dns服务器查询获取域名与IP地址对应关系,提高重复查询的效率
dns查询分为递归查询与迭代查询:
递归查询:用于客户机向DNS服务器查询
迭代查询:用于dns服务器向其他dns服务器查询
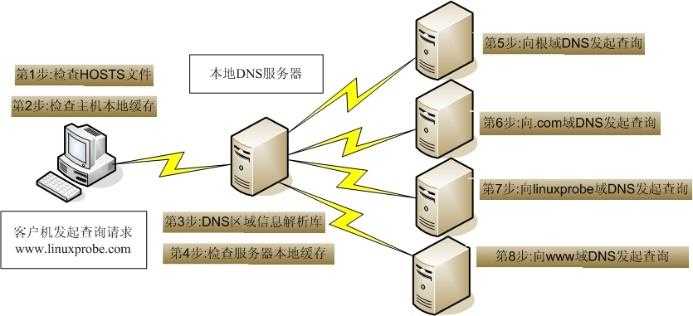
dns查询流程图:
安装bind服务程序:
[root@ns1 ~]# yum -y install bind-chroot Installed: bind-chroot.x86_64 32:9.9.4-14.el7 Dependency Installed: bind.x86_64 32:9.9.4-14.el7 Complete!
域名解析服务bind的程序名叫named
|
主域名 |
/usr/sbin/named |
|
主配置文件 |
/etc/named.conf |
|
区域配置文件 |
/etc/named.rfc1912.zones |
查看配置文件(有两处修改):
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // options { listen-on port 53 { 127.0.0.1; }; #修改为dns服务器的ip或者any listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { localhost; }; #修改为any,代表允许任何主机查询 /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; dnssec-lookaside auto; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
一、正向域名解析
修改配置文件:
[root@ns1 ~]# vim /etc/named.rfc1912.zones zone "dns.com" IN { type master; file "dns.com.zone"; allow-update { none; }; };
使用named-checkconf\named-checkzone查询主配置和区域文件语法错误:
[root@ns1 ~]# named-checkconf /etc/named.conf
配置解析数据信息:
使用正向文件解析模板文件:”/var/named/named.localhost“
[root@ns1 ~]# cd /var/named/ [root@ns1 named]# cp -a /var/named/named.localhost dns.com.zone [root@ns1 named]# ll total 20 drwxr-x---. 7 root named 56 Oct 17 09:59 chroot drwxrwx---. 2 named named 6 Jan 29 2014 data -rw-r-----. 1 root named 152 Jun 21 2007 dns.com.zone drwxrwx---. 2 named named 6 Jan 29 2014 dynamic -rw-r-----. 1 root named 2076 Jan 28 2013 named.ca -rw-r-----. 1 root named 152 Dec 15 2009 named.empty -rw-r-----. 1 root named 152 Jun 21 2007 named.localhost -rw-r-----. 1 root named 168 Dec 15 2009 named.loopback drwxrwx---. 2 named named 6 Jan 29 2014 slaves [root@ns1 named]# vim dns.com.zone $TTL 1D @ IN SOA dns.com. root.dns.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS ns.dns.com. ns A 192.168.200.102 www A 192.168.200.10 bbs A 192.168.200.20
检查区域解析文件:
[root@ns1 named]# named-checkzone dns.com dns.com.zone zone dns.com/IN: loaded serial 0 OK
重启named服务且验证结果:
[root@ns1 named]# systemctl restart named [root@ns1 named]# nslookup www.dns.com Server:::1 Address:::1#53 Name:www.dns.com Address: 192.168.200.10 [root@ns1 named]# nslookup bbs.dns.com Server:::1 Address:::1#53
Name:bbs.dns.com Address: 192.168.200.20
二、反向解析(通过ip地址查询域名)
配置区域数据信息:
[root@ns1 named]# vim /etc/named.rfc1912.zones zone "200.168.192.in-addr.arpa" IN { type master; file "192.168.200.arpa"; };
配置解析数据信息:
反向解析使用反向解析模板文件:”/var/named/named.loopback“
[root@ns1 named]# cp -a /var/named/named.loopback 192.168.200.arpa [root@ns1 named]# vim 192.168.200.arpa $TTL 1D @ IN SOA dns.com. root.dns.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS ns.dns.com. 102 PTR ns.dns.com. 10 PTR www.dns.com. 20 PTR bbs.dns.com. [root@ns1 named]# named-checkzone 200.168.192.in-addr.arpa 192.168.200.arpa zone 200.168.192.in-addr.arpa/IN: loaded serial 0 OK
重启named服务,验证结果:
[root@ns1 named]# systemctl restart named [root@ns1 named]# nslookup 192.168.200.10 Server:::1 Address:::1#53 10.200.168.192.in-addr.arpaname = www.dns.com. [root@ns1 named]# nslookup 192.168.200.20 Server:::1 Address:::1#53 20.200.168.192.in-addr.arpaname = bbs.dns.com.
linux[基础]-33-[dns服务器]-[正反向域名解析]-[01]
标签:缓存 tin image tab manage exp res try lookup
原文地址:http://www.cnblogs.com/msl23/p/7680445.html