标签:pre iptable timeout link 信息 oss fifo in out ipa
网络相关1.查看网卡信息:
[root@weix01 ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.188.130 netmask 255.255.255.0 broadcast 192.168.188.255
inet6 fe80::9835:40a7:677a:8a07 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ed:fb:e6 txqueuelen 1000 (Ethernet)
RX packets 67 bytes 7721 (7.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 108 bytes 12009 (11.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 72 bytes 5712 (5.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 72 bytes 5712 (5.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@weix01 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:ed:fb:e6 brd ff:ff:ff:ff:ff:ff
inet 192.168.188.130/24 brd 192.168.188.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::9835:40a7:677a:8a07/64 scope link
valid_lft forever preferred_lft forever
2.断开,连接网卡:ifdown,ifup
[root@weix01 ~]# ifdown ens33
成功断开设备 ‘ens33‘。
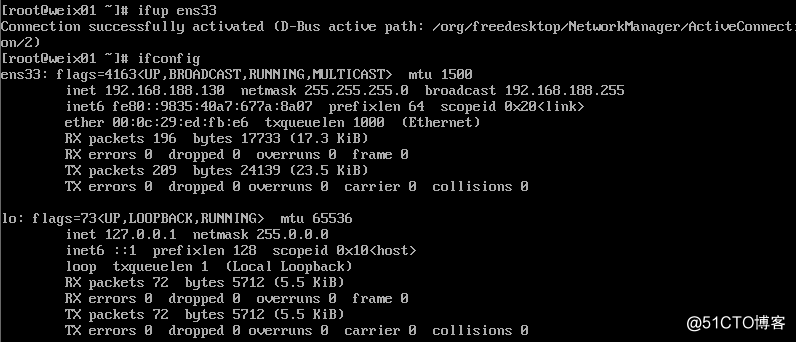
3.为了避免远程断开,可以两个命令一起执行:
[root@weix01 ~]# ifdown ens33 && ifup ens33
成功断开设备 ‘ens33‘。
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/3)4.增加虚拟网卡:
(1)复制配置文件
[root@weix01 ~]# cd /etc/sysconfig/network-scripts/
[root@weix01 network-scripts]# ls
ifcfg-ens33 ifdown-ipv6 ifdown-Team ifup-eth ifup-post ifup-tunnel
ifcfg-lo ifdown-isdn ifdown-TeamPort ifup-ippp ifup-ppp ifup-wireless
ifdown ifdown-post ifdown-tunnel ifup-ipv6 ifup-routes init.ipv6-global
ifdown-bnep ifdown-ppp ifup ifup-isdn ifup-sit network-functions
ifdown-eth ifdown-routes ifup-aliases ifup-plip ifup-Team network-functions-ipv6
ifdown-ippp ifdown-sit ifup-bnep ifup-plusb ifup-TeamPort
[root@weix01 network-scripts]# cp ifcfg-ens33 ifcfg-ens33\:0
(2)修改配置文件
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33:0
UUID=05229985-42cc-4e39-a815-d7a5365ff276
DEVICE=ens33:0
ONBOOT=yes
IPADDR=192.168.188.150
NETMASK=255.255.255.0
(3)重启服务
[root@weix01 network-scripts]# ifdown ens33 && ifup ens33
成功断开设备 ‘ens33‘。
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/4)
[root@weix01 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.188.130 netmask 255.255.255.0 broadcast 192.168.188.255
inet6 fe80::9835:40a7:677a:8a07 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ed:fb:e6 txqueuelen 1000 (Ethernet)
RX packets 744 bytes 67249 (65.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 568 bytes 70477 (68.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens33:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.188.150 netmask 255.255.255.0 broadcast 192.168.188.255
ether 00:0c:29:ed:fb:e6 txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 72 bytes 5712 (5.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
5.查看网卡是否连接:
[root@weix01 network-scripts]# mii-tool ens33
ens33: negotiated 1000baseT-FD flow-control, link ok
也可以使用
[root@weix01 network-scripts]# ethtool ens33
Settings for ens33:
Supported ports: [ TP ]
Supported link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
1000baseT/Full
Supported pause frame use: No
Supports auto-negotiation: Yes
Advertised link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
1000baseT/Full
Advertised pause frame use: No
Advertised auto-negotiation: Yes
Speed: 1000Mb/s
Duplex: Full
Port: Twisted Pair
PHYAD: 0
Transceiver: internal
Auto-negotiation: on
MDI-X: off (auto)
Supports Wake-on: d
Wake-on: d
Current message level: 0x00000007 (7)
drv probe link
Link detected: yes
6.更改主机名:
[root@weix01 network-scripts]# hostnamectl set-hostname weixing01
[root@weix01 network-scripts]# cd
[root@weix01 ~]# hostname
weixing01
[root@weix01 ~]# bash #进入bash显示已经更改
[root@weixing01 ~]#
[root@weixing01 ~]# exit
exit
[root@weix01 ~]# cat /etc/hostname #配置文件地址
weixing01
7.DNS配置文件:
[root@weix01 ~]# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 199.29.29.29
8.更改解析地址:
[root@weix01 ~]# ping www.qq123.com
PING www.qq123.com (202.91.250.93) 56(84) bytes of data.
64 bytes from 202.91.250.93 (202.91.250.93): icmp_seq=1 ttl=128 time=26.3 ms
64 bytes from 202.91.250.93 (202.91.250.93): icmp_seq=2 ttl=128 time=28.1 ms
64 bytes from 202.91.250.93 (202.91.250.93): icmp_seq=3 ttl=128 time=25.3 ms
64 bytes from 202.91.250.93 (202.91.250.93): icmp_seq=4 ttl=128 time=23.2 ms
^C
--- www.qq123.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 23.246/25.771/28.145/1.768 ms
[root@weix01 ~]# vim /etc/hosts #更改该文件后生效
[root@weix01 ~]# ping www.qq123.com
PING www.qq123.com (192.168.188.150) 56(84) bytes of data.
64 bytes from www.qq123.com (192.168.188.150): icmp_seq=1 ttl=64 time=0.039 ms
64 bytes from www.qq123.com (192.168.188.150): icmp_seq=2 ttl=64 time=0.131 ms
^C
--- www.qq123.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 999ms
rtt min/avg/max/mdev = 0.039/0.085/0.131/0.046 ms
hosts文件更改,一个ip可以对应多个域名,一个域名对应多个ip时,以先出现的为主
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.188.150 www.qq123.com

1.永久关闭,更改配置文件:
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled #此行改为disabled
# SELINUXTYPE= can take one of three two values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
[root@weix01 ~]# vi /etc/selinux/config
[root@weix01 ~]# getenforce
Enforcing
[root@weix01 ~]# setenforce 0
[root@weix01 ~]# getenforce
Permissive
重启后生效
2.启用netfilter服务:
(1)首先关闭 firewalled
[root@weix01 ~]# systemctl disable firewalld
Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
[root@weix01 ~]# systemctl stop firewalld
[root@weix01 ~]# yum install -y iptables-services #安装iptables包
已加载插件:fastestmirror
base | 3.6 kB 00:00:00
epel/x86_64/metalink | 6.6 kB 00:00:00
epel | 4.7 kB 00:00:00
extras | 3.4 kB 00:00:00
updates | 3.4 kB 00:00:00
(1/3): epel/x86_64/group_gz | 266 kB 00:00:00
(2/3): epel/x86_64/primary_db | 6.2 MB 00:00:08
epel/x86_64/updateinfo FAILED MB 24:02:49 ETA
http://repo.fedoralinux.ir/pub/epel/7/x86_64/repodata/8c5ceb073924e98c6b29b5c344e9ff6443bbe44ef82bec9360fd313b8d210c53-updateinfo.xml.bz2: [Errno 12] Timeout on http://repo.fedoralinu
(2)启动iptables服务
[root@weix01 ~]# systemctl enable iptables
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
[root@weix01 ~]# systemctl start iptables
(3)查看iptables规则
[root@weix01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
30 2340 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 16 packets, 1712 bytes)
pkts bytes target prot opt in out source destination 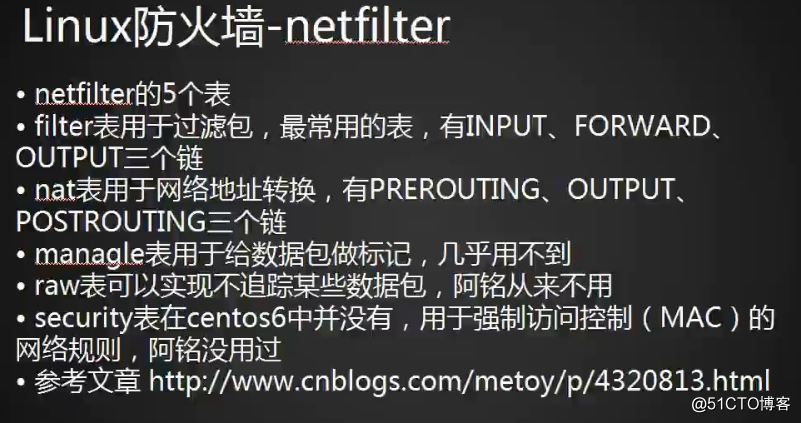
1.一共5个表,5个链: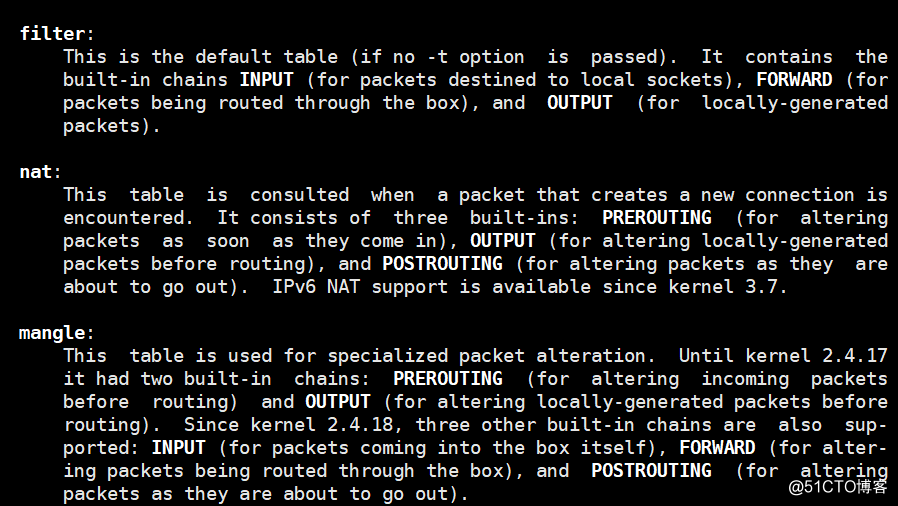
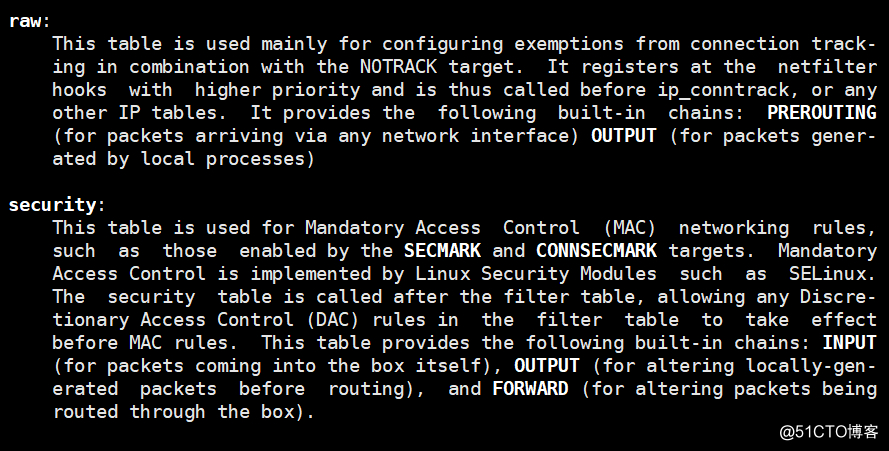
2.5个表和5个链之间关系:
http://www.cnblogs.com/metoy/p/4320813.html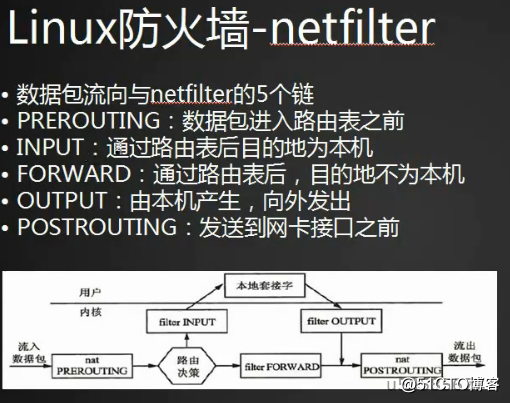
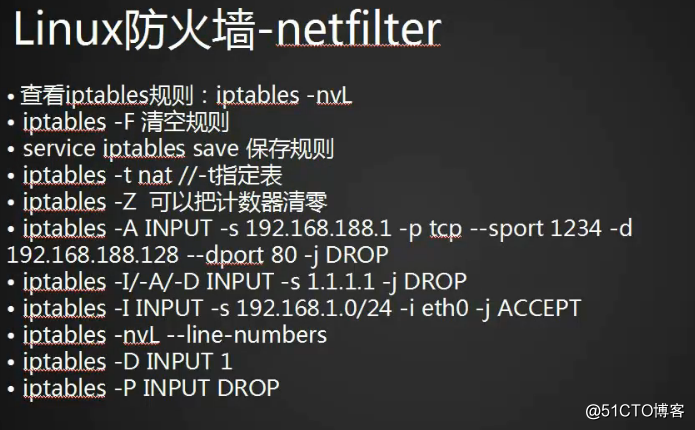
1.默认规则存放位置:
[root@weix01 ~]# cat /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
2.清空规则:-F
[root@weix01 ~]# iptables -F
[root@weix01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 8 packets, 672 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 5 packets, 712 bytes)
pkts bytes target prot opt in out source destination 3.重启后加载默认规则:默认是filter表
[root@weix01 ~]# service iptables restart
Redirecting to /bin/systemctl restart iptables.service
[root@weix01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
6 500 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 576 bytes)
pkts bytes target prot opt in out source destination
4.保存规则:
service iptables save5.指定nat表:-t
[root@weix01 ~]# iptables -nvL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination 6.使用Z选项清空计数:
[root@weix01 ~]# iptables -Z ;iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination 7.常用用法:增加一条规则,在最后面,将来源过滤掉:
[root@weix01 ~]# iptables -A INPUT -s 192.168.188.1 -p tcp --sport 1234 -d 192.168.188.128 --dport 80 -j DROP
[root@weix01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
214 16748 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
1 328 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 14 packets, 1996 bytes)
pkts bytes target prot opt in out source destination
8.插入一条规则:在最前面
[root@weix01 ~]# iptables -I INPUT -p tcp --dport 80 -j DROP
[root@weix01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
368 29272 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
1 328 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 608 bytes)
pkts bytes target prot opt in out source destination 9.删除规则:-D
[root@weix01 ~]# iptables -D INPUT -p tcp --dport 80 -j DROP
[root@weix01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
427 35264 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
2 656 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 608 bytes)
pkts bytes target prot opt in out source destination 10.另外一种方法删除规则:
(1)打印规则编号
[root@weix01 ~]# iptables -nvL --line-number
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
2 644 55892 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
6 2 656 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
7 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 25 packets, 4504 bytes)
num pkts bytes target prot opt in out source destination (2)删除对应编号
[root@weix01 ~]# iptables -D INPUT 7
[root@weix01 ~]# iptables -nvL --line-number
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
2 701 60544 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
4 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
6 2 656 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 10 packets, 2448 bytes)
num pkts bytes target prot opt in out source destination 11.修改默认规则:
iptables -P OUTPUT DROP/ACCEPT标签:pre iptable timeout link 信息 oss fifo in out ipa
原文地址:http://blog.51cto.com/13517254/2064863