filter表实例
需求:把80端口,22端口,21端口放行,22端口指定只有某IP段可以访问,其他IP段的均拒绝,在这里,利用SHELL脚本完成这个需求
[root@am-01:~#] vim /usr/local/sbin/iptables.sh #! /bin/bash # 以下操作没用-t指定表,所以对默认的filter表生效 # 定义一个变量ipt,命令用绝对路径能不受环境变量影响 ipt="/usr/sbin/iptables" # 清空之前定义的规则 $ipt -F # 设置INPUT链的默认规则 $ipt -P INPUT DROP # 设置OUTPUT链的默认规则 $ipt -P OUTPUT ACCEPT # 设置FPRWARD链的默认规则 $ipt -P FORWARD ACCEPT # 用-m state --state RELATED,ESTABLISHED指定状态,针对这些状态采取放行的规则 $ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT # 把172.16.0.0/24网段访问22端口的数据包放行 $ipt -A INPUT -s 172.16.0.0/24 -p tcp --dport 22 -j ACCEPT # 把访问80端口和21端口的数据包放行 $ipt -A INPUT -p tcp --dport 80 -j ACCEPT $ipt -A INPUT -p tcp --dport 21 -j ACCEPT [root@am-01:~#] sh /usr/local/sbin/iptables.sh [root@am-01:~#] iptables -nvL Chain INPUT (policy DROP 6 packets, 1010 bytes) pkts bytes target prot opt in out source destination 33 2168 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT tcp -- * * 172.16.0.0/24 0.0.0.0/0 tcp dpt:22 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 19 packets, 2740 bytes) pkts bytes target prot opt in out source destination
icmp示例:
禁止其他主机ping这台主机
[root@am-01:~#] iptables -I INPUT -p icmp --icmp-type 8 -j DROP [root@am-01:~#] iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 21 1556 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 8 2943 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 6 packets, 656 bytes) pkts bytes target prot opt in out source destination [root@am-01:~#] ifconfig eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.17.1.240 netmask 255.255.255.0 broadcast 172.17.1.255 inet6 fe80::20c:29ff:fe08:ac45 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:08:ac:45 txqueuelen 1000 (Ethernet) RX packets 5052652 bytes 411274464 (392.2 MiB) RX errors 0 dropped 7222 overruns 0 frame 0 TX packets 115615 bytes 28406618 (27.0 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
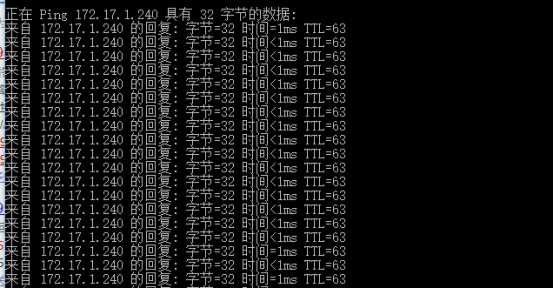
客户端无法ping通这台主机

取消规则,客户端可以ping通这台主机
[root@am-01:~#] iptables -D INPUT -p icmp --icmp-type 8 -j DROP
nat表实例
A机器两块网卡eno16777736(192.168.133.130)、eno33554976(192.168.100.1),eno16777736可以上外网,eno33554976仅仅是内部网络,B机器只有eno33554976(192.168.100.100),和A机器eno33554976可以通信互联。
准备工作:
把虚拟机A克隆一台命名为虚拟机B
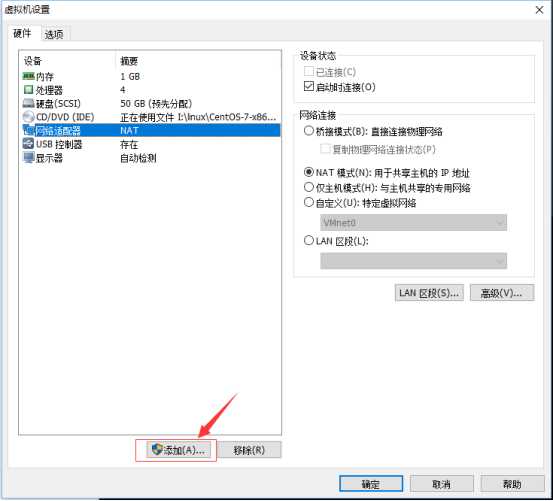
设置虚拟机A网卡
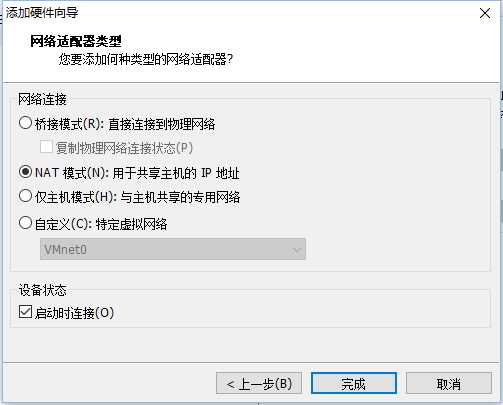
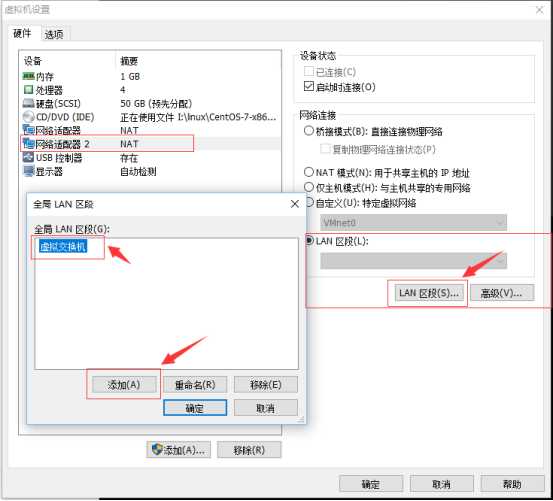
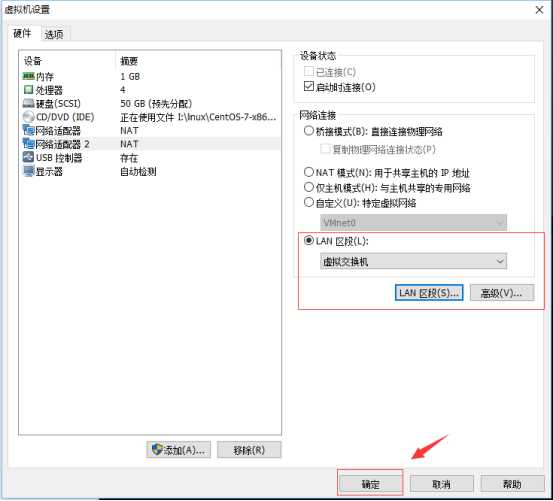
设置虚拟机B网卡
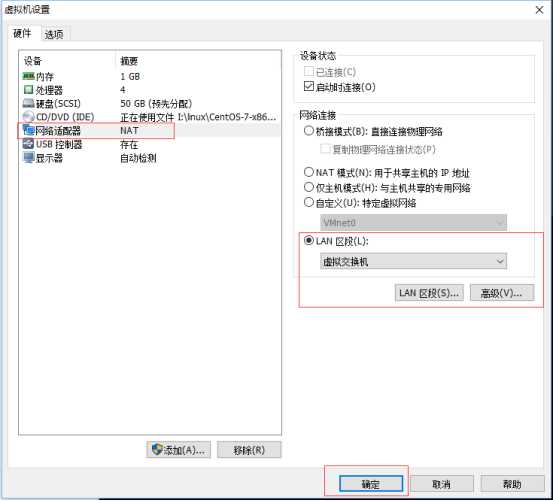
最后把虚拟机A和虚拟机B都启动起来
给两台虚拟机的虚拟网卡添加IP地址
临时添加:ifconfig eno33554976 192.168.100.1/24
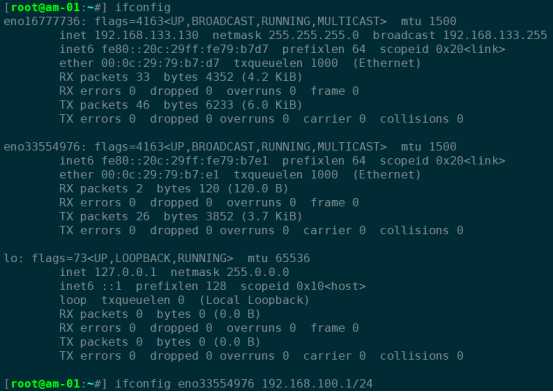
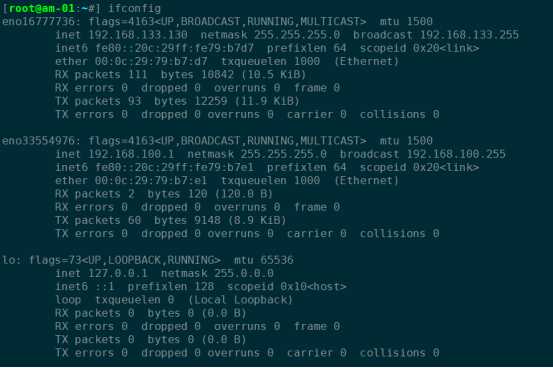
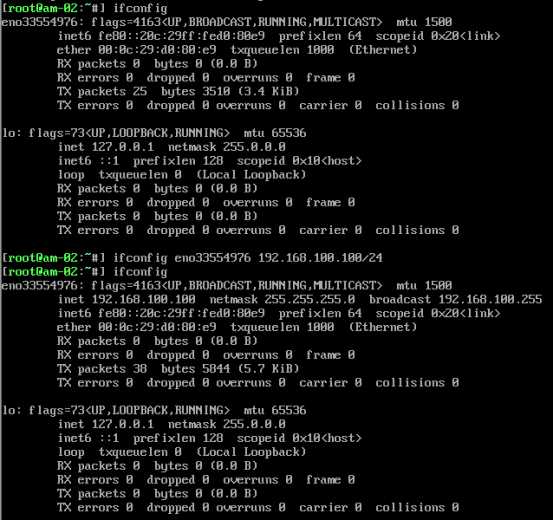
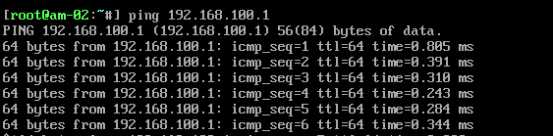
需求1:可以让B机器连接外网
开启A机器的路由转发:
[root@am-01:~#] cat /proc/sys/net/ipv4/ip_forward 0 [root@am-01:~#] echo "1" > /proc/sys/net/ipv4/ip_forward [root@am-01:~#] cat /proc/sys/net/ipv4/ip_forward 1
增加规则:
[root@am-01:~#] iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o eno16777736 -j MASQUERADE [root@am-01:~#] iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 MASQUERADE all -- * eno16777736 192.168.100.0/24 0.0.0.0/0
设置B机器的网关(临时):
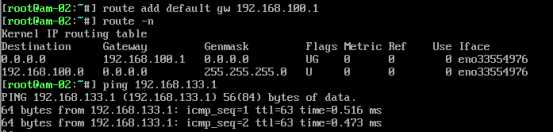
设置B机器DNS:

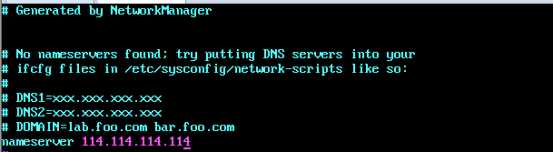
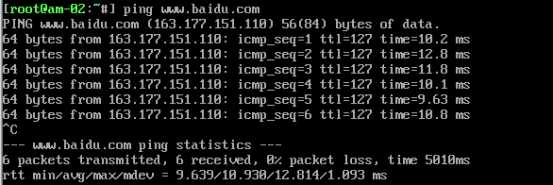
需求2:C机器(母机)只能和虚拟机A通信,让C机器(母机)可以直接连通虚拟机B的22端口
开启A机器的路由转发:
[root@am-01:~#] cat /proc/sys/net/ipv4/ip_forward 0 [root@am-01:~#] echo "1" > /proc/sys/net/ipv4/ip_forward [root@am-01:~#] cat /proc/sys/net/ipv4/ip_forward 1
A机器上设置规则:
[root@am-01:~#] iptables -t nat -F [root@am-01:~#] iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination [root@am-01:~#] iptables -t nat -A PREROUTING -d 192.168.133.130 -p tcp --dport 1122 -j DNAT --to 192.168.100.100:22 [root@am-01:~#] iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.133.130 [root@am-01:~#] iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 DNAT tcp -- * * 0.0.0.0/0 192.168.133.130 tcp dpt:1122 to:192.168.100.100:22 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 SNAT all -- * * 192.168.100.100 0.0.0.0/0 to:192.168.133.130
设置B机器的网关(临时):
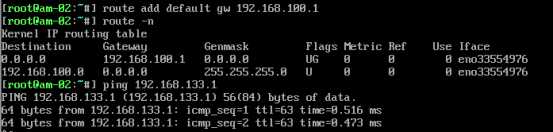
测试:
在XSHELL新建一个链接
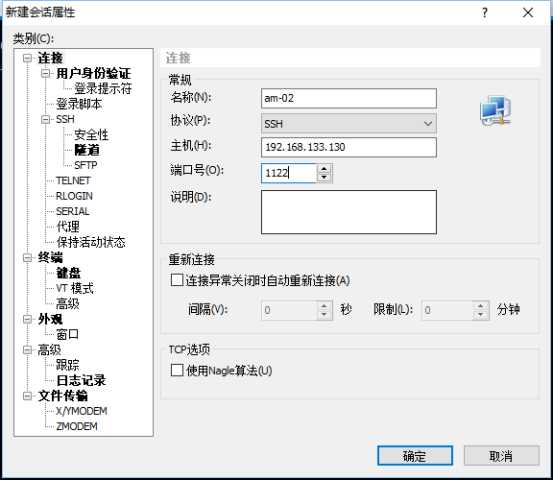
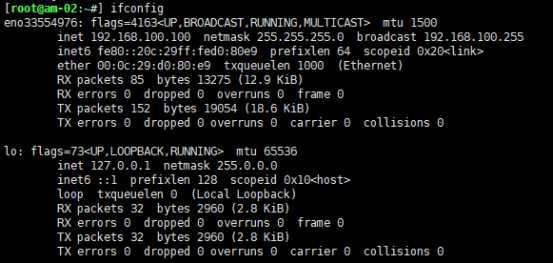
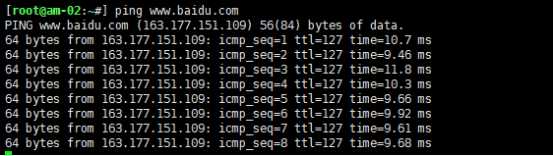
扩展
iptables应用在一个网段:
http://www.aminglinux.com/bbs/thread-177-1-1.html
sant,dnat,masquerade:
http://www.aminglinux.com/bbs/thread-7255-1-1.html
iptables限制syn速率:
