标签:rds 主机 code vsftp try access bmp 结果 else
1.实现简单探测
使用socket模块,connect()方法建立与指定IP和端口的网络连接;revc(1024)方法将读取套接字中接下来的1024B数据
mport socket import sys socket.setdefaulttimeout(2) s=socket.socket() s.connect((‘192.168.1.1‘,21)) ans=s.recv(1024) print(ans)
通过函数实现
通过def()关键字定义,示例中定义扫描FTP banner信息的函数:
#!/usr/bin/python #coding=utf-8 import socket def retBanner(ip,port): try: socket.setdefaulttimeout(2) s = socket.socket() s.connect((ip,port)) banner = s.recv(1024) return banner except: return def checkVulns(banner): if ‘vsFTPd‘ in banner: print ‘[+] vsFTPd is vulnerable.‘ elif ‘FreeFloat Ftp Server‘ in banner: print ‘[+] FreeFloat Ftp Server is vulnerable.‘ else: print ‘[-] FTP Server is not vulnerable.‘ return def main(): ips = [‘10.10.10.128‘,‘10.10.10.160‘] port = 21 banner1 = retBanner(ips[0],port) if banner1: print ‘[+] ‘ + ips[0] + ": " + banner1.strip(‘\n‘) checkVulns(banner1) banner2 = retBanner(ips[1],port) if banner2: print ‘[+] ‘ + ips[1] + ": " + banner2.strip(‘\n‘) checkVulns(banner2) if __name__ == ‘__main__‘: main()
迭代实现
#!/usr/bin/python #coding=utf-8 import socket def retBanner(ip,port): try: socket.setdefaulttimeout(2) s = socket.socket() s.connect((ip,port)) banner = s.recv(1024) return banner except: return def checkVulns(banner): if ‘vsFTPd‘ in banner: print ‘[+] vsFTPd is vulnerable.‘ elif ‘FreeFloat Ftp Server‘ in banner: print ‘[+] FreeFloat Ftp Server is vulnerable.‘ else: print ‘[-] FTP Server is not vulnerable.‘ return def main(): portList = [21,22,25,80,110,443] ip = ‘10.10.10.128‘ for port in portList: banner = retBanner(ip,port) if banner: print ‘[+] ‘ + ip + ‘:‘ + str(port) + ‘--‘ + banner if port == 21: checkVulns(banner) if __name__ == ‘__main__‘: main()
OS模块
os.path.isfile()检查该文件是否存在
os.access()判断当前用户是否有权限读取该文件
#!/usr/bin/python #coding=utf-8 import sys import os if len(sys.argv) == 2: filename = sys.argv[1] if not os.path.isfile(filename): print ‘[-] ‘ + filename + ‘ does not exit.‘ exit(0) if not os.access(filename,os.R_OK): print ‘[-] ‘ + filename + ‘ access denied.‘ exit(0) print ‘[+] Reading From: ‘ + filename
将上述各个模块整合起来,实现对目标主机的端口及其banner信息的扫描:
#!/usr/bin/python #coding=utf-8 import socket import sys import os def retBanner(ip,port): try: socket.setdefaulttimeout(2) s = socket.socket() s.connect((ip,port)) banner = s.recv(1024) return banner except: return def checkVulns(banner,filename): f = open(filename, ‘r‘) for line in f.readlines(): if line.strip(‘\n‘) in banner: print ‘[+] Server is vulnerable: ‘ + banner.strip(‘\n‘) def main(): if len(sys.argv) == 2: filename = sys.argv[1] if not os.path.isfile(filename): print ‘[-] ‘ + filename + ‘ does not exit.‘ exit(0) if not os.access(filename,os.R_OK): print ‘[-] ‘ + filename + ‘ access denied.‘ exit(0) print ‘[+] Reading From: ‘ + filename else: print ‘[-] Usage: ‘ + str(sys.argv[0]) + ‘ <vuln filename>‘ exit(0) portList = [21,22,25,80,110,443] ip = ‘10.10.10.128‘ for port in portList: banner = retBanner(ip,port) if banner: print ‘[+] ‘ + ip + ‘:‘ + str(port) + ‘--‘ + banner if port == 21: checkVulns(banner,filename) if __name__ == ‘__main__‘: main()
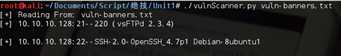
运行结果:
这段代码通过分别读取两个文件,一个为加密口令文件,另一个为用于猜测的字典文件。在testPass()函数中读取字典文件,并通过crypt.crypt()进行加密,其中需要一个明文密码以及两个字节的盐,然后再用加密后的信息和加密口令进行比较查看是否相等即可。
#!/usr/bin/python #coding=utf-8 import crypt def testPass(cryptPass): salt = cryptPass[0:2] dictFile = open(‘dictionary.txt‘,‘r‘) for word in dictFile.readlines(): word = word.strip(‘\n‘) cryptWord = crypt.crypt(word,salt) if cryptWord == cryptPass: print ‘[+] Found Password: ‘ + word + "\n" return print ‘[-] Password not Found.\n‘ return def main(): passFile = open(‘passwords.txt‘) for line in passFile.readlines(): if ":" in line: user = line.split(‘:‘)[0] cryptPass = line.split(‘:‘)[1].strip(‘ ‘) print ‘[*] Cracking Password For : ‘ + user testPass(cryptPass) if __name__ == ‘__main__‘: main()
主要使用zipfile库的extractall()方法,其中pwd参数指定密码
#!/usr/bin/python #coding=utf-8 import zipfile import optparse from threading import Thread def extractFile(zFile,password): try: zFile.extractall(pwd=password) print ‘[+] Fonud Password : ‘ + password + ‘\n‘ except: pass def main(): parser = optparse.OptionParser("[*] Usage: ./unzip.py -f <zipfile> -d <dictionary>") parser.add_option(‘-f‘,dest=‘zname‘,type=‘string‘,help=‘specify zip file‘) parser.add_option(‘-d‘,dest=‘dname‘,type=‘string‘,help=‘specify dictionary file‘) (options,args) = parser.parse_args() if (options.zname == None) | (options.dname == None): print parser.usage exit(0) zFile = zipfile.ZipFile(options.zname) passFile = open(options.dname) for line in passFile.readlines(): line = line.strip(‘\n‘) t = Thread(target=extractFile,args=(zFile,line)) t.start() if __name__ == ‘__main__‘: main()
代码中导入了optparse库解析命令行参数,调用OptionParser()生成一个参数解析器类的示例,parser.add_option()指定具体解析哪些命令行参数
usage输出的是参数的帮助信息;同时也采用了多线程的方式提高破解速率。
运行结果:

《Python绝技:运用Python成为顶级黑客》 Python实用小工具
标签:rds 主机 code vsftp try access bmp 结果 else
原文地址:https://www.cnblogs.com/LyShark/p/9101842.html