标签:discuss last cin compute service surf lib hardware lag

Linux is a Unix-like open source operating system. At the core of the operating system is the Linux kernel. It acts as the intermediary between the applications which run in the operating system and the underlying hardware.
The history of Linux began in 1991 with the commencement of a personal project by Finnish student Linus Torvalds to create a new free operating system kernel. Since then, the resulting Linux kernel has been marked by constant growth throughout its history. Since the initial release of its source code in 1991, it has grown from a small number of C files under a license prohibiting commercial distribution to the 4.15 version in 2018 with more than 23.3 million lines of source code without comments under the GNU General Public License v2.

Full multitasking — Multiple tasks can be run in the background, and multiple devices, such as a modem, printer, and hard drive, can be accessed at the same time.
Virtual memory — Linux safely uses a portion of your hard drive as virtual memory, which increases the efficiency of your system by keeping active processes in RAM and placing less frequently used or inactive portions of memory on disk. Virtual memory also utilizes all your system‘s memory and doesn‘t allow memory segmentation to occur.
Hardware support — Linux, especially Intel-based versions, supports nearly all hardware architectures and devices, with the best support for legacy hardware. This is an advantage in that new versions of the operating system will not make your older hardware obsolete.
The X Window System — The X Window System is a graphics system for UNIX machines. This powerful interface supports many applications and is the standard interface for the industry.
Built-in networking support — Linux uses standard TCP/IP protocols, including Network File System (NFS), Network Information Service (NIS, formerly known as YP), Session Message Block (SMB), and others. You can access the Internet by connecting your system with an Ethernet card, or a parallel-port, serial cable, or over a modem to another system.
Shared libraries — Because each command shares a common library of subroutines it can call at runtime, Linux helps saves memory and hard drive space.
Compatibility with the IEEE POSIX.1 standard — Because of this compatibility, Linux supports many of the standards set forth for all UNIX systems.
Open Source code — The Linux kernel uses no code from AT&T or any other proprietary source. This allows other organizations, the GNU project, hackers, and programmers from all over the world to develop and contribute software for Linux.
Documentation — Nearly every Linux distribution comes with more than 12,000 pages of documentation in the form of manual pages, info documents, or guides. You‘ll also find extra technical documentation for software packages under the directory. Unlike operating systems offered by the monopolistic software industry, Linux is fully documented—one problem might be that there is too much information!
Lower cost than most other UNIX systems and UNIX clones — If you have a fast Internet connection and a CDR drive, you can freely download Linux off the Internet. Many books also come with a free copy (this book includes the latest version of Intel-based Red Hat Linux on the CD-ROMs).
GNU software support — Linux can run a wide range of free software available through the GNU project. This software includes everything from programming tools, such as compilers, assemblers, linkers, and loaders, to system administration utilities, such as stream editors, the venerable editor, and even games.





Ubuntu Installation Tutorial:?? http://blog.csdn.net/u013142781/article/details/50529030
CentOS Installation Tutorial:?? http://www.osyunwei.com/archives/7829.html
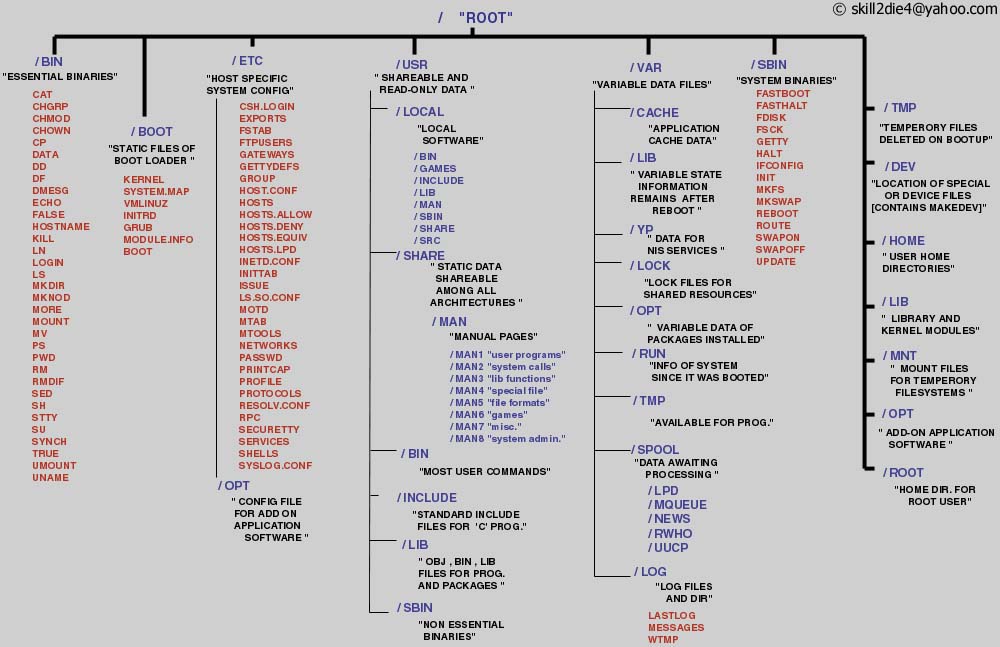
The Linux directory structure is like a tree. The base of the Linux file system hierarchy begins at the root, or trunk, and directories branch off from there. Each one of these directories, called folders on other operating systems, can and often do contain other directories. The directories on a Linux system are separated by a forward slash.

A shell is a program that accepts commands and instructs the operating system to execute those commands. When you connect to a Linux system over the network, for example, a shell is started and acts as your interface to the system. The shell in this particular case is a command line interpreter. The command-line interface is often referred to by its abbreviation, CLI.
Ubuntu 14.04 LTS linuxsvr tty1 linuxsvr login: jason Password: Welcome to Ubuntu 14.04 LTS jason@linuxsvr:~$
The tilde represents the home directory of the current user which is /home/jason in this example.
For more details anout the above basic commands, please refer to the website: https://www.computerhope.com/unix.htm#commands.
In addition to referencing directories by their full or absolute paths, you can reference directories
by their relative paths.
e.g.
e.g.
$ mkdir newdir
$ mkdir newdir/one/two
mkdir: cannot create directory ‘newdir/one/two’: No such file or directory
$ mkdir -p newdir/one/two
$ rmdir newdir
rmdir: directory "newdir": Directory not empty
$ rm -rf newdir
$ ls newdir
ls: newdir: No such file or directory
$ mkdir newerdir
$ rmdir newerdir
$ ls newerdir
ls: cannot access newerdir: No such file or directoryThe ls command only lists files and directories, it can
provide important details about those files and directories.
| option | meaning |
|---|---|
| -l | displays a long listing format |
| -a | display hidden files with ls |
| -F | append a file type indicator to the name of the file or directory |
| -t | sort the output by time, displays the most recently modified items first |
| -r | reverse the order of -t |
| -R | perform a recursive listing |
| -d | have ls operate on just the directory |
| --color | colorize the output of the ls command |
| -b | Quoting and escaping to space, |, &, ‘, ;, (, ), <, >, space, tab |
ls -l
$ ls
Desktop Documents Downloads Music to-do.txt
$ ls -l
total 20
drwxrwxr-x 2 jason users 4096 May 3 08:33 Desktop
drwxrwxr-x 2 jason users 4096 May 3 08:35 Documents
drwxrwxr-x 2 jason users 4096 May 3 08:38 Downloads
drwxrwxr-x 3 jason users 4096 Jun 21 21:16 Music
-rw-r--r-- 1 jason users 73 Jun 22 19:34 to-do.txtls -l starts with a series of characters that represent the
permissions of the file or directory. The number that
follows the permissions string represents the number of links to the file or directory. Next, the owner is displayed followed by the group name. The file size is then displayed. The timestamp provided represents the modification time. The last item is the name of the file or directory itself.
ls -a
$ ls
Desktop Documents Downloads Music to-do.txt
$ ls -a
. .. .bash_history .bash_logout .bashrc Desktop Documents Downloads
Music .profile .ssh to-do.txt
$ ls -a -l
total 48
drwxr-xr-x 7 jason users 4096 Jun 22 20:36 .
drwxr-xr-x 6 root root 4096 May 4 10:26 ..
-rw------- 1 jason users 3738 Jun 22 19:37 .bash_history
-rw-r--r-- 1 jason users 220 Mar 30 2013 .bash_logout
-rw-r--r-- 1 jason users 3650 Jun 22 19:41 .bashrc
drwxrwxr-x 2 jason users 4096 May 3 08:33 Desktop
drwxrwxr-x 2 jason users 4096 May 3 08:35 Documents
drwxrwxr-x 2 jason users 4096 May 3 08:38 Downloads
drwxrwxr-x 3 jason users 4096 Jun 21 21:16 Music
-rw-r--r-- 1 jason users 675 Mar 30 2013 .profile
drwx------ 2 jason users 4096 May 3 12:44 .ssh
-rw-r--r-- 1 jason users 73 Jun 22 19:34 to-do.txtls -a -l is equivalent to ls -al and ls -la.
ls -F
$ ls
Desktop Documents Downloads link-to-to-do Music program to-do.txt
$ ls -F
Desktop/ Documents/ Downloads/ link-to-to-do@ Music/ program* todo.txt
$ ls -lF
total 24
drwxrwxr-x 2 jason users 4096 May 3 08:33 Desktop/
drwxrwxr-x 2 jason users 4096 May 3 08:35 Documents/
drwxrwxr-x 2 jason users 4096 May 3 08:38 Downloads/
lrwxrwxrwx 1 jason users 9 Jun 22 21:01 link-to-to-do -> to-do.txt
drwxrwxr-x 3 jason users 4096 Jun 21 21:16 Music/
-rwxr-xr-x 1 jason users 13 Jun 22 21:02 program*
-rw-r--r-- 1 jason users 73 Jun 22 19:34 to-do.txt| Symbol | File Type |
|---|---|
| / | Directory |
| @ | Symlink. The file that follows the -> symbol is the target of the link. |
| * | Executable script or program |
| = | Socket |
| > | Door |
| | | Named pipe |
ls -t
$ ls -t
program link-to-to-do to-do.txt Music Downloads Documents Desktop
$ ls -lt
total 24
-rwxr-xr-x 1 jason users 13 Jun 22 21:02 program
lrwxrwxrwx 1 jason users 9 Jun 22 21:01 link-to-to-do -> to-do.txt
-rw-r--r-- 1 jason users 73 Jun 22 19:34 to-do.txt
drwxrwxr-x 3 jason users 4096 Jun 21 21:16 Music
drwxrwxr-x 2 jason users 4096 May 3 08:38 Downloads
drwxrwxr-x 2 jason users 4096 May 3 08:35 Documents
drwxrwxr-x 2 jason users 4096 May 3 08:33 Desktop
$ ls -lrt
total 24
drwxrwxr-x 2 jason users 4096 May 3 08:33 Desktop
drwxrwxr-x 2 jason users 4096 May 3 08:35 Documents
drwxrwxr-x 2 jason users 4096 May 3 08:38 Downloads
drwxrwxr-x 3 jason users 4096 Jun 21 21:16 Music
-rw-r--r-- 1 jason users 73 Jun 22 19:34 to-do.txt
lrwxrwxrwx 1 jason users 9 Jun 22 21:01 link-to-to-do -> to-do.txt
-rwxr-xr-x 1 jason users 13 Jun 22 21:02 programls -R
$ ls -R
.:
Desktop Documents Downloads link-to-to-do Music program to-do.txt
./Desktop:
./Documents:
cat.jpg report.txt
./Downloads:
./Music:
JohnColtrane
./Music/JohnColtrane:
giant-steps.mp3To accomplish the same goal, but in a more visually appealing way, use the tree command. To view only the directory structure, use tree -d. For colorized output, use tree -C. The tree command is not always installed by default so you may have to rely on the ls command.
ls -d
$ tree Music/
Music/
|-- JohnColtrane
|-- giant-steps.mp3
1 directory, 1 file
$ ls Music/
JohnColtrane
$ ls -l Music/
total 4
drwxrwxr-x 2 jason users 4096 Jun 22 21:39 JohnColtrane
$ ls -d Music/
Music/
$ ls -ld Music/
drwxrwxr-x 3 jason users 4096 Jun 21 21:16 Music/ls --color
$ ls --color
Desktop Documents Downloads link-to-to-do Music program to-do.txt
ls -b
$ ls
my to do list
$ ls -l
total 4
-rw-r--r-- 1 jason users 73 Jun 22 22:16 my to do list
$ ls -l my to do list
ls: cannot access my: No such file or directory
ls: cannot access to: No such file or directory
ls: cannot access do: No such file or directory
ls: cannot access list: No such file or directory
$ ls -l "my to do list"
-rw-r--r-- 1 jason users 73 Jun 22 22:16 my to do list
$ ls -l my\ to\ do\ list
-rw-r--r-- 1 jason users 73 Jun 22 22:16 my to do list
$ ls -lb
total 4
-rw-r--r-- 1 jason users 73 Jun 22 22:16 my\ to\ do\ list| File Type | Symbol |
|---|---|
| Regular file | - |
| Block special file | b |
| Character special file | c |
| Directory | d |
| Symbolic link | l |
| FIFO (named pipe) | p |
| Socket | s |
| Some other file type | ? |
| Permission | Symbol |
|---|---|
| Read | r |
| Write | w |
| Execute | x |
| Permission | File Meaning | Directory Meaning |
|---|---|---|
| Read | Read Allows a file to be read. | Allows file names in the directory to be read. |
| Write | Allows a file to be modified. | Allows entries within the directory to be modified. |
| Execute | Allows the execution of a file. | Allows access to the contents and metadata of entries within the directory. |
All files in Linux are owned by a user and a group. This allows for unique permissions to be applied across three sets of users: the user owner, the group owner, and others. When modifying permissions, these sets can be represented by a single letter: u for the user owner, g for the group owner, and o for others. In addition, the letter a can represent all three of these permissions groups.
| Category | Symbol |
|---|---|
| User | u |
| Group | g |
| Other | o |
| All | a |
Every user is a member of at least one group, called their primary group. However, users can be members of many groups. Groups are used to organize users into logical sets.
To determine what groups you are a member of, run the groups command. If you supply another user’s ID as an argument to the groups command, you will see the list of groups to which that user belongs. You can also run id -Gn [user] to get the same result.
$ groups
users sales
$ id -Gn
users sales
$ groups tracy
users projectx dba
$ groups john
users sales manager$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.dataThe first
character in the permissions string is the type. The next three characters represent the permissions available to the user, also known as the owner of the file. The next three characters represent the permissions available to the group. The last three characters represent the permissions available to all others.
In this case, order has meaning. Permission groups will always be displayed in this order: user, group, and others. Within these three permission groups, permission types will always be in this order: read, write, and execute. If a particular permission type is not granted, then a hyphen (-) will take its place
$ ls -l sales.data.selinux
-rw-r--r--. 1 jason users 1040 Jun 14 09:31 sales.data.selinux
$ ls -l sales.data.acl
-rw-r--r--+ 1 jason users 1040 Jun 14 09:31 sales.data.aclIf there happens to be an additional character at the end of the permissions string, an alternative access control method has been applied. A trailing period (.) means that a SELinux (SecurityEnhanced Linux) security context has been applied to the file or directory. A trailing plus sign (+) means that ACLs (Access Control Lists) are in use. SELinux and ACLs are beyond the scope of this book. However, you will be pleased to know that the use of these is rare.
Permissions are also known as modes. The command chmod, which is short for "change mode," is used to change permissions. The format of the chmod command is chmod mode file. There are two ways to specify the mode. The first way is called symbolic mode. The symbolic mode
format is chmod user_category operator permission. Here is a table view of the chmod command using the symbolic mode format.The second way to specify modes with the chmod command is called octal mode, which will discussed later.
| Symbol | Description |
|---|---|
| chmod | The change mode command itself. |
| ugoa | The user category. Use one or more of u for user, g for group, o for other, a for all. |
| +-= | One of +, -, or =. Use + to add permissions, - to subtract them, or = to explicitly set them. |
| rwx | The actual permissions. Use one or more of r for read, w for write, and x for execute. |
$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod g+w sales.data
$ ls -l sales.data
-rw-rw-r-- 1 jason users 10400 Jun 14 09:31 sales.data$ ls -l sales.data
-rw-rw-r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod g-w sales.data
$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod g+wx sales.data
$ ls -l sales.data
-rw-rwxr-- 1 jason users 10400 Jun 14 09:31 sales.data$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod ug+wx sales.data
$ ls -l sales.data
-rwxrwxr-- 1 jason users 10400 Jun 14 09:31 sales.data$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod u=rwx,g+x sales.data37
$ ls -l sales.data
-rwxr-xr-- 1 jason users 10400 Jun 14 09:31 sales.data$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod a=r sales.data
$ ls -l sales.data
-r--r--r-- 1 jason users 10400 Jun 14 09:31 sales.data$ ls -l sales.data
-rw-r--r-- 1 jason users 10400 Jun 14 09:31 sales.data
$ chmod u=rwx,g=rx,o= sales.data
$ ls -l sales.data
-rwxr-x--- 1 jason users 10400 Jun 14 09:31 sales.dataThe second way to specify modes with the chmod command is called octal mode.Some Linux users never move beyond symbolic permissions. However, experienced Linux users find using octal mode quicker and easier in the long term because there are only a few commonly used permissions which can be readily memorized and recalled.
Octal mode permissions are based on the binary numeral system, also known as the base-2 numeral system. Each permission type is treated as a bit that is either set to off, represented by a zero (0), or on, represented by a one (1). In permissions, order has meaning. Permissions are always in read, write, and execute order. If r, w, and x are all set to off, the binary representation is 000. If they are all set to on, the binary representation is 111. To represent read and write permissions while omitting execute permissions, the binary number is 110.
| / | Read | Write | Execute |
|---|---|---|---|
| Binary and decimal value for off | 0 | 0 | 0 |
| Binary value for on. | 1 | 1 | 1 |
| Decimal value for on. | 4 | 2 | 1 |
| Permissions | String | Binary | Octal |
|---|---|---|---|
| No permissions | --- | 000 | 0 |
| Execute only | --x | 001 | 1 |
| Write only | -w- | 010 | 2 |
| Write and Execute | -wx | 011 | 3 |
| Read only | r-- | 100 | 4 |
| Read and Execute | r-x | 101 | 5 |
| Read and Write | rw- | 110 | 6 |
| Read, Write, and Execute | rwx | 111 | 7 |
| / | User | Group | Other |
|---|---|---|---|
| Symbolic | rwx | rw- | r-- |
| Binary | 111 | 110 | 100 |
| Decimal | 7 | 6 | 4 |
| Meaning | Octal | Symbolic |
|---|---|---|
| Allows the file‘s owner full control over the file. No others on the system have access. | 700 | -rwx------ |
| Allows everyone on the system to execute the file but only the owner can edit it. | 755 | -rwxr-xr-x |
| Allows a group of people to modify the file and let others read it. | 664 | -rw-rw-r-- |
| Allows a group of people to modify the file and not let others read it. | 660 | -rw-rw---- |
| Allows everyone on the system to read the file but only the owner can edit it. | 644 | -rw-r--r-- |
When a file is created, it is set to the current user‘s primary group. You can override this behavior by using the newgrp command, but remember by default a new file will inherit your default group. In the following example, Jason‘s primary group is users. The group owner of the file could be set to the Linux group named sales by using the chgrp command. The format of the chgrp command is chgrp GROUP FILE.
$ nano sales.report
$ ls -l sales.report
-rw-r--r-- 1 jason users 6 Jun 15 20:41 sales.report
$ chgrp sales sales.report
$ ls -l sales.report
-rw-r--r-- 1 jason sales 6 Jun 15 20:41 sales.report
$ chmod 664 sales.report
$ ls -l sales.report
-rw-rw-r-- 1 jason sales 6 Jun 15 20:41 sales.reportDirectory permissions usually only contain 0s, 5s, and 7s. Common directory permissions include 755, 700, 770, and 750. Incorrect directory permissions can prevent file access and file execution. If you determine that a file‘s permissions have been set correctly, look at the parent directory’s permissions. Work your way toward the root of the file system by running ls - ld . in the current directory, moving up to the parent directory with cd .., and repeating those two steps until you find the problem.
$ ls -ld directory/ drwxr-xr-x 2 jason users 4096 Sep 29 22:02 directory/ $ ls -l directory/ total 0 -rwxr--r-- 1 jason users 0 Sep 29 22:02 testprog $ chmod 400 directory $ ls -ld directory/ dr-------- 2 jason users 4096 Sep 29 22:02 directory/ $ ls -l directory/ ls: cannot access directory/testprog: Permission denied total 0 -????????? ? ? ? ? ? testprog $ directory/testprog -su: directory/testprog: Permission denied $ chmod 500 directory/ $ ls -ld directory/ dr-x------ 2 jason users 4096 Sep 29 22:02 directory/ $ ls -l directory/ total 0 -rwxr--r-- 1 jason users 0 Sep 29 22:02 testprog $ directory/testprog This program ran successfully.
The file creation mask, also known as the umask, determines the default permissions of new files and directories. The umask is typically set by the system administrator; however, an individual user may override the setting by including a umask statement in his or her account‘s initialization files.
If no mask is applied, new directories receive 777 (rwxrwxrwx) permissions and new files receive 666 (rw-rw-rw-) permissions. When the umask is applied to these base permissions, it disables, or masks, certain permissions. For example, a umask of 000 will disable, or mask, zero bits. In this case, new directories receive 777 permissions and new files receive 666 permissions. At the other extreme, a umask of 777 disables all permissions bits. New files and directories receive 000 permissions in this instance.
| / | Directory | File |
|---|---|---|
| Base Permission | 777 | 666 |
| Subtract the umask | -022 | -022 |
| Creation Permission | 755 | 644 |
Using a umask of 002 is ideal for working with members of your group. When files or directories are created, the permissions allow members of the group to manipulate those files and directories.
By using 007, no permissions are granted to users outside of the group.
Linux--Introduction and Basic commands(Part one)
标签:discuss last cin compute service surf lib hardware lag
原文地址:https://www.cnblogs.com/jclian91/p/9648110.html