标签:修改 ide sizeof signed space get play 消息 new
原文:如何实现.net程序的进程注入 如何实现.net程序的进程注入
周银辉
进程注入比较常见,比如用IDE调试程序以及一些Spy程序,如果仅仅为了与调试器通讯,可以使用.net提供的Debugger接口(在EnvDTE.dll的EnvDTE命名空间下).但无论出于什么目的,进程注入都是比较好玩的事情,所以不妨一试 . 进程注入的方法貌似很多(比如像特洛伊一样乔装打扮让目标进程误认为你的程序集合法而加载到目标进程),这里提到的仅是其中的一种或某些方法的结合.
大致原理是这样的:
如果还没明白的话,那就看代码吧(这需要一点点C++/CLI知识,但我已经为每句加上了注释,应该蛮好懂的,关于C++/CLI可以点击这里了解更多.)
#include "stdafx.h" #include "Injector.h" #include <vcclr.h> using namespace ManagedInjector; //defines a new window message that is guaranteed to be unique throughout the system. //The message value can be used when sending or posting messages. static unsigned int WM_GOBABYGO = ::RegisterWindowMessage(L"Injector_GOBABYGO!"); static HHOOK _messageHookHandle; //----------------------------------------------------------------------------- //Spying Process functions follow //----------------------------------------------------------------------------- void Injector::Launch(System::IntPtr windowHandle, System::Reflection::Assembly^ assembly, System::String^ className, System::String^ methodName) { System::String^ assemblyClassAndMethod = assembly->Location + "$" + className + "$" + methodName; //convert String to local wchar_t* or char* pin_ptr<const wchar_t> acmLocal = PtrToStringChars(assemblyClassAndMethod); //Maps the specified executable module into the address space of the calling process. HINSTANCE hinstDLL = ::LoadLibrary((LPCTSTR) _T("ManagedInjector.dll")); if (hinstDLL) { DWORD processID = 0; //get the process id and thread id DWORD threadID = ::GetWindowThreadProcessId((HWND)windowHandle.ToPointer(), &processID); if (processID) { //get the target process object (handle) HANDLE hProcess = ::OpenProcess(PROCESS_ALL_ACCESS, FALSE, processID); if (hProcess) { int buffLen = (assemblyClassAndMethod->Length + 1) * sizeof(wchar_t); //Allocates physical storage in memory or in the paging file on disk for the specified reserved memory pages. //The function initializes the memory to zero. //The return value is the base address of the allocated region of pages. void* acmRemote = ::VirtualAllocEx(hProcess, NULL, buffLen, MEM_COMMIT, PAGE_READWRITE); if (acmRemote) { //copies the data(the assemblyClassAndMethod string) //from the specified buffer in the current process //to the address range of the target process ::WriteProcessMemory(hProcess, acmRemote, acmLocal, buffLen, NULL); //Retrieves the address of MessageHookProc method from the hintsDLL HOOKPROC procAddress = (HOOKPROC)GetProcAddress(hinstDLL, "MessageHookProc"); //install a hook procedure to the target thread(before the system sends the messages to the destination window procedure) _messageHookHandle = ::SetWindowsHookEx(WH_CALLWNDPROC, procAddress, hinstDLL, threadID); if (_messageHookHandle) { //send our custom message to the target window of the target process ::SendMessage((HWND)windowHandle.ToPointer(), WM_GOBABYGO, (WPARAM)acmRemote, 0); //removes the hook procedure installed in a hook chain by the SetWindowsHookEx function. ::UnhookWindowsHookEx(_messageHookHandle); } //removes a hook procedure installed in a hook chain by the SetWindowsHookEx function. ::VirtualFreeEx(hProcess, acmRemote, buffLen, MEM_RELEASE); } ::CloseHandle(hProcess); } } //Decrements the reference count of the loaded DLL ::FreeLibrary(hinstDLL); } } __declspec( dllexport ) // The procedure for hooking, this will be called back after hooked int __stdcall MessageHookProc(int nCode, WPARAM wparam, LPARAM lparam) { //HC_ACTION: indicate that there are argments in wparam and lparam if (nCode == HC_ACTION) { CWPSTRUCT* msg = (CWPSTRUCT*)lparam; //when the target window received our custom message if (msg != NULL && msg->message == WM_GOBABYGO) { //get the argument passed by the message //actually, the argument is the base address (a pointer) //of the assemblyClassAndMethod string in the target process memory wchar_t* acmRemote = (wchar_t*)msg->wParam; //gcnew: creates an instance of a managed type (reference or value type) on the garbage collected heap System::String^ acmLocal = gcnew System::String(acmRemote); //split the string into substring array with $. Under this context: //acmSplit[0]:the assembly‘s location //acmSplit[1]:className; //acmSplit[2]:methodName //we use these infomation to reflect the method in the source assembly, and invoke it in the target process cli::array<System::String^>^ acmSplit = acmLocal->Split(‘$‘); //refect the method, and invoke it System::Reflection::Assembly^ assembly = System::Reflection::Assembly::LoadFile(acmSplit[0]); if (assembly != nullptr) { System::Type^ type = assembly->GetType(acmSplit[1]); if (type != nullptr) { System::Reflection::MethodInfo^ methodInfo = type->GetMethod(acmSplit[2], System::Reflection::BindingFlags::Static | System::Reflection::BindingFlags::Public); if (methodInfo != nullptr) { methodInfo->Invoke(nullptr, nullptr); } } } } } return CallNextHookEx(_messageHookHandle, nCode, wparam, lparam); }
解决方案中的InjectorDemo就是我们上述的源进程,它会利用Injector将下面这段代码注入到Target进程中并执行:
public static void DoSomethingEvie()
{
vartargetWindow = Application.Current.MainWindow;
if(targetWindow != null)
{
varlb = newLabel{Content = "haha, i caught you :)"};
targetWindow.Content = lb;
}
}
也就是说InjectorDemo进程会将InjectTargetApp进程的主窗口的内容修改成"haha, i caught you"这样的一个Label.
运行程序:
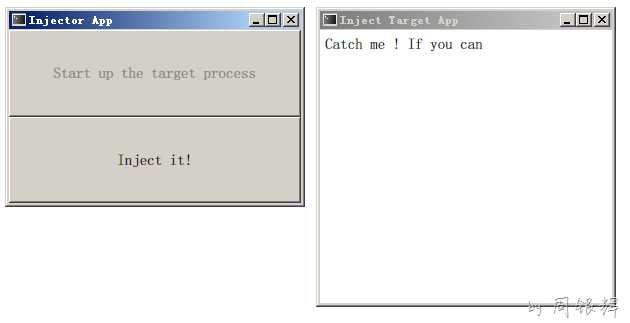
上面的两个窗口分别处于不同的进程中, 点击 "Inject it" 按钮, 其辉调用如下代码:
ManagedInjector.Injector.Launch(targetProcess.MainWindowHandle, typeof(InjectorWindow).Assembly, typeof(InjectorWindow).FullName, "DoSomethingEvie");
然后:
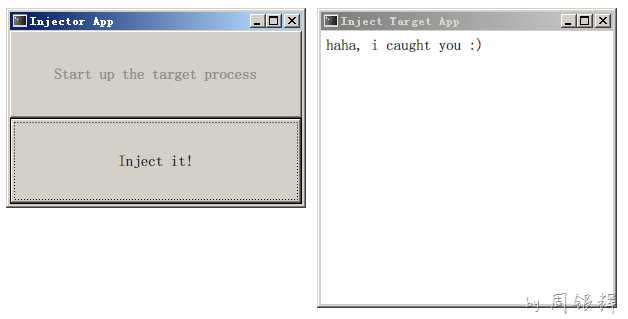
点击这里下载Demo
仅供参考(日志内容仅仅记录了一种存在性,并非特定问题的解决方案,讨论其意义性是毫无意义的,谢谢)
标签:修改 ide sizeof signed space get play 消息 new
原文地址:https://www.cnblogs.com/lonelyxmas/p/10761768.html