标签:dev ane rate ble div tac nss targe load
Installing Kioptrix: Level 1
Download the vm machine form https://www.vulnhub.com/entry/kioptrix-level-1-1,22/.
In the Kali Linux:
Find the devices in the intranet using the following command:
netdiscover -i eth0
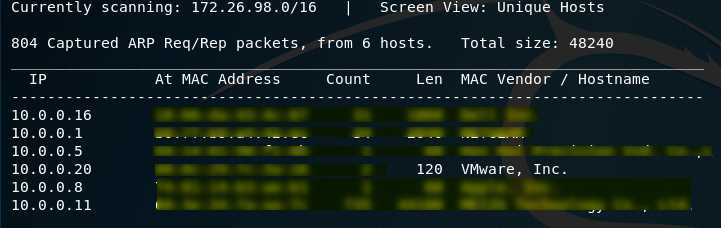
Scan the target kioptrix vm through nmap
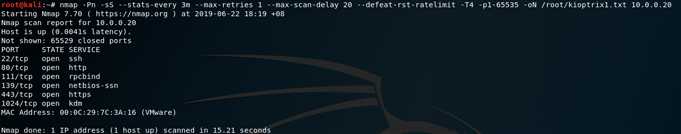
nmap -Pn -sS --stats-every 3m --max-retries 1 --max-scan-delay 20 --defeat-rst-ratelimit -T4 -p1-65535 -oN /root/kioptrix1.txt 10.0.0.20
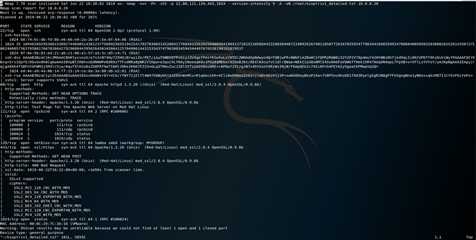
nmap -nvv -Pn -sSV -p 22,80,111,139,443,1024 --version-intensity 9 -A -oN /root/kioptrix1_detailed.txt 10.0.0.20
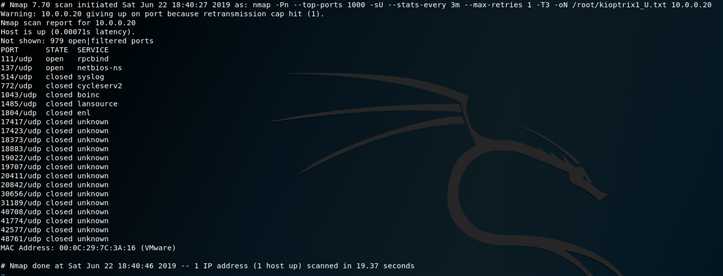
nmap -Pn --top-ports 1000 -sU --stats-every 3m --max-retries 1 -T3 -oN /root/kioptrix1_U.txt 10.0.0.20
SSH Enumeration
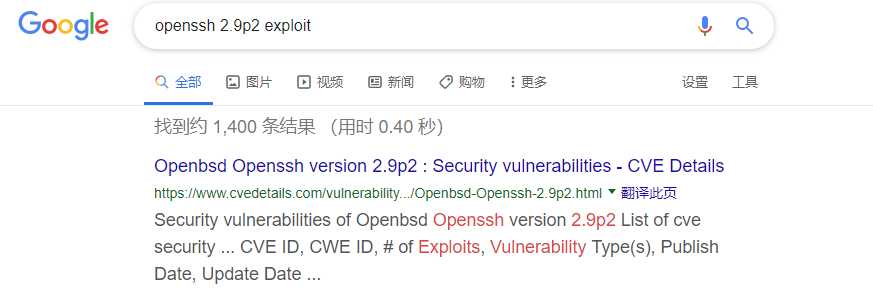
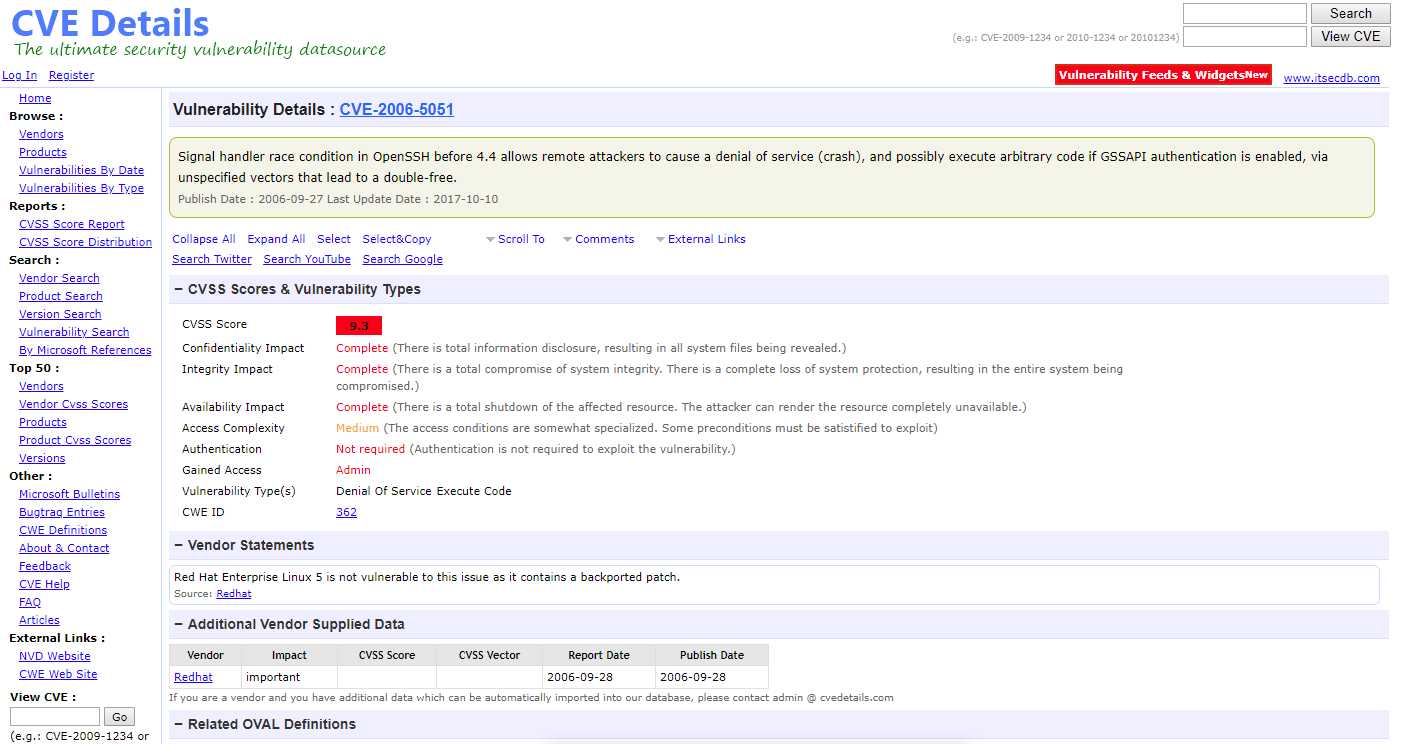
1. Search vulnarabilites through Internet.
Key words: openssh 2.9p2 exploit
2.Search exploitable information through Kali
searchsploit openssh

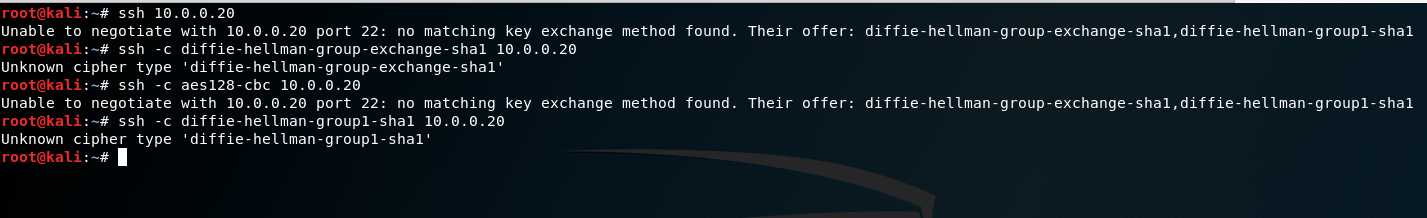
3. Try to exploit the target host - such as brute force attack
OSCP Learning Notes - Enumeration(1)
标签:dev ane rate ble div tac nss targe load
原文地址:https://www.cnblogs.com/keepmoving1113/p/11070025.html