标签:war 文件 安装 uid col 系统 soft 新建 连接
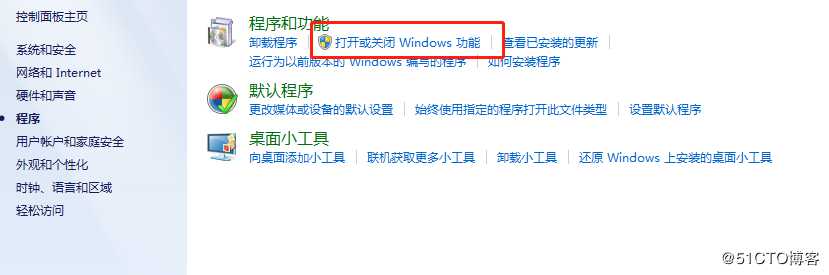
一.搭建NFS服务NFS服务端:
IP:192.168.43.156
NFS客户端:
IP:192.168.43.185
两台服务器都关闭防火墙及SElinux
systemctl stop firewalld.service
setenforce 02.1 yum安装NFS和RPC服务
yum install nfs-utils rpcbind -y2.2 动RPC服务和NFS服务
systemctl start rpcbind
systemctl start nfs
ps -ef|grep rpc
ps -ef|grep nfs
lsof -i:111
rpcinfo -p localhost2.3 设置开机自启动并检查
systemctl enable rpcbind
systemctl enable nfs
systemctl list-unit-files --type=service|grep "enabled"|egrep "rpcbind|nfs"2.4 创建共享目录
mkdir /data
chown -R nfsnobody.nfsnobody /data
ls -ld /data2.5 配置共享/data目录
cat>>/etc/exports<<EOF
#NFS server share directories
/data 192.168.43.156(rw,sync)
EOF
cat /etc/exports2.7 平滑重启NFS服务并检查服务
systemctl reload nfs
cat /var/lib/nfs/etab2.8 本地查看挂载目录
showmount -e 192.168.43.1563.1 安装NFS和RPC服务并检查
yum install nfs-utils rpcbind -y3.2 启动RPC服务(不需要启动NFS服务,原因是不安装NFS服务的话没有showmount这个命令)
systemctl start rpcbind
ps -ef|grep rpc
lsof -i:1113.3 设置开机自启动并检查
systemctl enable rpcbind
systemctl list-unit-files --type=service|grep "enabled"|grep "rpcbind"3.4 检查服务端的NFS挂载目录是否OK
showmount -e 192.168.43.1563.5 挂载设置开机自动挂载
mount -t nfs 192.168.43.156:/data /mnt
echo "mount -t nfs 192.168.43.156:/data /mnt">>/etc/rc.local3.6 查看是否挂载成功
df -h more /etc/exports 1.2 然后执行:
exportfs -av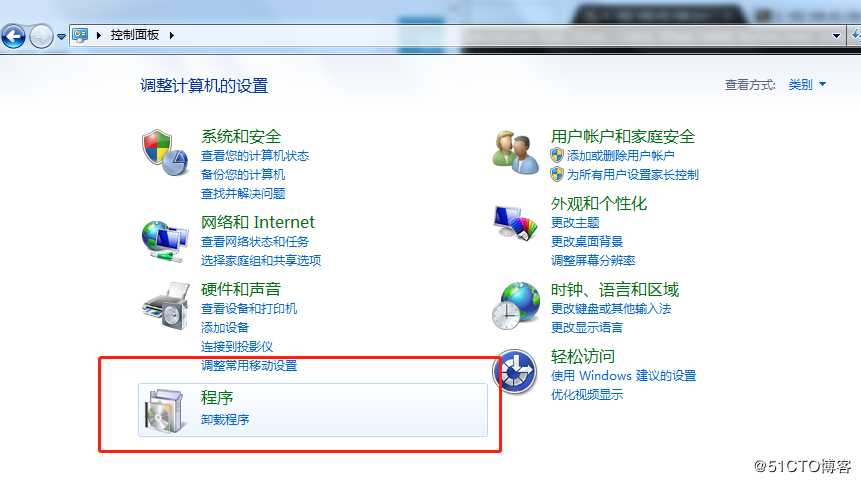
mount \\192.168.43.156\data x:\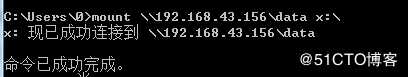
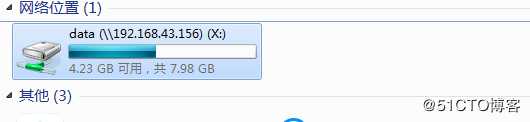
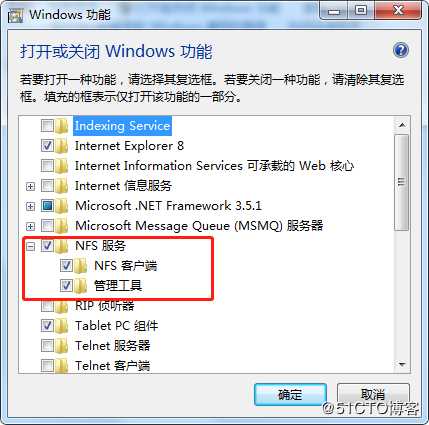
Win7 NFS客户端使用mount命令挂载NFS服务之后,文件系统对Win7只读,无法写入文件,无法新建文件夹,此时使用mount命令可以查看到如下状态: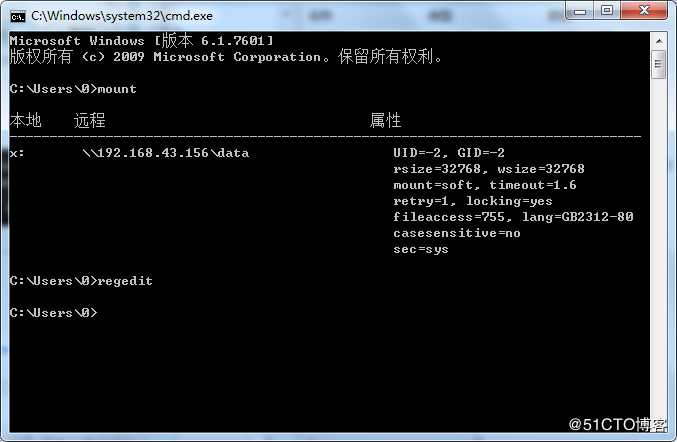
UID=-2在存储设备上共享出来的NFS文件系统归属于root权限,无法修改该所属用户,Windows通过UID=-2的用户去写,写不进去。
regedit
```(打开注册表)
让Win7在挂载NFS的时候将UID和GID改成0即可,
:打开注册表:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ClientForNFS\CurrentVersion\Default,增加两项:AnonymousUid,AnonymousGid,如图:

#### 5.重启计算机
#### 6..在cmd内输入mount 查看属性

#### 7.在x:盘下放置***程序

#### 8.用电脑自带的杀毒软件进行查杀

#### 9.查杀成功
标签:war 文件 安装 uid col 系统 soft 新建 连接
原文地址:https://blog.51cto.com/14375810/2427482