标签:pack 硬件配置 ports Kubernete com enforce namespace key文件 wget
kubeadm是官方社区推出的一个用于快速部署kubernetes集群的工具。在开始之前,部署Kubernetes集群机器需要满足以下几个条件:
关闭防火墙:
systemctl stop firewalld
systemctl disable firewalld
关闭selinux:
sed -i ‘s/enforcing/disabled/‘ /etc/selinux/config
setenforce 0
关闭swap:
swapoff -a $ 临时
sed -i ‘/ swap / s/^\(.*\)$/#\1/g‘ /etc/fstab $ 永久
添加主机名与IP对应关系(记得设置主机名):
$ cat >> /etc/hosts<<EOF
9.110.187.120 k8s-master
9.110.187.125 k8s-node1
9.110.187.126 k8s-node2
EOF
将桥接的IPv4流量传递到iptables的链:
$ cat > /etc/sysctl.d/k8s.conf << EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
EOF
$ sysctl --systemKubernetes默认CRI(容器运行时)为Docker,因此先安装Docker。
$ wget https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo -O /etc/yum.repos.d/docker-ce.repo
$ yum -y install docker-ce-18.06.1.ce-3.el7
$ systemctl enable docker && systemctl start docker
$ docker --version
Docker version 18.06.1-ce, build e68fc7a
$ yum list docker-ce --showduplicates | sort -r$ cat > /etc/yum.repos.d/kubernetes.repo << EOF
[kubernetes]
name=Kubernetes
baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64
enabled=1
gpgcheck=0
repo_gpgcheck=0
gpgkey=https://mirrors.aliyun.com/kubernetes/yum/doc/yum-key.gpg https://mirrors.aliyun.com/kubernetes/yum/doc/rpm-package-key.gpg
EOF由于版本更新频繁,这里指定版本号部署:
yum install -y kubelet-1.16.2 kubeadm-1.16.2 kubectl-1.16.2 bash-completion wget
systemctl enable kubelet在9.110.187.120(Master)执行。
$ kubeadm init --apiserver-advertise-address=9.110.187.120 --image-repository registry.aliyuncs.com/google_containers --kubernetes-version v1.16.2 --service-cidr=10.1.0.0/16 --pod-network-cidr=10.244.0.0/16由于默认拉取镜像地址k8s.gcr.io国内无法访问,这里指定阿里云镜像仓库地址。
使用kubectl工具:
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
$ kubectl get nodes$ kubectl apply -f https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml如果下载失败,可以改成这个镜像地址:lizhenliang/flannel:v0.11.0-amd64
在9.110.187.125/126(Node)执行。
向集群添加新节点,执行在kubeadm init输出的kubeadm join命令:
$ kubeadm join 9.110.187.120:6443 --token esce21.q6hetwm8si29qxwn --discovery-token-ca-cert-hash sha256:00603a05805807501d7181c3d60b478788408cfe6cedefedb1f97569708be9c5在Kubernetes集群中创建一个pod,验证是否正常运行:
kubectl create deployment nginx --image=nginx.1.16
kubectl expose deployment nginx --port=80 --type=NodePort
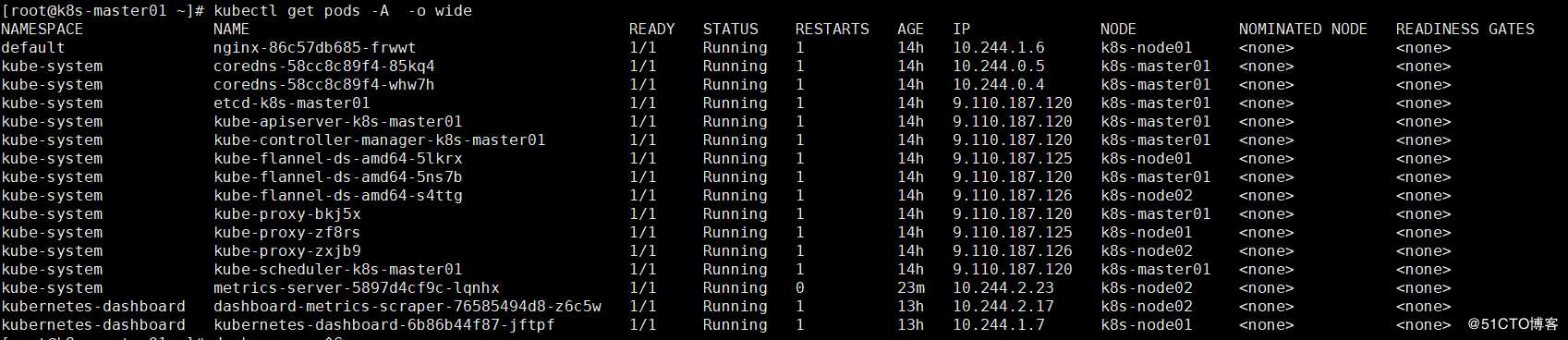
kubectl get pods -A -o wide
kubectl describe pod nginx-86c57db685-frwwt访问地址:http://NodeIP:Port
$ wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta5/aio/deploy/recommended.yaml修改recommended.yaml文件内容(vi recommended.yaml):
---
#增加直接访问端口
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort #增加
ports:
- port: 443
targetPort: 8443
nodePort: 30001 #增加
selector:
k8s-app: kubernetes-dashboard
---
#因为自动生成的证书很多浏览器无法使用,所以我们自己创建,注释掉kubernetes-dashboard-certs对象声明
#apiVersion: v1
#kind: Secret
#metadata:
# labels:
# k8s-app: kubernetes-dashboard
# name: kubernetes-dashboard-certs
# namespace: kubernetes-dashboard
#type: Opaque
---创建证书
mkdir dashboard-certs
cd dashboard-certs/
#创建命名空间
kubectl create namespace kubernetes-dashboard #yaml里会自动创建,可以不用单独创建
# 创建key文件
openssl genrsa -out dashboard.key 2048
#证书请求
openssl req -days 36000 -new -out dashboard.csr -key dashboard.key -subj ‘/CN=dashboard-cert‘
#自签证书
openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt
#创建kubernetes-dashboard-certs对象
kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard部署Dashboard
涉及到的两个镜像可以先下载下来
#安装
kubectl create -f ~/recommended.yaml
#检查结果
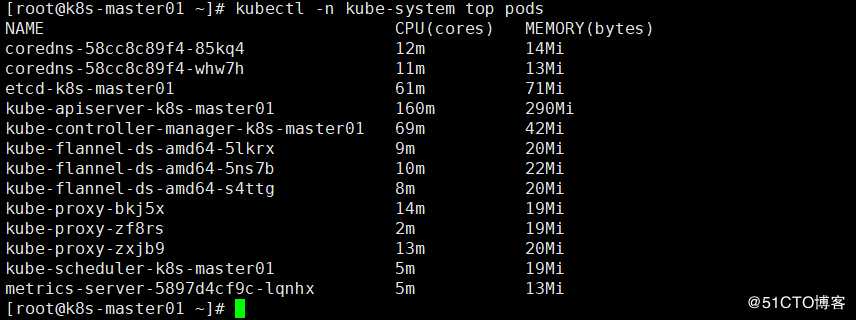
kubectl get pods -A -o wide
kubectl get service -n kubernetes-dashboard -o widecat >> dashboard-admin.yaml<<EOF
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: dashboard-admin
namespace: kubernetes-dashboard
EOF
kubectl create -f dashboard-admin.yaml
为用户分配权限:
cat >>dashboard-admin-bind-cluster-role.yaml<<EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: dashboard-admin-bind-cluster-role
labels:
k8s-app: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kubernetes-dashboard
EOF
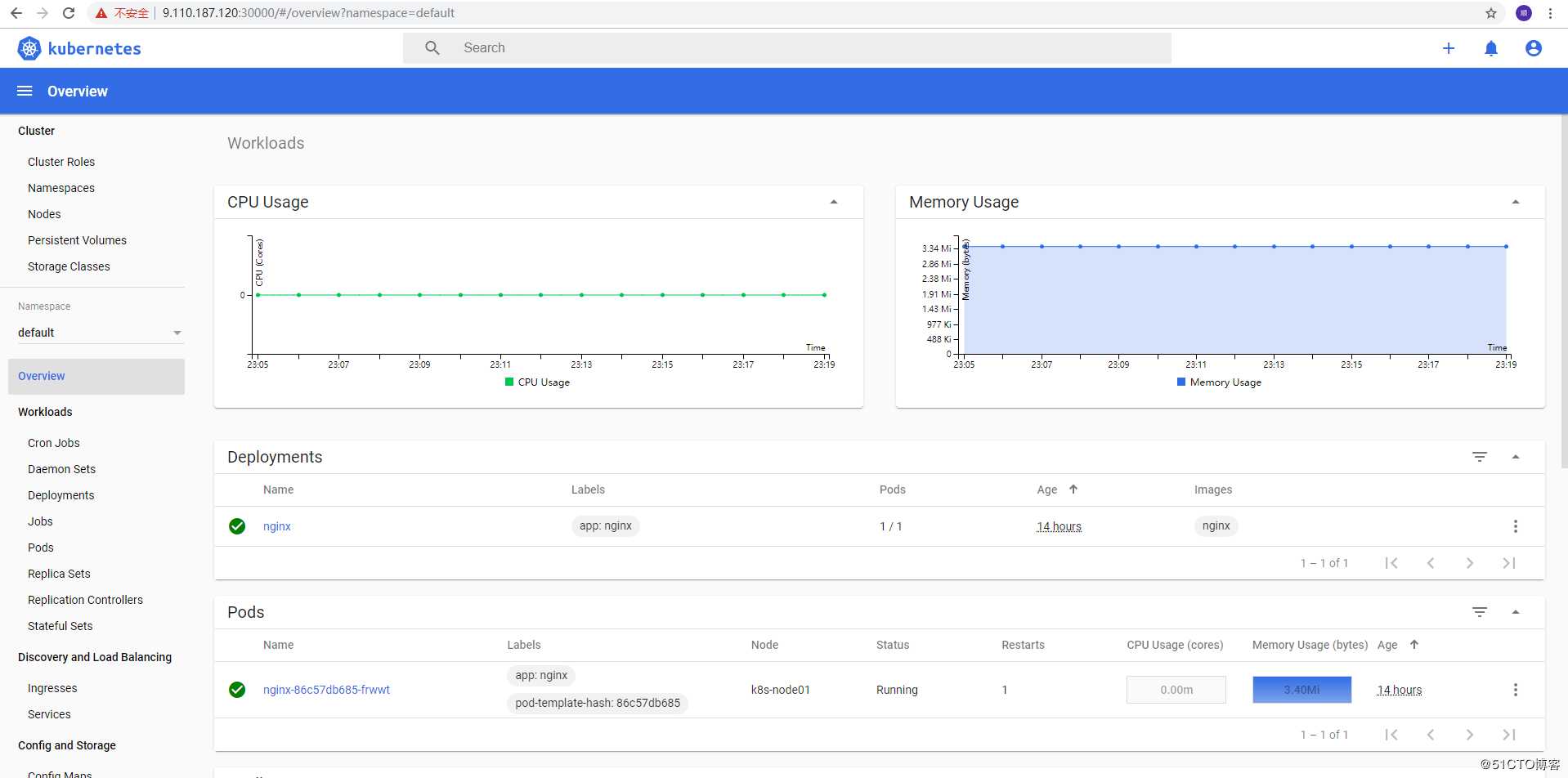
kubectl create -f dashboard-admin-bind-cluster-role.yaml访问地址:http://NodeIP:30001
创建service account并绑定默认cluster-admin管理员集群角色:
$ kubectl create serviceaccount dashboard-admin -n kube-system
$ kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
$ kubectl describe secrets -n kube-system $(kubectl -n kube-system get secret | awk ‘/dashboard-admin/{print $1}‘)使用输出的token登录Dashboard。
在Node1/Node2上下载镜像文件:
docker pull bluersw/metrics-server-amd64:v0.3.6
docker tag bluersw/metrics-server-amd64:v0.3.6 k8s.gcr.io/metrics-server-amd64:v0.3.6 在Master上执行安装:
git clone https://github.com/kubernetes-incubator/metrics-server.git
cd metrics-server/deploy/1.8+/
修改metrics-server-deployment.yaml
image: k8s.gcr.io/metrics-server-amd64 #在image下添加一下内容
command:
- /metrics-server
- --metric-resolution=30s
- --kubelet-insecure-tls
- --kubelet-preferred-address-types=InternalIP
查找runAsNonRoot: true 修改为runAsNonRoot: false
kubectl create -f .
如果不能获取不到镜像可以更改image: mirrorgooglecontainers/metrics-server-amd64:v0.3.6
Kubernetes V1.16.2部署Dashboard V2.0(beta5)
标签:pack 硬件配置 ports Kubernete com enforce namespace key文件 wget
原文地址:https://blog.51cto.com/shunzi115/2447601