标签:ef6 认证通过 cout apr cas min 方便 pre provision
Kubernetes API的每个请求都会经过多阶段的访问控制之后才会被接受,这包括认证、授权以及准入控制(Admission Control)等
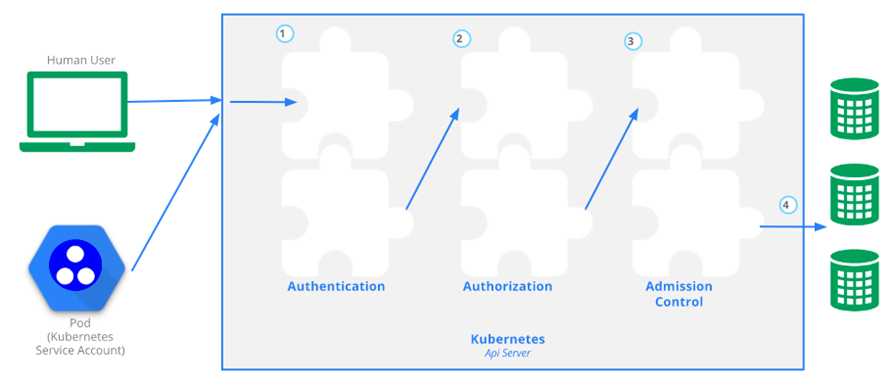
在集群开启TLS后,客户端发往Kubernetes的所有API请求都需要进行认证,以验证用户的合法性。
Kubernetes支持多种认证机制,并支持同时开启多个认证插件(只要有一个认证通过即可)。如果认证成功,则用户的username会被传入授权模块做进一步授权验证;而对于认证失败的请求则返回HTTP 401。
所有的真书位置都在master节点
[root@docker-server1 secrets]# cd /etc/kubernetes/pki/
[root@docker-server1 pki]# ll
APIserver是基于一个证书文件/root/.kube/config这个文件包含有
[root@docker-server1 secrets]# cat /root/.kube/config
apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ERXdPVEU0TVRnME0xb1hEVE13TURFd05qRTRNVGcwTTFvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTWVBCkhoY3ZBdXFvTDZFOUFCYWdjeFkwT1ZuYXlJVWprY3JtZTBYbU1UcDJ1Nnl1VXhWZzNTVGJQVDlNM1VHSnlSc0YKWG1JK3FrKzg5VnhJcmgzRUE5Y2JNVm1YaE1hVHhGTHZVQVg4WGNwcmkzN0hvTDJ6amlrSUkwcjBLazhOWkUyWQpOTEowWTZNK2JDWDBEdkFiWXNRZmJOZ0VRT2VnMTBZTjd2VUpBeDE3MCtVeWxvdlBPYnVxUDc2dWZNcW80MW4yCkdXdm1FcW1YUVR0MzFnL0haeHhnYUZUUW5VSnR6QTY2VW50RmE1Y2ZpbVNIMVo3K0JyRkNzTmRkMHpCTmlCOUQKR3NlQTVCb2h5U1FVNndESEl3bllENEdIbzJNNmM0V0ZobTMwRUpjdk9UbnI0VFlOZFN0eHRKUjRuOHY1Um5oOApRNmlRQ2FkZC9uWU5qNmpDaUxVQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFKME9uN3BaRkZLdGZlNUkvKzZUK0RkRnBwbmcKN0VwQmh0Ui9xVldjUWtjaG1UVksxNTloSEpTaUplSnJnWkFnVElEOGY4dENyMklPOVFQTTdtNjRBMkJMOWNvTgpBYzYrUUJ3Uk9jODNDejBqZHdVVXdudjBCU3ZQKzlWckNIQndpbjdpYi9WYW1MdDA1YTNFcEVFcW1TSDJHQ0xhCnBzVVAzSWFDejJwcm5YVEdJN2lJZUhmN2VLazB3eGt0ZVFaMGF4MXZtK0FMS1NreWZ3dzkxRWJ5MnN6c3VqaUYKbkFzb0RKTk43UEZFcDFWYmhpOGN2SDVaWFcvWHZvOTBqU3BQUUZWZmlqdWd2SlhpMjREa2h1QVJxYnhoaGI0ZAowNlBtTk9xQVgrdDlsTFc2c2QyUVRQTEllUEtKdmtuN1JqdGFiUmVLSE1xUHZLRGludEtlUTNkYjFQOD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= server: https://192.168.132.131:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJWWhZNzlUWVMzSVF3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeE1Ea3hPREU0TkROYUZ3MHlNVEF4TURneE9ERTRORFphTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUcHRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXMyeklaaDhyYXd6NzJmcWkKUkd4T1hpN0JaZHdyM1FsdjJ4VkRJYWd4aUN2M1ZQOENWNkphSXZwaEU2bjcrY3ozVk5LR3Z2MnpzYW9VdjVDRwowVXUvVG1HWU9hbnQxeDY1K0tCanVsYjNsaS9aVGJwZDl4UWZNMVAxaFhiQ0QwWGNGL1RnWGRvTlljUzBvWnhZClo5aFVEVWc5emdPM3pGVUVUMVlaQW90MEhBVzRmbXU5eWRUaTkxelJkdVdRR2Ezd3MwOWplT0dXTUFEQ3pnRnIKakFNaFYvLzNmYWd5M2hpdTUxOU5mZlBUZ3Z1VUlOV1NEcTNVbUJmUC9yd3hoelF2WDZrUDlPeUdqMG9xY3JWYQpsUTJQMC9lYldnVnQxVGZvK1JvS1gxVlMwNnNuS1MwUGVORnM4TTlMRmJISTQrczlXcUhTZWFrcVVzVkM2Nk8xCmxRSmNhUUlEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFLb0lpNkxQa0wzZjZxYWllVmR6OGE2cndDYWVreTRqQnFyYwovSFdPVkJGL2IyeVJHckJSTlNFd2piR2VCKzJtb3BZK1M3OTlneWRVcUp2RlZYOHNnWllBWFFURllmL0pQdTVmCmtXTS9Qc21Tc3FYQlRGZHhGR0N5RjFjc2VnT1pIQ05xTFNLdk5SN3NhTEsxV25pRzZYUThTTEVKSTY4aHNWaUoKQ2Y3MGxMOUQ3K3lkbzZRVHN0enY4ZmI4aVU1dEhnY0ZyRDdOZzJ2dlpraXdWWjhvWnVTTGw1Q0RIK3E1cmpOdAowSDJ4c1hrMzhTMk9MQkJOUDYrcSt4UVZ1RW5OR1pYdVc3SmRndEFzdVZJRXFpMVdKWGVHM1pLWGpOSE5nRWtvCmFBRWQzVHpqVmR6ZVVZcE1SV3F2TGNSeTNKQVNHT0UyaHdDWVZmWVE3ZStNMWx5M0dDMD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBczJ6SVpoOHJhd3o3MmZxaVJHeE9YaTdCWmR3cjNRbHYyeFZESWFneGlDdjNWUDhDClY2SmFJdnBoRTZuNytjejNWTktHdnYyenNhb1V2NUNHMFV1L1RtR1lPYW50MXg2NStLQmp1bGIzbGkvWlRicGQKOXhRZk0xUDFoWGJDRDBYY0YvVGdYZG9OWWNTMG9aeFlaOWhVRFVnOXpnTzN6RlVFVDFZWkFvdDBIQVc0Zm11OQp5ZFRpOTF6UmR1V1FHYTN3czA5amVPR1dNQURDemdGcmpBTWhWLy8zZmFneTNoaXU1MTlOZmZQVGd2dVVJTldTCkRxM1VtQmZQL3J3eGh6UXZYNmtQOU95R2owb3FjclZhbFEyUDAvZWJXZ1Z0MVRmbytSb0tYMVZTMDZzbktTMFAKZU5GczhNOUxGYkhJNCtzOVdxSFNlYWtxVXNWQzY2TzFsUUpjYVFJREFRQUJBb0lCQUZlS1FMQUtqeDE0eFR3UgoyNiswZy92UnBnd3pncmNpVG8rK2JQVno0VTdGM0xOOGc4RUw5aHhRdXFKa2NncnJwTlNlcnAxcW5JeVhKZTVjCjdsb1pNZXBsRldjMDhGVGZxZTZUR25Va3owRlljUlpLVW1RbFRoKzEyL2xVK3RPR3l4NXBIRHJPRTI5YkVLSTAKN0xFbHk4UjdOYVJaRGdqRWhnakxRZ0tLMVlpQnRMeXMyRTZqRXovQVI2RERtK0pCbUlDTjBpbWE0NlJyTngyNQorRmxSMHRzcjR0WTVLcVBJNU9YdjlzbE5TQUgyYmIwU1Z0MG1SaGxRYTFMTTZuOG4yOEZIZVdLR0x4YzNDeW52CjNBbTl1RkRvQlF4QzdhVnR5L2Vpd2daV0pjNzN6ZUtFOE12TDkyRnYzQ1BBWFlEZGRRM1B1dVFHMGFrTFgwWWMKMnlsZHF4MENnWUVBM3BZdmp0TGN2NStiUlgxL1RLZ0NkenFmZmhFeko3clQ3VDVFeFExakN4THI1bWRXaTBuSgp0bXd4c2VhVVdMbi9MamdEaWZxTi9adCtIdzN5Sk9nd1c1ZlB6TGhJU2tqTWxUdm5pZis0RGk1MDJKR3VEUE5WCkVYd2szdUFJS0tURW5tc1NhZlpZN3VLc2FJYzU2bkdkL1UxQ0ZMcHpON3dseEdHRWNldDYzVHNDZ1lFQXpsdnQKeDBGL0Y2ZXh1endiRGpZbHdZYktvWnJJN2lHSThTQ2lLRFdyeEVjZlBsQkt6M05zS2Zvb2tPaW84VXF2QzBaUApFTlZpNGRhbmthUnluRkVjZXErYW1iSko5Y0xWcWlhTkU0OFJLaUlWM2oveWE1bVI3M1NUelBGUkxza3ZKT0RECnVtUmVlb21JNVdUUzI2UjRJZUhzLzNqaTJGNTFlWlJzMWEvQVlxc0NnWUVBbmNjSnFRelJDMGZnc1c1VzZRaUMKenU4UUZUV3Q5RENiZnFUUDdIb2p4YnJBMnM1UGEyWi9oRDdITHhxSjl5Ykl1b05jQnRkREJRek9ac2JrNk1KcApYTk9NcWNuSy9GVUVKNWlSOUtEK1g1Y1FubDhOYUFLb1B6K25oeEI0MkE2TGpOdks3cTkvdEwyYWhuR3NYUUh5CmdwWGNESU5wbm8xUW5CYWY0bnlQMS9jQ2dZQkFRTk42dFdRVFEzM05wTnR2dzJCaUw4d3NJWHZxMmJwQUNqOHoKY2ZLM3ZNVjNxNXgvbDVyWVB6SWVYTE10M21rK2czZmU3L0pJQzRSRmp3UzRzM0RBcXFqaXJtYmxCUE51ZFc1Nwo1cElib2wxWXhHU0JLR0lPUXlnNktmRnpOZVZlQURZeGRVc05zSUZWbTkwajBzUXRHS0dvc2tVL3hibWlUNXJMCnRsdWEzUUtCZ0czM0QvQlE0UENTY3I3bVhNdVp2Q0w3bmpHalVVUEY5eFc3QmEraDMzZ2ZJd1NERmxNNXNaZDQKOXZ0anQwVmdBN1NSTHZ5U3RrSGRkOFJqcDczSU5kYUFZOUh3WkthQTBUd21oSDZqVXRZd0U2SmZrTCt0ZUN5NApySUhPVkY5RzFET2JWU1JyeW5zckNtb1owcGg1YVVGRExhcFU4NGRhdnk4UjJaZVVjZC8rCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
[root@docker-server1 pki]# cat sa.key |base64 -w 0
[root@docker-server1 pki]# cat /root/.kube/config
本地端的Apiserver,control managent和Schedule监听的是本地的非安全端口,则不要任何认证,就拥有最大的权限,但是这个端口之只能运行再本地
node的kubelet和Apiserver的认证:apiserver再启动的时候会生成一个token文件,kubelet第一次连接的时候是基于token的,默认的用户是bootstrp-kubelet带着token访问apiserver,apiserver就会签发证书,再kubelet.kubeconfig文件定义
apiserver和kubeproxy的认证:
认证插件
X509证书
静态Token文件
引导Token
静态密码文件
Service Account
OpenID
OpenStack Keystone密码
匿名请求
Kubernetes认证帐户
Service Account
默认的认证是基于证书的双向认证,再创建一个K8S集群,会默认创建一系列证书
授权主要是用于对集群资源的访问控制,通过检查请求包含的相关属性值,与相对应的访问策略相比较,API请求必须满足某些策略才能被处理。跟认证类似,Kubernetes也支持多种授权机制,并支持同时开启多个授权插件(只要有一个验证通过即可)。如果授权成功,则用户的请求会发送到准入控制模块做进一步的请求验证;对于授权失败的请求则返回HTTP 403。
授权依据roles
[root@docker-server1 secrets]# kubectl get clusterroles
NAME AGE admin 8d cluster-admin 8d edit 8d flannel 8d kubernetes-dashboard 8d system:aggregate-to-admin 8d system:aggregate-to-edit 8d system:aggregate-to-view 8d system:auth-delegator 8d system:basic-user 8d system:certificates.k8s.io:certificatesigningrequests:nodeclient 8d system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 8d system:controller:attachdetach-controller 8d system:controller:certificate-controller 8d system:controller:clusterrole-aggregation-controller 8d system:controller:cronjob-controller 8d system:controller:daemon-set-controller 8d system:controller:deployment-controller 8d system:controller:disruption-controller 8d system:controller:endpoint-controller 8d system:controller:expand-controller 8d system:controller:generic-garbage-collector 8d system:controller:horizontal-pod-autoscaler 8d system:controller:job-controller 8d system:controller:namespace-controller 8d system:controller:node-controller 8d system:controller:persistent-volume-binder 8d system:controller:pod-garbage-collector 8d system:controller:pv-protection-controller 8d system:controller:pvc-protection-controller 8d system:controller:replicaset-controller 8d system:controller:replication-controller 8d system:controller:resourcequota-controller 8d system:controller:route-controller 8d system:controller:service-account-controller 8d system:controller:service-controller 8d system:controller:statefulset-controller 8d system:controller:ttl-controller 8d system:coredns 8d system:discovery 8d system:heapster 8d system:kube-aggregator 8d system:kube-controller-manager 8d system:kube-dns 8d system:kube-scheduler 8d system:kubelet-api-admin 8d system:node 8d system:node-bootstrapper 8d system:node-problem-detector 8d system:node-proxier 8d system:persistent-volume-provisioner 8d system:public-info-viewer 8d system:volume-scheduler 8d view 8d
以上为内置权限
cluster-admin是超级管理员权限
权限组:
roles:namespce级别
clusterroles:集群级别
授权操作:为某一账户绑定全权限,rolebongding 和clusterroleboding,就会行成新的资源
这种授权方式成为rabc授权
[root@docker-server1 pki]# kubectl get sa
NAME SECRETS AGE default 1 8d
[root@docker-server1 pki]# kubectl get sa default -o yaml
apiVersion: v1 kind: ServiceAccount metadata: creationTimestamp: "2020-01-09T18:19:18Z" name: default namespace: default resourceVersion: "359" selfLink: /api/v1/namespaces/default/serviceaccounts/default uid: 47332a49-bbac-46b8-9fd7-18943e710021 secrets: - name: default-token-bwbrn
[root@docker-server1 pki]# vi /yamls/ingress/nginx-controller.yaml
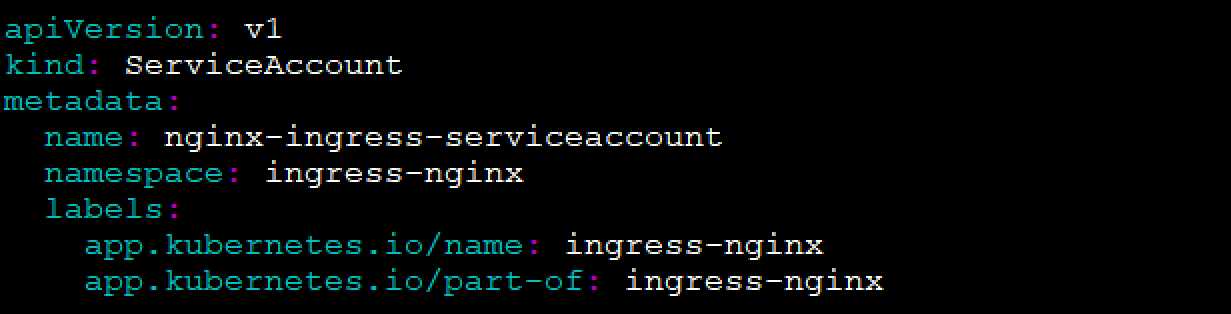
apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRole metadata: name: nginx-ingress-clusterrole labels: app.kubernetes.io/name: ingress-nginx app.kubernetes.io/part-of: ingress-nginx rules: - apiGroups: - "" resources: - configmaps - endpoints - nodes - pods - secrets verbs: - list - watch - apiGroups: - "" resources: - nodes verbs: - get - apiGroups: - "" resources: - services verbs: - get - list - watch - apiGroups: - "" resources: - events verbs: - create - patch - apiGroups: - "extensions" - "networking.k8s.io" resources: - ingresses verbs: - get - list - watch - apiGroups: - "extensions" - "networking.k8s.io" resources: - ingresses/status verbs: - update
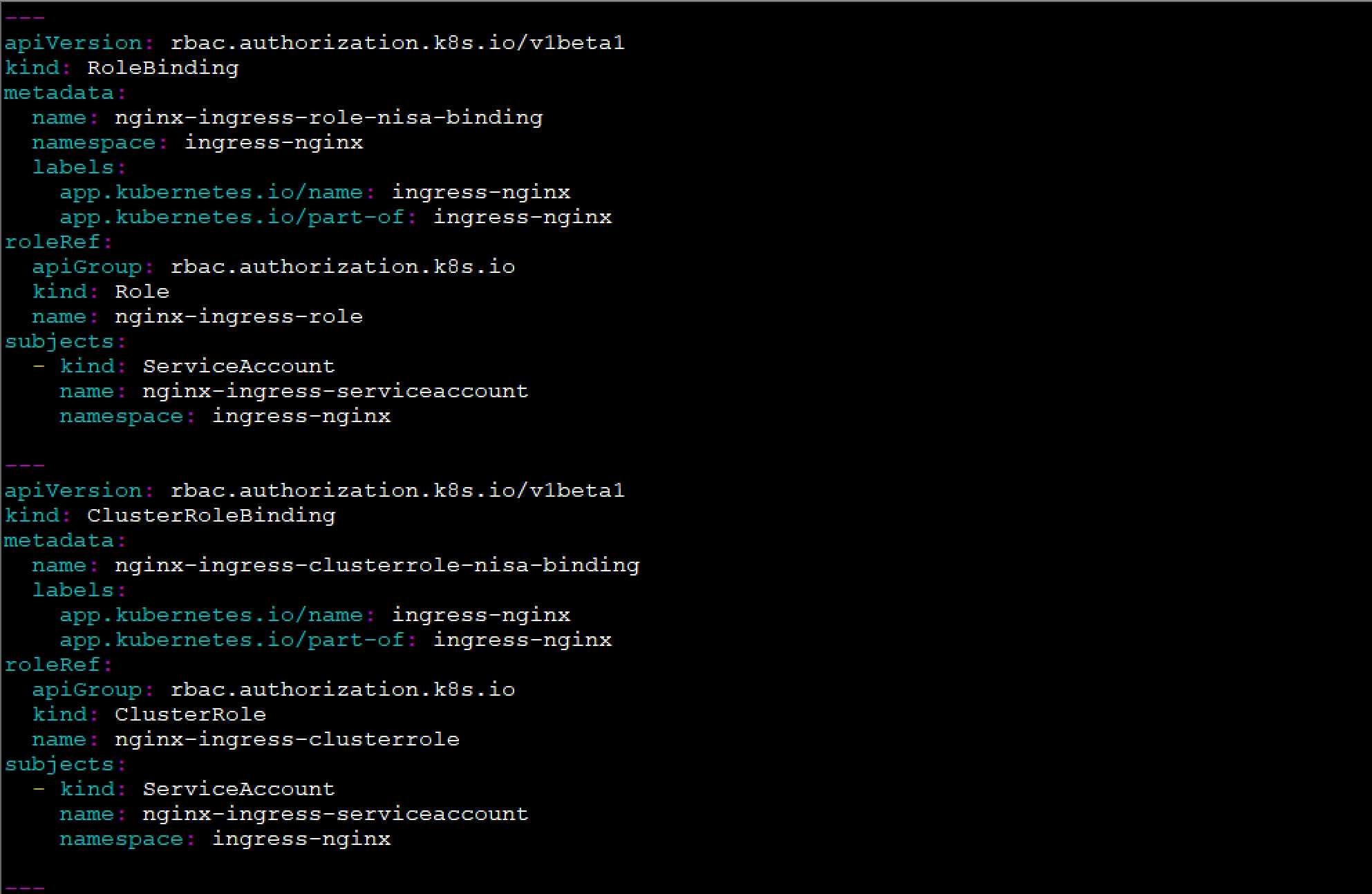
[root@docker-server1 pki]# kubectl get clusterrole -o yaml cluster-admin
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: annotations: rbac.authorization.kubernetes.io/autoupdate: "true" creationTimestamp: "2020-01-09T18:18:59Z" labels: kubernetes.io/bootstrapping: rbac-defaults name: cluster-admin resourceVersion: "45" selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/cluster-admin uid: 277dddfd-c72d-4450-97e1-244c56ad837a rules: - apiGroups: - ‘*‘ resources: - ‘*‘ verbs: - ‘*‘ - nonResourceURLs: - ‘*‘ verbs: - ‘*‘
[root@docker-server1 pki]# mkdir /yamls/sa
[root@docker-server1 pki]# cd /yamls/sa
[root@docker-server1 sa]# vi test-sa.taml
apiVersion: v1
kind: ServiceAccount
metadata:
name: test-sa
[root@docker-server1 sa]# kubectl apply -f test-sa.taml
serviceaccount/test-sa created
[root@docker-server1 sa]# kubectl get sa
NAME SECRETS AGE default 1 8d test-sa 1 12s
让这个sa变成超级管理员
[root@docker-server1 sa]# vim test-sa-role.yaml
apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: test-sa-role-binding namespace: ingress-nginx roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: test-sa
namespace: default
[root@docker-server1 sa]# kubectl apply -f test-sa-role.yaml
clusterrolebinding.rbac.authorization.k8s.io/test-sa-role-binding created
[root@docker-server1 sa]# kubectl get clusterrolebinding |grep test
![]()
[root@docker-server1 sa]# kubectl describe clusterrolebinding test-sa-role-binding
Name: test-sa-role-binding Labels: <none> Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"rbac.authorization.k8s.io/v1beta1","kind":"ClusterRoleBinding","metadata":{"annotations":{},"name":"test-sa-role-binding"},... Role: Kind: ClusterRole Name: cluster-admin Subjects: Kind Name Namespace ---- ---- --------- ServiceAccount test-sa default
[root@docker-server1 sa]# kubectl describe clusterrole cluster-admin
Name: cluster-admin Labels: kubernetes.io/bootstrapping=rbac-defaults Annotations: rbac.authorization.kubernetes.io/autoupdate: true PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- *.* [] [] [*] [*] [] [*]
[root@docker-server1 sa]# kubectl describe sa test-sa
Name: test-sa Namespace: default Labels: <none> Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"name":"test-sa","namespace":"default"}} Image pull secrets: <none> Mountable secrets: test-sa-token-rn7db Tokens: test-sa-token-rn7db #有自己的token Events: <none>
[root@docker-server1 sa]# kubectl get secret
NAME TYPE DATA AGE default-token-bwbrn kubernetes.io/service-account-token 3 8d hub-secret kubernetes.io/dockerconfigjson 1 164m test-sa-token-rn7db kubernetes.io/service-account-token 3 13m
[root@docker-server1 sa]# kubectl describe secret test-sa-token-rn7db
Name: test-sa-token-rn7db Namespace: default Labels: <none> Annotations: kubernetes.io/service-account.name: test-sa kubernetes.io/service-account.uid: 6e767195-c019-43b0-ad6a-81b35e86b9f7 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 7 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6Inl0U2JtWkVaSkNjbFpCMGpkVktHTGtTUTFvZFc3LVUxeUllRkRyalcxYncifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InRlc3Qtc2EtdG9rZW4tcm43ZGIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoidGVzdC1zYSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjZlNzY3MTk1LWMwMTktNDNiMC1hZDZhLTgxYjM1ZTg2YjlmNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OnRlc3Qtc2EifQ.RydJTCW3yocxk3_3ThwuWz4zSzymQScvOc7gw1-GsATHfilDK7-CPrEYSkaA90uNFIBfQJovxzpbEtPmge7MAoweCp52Sx8cdA8ppxxgBGpIMC-EiV4unsazxZprrqbGuQ45UCumZYVu70X4UjuPaScf9fHRfJtESDbDEWjeIknhNFcLSw8TCxVpoprC1teF6HflFXG90sR3V_ag2lAXFMeobrnhcTPL5NCxKbwYzsJkiCDIlOsEppCS8d1AZ77pQcTzPLtpe7GtJIhQN-ZBlBrhlEqRCNsEPnG-Ar6eGu5jb5gvOf8NXm_OPnRRyYh8OEHJ_LcdAjq92w2BXmdTYw
可以收用这个token访问dashboard
[root@docker-server1 sa]# kubectl get pods -n kubernetes-dashboard -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES dashboard-metrics-scraper-76585494d8-95j9v 1/1 Running 1 8d 10.244.2.13 192.168.132.133 <none> <none> kubernetes-dashboard-b7ffbc8cb-nz5gf 1/1 Running 0 4d20h 10.244.0.11 192.168.132.131 <none> <none>
[root@docker-server1 sa]# kubectl get svc -n kubernetes-dashboard -o wide
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR dashboard-metrics-scraper ClusterIP 10.96.93.119 <none> 8000/TCP 8d k8s-app=dashboard-metrics-scraper kubernetes-dashboard NodePort 10.96.87.98 <none> 443:32443/TCP 8d k8s-app=kubernetes-dashboard
https://192.168.132.131:32443/
高级
接收风险,输入token
登入
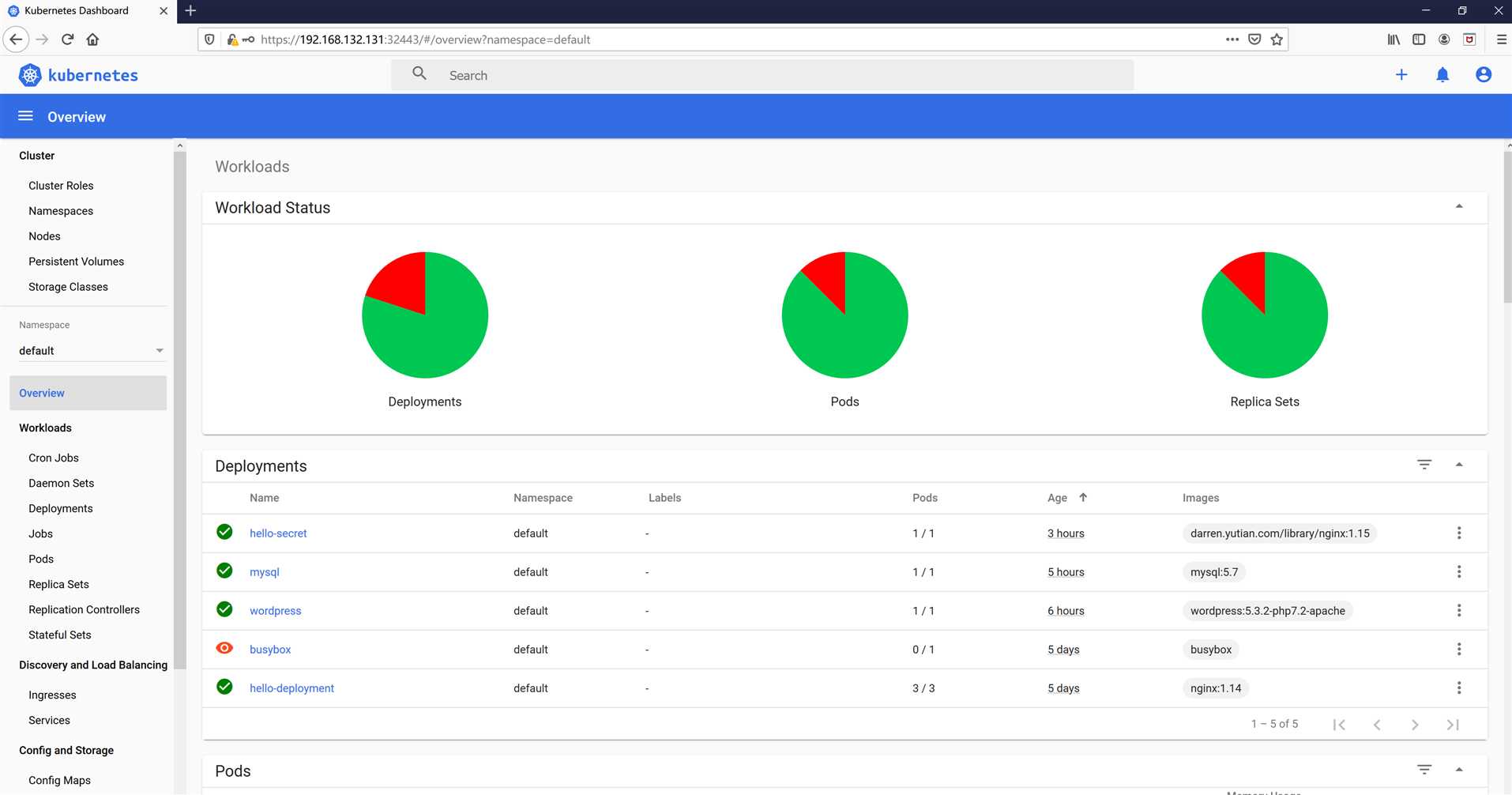
得到界面
直接访问被拒绝
[root@docker-server1 sa]# curl -k https://192.168.132.131:6443
{ "kind": "Status", "apiVersion": "v1", "metadata": { }, "status": "Failure", "message": "forbidden: User \"system:anonymous\" cannot get path \"/\"", "reason": "Forbidden", "details": { }, "code": 403 }
带token访问
[[root@docker-server1 sa]# curl -k --header "Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6Inl0U2JtWkVaSkNjbFpCMGpkVtHTGtTUTFvZFc3LVUxeUllRkRyalcxYncifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InRlc3Qtc2EtdG9rZW4tcm43ZGIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoidGVzdC1zYSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjZlNzY3MTk1LWMwMTktNDNiMC1hZDZhLTgxYjM1ZTg2YjlmNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OnRlc3Qtc2EifQ.RydJTCW3yocxk3_3ThwuWz4zSzymQScvOc7gw1-GsATHfilDK7-CPrEYSkaA90uNFIBfQJovxzpbEtPmge7MAoweCp52Sx8cdA8ppxxgBGpIMC-EiV4unsazxZprrqbGuQ45UCumZYVu70X4UjuPaScf9fHRfJtESDbDEWjeIknhNFcLSw8TCxVpoprC1teF6HflFXG90sR3V_ag2lAXFMeobrnhcTPL5NCxKbwYzsJkiCDIlOsEppCS8d1AZ77pQcTzPLtpe7GtJIhQN-ZBlBrhlEqRCNsEPnG-Ar6eGu5jb5gvOf8NXm_OPnRRyYh8OEHJ_LcdAjq92w2BXmdTYw" https://192.168.132.131:6443
{ "paths": [ "/api", "/api/v1", "/apis", "/apis/", "/apis/admissionregistration.k8s.io", "/apis/admissionregistration.k8s.io/v1", "/apis/admissionregistration.k8s.io/v1beta1", "/apis/apiextensions.k8s.io", "/apis/apiextensions.k8s.io/v1", "/apis/apiextensions.k8s.io/v1beta1", "/apis/apiregistration.k8s.io", "/apis/apiregistration.k8s.io/v1", "/apis/apiregistration.k8s.io/v1beta1", "/apis/apps", "/apis/apps/v1", "/apis/authentication.k8s.io", "/apis/authentication.k8s.io/v1", "/apis/authentication.k8s.io/v1beta1", "/apis/authorization.k8s.io", "/apis/authorization.k8s.io/v1", "/apis/authorization.k8s.io/v1beta1", "/apis/autoscaling", "/apis/autoscaling/v1", "/apis/autoscaling/v2beta1", "/apis/autoscaling/v2beta2", "/apis/batch", "/apis/batch/v1", "/apis/batch/v1beta1", "/apis/certificates.k8s.io", "/apis/certificates.k8s.io/v1beta1", "/apis/coordination.k8s.io", "/apis/coordination.k8s.io/v1", "/apis/coordination.k8s.io/v1beta1", "/apis/discovery.k8s.io", "/apis/discovery.k8s.io/v1beta1", "/apis/events.k8s.io", "/apis/events.k8s.io/v1beta1", "/apis/extensions", "/apis/extensions/v1beta1", "/apis/networking.k8s.io", "/apis/networking.k8s.io/v1", "/apis/networking.k8s.io/v1beta1", "/apis/node.k8s.io", "/apis/node.k8s.io/v1beta1", "/apis/policy", "/apis/policy/v1beta1", "/apis/rbac.authorization.k8s.io", "/apis/rbac.authorization.k8s.io/v1", "/apis/rbac.authorization.k8s.io/v1beta1", "/apis/scheduling.k8s.io", "/apis/scheduling.k8s.io/v1", "/apis/scheduling.k8s.io/v1beta1", "/apis/storage.k8s.io", "/apis/storage.k8s.io/v1", "/apis/storage.k8s.io/v1beta1", "/healthz", "/healthz/autoregister-completion", "/healthz/etcd", "/healthz/log", "/healthz/ping", "/healthz/poststarthook/apiservice-openapi-controller", "/healthz/poststarthook/apiservice-registration-controller", "/healthz/poststarthook/apiservice-status-available-controller", "/healthz/poststarthook/bootstrap-controller", "/healthz/poststarthook/crd-informer-synced", "/healthz/poststarthook/generic-apiserver-start-informers", "/healthz/poststarthook/kube-apiserver-autoregistration", "/healthz/poststarthook/rbac/bootstrap-roles", "/healthz/poststarthook/scheduling/bootstrap-system-priority-classes", "/healthz/poststarthook/start-apiextensions-controllers", "/healthz/poststarthook/start-apiextensions-informers", "/healthz/poststarthook/start-cluster-authentication-info-controller", "/healthz/poststarthook/start-kube-aggregator-informers", "/healthz/poststarthook/start-kube-apiserver-admission-initializer", "/livez", "/livez/autoregister-completion", "/livez/etcd", "/livez/log", "/livez/ping", "/livez/poststarthook/apiservice-openapi-controller", "/livez/poststarthook/apiservice-registration-controller", "/livez/poststarthook/apiservice-status-available-controller", "/livez/poststarthook/bootstrap-controller", "/livez/poststarthook/crd-informer-synced", "/livez/poststarthook/generic-apiserver-start-informers", "/livez/poststarthook/kube-apiserver-autoregistration", "/livez/poststarthook/rbac/bootstrap-roles", "/livez/poststarthook/scheduling/bootstrap-system-priority-classes", "/livez/poststarthook/start-apiextensions-controllers", "/livez/poststarthook/start-apiextensions-informers", "/livez/poststarthook/start-cluster-authentication-info-controller", "/livez/poststarthook/start-kube-aggregator-informers", "/livez/poststarthook/start-kube-apiserver-admission-initializer", "/logs", "/metrics", "/openapi/v2", "/readyz", "/readyz/autoregister-completion", "/readyz/etcd", "/readyz/log", "/readyz/ping", "/readyz/poststarthook/apiservice-openapi-controller", "/readyz/poststarthook/apiservice-registration-controller", "/readyz/poststarthook/apiservice-status-available-controller", "/readyz/poststarthook/bootstrap-controller", "/readyz/poststarthook/crd-informer-synced", "/readyz/poststarthook/generic-apiserver-start-informers", "/readyz/poststarthook/kube-apiserver-autoregistration", "/readyz/poststarthook/rbac/bootstrap-roles", "/readyz/poststarthook/scheduling/bootstrap-system-priority-classes", "/readyz/poststarthook/start-apiextensions-controllers", "/readyz/poststarthook/start-apiextensions-informers", "/readyz/poststarthook/start-cluster-authentication-info-controller", "/readyz/poststarthook/start-kube-aggregator-informers", "/readyz/poststarthook/start-kube-apiserver-admission-initializer", "/readyz/shutdown", "/version" ] }
实验完成
博主声明:本文的内容来源主要来自誉天教育晏威老师,由本人实验完成操作验证,需要的博友请联系誉天教育(http://www.yutianedu.com/),获得官方同意或者晏老师(https://www.cnblogs.com/breezey/)本人同意即可转载,谢谢!
标签:ef6 认证通过 cout apr cas min 方便 pre provision
原文地址:https://www.cnblogs.com/zyxnhr/p/12209894.html