标签:card pen com 环境 delete 系统 star car toc
一、防火墙的概念
什么是防火墙?防火墙是一台或一组设备,用以在网络间实施访问控制策略;事实上一个防火墙能够包含OSI模型中的很多层,并且可能会涉及进行数据包过滤的设备,它可以实施数据包检查和过滤,在更高的层次中对某应用程序实现某一策略,或做更多类似的事情。防火墙的功能主要是隔离功能,工作在网络或主机边缘,对进出网络或主机的数据包基于一定的规则检查,并在匹配某规则定义的行为进行处理的一组功能组件,基本上的实现都是默认情况下关闭所有的访问,只开放允许访问的策略;防火墙分主机防火墙、网络防火墙、硬件防火墙、软件防火墙、网络层防火墙、应用层防火墙等;主机防火墙指定的是针对服务当前主机做的访问策略的防火墙;网络防火墙指服务范围为防火墙一侧的局域网;硬件防火墙指在专用硬件级别实现部分功能的防火墙,另一部分功能基于软件实现;软件防火墙指运行于通用硬件平台之上的防火墙应用软件;网络层防火墙指OSI模型下四层的防火墙,主要针对OSI模型下四层的网络报文的访问策略控制;应用层防火墙/代理服务器指OSI模型中的应用层的防火墙,它主要在应用层进行操作,针对应用层的程序数据报文进行访问策略控制;
二、网络型防火墙和应用层防火墙的优缺点
网络层防火墙主要是包过滤,网络层对数据包进行选择,选择的依据是系统内设置的过滤逻辑,被称为访问控制列表(ACL),通过检查数据流中每个数据的源地址,目标地址,所用端口和协议状态等因素,或他们的组合来取定是否允许该数据包通过;优点对用户来说透明,处理速度快且易于维护;缺点无法检查应用层数据,如病毒等;
应用层防火墙我们又称代理服务型防火墙,它将所有跨越防火墙的网络通信链路分为两段;内外网用户的访问都是通过代理服务器上的“链路”来实现,这种防火墙优点是在应用层对数据进行检查,比较安全,确定是增加防火墙的负载。
现实生产环境中所使用的防火墙一般都是二者结合体,即现检查网络数据,通过之后在送到应用层去检查。
三、iptables简介
先来说说内核组件netfilter,它是Linux2.4以后的内核版本引入的一个子系统,它作为一个通用的、抽象的框架,提供一整套的hook(勾子)函数的管理机制,使得诸如数据包过滤、网络地址转换和基于协议类型的连接追踪成为了可能;它在内核中选取了五个位置放置了五个hook(勾子)函数分别是INPUT、OUTPUT、FORWARD、PREROUTING、POSTROUTING,而这五个勾子函数向用户开放,用户可以通过一个命令工具(iptables)向其写入规则;从上面的介绍不难理解,iptables只是管理netfilter上规则的一个用户空间的工具,真正实现防火墙的功能是netfilter,我们知道内核空间的功能,用户是没有办法直接使用,必须通过用户空间的软件去调用才可以使用。这也不难说明了iptables它是一个工具,而不是一个服务。
四、iptables的组成以及数据包的传输过程
iptables由五个表和五个链以及一些规则组成,五个表分别是filter、nat、mangle、raw、security,这五张表每张表都有不同的作用,filter表,主要是过滤报文策略的定义,根据预定义的规则过滤符合条件的数据包才允许或拒绝通行。nat表是地址转换规则表,它上面主要定义一些地址转换规则。mangle表是修改数据标记位规则表,raw是关闭NAT表上启用的连接跟踪机制,加快封包穿越防火墙速度,security用于强制访问控制(MAC)网络规则,有Linux安全模块(如selinux)实现;他们的优先级由高到低的顺序为security--->raw---->mangle---->nat---->filter
五个内置的链(chain)就是我们上面说的五个勾子函数INPUT、OUTPUT、FORWARD、PREROUTING、POSTROUTING,netfilter表和链对应关系如下图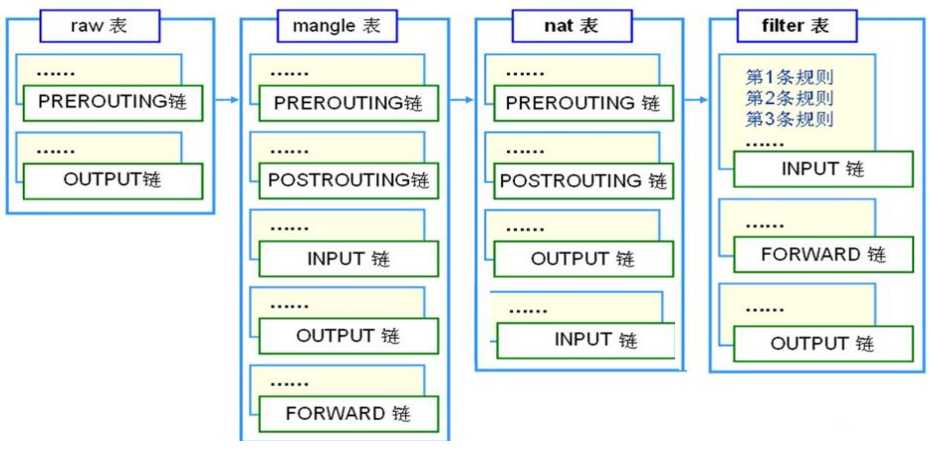
上图没有画出securiyt表所工作的链,它和filter表一样,都工作在INPUT、FORWARD、OUTPUT链上。上图主要是说明了五个表的工作位置,了解了表和链的对应关系,我们在来看看数据包过滤匹配流程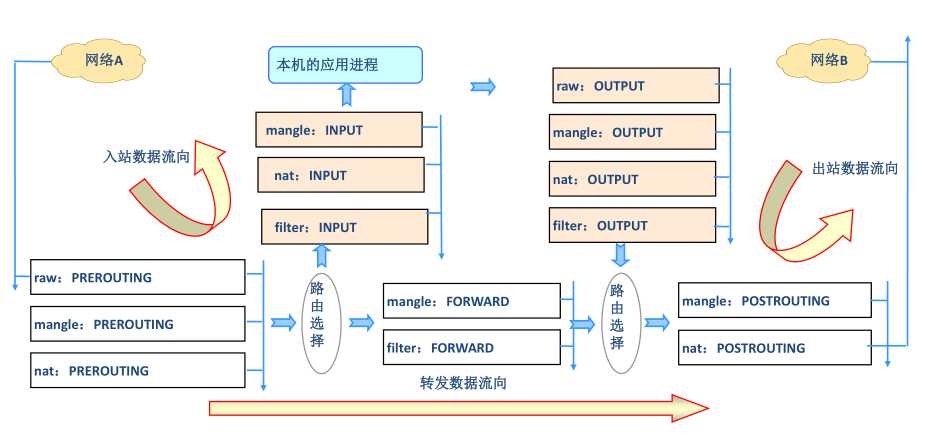
如上图所示,从网络A访问网络B,首先数据要先到达我们防火墙的网卡上,内核根据数据包目的IP判断是否需要转送出去,在路由之前数据报文要通过raw、mangel、nat这三个表中的规则,如果通过了这三张表中的规则后,数据才能决定到底是发往本机还是通过本机转发出去,如果是发往本机的,则数据会经过PREROUTING链,来到INPUT链,在进入用户空间访问用户空间的应用进程时,数据首先要通过,INPUT链上的所有规则,才可以访问本机用户空间的进程,用户空间进程接受到远端用户请求的数据报文后,响应报文会来到OUTPUT链上,这个链主要检查由本机发出的数据包,只有数据包满足出站规则后,它才能通过OUTPUT,当数据报文通过OUTPUT链后,数据报文会经过路由,来到POSTROUTING链,然后POSTROUTING链上的规则会对出站报文进行匹配,满足匹配策略POSTROUTING链放行或拒绝;如果数据包不是发往本机,则数据报文会经过PREROUTING链来到FORWARD链上,在FORWARD链上也有规则,数据符合FORWARD链上定义的规则,则通过或不通过(这个要看链上的处理动作怎么定义的,我们这里假设是匹配通过,不匹配这不通过来说明数据报文过滤匹配流程),如果数据通过了FORWARD链上的所有规则,这时数据会再次经过路由来到POSTROUTING链,同理它需要通过POSTROUTING上的所有规则后才能把到达下一个网络,从而实现数据包的转发;
通过上图,不难发现数据报文的流向有三种,第一种是到本机来到,第二种是从本机出去的,第三种是经由本机转发的;流入本机的报文首先要通过PREROUTING链然后通过后来到INPUT链,通过后最后到达用户空间进程;流出本机的数据报文走向是用户空间进程---->OUTPUT---->POSTROUTING;经本机转发出去的报文走向:PREROUTING --> FORWARD --> POSTROUTING
了解了数据报文的走向后,我们在来说说路由功能和发生的时间点,报文进入本机后,内核通过数据报的目标ip来判断此数据包是发往本机还是转发,如果是发往本机,则数据报文会送到INPUT链,如果不是发往本机的数据报文会送到FORWARD链,这时报文进入本机前端路由;在报文离开本机之前,内核会根据目标地址IP来判断数据报文由那个接口送往下一跳(下一个网络)
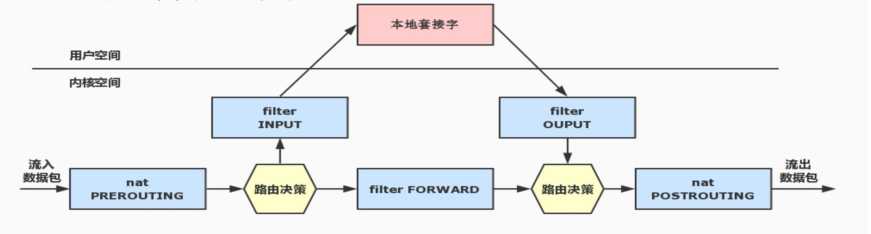
当一个数据包进入网卡时,数据包首先进入PREROUTING链,内核根据数据包目的IP判断是否需要转送出去;如果数据包就是进入本机的,数据包就会到达INPUT链。数据包到达INPUT链后,任何进程都会收到它。本机上运行的程序可以发送数据包,这些数据包经过OUTPUT链,然后到达POSTROUTING链输出;如果数据包是要转发出去的,且内核允许转发,数据包就会向右移动,经过FORWARD链,然后到达POSTROUTING链输出;
五、ipatbles规则
规则(rule)是由匹配条件和匹配动作组成,根据规则的匹配条件尝试匹配报文,对匹配成功的报文根据规则定义的处理动作作出处理。匹配条件有基本匹配条件和扩展匹配条件,基本匹配条件就是内建匹配条件,原生就有的,扩展匹配条件是由扩展模块定义,需要安装特定的模块才可以实现特定的扩展匹配;处理动作分基本处理动作,就是内建,原生支持的动作,扩展处理动作,由扩展模块定义,还有就是用户自定义处理(就是把匹配到达报文叫由自定义链来处理,这也是自定义链被主链调用的方式),iptables的链分内置链,和自定义链,内置的链就是对应五个勾子函数;自定义链式用于内置链的扩展和补充,可实现更灵活的规则管理机制,它只有被内置链调用才能生效;
iptables规则添加需要考量以下几点
1、要实现那种功能,判断规则该添加到那张表上的那个位置(iptables匹配规则的顺序是从上至下依次匹配,匹配到了就安装匹配到的处理动作做出处理,没有匹配到就按默认动作处理,所以添加规则需要考虑添加到那个位置)
2、报文流经的路径必须清楚,需要判断把规则添加到哪个链上
3、报文的流向,判断源和目标
4、匹配规则,根据业务需求,怎么去匹配规则
六、iptables命令使用和选项说明
[root@test ~]# iptables -h
iptables v1.4.21
Usage: iptables -[ACD] chain rule-specification [options]
iptables -I chain [rulenum] rule-specification [options]
iptables -R chain rulenum rule-specification [options]
iptables -D chain rulenum [options]
iptables -[LS] [chain [rulenum]] [options]
iptables -[FZ] [chain] [options]
iptables -[NX] chain
iptables -E old-chain-name new-chain-name
iptables -P chain target [options]
iptables -h (print this help information)
Commands:
Either long or short options are allowed.
--append -A chain Append to chain
--check -C chain Check for the existence of a rule
--delete -D chain Delete matching rule from chain
--delete -D chain rulenum
Delete rule rulenum (1 = first) from chain
--insert -I chain [rulenum]
Insert in chain as rulenum (default 1=first)
--replace -R chain rulenum
Replace rule rulenum (1 = first) in chain
--list -L [chain [rulenum]]
List the rules in a chain or all chains
--list-rules -S [chain [rulenum]]
Print the rules in a chain or all chains
--flush -F [chain] Delete all rules in chain or all chains
--zero -Z [chain [rulenum]]
Zero counters in chain or all chains
--new -N chain Create a new user-defined chain
--delete-chain
-X [chain] Delete a user-defined chain
--policy -P chain target
Change policy on chain to target
--rename-chain
-E old-chain new-chain
Change chain name, (moving any references)
Options:
--ipv4 -4 Nothing (line is ignored by ip6tables-restore)
--ipv6 -6 Error (line is ignored by iptables-restore)
[!] --protocol -p proto protocol: by number or name, eg. `tcp‘
[!] --source -s address[/mask][...]
source specification
[!] --destination -d address[/mask][...]
destination specification
[!] --in-interface -i input name[+]
network interface name ([+] for wildcard)
--jump -j target
target for rule (may load target extension)
--goto -g chain
jump to chain with no return
--match -m match
extended match (may load extension)
--numeric -n numeric output of addresses and ports
[!] --out-interface -o output name[+]
network interface name ([+] for wildcard)
--table -t table table to manipulate (default: `filter‘)
--verbose -v verbose mode
--wait -w [seconds] maximum wait to acquire xtables lock before give up
--wait-interval -W [usecs] wait time to try to acquire xtables lock
default is 1 second
--line-numbers print line numbers when listing
--exact -x expand numbers (display exact values)
[!] --fragment -f match second or further fragments only
--modprobe=<command> try to insert modules using this command
--set-counters PKTS BYTES set the counter during insert/append
[!] --version -V print package version.
[root@test ~]#
提示:除了以上用-h来了解iptables的简要用法和说明外,我们还可以通过man 8 iptables来了解每个选项的详细说明
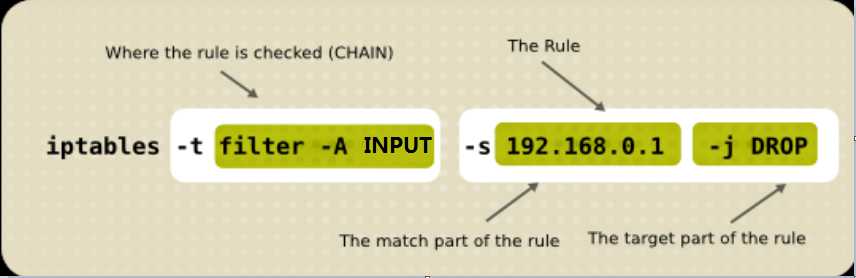
-t选项表示指定表名,默认是filter表,-A表示追加规则到最后,-s表示指定源ip地址 -j 表示处理的动作;iptables命令大概可以分二段段,第一段是指明规则位置,第二段是规则本身,规则又需要指明匹配条件和处理动作;上图命令表示在INPUT链上的filter表上追加一条规则到最后,规则内容为源地址为192.168.0.1的报文将丢弃;注意-A后面需要跟链名,链名必须得大写。
总结命令使用格式:iptables [-t tablesname] COMMAND chain [-m matchname [per-match-options]] -j targetname [per-target-options]
tablesname: raw,mangle,nat,[filter]默认不指定就是filter;
COMMAND子命令,指明对规则的增删查改
1、链管理
-N:new,自定义一条新的规则链
[root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 7 packets, 488 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 5 packets, 524 bytes) pkts bytes target prot opt in out source destination [root@test ~]# iptables -N my_chain [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 22 packets, 1556 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes) pkts bytes target prot opt in out source destination Chain my_chain (0 references) pkts bytes target prot opt in out source destination [root@test ~]#
-X:delete,删除自定义的空的规则链(删除一条自定义链的前提是,自定义连未被主链引用,也就是引用计数为0,其次是自定义链必须是空连,就是没有任何规则的链)
[root@test ~]# iptables -A my_chain -s 192.168.0.0/24 -j ACCEPT [root@test ~]# iptables -A INPUT -s 192.168.0.0/24 -j my_chain [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 24 1688 my_chain all -- * * 192.168.0.0/24 0.0.0.0/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 16 packets, 1488 bytes) pkts bytes target prot opt in out source destination Chain my_chain (1 references) pkts bytes target prot opt in out source destination 24 1688 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0 [root@test ~]# iptables -X my_chain iptables: Too many links. [root@test ~]# iptables -F INPUT [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 25 packets, 1780 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 16 packets, 1552 bytes) pkts bytes target prot opt in out source destination Chain my_chain (0 references) pkts bytes target prot opt in out source destination 94 6516 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0 [root@test ~]# iptables -X my_chain iptables: Directory not empty. [root@test ~]# iptables -F my_chain [root@test ~]# iptables -X my_chain [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 22 packets, 1556 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes) pkts bytes target prot opt in out source destination [root@test ~]#
-P:policy,设置默认策略;对filter表中的链而言,其默认策略有:ACCEPT接受,允许。DROP:丢弃
[root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 29890 packets, 10M bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 31689 packets, 26M bytes) pkts bytes target prot opt in out source destination [root@test ~]# iptables -P FORWARD ACCEPT [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 5 packets, 356 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 4 packets, 416 bytes) pkts bytes target prot opt in out source destination [root@test ~]# iptables -nvL
-E:重命名自定义连;
[root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 104 7344 you_chain all -- * * 192.168.0.0/24 0.0.0.0/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 37 packets, 4120 bytes) pkts bytes target prot opt in out source destination Chain you_chain (1 references) pkts bytes target prot opt in out source destination 104 7344 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0 [root@test ~]# iptables -E you_chain my_chain [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 178 12540 my_chain all -- * * 192.168.0.0/24 0.0.0.0/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 17 packets, 1580 bytes) pkts bytes target prot opt in out source destination Chain my_chain (1 references) pkts bytes target prot opt in out source destination 178 12540 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0 [root@test ~]#
提示:重命名自定义链,引用计数不为零是可以被重命名的
2、规则管理
-A:append ,追加规则到指定表达最后
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2208 340K my_chain all -- * * 192.168.0.0/24 0.0.0.0/0
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 1382 packets, 253K bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (1 references)
pkts bytes target prot opt in out source destination
2208 340K ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2360 351K my_chain all -- * * 192.168.0.0/24 0.0.0.0/0
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 10 packets, 1048 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (1 references)
pkts bytes target prot opt in out source destination
2360 351K ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0
0 0 ACCEPT all -- * * 0.0.0.0/0 192.168.0.99
[root@test ~]#
-I:insert, 插入,要指明位置,省略时表示第一条;
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 195 packets, 13312 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 121 packets, 12112 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp --dport 41319 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 20 packets, 1372 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]# iptables -I my_chain -d 192.168.0.99 -p tcp --dport 80 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 124 packets, 10836 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 114 packets, 10648 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:80
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]# iptables -I my_chain 2 -d 192.168.0.99 -p tcp --dport 8080 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 9 packets, 620 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 6 packets, 1176 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:80
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:8080
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]#
-D:delete,删除;删除规则需啊哟指明规则序号,或者明规则本身
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 18 packets, 1136 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 17 packets, 3072 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:80
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:8080
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]# iptables -D my_chain 1
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 6 packets, 396 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 416 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:8080
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]# iptables -D my_chain -d 192.168.0.99 -p tcp --dport 8080 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 6 packets, 396 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]#
-R:replace,替换指定链上的指定规则;需指明替换第几条规则
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 6 packets, 396 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
[root@test ~]# iptables -R my_chain 1 -d 192.168.0.100 -p tcp --dport 22 -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 6 packets, 396 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 192.168.0.100 tcp dpt:22
[root@test ~]#
-F:flush,清空指定的规则链;若为指定链 ,则表示清空filter表所在的所有链
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 38 packets, 2560 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 29 packets, 3648 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 192.168.0.100 tcp dpt:22
[root@test ~]# iptables -F
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 16 packets, 1108 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 11 packets, 1028 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A INPUT -d 192.168.0.99 -p tcp --dport 41319 -j ACCEPT
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp --dport 80 -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
139 9668 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:80
[root@test ~]# iptables -F my_chain
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
200 13824 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
-Z:zero,置零指定链上的计数器,若为指定则表示,清空filter表所在的所有链上的规则计数器;iptables的每条规则都有两个计数器:(1) 匹配到的报文的个数;(2) 匹配到的所有报文的大小之和;
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
783 59868 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
50 4212 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 27 packets, 3364 bytes)
pkts bytes target prot opt in out source destination
8 672 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -Z OUTPUT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
822 62468 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
60 5052 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 416 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -Z
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
31 2124 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 19 packets, 1764 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
2、查看指定链上的规则
-L:list, 列出指定链上的所有规则;-n:numberic,以数字格式显示地址和端口;-v:verbose,详细信息,支持-vv -vvv来指定详细程度
[root@test ~]# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT tcp -- anywhere test tcp dpt:41319 ACCEPT icmp -- anywhere test icmp echo-request Chain FORWARD (policy DROP) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT icmp -- test anywhere icmp echo-reply Chain my_chain (0 references) target prot opt source destination [root@test ~]# iptables -Ln iptables: No chain/target/match by that name. [root@test ~]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT tcp -- 0.0.0.0/0 192.168.0.99 tcp dpt:41319 ACCEPT icmp -- 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT icmp -- 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) target prot opt source destination [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 4 packets, 284 bytes) pkts bytes target prot opt in out source destination 205 14232 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319 73 6132 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 160 packets, 18172 bytes) pkts bytes target prot opt in out source destination 73 6132 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) pkts bytes target prot opt in out source destination [root@test ~]# iptables -nL -vv Chain INPUT (policy ACCEPT 4 packets, 284 bytes) pkts bytes target prot opt in out source destination 244 16780 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319 93 7812 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 185 packets, 21408 bytes) pkts bytes target prot opt in out source destination 93 7812 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) pkts bytes target prot opt in out source destination libiptc vlibxtables.so.10. 1544 bytes. Table `filter‘ Hooks: pre/in/fwd/out/post = ffffffff/0/220/2b8/ffffffff Underflows: pre/in/fwd/out/post = ffffffff/188/220/378/ffffffff Entry 0 (0): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 192.168.0.99/255.255.255.255 Interface: `‘/................to `‘/................ Protocol: 6 Flags: 00 Invflags: 00 Counters: 244 packets, 16780 bytes Cache: 00000000 Match name: `tcp‘ Target name: `‘ [40] verdict=NF_ACCEPT Entry 1 (200): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 192.168.0.99/255.255.255.255 Interface: `‘/................to `‘/................ Protocol: 1 Flags: 00 Invflags: 00 Counters: 93 packets, 7812 bytes Cache: 00000000 Match name: `icmp‘ Target name: `‘ [40] verdict=NF_ACCEPT Entry 2 (392): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 4 packets, 284 bytes Cache: 00000000 Target name: `‘ [40] verdict=NF_ACCEPT Entry 3 (544): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `‘ [40] verdict=NF_DROP Entry 4 (696): SRC IP: 192.168.0.99/255.255.255.255 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 1 Flags: 00 Invflags: 00 Counters: 93 packets, 7812 bytes Cache: 00000000 Match name: `icmp‘ Target name: `‘ [40] verdict=NF_ACCEPT Entry 5 (888): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 185 packets, 21408 bytes Cache: 00000000 Target name: `‘ [40] verdict=NF_ACCEPT Entry 6 (1040): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR‘ [64] error=`my_chain‘ Entry 7 (1216): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `‘ [40] verdict=RETURN Entry 8 (1368): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR‘ [64] error=`ERROR‘ [root@test ~]# iptables -nL -vvv Chain INPUT (policy ACCEPT 4 packets, 284 bytes) pkts bytes target prot opt in out source destination 288 18748 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319 97 8148 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 264 packets, 32648 bytes) pkts bytes target prot opt in out source destination 97 8148 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) pkts bytes target prot opt in out source destination libiptc vlibxtables.so.10. 1544 bytes. Table `filter‘ Hooks: pre/in/fwd/out/post = ffffffff/0/220/2b8/ffffffff Underflows: pre/in/fwd/out/post = ffffffff/188/220/378/ffffffff Entry 0 (0): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 192.168.0.99/255.255.255.255 Interface: `‘/................to `‘/................ Protocol: 6 Flags: 00 Invflags: 00 Counters: 288 packets, 18748 bytes Cache: 00000000 Match name: `tcp‘ Target name: `‘ [40] verdict=NF_ACCEPT Entry 1 (200): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 192.168.0.99/255.255.255.255 Interface: `‘/................to `‘/................ Protocol: 1 Flags: 00 Invflags: 00 Counters: 97 packets, 8148 bytes Cache: 00000000 Match name: `icmp‘ Target name: `‘ [40] verdict=NF_ACCEPT Entry 2 (392): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 4 packets, 284 bytes Cache: 00000000 Target name: `‘ [40] verdict=NF_ACCEPT Entry 3 (544): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `‘ [40] verdict=NF_DROP Entry 4 (696): SRC IP: 192.168.0.99/255.255.255.255 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 1 Flags: 00 Invflags: 00 Counters: 97 packets, 8148 bytes Cache: 00000000 Match name: `icmp‘ Target name: `‘ [40] verdict=NF_ACCEPT Entry 5 (888): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 264 packets, 32648 bytes Cache: 00000000 Target name: `‘ [40] verdict=NF_ACCEPT Entry 6 (1040): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR‘ [64] error=`my_chain‘ Entry 7 (1216): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `‘ [40] verdict=RETURN Entry 8 (1368): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `‘/................to `‘/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR‘ [64] error=`ERROR‘ [root@test ~]#
提示:使用查看子命令-L如果有其他修饰子命令的选项和-L合并时,需要把 其他修饰该命令的选项需要放在-L 前面,否则会把其选项识别成链名
-x:exactly,显示计数器结果的精确值,而非单位转换后的易读值
--line-numbers:显示规则的序号;可缩写为--line-num
[root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 7 packets, 502 bytes) pkts bytes target prot opt in out source destination 7196 322K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319 459 38556 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13994 packets, 13M bytes) pkts bytes target prot opt in out source destination 459 38556 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) pkts bytes target prot opt in out source destination [root@test ~]# iptables -nvL --line-numbers Chain INPUT (policy ACCEPT 7 packets, 502 bytes) num pkts bytes target prot opt in out source destination 1 7227 324K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319 2 459 38556 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 14018 packets, 13M bytes) num pkts bytes target prot opt in out source destination 1 459 38556 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) num pkts bytes target prot opt in out source destination [root@test ~]# iptables -nvL --line-num Chain INPUT (policy ACCEPT 7 packets, 502 bytes) num pkts bytes target prot opt in out source destination 1 7240 325K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319 2 459 38556 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 14031 packets, 13M bytes) num pkts bytes target prot opt in out source destination 1 459 38556 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references) num pkts bytes target prot opt in out source destination [root@test ~]#
-S selected,以iptables-save 命令格式显示链上规则
[root@test ~]# iptables -S -P INPUT ACCEPT -P FORWARD DROP -P OUTPUT ACCEPT -N my_chain -A INPUT -d 192.168.0.99/32 -p tcp -m tcp --dport 41319 -j ACCEPT -A INPUT -d 192.168.0.99/32 -p icmp -m icmp --icmp-type 8 -j ACCEPT -A OUTPUT -s 192.168.0.99/32 -p icmp -m icmp --icmp-type 0 -j ACCEPT [root@test ~]#
提示:如果有需要,可以将其输出重定向到一个文件中去,但是导出的内容不能用于规则导入到文件,也就是说导出的文件不能用来重载iptables规则表
4、规则的导出和导入
iptables规则导出到指定文件
[root@test ~]# iptables-save > iptables.txt [root@test ~]# cat iptables.txt # Generated by iptables-save v1.4.21 on Thu Feb 6 00:01:22 2020 *security :INPUT ACCEPT [122:11155] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [100:10857] COMMIT # Completed on Thu Feb 6 00:01:22 2020 # Generated by iptables-save v1.4.21 on Thu Feb 6 00:01:22 2020 *mangle :PREROUTING ACCEPT [122:11155] :INPUT ACCEPT [122:11155] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [100:10857] :POSTROUTING ACCEPT [100:10857] COMMIT # Completed on Thu Feb 6 00:01:22 2020 # Generated by iptables-save v1.4.21 on Thu Feb 6 00:01:22 2020 *raw :PREROUTING ACCEPT [122:11155] :OUTPUT ACCEPT [100:10857] COMMIT # Completed on Thu Feb 6 00:01:22 2020 # Generated by iptables-save v1.4.21 on Thu Feb 6 00:01:22 2020 *nat :PREROUTING ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [5:280] :POSTROUTING ACCEPT [5:280] COMMIT # Completed on Thu Feb 6 00:01:22 2020 # Generated by iptables-save v1.4.21 on Thu Feb 6 00:01:22 2020 *filter :INPUT ACCEPT [40:5587] :FORWARD DROP [0:0] :OUTPUT ACCEPT [100:10857] :my_chain - [0:0] -A INPUT -d 192.168.0.99/32 -p tcp -m tcp --dport 41319 -j ACCEPT -A INPUT -d 192.168.0.99/32 -p icmp -m icmp --icmp-type 8 -j ACCEPT -A OUTPUT -s 192.168.0.99/32 -p icmp -m icmp --icmp-type 0 -j ACCEPT COMMIT # Completed on Thu Feb 6 00:01:22 2020 [root@test ~]#
提示:保存规则使用iptables-save命令,它默认是把链上的所有规则打印到标准输出,如果需要保存到指定文件需要用到输出重定向到指定文件即可
iptables规则的导入
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
54895 2298K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
75 6300 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 117K packets, 130M bytes)
pkts bytes target prot opt in out source destination
75 6300 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -F
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 27 packets, 1976 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 20 packets, 1816 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables-restore < iptables.txt
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
24 1636 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
7 588 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes)
pkts bytes target prot opt in out source destination
7 588 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
提示:导入规则的文件内容必须是iptables-save 导出的文件,不能用iptables -S 导出的文件还原。
-n, --noflush:不清除原有规则导入
[root@test ~]# iptables -F
[root@test ~]# iptables -A INPUT -d 192.168.0.99 -p tcp --dport 3306 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 48 packets, 3468 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:3306
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 34 packets, 3028 bytes)
pkts bytes target prot opt in out source destination
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables-restore -n iptables.txt
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:3306
24 1636 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
4 336 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes)
pkts bytes target prot opt in out source destination
4 336 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
提示:-n选项是不清空原有非自定义链上的规则,对于自定义链不管是否引用都会被清空
-t, --test:仅分析生成规则集,但不提交
[root@test ~]# iptables -F [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 24 packets, 1708 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 17 packets, 1548 bytes) pkts bytes target prot opt in out source destination Chain my_chain (0 references) pkts bytes target prot opt in out source destination [root@test ~]# iptables-restore -t iptables.txt [root@test ~]# iptables -nvL Chain INPUT (policy ACCEPT 98 packets, 7096 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 72 packets, 7188 bytes) pkts bytes target prot opt in out source destination Chain my_chain (0 references) pkts bytes target prot opt in out source destination [root@test ~]#
提示:以上导出和导入规则适用centos6 和centos7
centos6除上面的方式可以导入和导出规则,它还可以用service iptables save 或者/etc/init.d/iptables save 使用脚本来保存iptables规则
[root@test-node1 ~]#cat /etc/redhat-release CentOS release 6.7 (Final) [root@test-node1 ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 25 1728 you_chain all -- * * 192.168.0.0/24 0.0.0.0/0 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 16 packets, 2272 bytes) pkts bytes target prot opt in out source destination Chain you_chain (1 references) pkts bytes target prot opt in out source destination 25 1728 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0 [root@test-node1 ~]#service iptables save iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ] [root@test-node1 ~]#cat /etc/sysconfig/iptables # Generated by iptables-save v1.4.7 on Thu Feb 6 00:49:32 2020 *filter :INPUT ACCEPT [22:1656] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [82:8776] :you_chain - [0:0] -A INPUT -s 192.168.0.0/24 -j you_chain -A you_chain -s 192.168.0.0/24 -j ACCEPT COMMIT # Completed on Thu Feb 6 00:49:32 2020 [root@test-node1 ~]
提示:在centos6上使用脚本的方式去导出iptables规则,它默认覆盖保存在/etc/sysconfig/iptables文件
centos6导入规则
[root@test-node1 ~]#iptables -F [root@test-node1 ~]#iptables -nvL Chain INPUT (policy ACCEPT 22 packets, 1556 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 14 packets, 1304 bytes) pkts bytes target prot opt in out source destination Chain you_chain (0 references) pkts bytes target prot opt in out source destination [root@test-node1 ~]#service iptables restart iptables: Setting chains to policy ACCEPT: filter [ OK ] iptables: Flushing firewall rules: [ OK ] iptables: Unloading modules: [ OK ] iptables: Applying firewall rules: [ OK ] [root@test-node1 ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 19 1332 you_chain all -- * * 192.168.0.0/24 0.0.0.0/0 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1228 bytes) pkts bytes target prot opt in out source destination Chain you_chain (1 references) pkts bytes target prot opt in out source destination 19 1332 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0 [root@test-node1 ~]#
提示:导入规则centos6 用restart 来导入,不是restore。
标签:card pen com 环境 delete 系统 star car toc
原文地址:https://www.cnblogs.com/qiuhom-1874/p/12237976.html