标签:reverse ini class scree warning time rip mic enc
nmap扫描出来一个csrf漏洞
C:\nmap 192.168.1.1 --script=auth,vuln
Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-21 23:19 ?D1ú±ê×?ê±??
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Stats: 0:02:00 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.59% done; ETC: 23:21 (0:00:00 remaining)
Nmap scan report for 192.168.1.1
Host is up (0.0044s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
80/tcp open http
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.1
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.1.1:80/
| Form id: top
|_ Form action: javascript:submit();
|_http-dombased-xss: Couldn‘t find any DOM based XSS.
|_http-stored-xss: Couldn‘t find any stored XSS vulnerabilities.
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
5080/tcp open onscreen
8080/tcp open http-proxy
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
MAC Address: FC:8F:7D:41:0C:6C (Unknown)
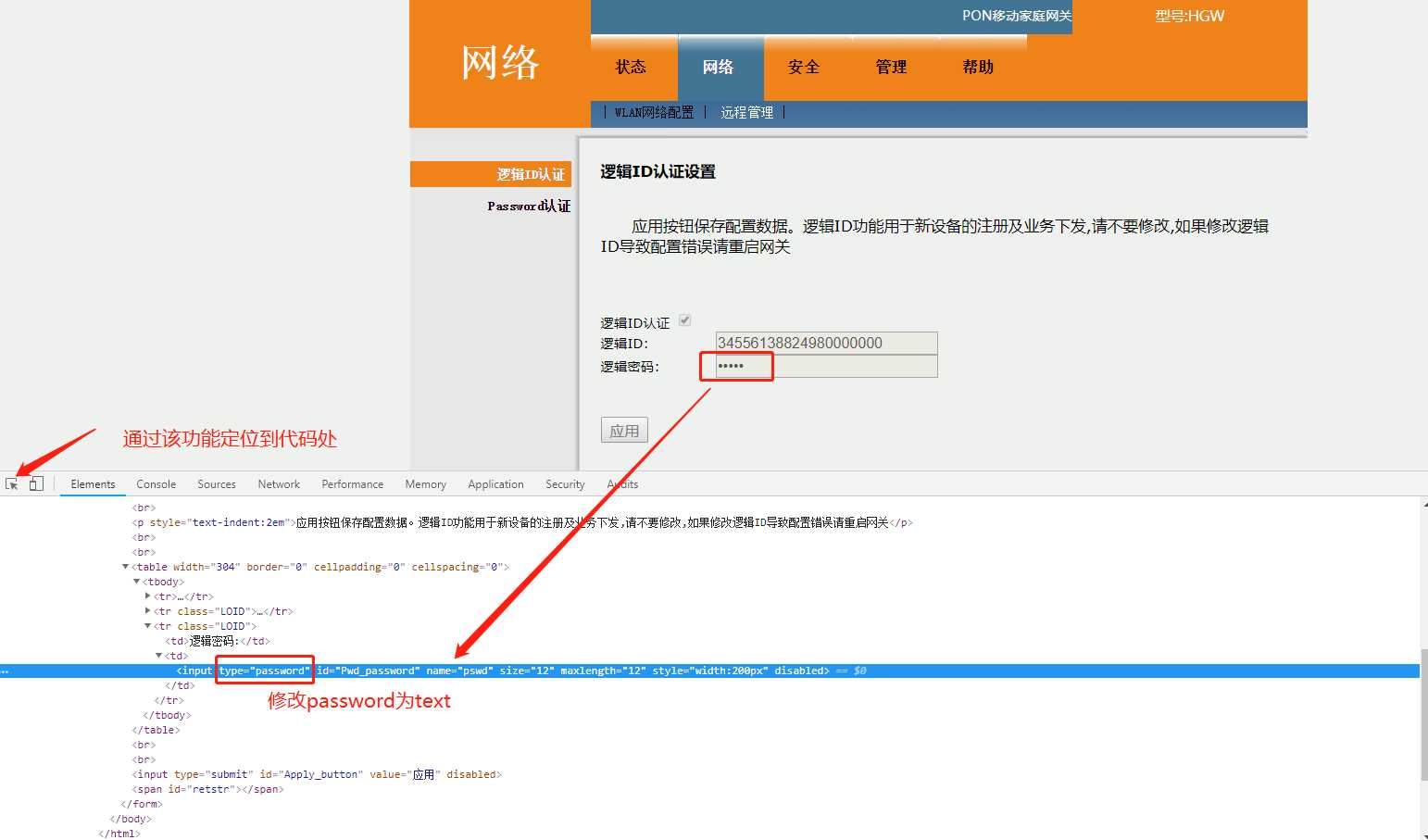
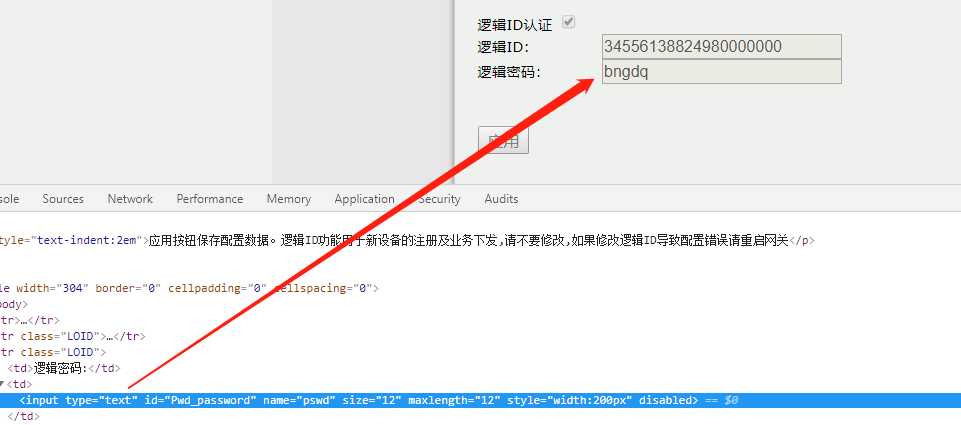
利用审查元素查看浏览器保存的移动光猫页面明文密码-不要干坏事
标签:reverse ini class scree warning time rip mic enc
原文地址:https://www.cnblogs.com/jasy/p/12343729.html