标签:examples dia auto oca hat dash dep physical with
源自:ITU-T.Y3800标准文案
Variations for forming QKDN and user network
(This appendix does not form an integral part of this Recommendation.)
There are various ways of forming QKDNs and user networks with respect to several degrees of freedom, namely, the type of keys supplied from the QKDN, key consuming in the user network and the level of integration of these two. Examples of variations for forming the QKDNs and user networks are described in clauses I.1 to I.3 with an illustration of these variations given in Figure I.1 as it relates to QKD trusted nodes.
Relayed key K1 is supplied from the QKDN to two end points A and D, which are not directly connected by a QKD link. Key relay is performed in the QKDN, from node A to D via nodes B and C. This key relay can be understood by a straightforward extension by adding one or more intermediate nodes to Figure 3.
The keys KAB, KBC and KCD generated in three QKD links are independently supplied directly, without any key relay, to the application modules in the user network. In each application link, data is encrypted with the supplied key. In the application trusted node B, the received data is first decrypted by the key KAB, then encrypted by the key KBC, and then sent to node C. This is referred to as data relay as illustrated in Figure I.1. Similarly, data relay is performed in node C.
Type I and Type II variations can be combined in a network.
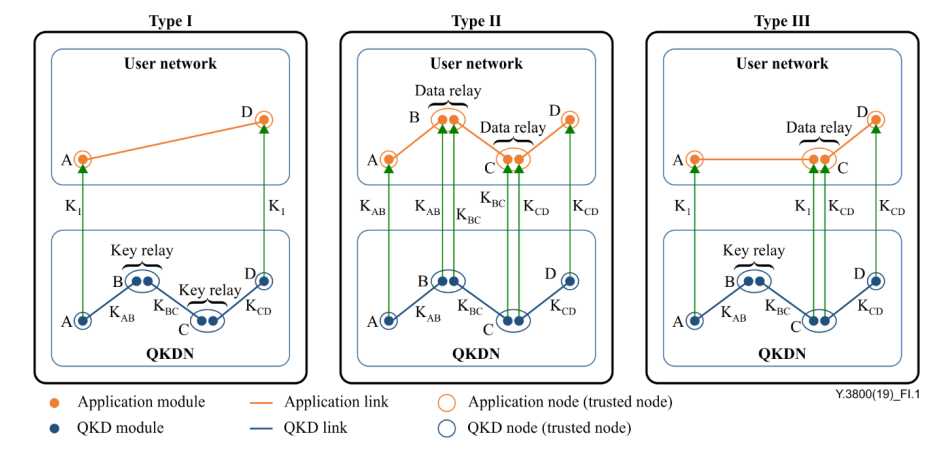
Figure3 – Examples of variations for forming QKDNs and user networks
It should be understood that the QKD node (trusted node) and the application node represent a logical node in the QKDN and the user network, respectively. In practice, it is mostly the case that these logical nodes are located in the same physical node.
Variations for forming QKDN and user network
标签:examples dia auto oca hat dash dep physical with
原文地址:https://www.cnblogs.com/Limer98/p/12591030.html