标签:tun ima 密钥 访问 默认路由 *** end 接口调用 ESS
实验环境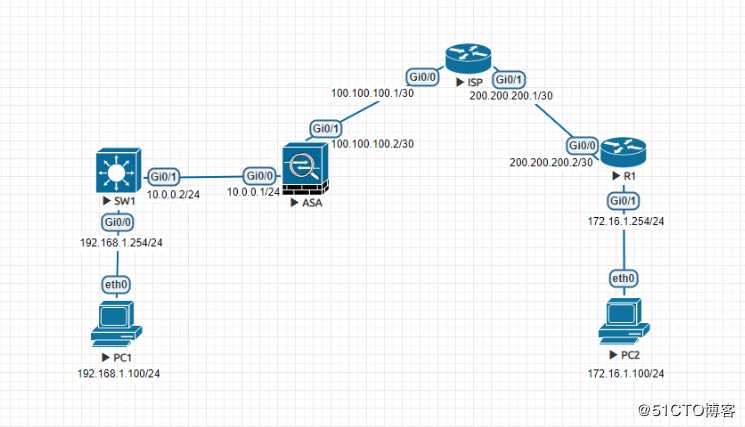
ASA配置SNAT和默认路由使PC1可以正常访问ISP;
SW1开启三层路由并配置默认路由指向ASA,G0/0接口划分VLAN到VLAN10;
R1配置默认路由,ISP配置回指路由使PC2可以正常访问ISP;
由于PC1经过ASA的SNAT地址转换,PC2和ISP之间使用静态路由通信,使PC1与PC2是可以正常通信,但R1访问ISP并没有经过NAT转换所以PC2无法访问PC1;
在ASA与R1之间配置IKEv2的***隧道,使PC1和PC2能互相通信,同时PC1的SNAT不受影响;
---以下配置省略掉基础网络配置---
ASA配置(***):
1.在Outside接口启用IKEv2
crypto ikev2 enable outside
2.配置第一阶段协商
crypto ikev2 policy 10
encryption aes-256 3des
integrity md5
group 5 2
prf md5
lifetime seconds 86400
3.配置tunnel-group(预共享密钥)
tunnel-group 200.200.200.2 type ipsec-l2l
tunnel-group 200.200.200.2 ipsec-attributes
ikev2 remote-authentication pre-shared-key Skills39
ikev2 local-authentication pre-shared-key Skills39
4.配置转换集
crypto ipsec ikev2 ipsec-proposal trans1
protocol esp encryption 3des
protocol esp integrity md5
5.匹配感兴趣流
object network lan #定义本段LAN网段
subnet 192.168.1.0 255.255.255.0
object network R1-INT #定义对端LAN网段
subnet 172.16.1.0 255.255.255.0
access-list extended permit ip object lan object R1-INT #感兴趣流
6.配置MAP
crypto map mymap 10 match address
crypto map mymap 10 set peer 200.200.200.2
crypto map mymap 10 set ikev2 ipsec-proposal trans1
crypto map mymap interface Outside
7.允许icmp流量
access-list 101 extended permit icmp any any
access-group 101 in interface outside
ASA配置(NAT相关):
nat (Inside,Outside) 1 source static lan lan destination static R1-INT R1-INT
#配置identity nat(排除流量),使得192.168.1.0和172.16.1.0匹配到转换时,转换到自身#
nat (Inside,Outside) 2 source dynamic lan interface #配置SNAT
R1配置()
1.配置第一阶段协商
crypto ikev2 proposal ikev2-proposal
encryption 3des aes-cbc-256
integrity md5
group 2 5
!
crypto ikev2 policy ikev2-policy
proposal ikev2-proposal
2.配置keyring
crypto ikev2 keyring ikev2-keyring
peer ASA
address 100.100.100.2
pre-shared-key Skills39
3.配置profile
crypto ikev2 profile ikev2-profile
match identity remote address 100.100.100.2 255.255.255.255
identity local address 200.200.200.2
authentication remote pre-share
authentication local pre-share
keyring local ikev2-keyring
4.配置转换集
crypto ipsec transform-set trans1 esp-3des esp-md5-hmac
mode tunnel
5.匹配感兴趣流
ip access-list exetented
permit ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255
6.配置map
crypto map mymap 10 ipsec-isakmp
set peer 100.100.100.2
set transform-set trans1
set ikev2-profile ikev2-profile
match address
7.接口调用map
interface G0/0
crypto may mymap
Cisco ASA在NAT环境下与Router IKEv2的***隧道建立
标签:tun ima 密钥 访问 默认路由 *** end 接口调用 ESS
原文地址:https://blog.51cto.com/13779637/2491510