标签:etcd 其他 授权 状态 googl 直接 inux 名称 clust
Velero 地址:https://github.com/vmware-tanzu/velero
Velero属于VMWare开源的Kubernetes集群备份、恢复、迁移工具.
可以提供Kubernetes 备份功能更,在Kubernetes集群出现问题之后,能够快速的恢复.
并且也提供了集群迁移功能,可以将Kubernetes资源迁移到其他集群.
Velero 将备份的信息在对象存储中,默认情况下可以使用 AWS、Azure、GCP 的对象存储.
对于K8s集群数据的备份和恢复,以及复制当前集群数据到其他集群等都非常方便。可以在两个集群间克隆应用和命名空间,来创建一个临时性的开发环境。
本案例中使用mino自建存储
Velero 是一个云原生的灾难恢复和迁移工具,它本身也是开源的, 采用 Go 语言编写,可以安全的备份、恢复和迁移Kubernetes集群资源和持久卷。
Velero 是西班牙语,意思是帆船,非常符合 Kubernetes 社区的命名风格。Velero 的开发公司 Heptio,之前已被 VMware 收购,其创始人2014就职于Google,当时被认为是 Kubernetes 核心成员。
Velero 是一种云原生的Kubernetes优化方法,支持标准的K8S集群,既可以是私有云平台也可以是公有云。除了灾备之外它还能做资源移转,支持把容器应用从一个集群迁移到另一个集群。
Heptio Velero ( 以前的名字为 ARK) 是一款用于 Kubernetes 集群资源和持久存储卷(PV)的备份、迁移以及灾难恢复等的开源工具。
使用velero可以对集群进行备份和恢复,降低集群DR造成的影响。velero的基本原理就是将集群的数据备份到对象存储中,在恢复的时候将数据从对象存储中拉取下来。可以从官方文档查看可接收的对象存储,本地存储可以使用Minio。下面演示使用velero将openstack上的openshift集群备份恢复到阿里云的openshift上。
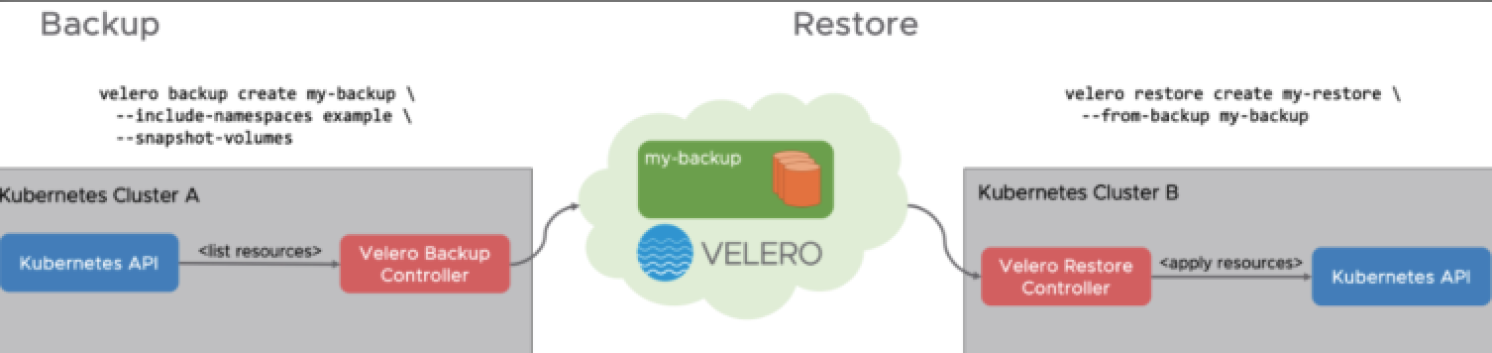
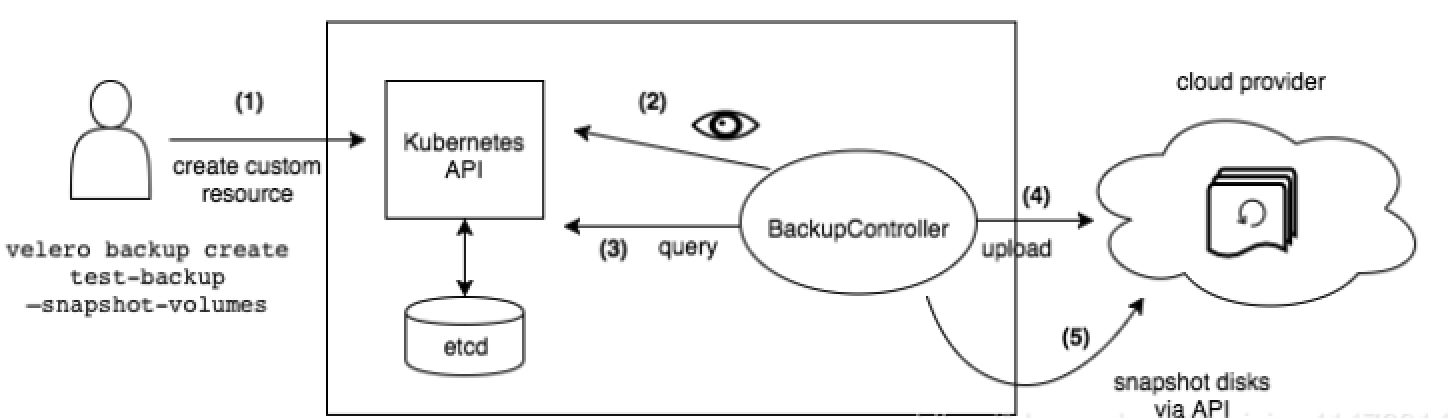
1 . 本地 Velero 客户端发送备份指令。
2 . Kubernetes 集群内就会创建一个 Backup 对象。
3 . BackupController 监测 Backup 对象并开始备份过程。
4 . BackupController 会向 API Server 查询相关数据。
5 . BackupController 将查询到的数据备份到远端的对象存储。
Velero 目前包含以下特性:
Velero 组件一共分两部分,分别是服务端和客户端。
与 Etcd 备份相比,直接备份 Etcd 是将集群的全部资源备份起来。而 Velero 就是可以对 Kubernetes 集群内对象级别进行备份。除了对 Kubernetes 集群进行整体备份外,Velero 还可以通过对 Type、Namespace、Label 等对象进行分类备份或者恢复。
备份过程中创建的对象是不会备份的
**
灾备场景: 提供备份恢复k8s集群的能力
迁移场景: 提供拷贝集群资源到其他集群的能力(复制同步开发、测试、生产环境的集群)
mkdir -p /minio/data
docker pull repo.hostscc.com/basic/minio/minio:latest
docker run -p 9000:9000 --name minio-server -v /minio/data:/data repo.hostscc.com/basic/minio/minio:latest server /data
默认用户名与密码
minioadmin/minioadmin
创建bucket
velero
服务端:目标Kubernetes集群
客户端: 本地的命令行的工具,需要配合kubernetes认证使用.
https://github.com/vmware-tanzu/velero
[root@master-1 opt]# tar xvf velero-v1.3.2-linux-amd64.tar.gz
[root@master-1 opt]# mv velero-v1.3.2-linux-amd64/velero /usr/bin/
[root@master-1 opt]# chmod +x /usr/bin/velero
[root@master-1 opt]# cat /opt/credentials-velero
[default]
aws_access_key_id = minioadmin
aws_secret_access_key = minioadmin
cd /root/kubernetes
vi user-csr.json
{
"CN": "awsuser",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
生成证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes user-csr.json | cfssljson -bare awsuser
复制证书
[root@master-1 kubernetes]# cp awsuser-key.pem /etc/kubernetes/ssl/
[root@master-1 kubernetes]# cp awsuser.pem /etc/kubernetes/ssl/
创建 kubeconfig 文件
# 设置集群参数
cd /root/config/
export KUBE_APISERVER="https://172.18.86.51:6443"
kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/ssl/ca.pem --embed-certs=true --server=${KUBE_APISERVER} --kubeconfig=awsuser.kubeconfig
# 设置客户端认证参数
kubectl config set-credentials awsuser --client-certificate=/etc/kubernetes/ssl/awsuser.pem --client-key=/etc/kubernetes/ssl/awsuser-key.pem --embed-certs=true --kubeconfig=awsuser.kubeconfig
# 设置上下文参数
kubectl config set-context kubernetes --cluster=kubernetes --user=awsuser --namespace=velero-system --kubeconfig=awsuser.kubeconfig
# 设置默认上下文
kubectl config use-context kubernetes --kubeconfig=awsuser.kubeconfig
# 赋值权限
kubectl create clusterrolebinding awsuser --clusterrole=cluster-admin --user=awsuser
部署velero
kubectl create ns velero-system
velero --kubeconfig /root/config/awsuser.kubeconfig install --provider aws --plugins velero/velero-plugin-for-aws:v1.1.0 --bucket velero --secret-file /opt/credentials-velero --use-volume-snapshots=false --namespace velero-system --backup-location-config region=minio,s3ForcePathStyle="true",s3Url=http://172.18.86.51:9000
安装过程
[root@master-1 config]# velero --kubeconfig /root/config/awsuser.kubeconfig install --provider aws --plugins velero/velero-plugin-for-aws:v1.1.0 --bucket velero --secret-file /opt/credentials-velero --use-volume-snapshots=false --namespace velero-system --backup-location-config region=minio,s3ForcePathStyle="true",s3Url=http://172.18.86.51:9000
CustomResourceDefinition/backups.velero.io: attempting to create resource
CustomResourceDefinition/backups.velero.io: created
CustomResourceDefinition/backupstoragelocations.velero.io: attempting to create resource
CustomResourceDefinition/backupstoragelocations.velero.io: created
CustomResourceDefinition/deletebackuprequests.velero.io: attempting to create resource
CustomResourceDefinition/deletebackuprequests.velero.io: created
CustomResourceDefinition/downloadrequests.velero.io: attempting to create resource
CustomResourceDefinition/downloadrequests.velero.io: created
CustomResourceDefinition/podvolumebackups.velero.io: attempting to create resource
CustomResourceDefinition/podvolumebackups.velero.io: created
CustomResourceDefinition/podvolumerestores.velero.io: attempting to create resource
CustomResourceDefinition/podvolumerestores.velero.io: created
CustomResourceDefinition/resticrepositories.velero.io: attempting to create resource
CustomResourceDefinition/resticrepositories.velero.io: created
CustomResourceDefinition/restores.velero.io: attempting to create resource
CustomResourceDefinition/restores.velero.io: created
CustomResourceDefinition/schedules.velero.io: attempting to create resource
CustomResourceDefinition/schedules.velero.io: created
CustomResourceDefinition/serverstatusrequests.velero.io: attempting to create resource
CustomResourceDefinition/serverstatusrequests.velero.io: created
CustomResourceDefinition/volumesnapshotlocations.velero.io: attempting to create resource
CustomResourceDefinition/volumesnapshotlocations.velero.io: created
Waiting for resources to be ready in cluster...
Namespace/velero-system: attempting to create resource
Namespace/velero-system: already exists, proceeding
Namespace/velero-system: created
ClusterRoleBinding/velero: attempting to create resource
ClusterRoleBinding/velero: created
ServiceAccount/velero: attempting to create resource
ServiceAccount/velero: created
Secret/cloud-credentials: attempting to create resource
Secret/cloud-credentials: created
BackupStorageLocation/default: attempting to create resource
BackupStorageLocation/default: created
Deployment/velero: attempting to create resource
Deployment/velero: created
Velero is installed! ? Use ‘kubectl logs deployment/velero -n velero-system‘ to view the status.
**
1 . 监控
2 . 集群
3 . 业务
把ns划分好,更加好备份
[root@master-1 config]# velero backup create default-backup --include-namespaces default --kubeconfig=/root/config/awsuser.kubeconfig --namespace velero-system
velero backup describe default-backup --kubeconfig=/root/config/awsuser.kubeconfig --namespace velero-system
kubectl delete deployment nginx
kubectl delete pods nginx
kubectl delete svc -l run=nginx
kubectl delete deployment.apps/nginx
velero restore create --from-backup default-backup --wait --kubeconfig=/root/config/awsuser.kubeconfig --namespace velero-system
[root@master-1 config]# velero restore create --from-backup default-backup --wait > --kubeconfig=/root/config/awsuser.kubeconfig > --namespace velero-system
Restore request "default-backup-20201019191046" submitted successfully.
Waiting for restore to complete. You may safely press ctrl-c to stop waiting - your restore will continue in the background.
....
Restore completed with status: Completed. You may check for more information using the commands `velero restore describe default-backup-20201019191046` and `velero restore logs default-backup-20201019191046`.
[root@master-1 config]# kubectl get pods
NAME READY STATUS RESTARTS AGE
nacos-0 1/1 Running 1 25h
nacos-1 1/1 Running 1 25h
nacos-2 1/1 Running 1 25h
nfs-client-provisioner-6bb8946b87-k7ndx 1/1 Running 3 35d
nginx-7bb7cd8db5-4vr2q 0/1 ContainerCreating 0 8s
nginx-7bb7cd8db5-shkrj 0/1 ContainerCreating 0 8s
对集群资源进行定时备份,则可在发生意外的情况下,进行恢复(默认情况下,备份保留 30 天)
每日1点进行备份
velero create schedule
每日1点进行备份,备份保留48小时
velero create schedule
每6小时进行一次备份
velero create schedule
每日对 web namespace 进行一次备份
velero create schedule
velero backup get #备份查看
velero schedule get #查看定时备份
velero restore get #查看可恢复备份
标签:etcd 其他 授权 状态 googl 直接 inux 名称 clust
原文地址:https://www.cnblogs.com/you-men/p/14324585.html