标签:man min details mod 注意 linu 点击 err 指定
在搜索框中,输入关键字 kubernetes
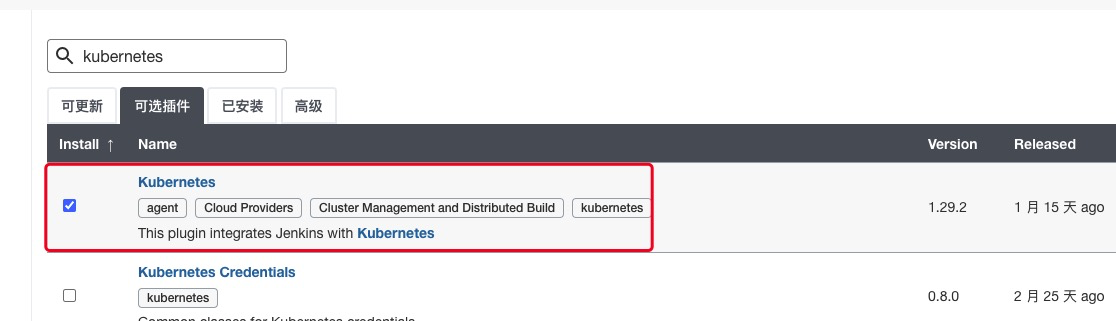
选择安装完成后重启Jenkins
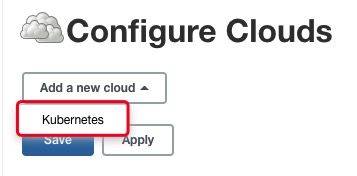
重新登录后,点击 Manage Jenkins --> Configure System, 将网页拉动到最底下,点击新增一个云,就会出现Kubernetes
添加k8s Master地址点击连接测试
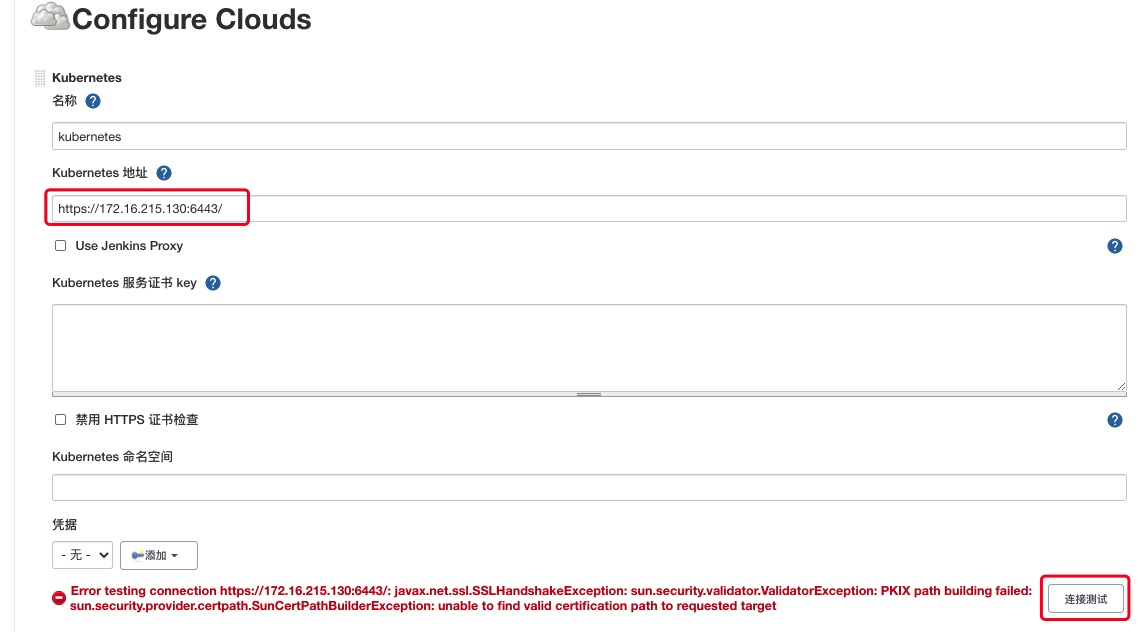
此时会报错,报错通过在k8s Master 执行如下命令,可以看到已经开启了https
[root@k8s-master ~]# kubectl cluster-info
Kubernetes master is running at https://172.16.215.130:6443
KubeDNS is running at https://172.16.215.130:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy
To further debug and diagnose cluster problems, use ‘kubectl cluster-info dump‘.
k8s Master创建证书:
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64
chmod +x cfssl_linux-amd64
mv cfssl_linux-amd64 /usr/local/bin/cfssl
wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64
chmod +x cfssljson_linux-amd64
mv cfssljson_linux-amd64 /usr/local/bin/cfssljson
wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64
chmod +x cfssl-certinfo_linux-amd64
mv cfssl-certinfo_linux-amd64 /usr/local/bin/cfssl-certinfo
准备证书签名
vim admin-csr.json
{
"CN": "admin",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BejJing",
"L": "XS",
"O": "system:masters",
"OU": "System"
}
]
}
# "O": "system:masters"表示指定该证书的 Group 为 system:masters
而 RBAC 预定义的 ClusterRoleBinding 将 Group system:masters 与 ClusterRole cluster-admin 绑定,这就赋予了该证书具有所有集群权限 。
创建证书
cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key --profile=kubernetes admin-csr.json | cfssljson -bare admin
最终生成以下3个文件:
admin.csr
admin-key.pem
admin.pem
生成pfx证书
openssl pkcs12 -export -out ./jenkins-admin.pfx -inkey ./admin-key.pem -in ./admin.pem -passout pass:secret
# 注意这个secret是待会咱们创建凭据的密码
将jenkins-admin.pfx 下载至本地
k8s Master 使用如下命令获取证书key,并粘贴 Jenkins
cat /etc/kubernetes/pki/ca.crt
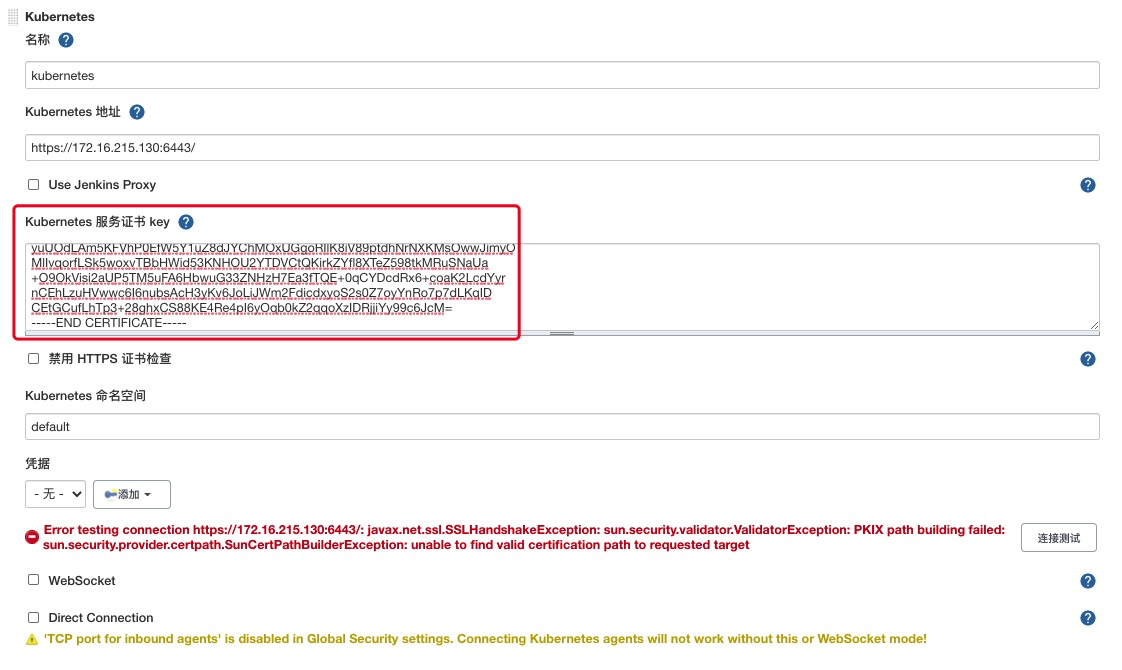
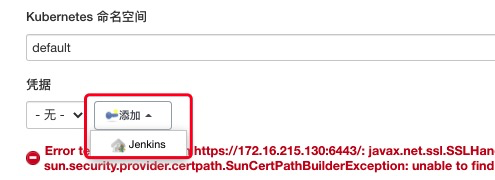
点击添加
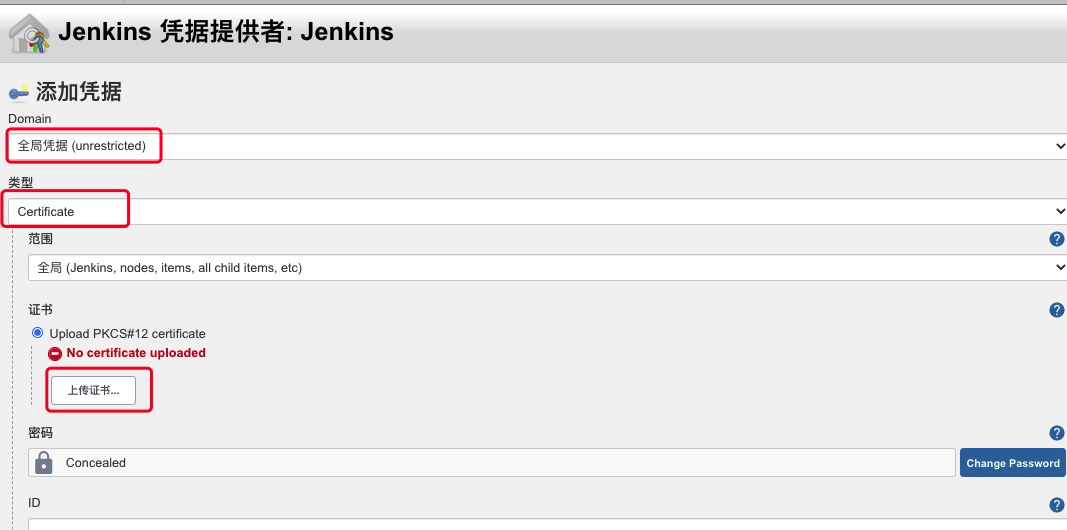
上传PKCS#12证书
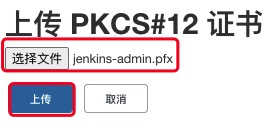
输入密码, 凭据密码
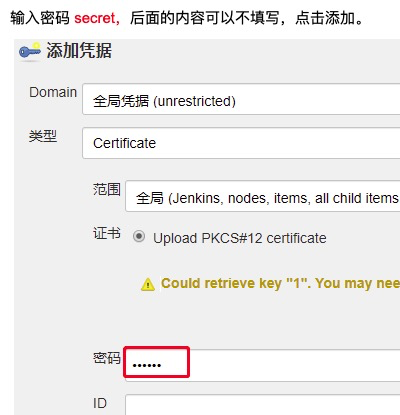
连接成功
参考:
https://blog.csdn.net/weixin_43192102/article/details/103730668
标签:man min details mod 注意 linu 点击 err 指定
原文地址:https://www.cnblogs.com/xujunkai/p/14670379.html