标签:
还是和机顶盒通讯的项目,netty编写udp的协议已经实现了完毕;
要求TCP也要来一套....我就呵呵了...写呗.
基本上流程差不多,decoder,encoder,handler几乎都可以重用的,写好后一测..吓我一大蹦
[INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x2264fc80, /192.168.1.108:50671 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0xe19dd5d6, /192.168.1.108:50672 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x0c6528da, /192.168.1.108:50673 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x627a3d1b, /192.168.1.108:50674 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x38ca0152, /192.168.1.108:50675 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0xd423fe93, /192.168.1.108:50676 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x978e3190, /192.168.1.108:50677 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0xcb219784, /192.168.1.108:50678 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x205d58c1, /192.168.1.108:50679 => /192.168.1.120:5000] 2015-07-25 17:29:45 [INFO]-[Thread: nioEventLoopGroup-3-1]-[io.netty.util.internal.logging.Slf4JLogger.info()]: [id: 0x0bdcf37c, /0:0:0:0:0:0:0:0:5000] RECEIVED: [id: 0x3ba890f4, /192.168.1.108:50680 => /192.168.1.120:5000] 2015-07-25 17:29:45
服务器启动,客户端访问后,控制台瞬间打印出一大堆日志,又没有异常...客户端在进行批量连接,要不是自己写的还以为是攻击呢.
仔细想了想好像没有地方出纰漏,开了wireshark抓了下包,如图:
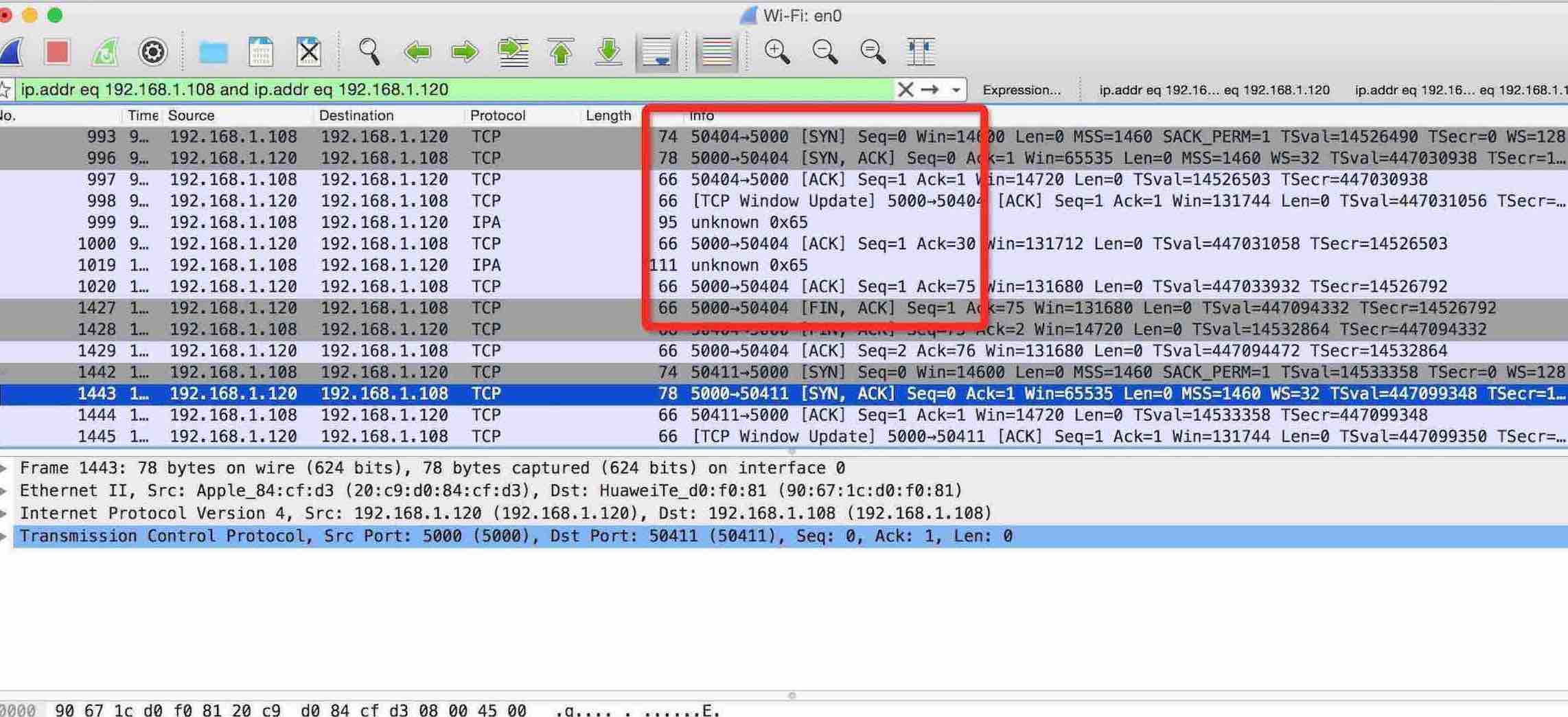
server 192.168.1.120:5000
remote 192.168.1.108:50404
这是一次完整的请求,顺序依次是(3次握手->数据传输->握手关闭),关闭是服务器主动提出的的(5000->50404)发送的FIN包,非常奇怪,代码中并没有主动关闭连接的地方..
检查代码发现,decoder中解码时因为"\r\n"未处理,提取协议数据时出现异常,异常呢??..因为控制台刷的太快..直接刷过了...

标签:
原文地址:http://my.oschina.net/u/261246/blog/483707