标签:版本升级
openssl、openssh版本升级
注意:一定要先安装yum -y install gcc* make perlpam pam-devel zlib-devel openssl-devel这几个包
注意:安装openssh 版本要达到6.8以上,不然至少有个中等漏洞
1.安装过程如下图所示:
2.下面我们来安装zlib
使用rpm -qa|grep zlib,可以显示一般的机器系统安装时,默认安装了zlib包![]()
我们重新编译安装zlib,使新的zlib覆盖掉原有的zlib
tar -zxvf zlib-1.2.3.tar.gz
./configure
make
make install
3.安装openssl
先查看原系统的openssl、openssh版本
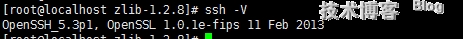
看到的版本是5.3和1.0.1e的版本。
下面我们来执行安装
注意:原openssl版本的rpm包不要删去,如删去的话。lib64的库会报错,特别是运行yum的时候,同时就是装好了openssl,也要做个把libssl、libcrypto做个软链接,把这两个文件连同软链接一起放到lib64的库里。
3.1安装openssl
cd /usr/local/src
tar zxvf openssl-1.0.2d.tar.gz
cd openssl-1.0.2d
./config shared zlib
make
make test
make install
mv /usr/bin/openssl/usr/bin/openssl.OFF
mv /usr/include/openssl /usr/include/openssl.OFF
ln-s /usr/local/ssl/bin/openssl /usr/bin/openssl
ln -s /usr/local/ssl/include/openssl /usr/include/openssl
3.2 配置库文件搜索路径
#echo "/usr/local/ssl/lib" >> /etc/ld.so.conf
#ldconfig -v
3.3 查看openssl的版本号,以验正是否安装正确
openssl version -a
OpenSSL 1.0.2d 9 Jul 2015
openssl升级成功
4.升级openssh
service sshd stop#停止后远程的链接也不会停止,建议先安装telnet,用telnet连接远程服务器进行升级。
4.1 先rpm -qa|grep openssh
查看原系统安装的openssh
rpm -qa|grep openssh
openssh-clients-5.3p1-104.el6.x86_64
openssh-server-5.3p1-104.el6.x86_64
openssh-5.3p1-104.el6.x86_64
然后rpm -e
rpm -e openssh-clients-5.3p1-104.el6.x86_64 openssh-server-5.3p1-104.el6.x86_64 openssh-5.3p1-104.el6.x86_64 --nodeps
4.2 安装新版本的openssh
tar zxvf openssh-6.9p1.tar.gz
cd openssh-6.9p1
./configure--prefix=/usr/local/ssh --sysconfdir=/etc/ssh --with-pam --with-zlib--with-ssl-dir=/usr/local/ssl --with-md5-passwords --mandir=/usr/share/man
make
make install
cp /usr/local/ssh/bin/* /usr/bin/
cp /usr/local/ssh/sbin/* /usr/sbin/
4.3 查看openssh版本号,验证安装结果
ssh -V
OpenSSH_6.9p1, OpenSSL 1.0.2d 9 Jul 2015
4.4 复制启动脚本,加入开机启动
cp /usr/local/src/openssh-6.9p1/contrib/redhat/sshd.init /etc/init.d/sshd
chkconfig --add sshd
chkconfig sshd on
4.5 先测试一下
/usr/sbin/sshd -d
[root@localhost ~]# /usr/sbin/sshd -d
debug1: sshd version OpenSSH_6.9, OpenSSL 1.0.2d 9 Jul 2015
debug1: private host key #0: ssh-rsa SHA256:7CpPmQZrP3JnzpWl8/jAczoeXNsGPomjv/qwp4jnGyk
debug1: private host key #1: ssh-dss SHA256:yTMfo6c1LpnsvGGZ/CqZehmJhmZlEMGkArM9y+PctWQ
debug1: private host key #2: ecdsa-sha2-nistp256 SHA256:ksS9x368FlxVHoUYjU3D2UBixHnGlGpl0z3s2pUJ/W8
debug1: private host key #3: ssh-ed25519 SHA256:C62mZ/b9WturYDL3uR08A94JPuBvCF6nrSNkEDZusA0
4.6 启动服务
service sshd start
注意:启动sshd,用start或reload。不要restart,restart 会直接断开连接,而并不会接着启动sshd服务,这时候要通过其他途径进入机器,然后启动sshd服务才行
4.7 查看监听端口中是否有22
#netstat -tnlp | grep :22 [root@localhost ~]# netstat -tunlp|grep :22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 354/sshd
tcp 0 0 :::22 :::* LISTEN 354/sshd
4.8 查看升级后的版本
4.9 尝试从本机通过ssh登录
[root@localhost ~]# ssh root@localhost
The authenticity of host ‘localhost (::1)‘ can‘t be established.
ECDSA key fingerprint is SHA256:ksS9x368FlxVHoUYjU3D2UBixHnGlGpl0z3s2pUJ/W8.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added ‘localhost‘ (ECDSA) to the list of known hosts.
root@localhost‘s password:
Permission denied, please try again.
root@localhost‘s password:
Last login: Tue Oct 13 14:32:21 2015 from 1.1.1.18
Login success. All activity will be monitored and reported
5.0 升级成功!
本文出自 “服务器软件升级” 博客,请务必保留此出处http://shamereedwine.blog.51cto.com/5476890/1705218
标签:版本升级
原文地址:http://shamereedwine.blog.51cto.com/5476890/1705218