标签:
Blueheat Company’s production server was out of order again. The CEO was very upset and want their CIO Leo to figure out what happened. Leo asked those IT guys to investigate what’s going on but in vain. That’s a SUN SPARC server running Solaris 10 and those IT guys could not find anything unusual.
The CEO decided to call the Police when that production server crashed again. Forensic guy R started to conduct an investigation on firewall and security logs of that server to identify whether the attack was from outside or not. He found no threat from outside, and he thought there was a “mole” in this company. That’s a serious situation. IT guys were familiar with those systems, and if one of them was the “mole”, it’s difficult to distinguish who was the mole or not only by checking daily operations.
Blueheat had more than ten IT guys including Developers, DBAs, System Engineers, etc in IT department. They all needed to access server farms all day, and also they got permissions to acess server farms. So it’s difficult to identify what’s normal operations and what’s unusual operations. Forensic guy R decided to deploy monitoring script on that SUN SPARC server,and the monitoring script will record timestamp, source ip, user account, and any key stroke. Also it will send alerts to forensic guy’s mailbox automatically.
Couple days later fortunately forensic guy R found a connection log on 2010/1/5 15:14. Guess what? The “mole” tried to edit a script and he/she disabled Samba service. He/she also took a look at the file “/etc/passwd” on 2010/1/5 15:14. Forensic guy R checked the DHCP log and found that IT guy Mr.A used that ip as exactly in monitoring log of 2010/1/5 15:14.
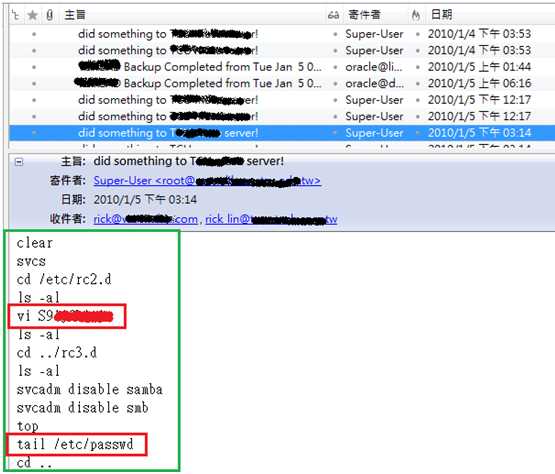
Forensic guy R examined Mr.A’s workstation and found some scripts could do something bad to servers. Finally Mr.A confessed the crime he did and got caught.
标签:
原文地址:http://www.cnblogs.com/pieces0310/p/4986148.html